In the 1960s and ’70s, the US firearms market saw an influx of cheaply-made, imported handguns. Legislators targeted the proliferation of these inexpensive and frequently unreliable weapons, ostensibly because they were believed to pose a risk to their owners and facilitate criminality. This was not an issue unique to the US or to that time period, of course; in the UK, where handguns are now strictly regulated, criminals often resort to reactivated, or even home-made or antique, firearms.
Despite ‘junk guns’ often being inaccurate and prone to malfunction, purchasing or creating them does have advantages for a would-be criminal. Such weapons are unlikely to be on law enforcement’s radar, and can be difficult to trace. They tend to be cheap, lowering the cost of entry to illicit ownership and usage. And they can often be made or obtained without needing access to extensive criminal networks.
During a recent investigation into several underground cybercrime forums – particularly those frequented by lower-skilled threat actors – Sophos X-Ops discovered something interesting: a ransomware equivalent to junk guns.
We found multiple examples of independently produced, inexpensive, and crudely-constructed ransomware, mostly sold as a one-time purchase rather than typical affiliate-based Ransomware-as-a-Service (RaaS) models (and none of the ‘junk-gun ransomware’ we found appears on the ransomwatch group index as of this writing). This appears to be a relatively new phenomenon (although, of course, threat actors have been creating and selling cheap, low-quality RATs and other malware for decades). We also saw other threat actors, a rung or two down the skills ladder, express interest in developing new ransomware – swapping tips on languages, evasion techniques, targets, and licencing models.
At first glance, the prospect of individuals making and selling junk-gun ransomware doesn’t seem to pose a significant threat; it’s a far cry from the notorious, well-organized ransomware groups that usually come to mind. Here, there are no leak sites; no initial access brokers (IABs); no affiliates; no corporate-like hierarchies; no multi-million dollar ransom demands; no publicity stunts; no high-profile targets; no sophisticated malware intended to defeat advanced EDR products; no seeking headlines and media attention; and little in-depth analysis by researchers.
But as we dug deeper, we uncovered some concerning intelligence. Some individuals claimed to have used junk-gun ransomware in real-world attacks, completing the entire attack chain by themselves, without IABs. Others advocated using it to attack small businesses and individuals – targets that the likes of Cl0p and ALPHV/BlackCat would probably not consider worthwhile, but which could nevertheless generate significant profit for an individual threat actor. Some users claimed to prefer standalone ransomware because they don’t have to profit-share – as in many RaaS models – or rely on infrastructure developed and operated by others.
Away from the complex infrastructure of modern ransomware, junk-gun ransomware allows criminals to get in on the action cheaply, easily, and independently. They can target small companies and individuals, who are unlikely to have the resources to defend themselves or respond effectively to incidents, without giving anyone else a cut.
Of course, junk-gun ransomware may occasionally blow up in threat actors’ faces – it may be defective, trigger alerts, or be backdoored as part of a scam – or their own lack of experience may result in failure or detection. In their minds, however, these are likely acceptable risks – not least because using junk-gun ransomware may eventually lead to more lucrative employment opportunities with prominent ransomware gangs.
In this article we’ll reveal our findings, share details of the junk-gun ransomware we found, and discuss the implications for organizations, the wider public, and the security community.
Off-the-shelf junk-gun ransomware
We observed 19 junk-gun ransomware varieties either offered for sale or cited as being under development, across four forums, between June 2023 and February 2024. Our findings are summarized in the table below.
| Name | Date posted | Status | Price | Language | Used in attacks | Detection | Features |
| CatLogs | December 2023 | For sale | Unknown | .NET | Unknown | Unknown | Stealer, RAT, ransomware, clipper, keylogger |
| Unnamed console app | November 2023 | In development | N/A | C# | N/A | Defender, 2/70 VT | Loops over desktop, documents, pictures, music, videos |
| Custom RaaS | July 2023 | For sale | $200 | Unknown | Unknown | Unknown | RSA 2048/4096, anti-VM and debugger, UAC bypass, random extensions |
| Diablo | January 2024 | For sale | $50 per month | Unknown | Unknown | Defender | AES, threaded, external drives, offline mode, Defender bypass, persistence |
| Evil Extractor | December 2023 | For sale | $99 – $199 per month | Unknown | Yes | Unknown | Stealer, RAT, ransomware, FTP server, crypter, persistence, self-destruct, anti-VM |
| HardShield | September 2023 | Open source | Free | C++ | Unknown | Unknown | CBC AES128+RSA 2048, delete shadow copies, threaded, self-deletion |
| Jigsaw | June 2023 | For sale | $500 | .NET | Unknown | Multiple | Offline encryption, AES-RSA, threaded |
| Kryptina | December 2023 | For sale | $20 for single build / $800 for source code / free | C | Unknown | Unknown | Targets Linux, threaded, offline, AES-256 CBC |
| Lolicrypt | August 2023 | For sale | $1000 | Unknown | Yes | Unknown | Intermittent encryption, chacha20, cross-platform |
| Loni | July 2023 | For sale | $999 per month / $9999 lifetime | C | Unknown | Unknown | Remote, delete shadow copies, self-destruct, XTEA, intermittent encryption |
| Nevermore | October 2023 | For sale | $250 | C# | Unknown | Defender | AES-256, threaded, stealer, unique payloads, |
| RansomTuga | June 2023 | Open source | Free | C++ | Unknown | Multiple | Stealer |
| Yasmha | February 2024 | For sale | $500 | C# | Unknown | Multiple | N/A |
| Ergon | September 2023 | For sale | 0.5 BTC per compile, 2.5 BTC for source code | Unknown | Yes | Unknown | Custom builds, support, RaaS model |
| Unnamed ransomware | September 2023 | In development | N/A | Go | N/A | Unknown | Salsa20 encryption |
| Unnamed ransomware | July 2023 | For sale | $1000 | C++ | Unknown | Unknown | Threaded, delete shadow copies, self-delete, partial and full encryption |
| Unnamed ransomware | January 2024 | For sale | $60 | Unknown | Unknown | Unknown | Customer provides RSA keys, ransom note, desktop background, etc |
| Unnamed ransomware | February 2024 | For sale | $50 | Python | Unknown | Unknown | Unknown |
| Unnamed ransomware | June 2023 | For sale | $500 | Unknown | Unknown | Unknown | No decryption key |
Table 1: An overview of the off-the-shelf junk-gun ransomware varieties we observed on four criminal forums, between June 2023 and February 2024
Cheap and cheerless
Of the 19 varieties we found, one had no price listed, two were open-source, and two were under active development and therefore had no price listed. Prices for the remaining 14 ranged from $20 (for a single build of Kryptina; we later noted that the Kryptina developer released their ransomware for free after struggling to make sales) to 0.5 BTC, or approximately $13,000 at the time of the posting.
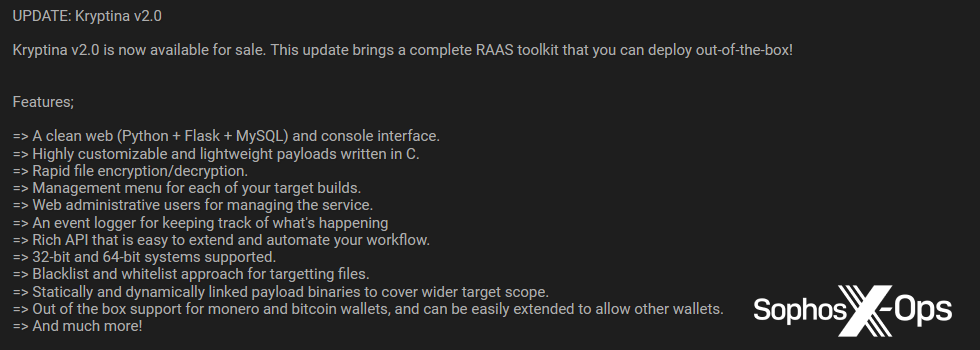
Figure 1: One of the adverts for Kryptina
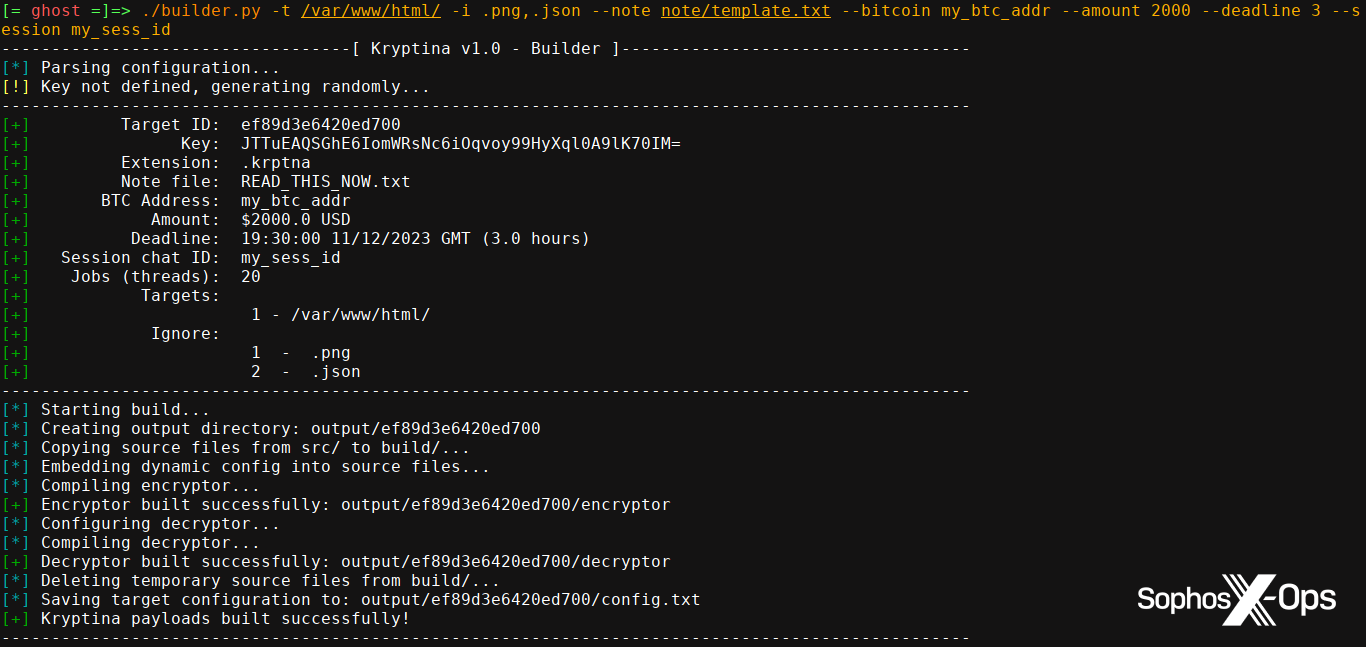
Figure 2: A screenshot showing a build of Kryptina, provided by the seller as part of their promotional materials

Figure 3: An advert for an unnamed junk-gun ransomware written in C++, offered for sale on a criminal forum
That 0.5 BTC price (for a single build of Ergon) appears to be something of an outlier, however. The median average price across all varieties was $375, and the mode was $500. The mean average was $1,302 including Ergon, but $402.15 without. That’s notably cheap, given that some RaaS affiliates reportedly pay up to thousands of dollars for access to kits (although note that some kits cost much less).
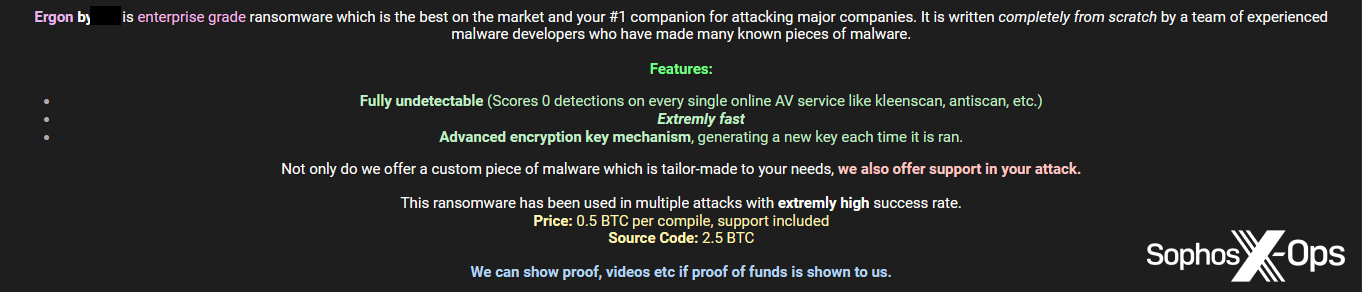
Figure 4: A post promoting the Ergon ransomware. Note the claim that Ergon “has been used in multiple attacks with extremly [sic] high success rate [emphasis in original].” We’ll cover in-the-wild junk-gun ransomware attacks shortly
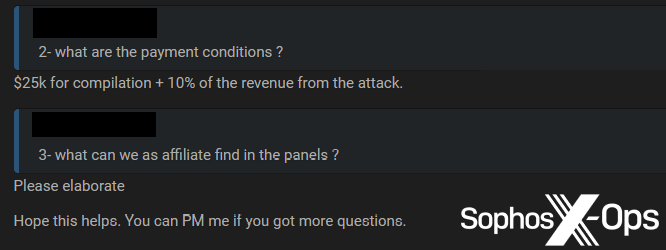
Figure 5: As well as its high price, Ergon was also an outlier in that its developer(s) asked for 10% of any revenue from attacks; we didn’t see this sort of stipulation anywhere else during our research
Most junk-gun ransomware was available for a single, one-off price. Only three adopted any sort of subscription model (Diablo, with licences at $50 per month; Evil Extractor, at $99 – $199 per month depending on the selected ‘plan’; and Loni, at $999 per month or $9,999 for a lifetime licence). Both Kryptina and Ergon also offered source code at a premium cost, relative to the price of a single build ($800 for Kryptina, and 2.5BTC, or about $39,000, for Ergon).
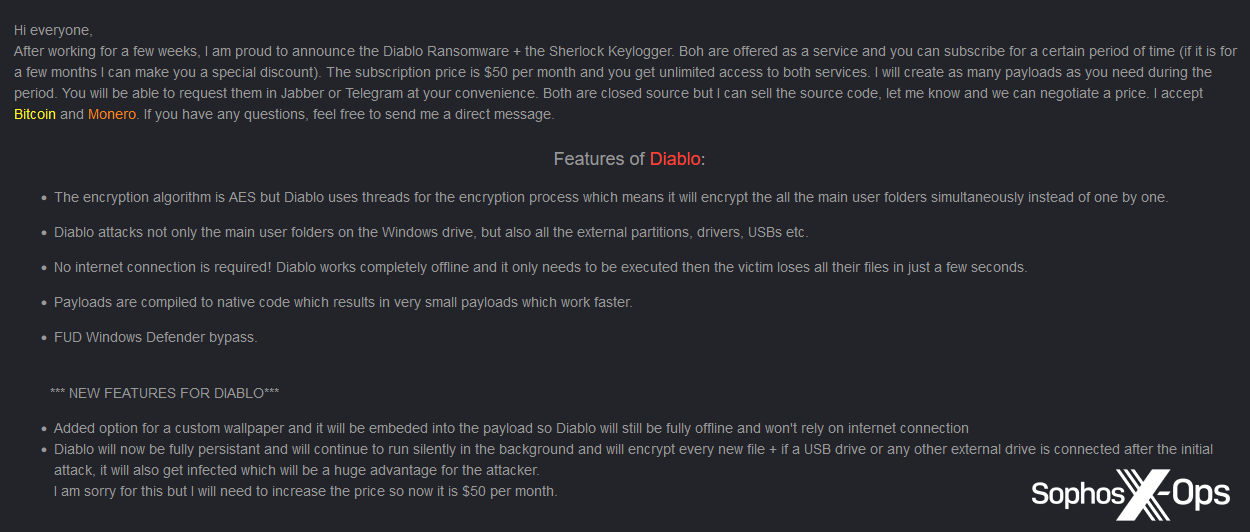
Figure 6: A post advertising the Diablo ransomware, with a subscription price of $50 per month
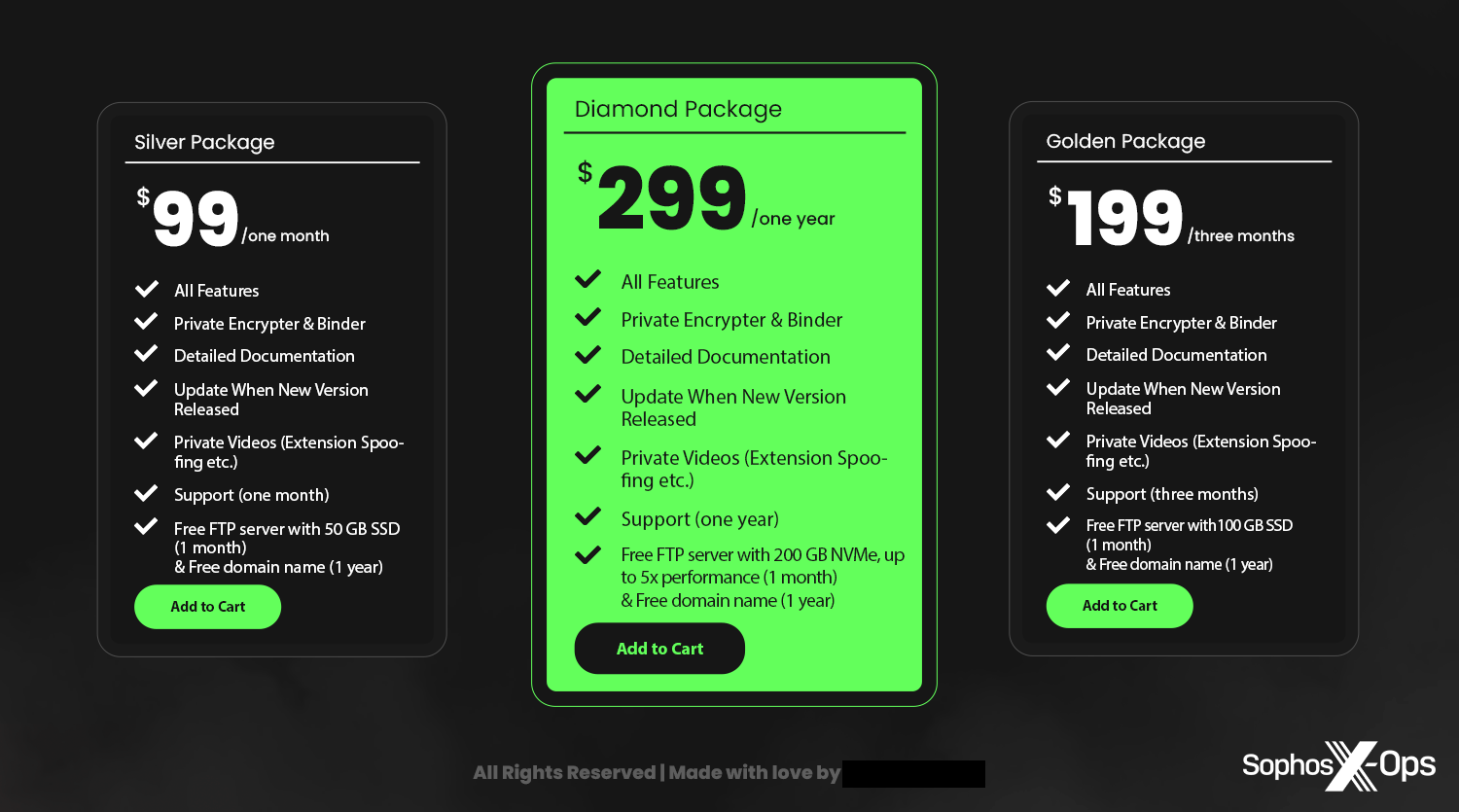
Figure 7: The available ‘packages’ for Evil Extractor
Interestingly, at least two examples of junk-gun ransomware – Diablo and Jigsaw – use names associated with historic ransomware families. Diablo was a variant of Locky in 2017, and Jigsaw (previously BitcoinBlackmailer) was released in 2016. This may be a coincidence, and neither seller stated that their ransomware was linked to these earlier families. That didn’t stop some users wondering if there was a connection, particularly in the case of Jigsaw – although the seller denied this.
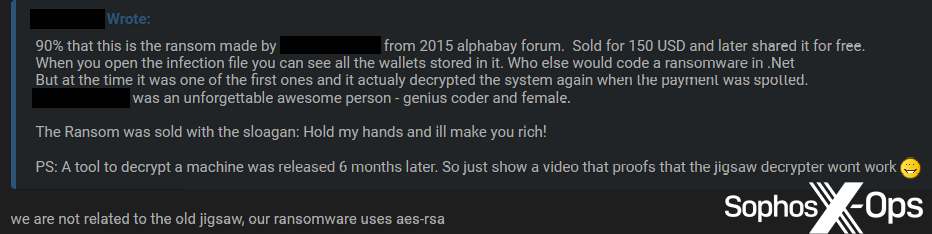
Figure 8: The Jigsaw seller/developer denies being connected to “the old jigsaw” ransomware
It’s possible that these threat actors are deliberately using the names of earlier, well-known ransomware to benefit from ‘brand recognition’ and give their junk gun variants an air of ‘legitimacy’ – despite the fact that they may be counterfeits.
In any case, it appears that at least some junk-gun ransomware developers are making money from their products. While the Kryptina developer admitted that they had struggled to turn a profit, the Nevermore developer said that they had made “more than I expected” from ransomware.
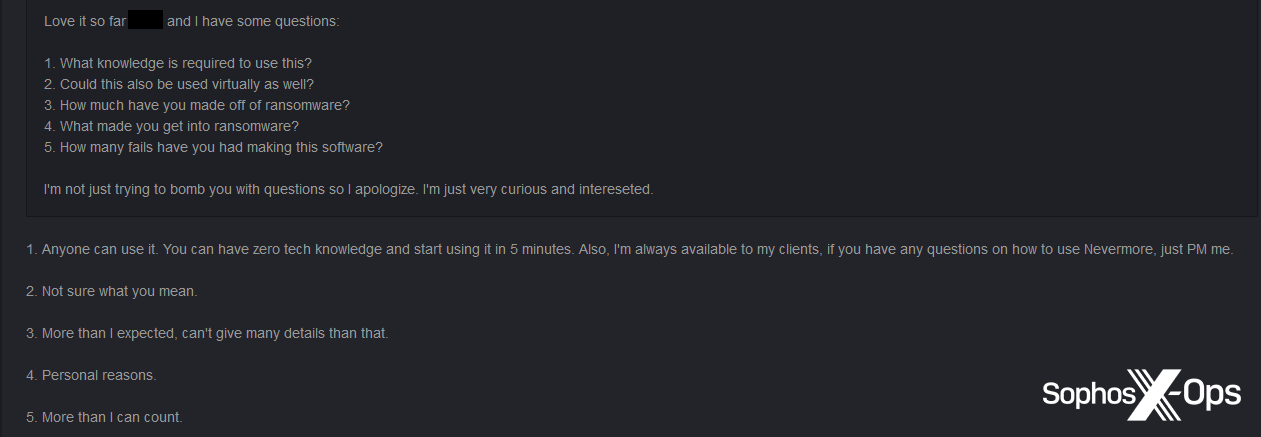
Figure 9: The Nevermore developer answers some questions from a forum user, including how much money they’ve made from ransomware
It’s worth noting at this juncture that some junk-gun ransomware may well be a scam. We’ve previously reported on criminals defrauding and hacking each other in a variety of ways on marketplaces – including ‘rip and run’ scams and backdoored malware – and it’s entirely possible that some of the variants we discuss here are schemes in this vein. We only found one allegation of this nature, however.
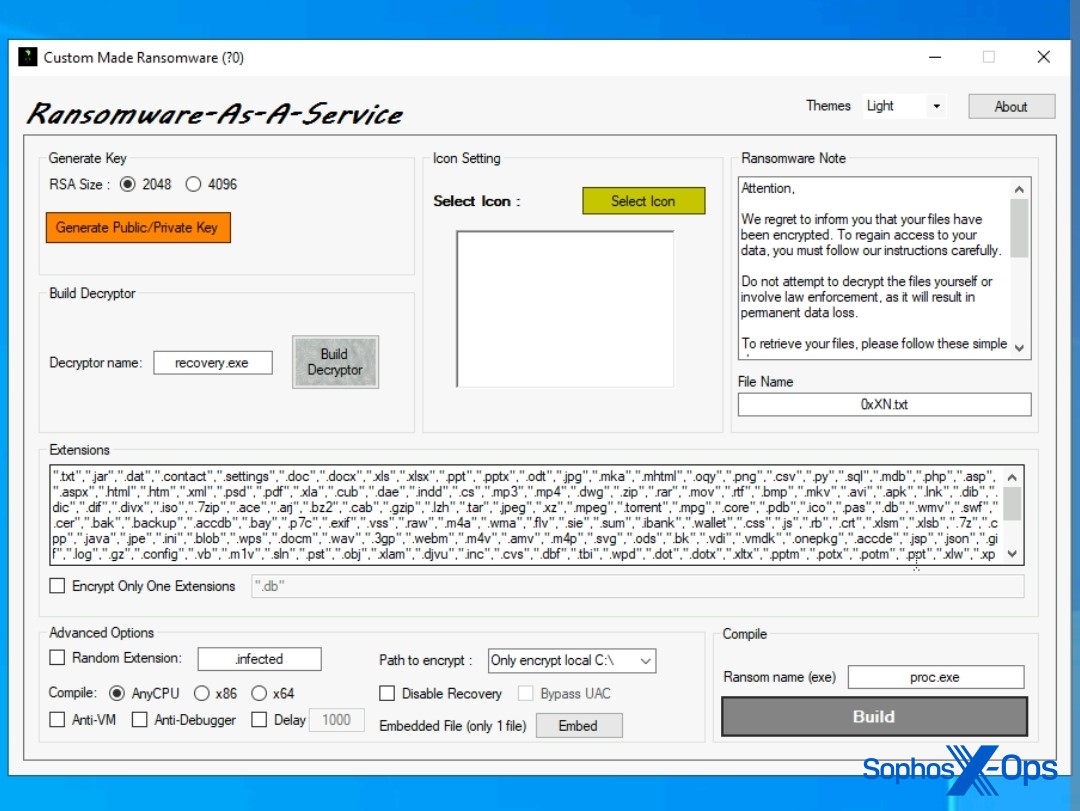
Figure 10: A screenshot of an unnamed junk-gun ransomware, posted to a forum as part of a listing. Despite the window title of “Ransomware-As-A-Service”, we didn’t observe any indication of any common RaaS-type revenue models or features with this product, and it was offered at a standalone price of $200
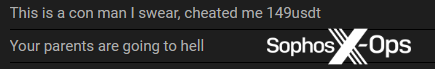
Figure 11: A user alleges that this ransomware is a scam and that they were defrauded to the tune of $149 USDT (Tether)
However, even affiliates of prominent ransomware families, operating under common RaaS models, run the risk of being scammed by RaaS operators. Standalone junk-gun ransomware may therefore be the lesser of two evils in the minds of some less-experienced threat actors, as it can provide them with more independence and control.
Languages
12 of the 19 adverts included details about the development language and/or framework, either in the initial post or in subsequent discussions. Interestingly, .NET/C# was the most popular (five variants), with C++ accounting for three, two in C, and Python and Go one each.
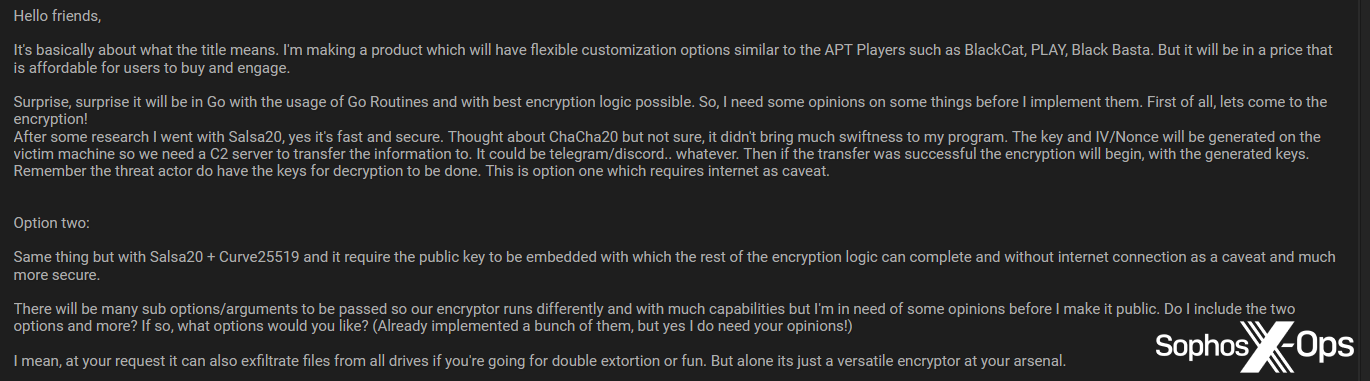
Figure 12: A user solicits development advice for an ongoing ransomware project written in Go. Note the aspiration to make the ransomware “similar to the APT Players such as BlackCat, PLAY, Black Basta”
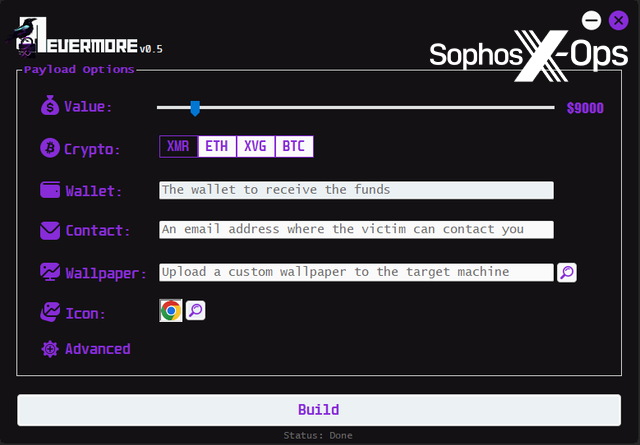
Figure 13: Most junk-gun ransomware we observed, however, appeared to have been written in C#/.NET
This would seem to be at odds with ‘traditional’ malware and ransomware (often written in C or C++), and more modern strains (several ransomware families, including BlackCat and Hive, shifted to Rust and Go). It’s not entirely surprising, however; C# and .NET tend to have a shallower learning curve than many programming languages and frameworks, and may therefore be more attractive to less experienced developers.
Perhaps in keeping with this, virtually all the junk-gun ransomware we saw – with the exception of Evil Extractor – lacked the slick graphics and branding associated with more prominent ransomware. In the majority of cases, logos and interfaces were crude and amateurish (and some varieties were deliberately unbranded and unnamed, and so had no logos at all).

Figure 14: The Lolicrypt logo
Features
The advertised capabilities of junk-gun ransomware varied widely. We observed a range of cited encryption methods, although AES-256 and/or RSA-2048 were, unsurprisingly given their ubiquity, the most popular, appearing in seven of the ten listings in which threat actors provided this detail. However, we also saw some relatively rare algorithms, including Chacha20, XTEA, and Salsa20.
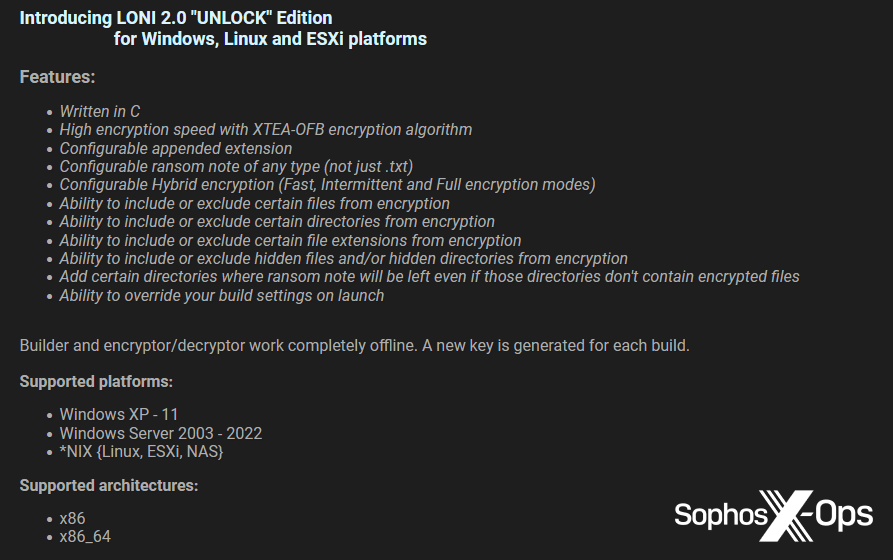
Figure 15: A promotional post for Loni, referring to the use of the XTEA cipher. Loni was notable for the amount of technical information provided about its features
Four varieties (Evil Extractor; CatLogs; Nevermore; and RansomTuga) bundled other capabilities, such as infostealing and/or keylogging, along with ransomware functionality. With regards to ransomware-related features, only three varieties referred to deletion of volume shadow copies (a well-known ransomware tactic), which was somewhat surprising – although six mentioned multi-threaded encryption (another very common tactic, which increases the speed of encryption).
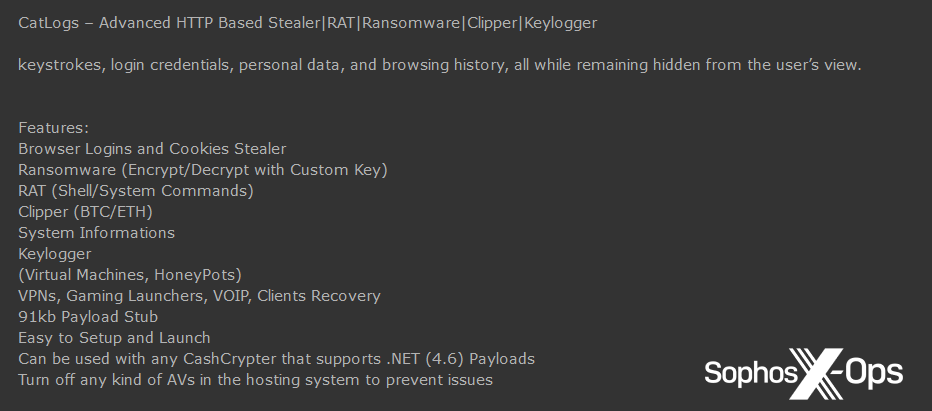
Figure 16: A post advertising the CatLogs junk-gun ransomware, which bundles multiple other features
Only one variety, Kryptina, was described as specifically targeting Linux operating systems, although both the Lolicrypt and Loni developers stated that they had introduced cross-platform capabilities or Linux-specific variants.
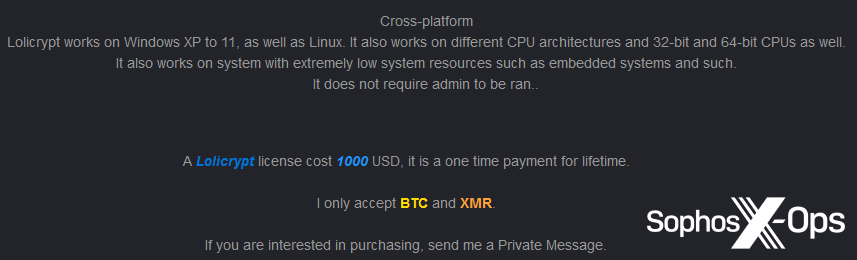
Figure 17: The Lolicrypt developer claims that their ransomware has cross-platform capabilities
Going against the grain, only Loni claimed to have remote encryption capabilities. This perhaps illustrates how low-quality and crude most junk-gun ransomware is, being limited to local encryption, whereas many major ransomware families are capable of remote encryption.
Just two adverts (an unnamed variety, and Evil Extractor) mentioned any kind of anti-VM or anti-debugger features.

Figure 18: A feature list for an unnamed junk-gun ransomware includes references to “Anti Virtual Machine” and “Anti Debugger” capabilities
We did note that some junk-gun ransomware developers appear to have ambitions to eventually evolve their projects into more complex offerings. The Loni developer, for example, argued that their ransomware is superior to RaaS schemes because there’s no need to profit-share, pay affiliate joining fees, or run the risk of RaaS operators interfering with negotiations and payments.
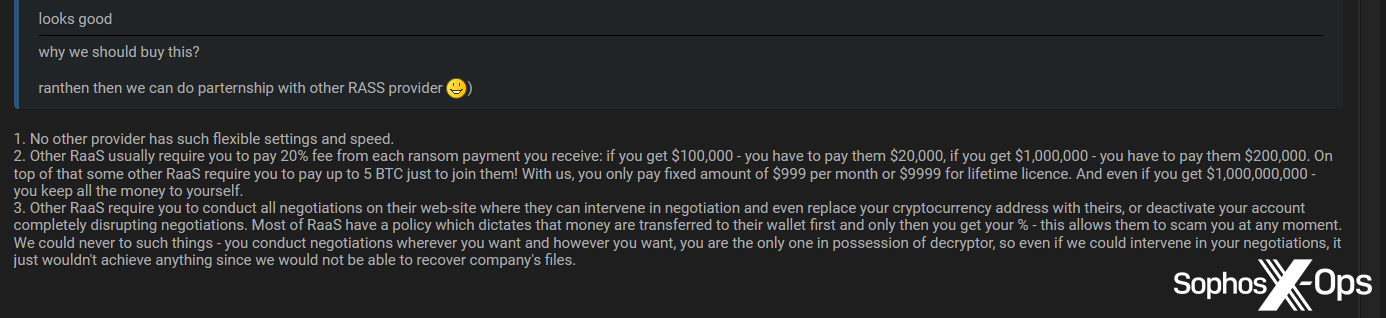
Figure 19: The Loni developer makes an argument for their product versus RaaS schemes. Note the reference to RaaS operators scamming affiliates, which we alluded to earlier
However, the developer later mentioned that when they have collected enough funds, they will “scale up infrastructure and launch a data leak site” – thereby creating a sort of hybrid of a conventional RaaS infrastructure and junk-gun ransomware.
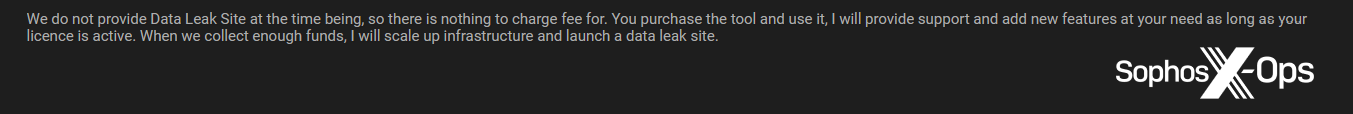
Figure 20: The Loni developer reveals ambitions to later launch a data leak site, as well as promising buyers “support and…new features”
We also saw an advert which appeared to mimic some of the ‘affiliate rules’ stipulated by prominent ransomware families. In one post, for an unnamed junk-gun ransomware, the developer listed “forbidden targets”, including hospitals and governments. However, this advert appeared to be for standalone ransomware, so it’s unclear how these rules would be enforced.

Figure 21: A junk-gun ransomware advert specifies “forbidden targets”
In the wild?
It’s difficult to assess the extent to which most junk-gun ransomware has been used in real-world attacks. One of its major selling points is that little or no supporting infrastructure is required, and this includes leak sites – so there is no central source of information for researchers and investigators to monitor. Moreover, if buyers are targeting small businesses and individuals, such incidents are unlikely to be publicized to the same extent as those involving higher-profile organizations.
Threat actors are also unlikely to discuss attacks on ‘public’ forums, particularly if they were directly involved in those attacks. And it’s difficult to obtain technical information, such as hashes and other IOCs, without either purchasing the ransomware or investigating known incidents – so it’s hard to determine if we’ve seen any of these varieties before, under different names or identities.
However, we do know that threat actors have used Evil Extractor – to our knowledge, the only example that has received any in-depth coverage – in real-world attacks. We also observed claims – two from sellers, one from a buyer – that three variants (Ergon, Loni, and Lolicrypt) have been used in the wild, but we were unable to obtain any further information.
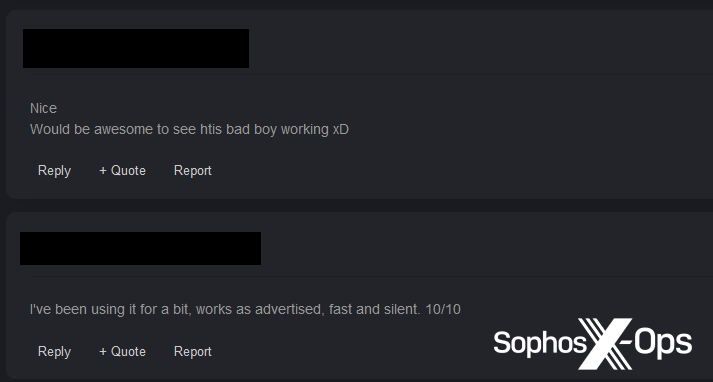
Figure 22: A Lolicrypt buyer claims that they have “been using it for a bit, works as advertised”
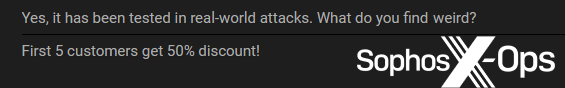
Figure 23: The Loni developer states that Loni “has been tested in real-world attacks”
Detections
When threat actors advertise malware on criminal forums, they often include detection rates from online scanners, either in the form of a number or a screenshot. While these results are almost always related to static, rather than dynamic, detections, the criminal community often regards them as something of a quality benchmark. Threat actors may use a zero-detection rate (popularly known as ‘FUD’: ‘fully undetected’ or ‘fully undetectable’), for example, as a selling point, even if that figure doesn’t necessarily mean much in the context of real-world attacks.
Six of the 19 adverts referred to some form of detection – three mentioning Windows Defender specifically (either in the context of detections or bypasses), and three referring to detections by multiple security products in online scanners.
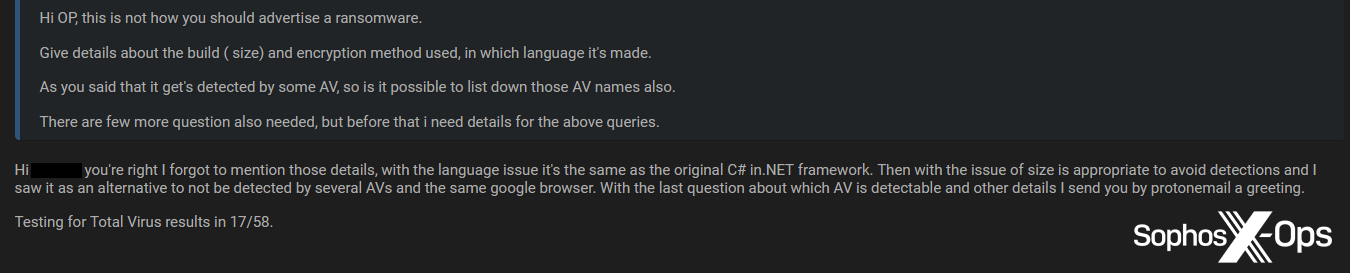
Figure 24: The Yasmha developer responds to criticism of their initial advert by including details about the language and detection rate
However, as we noted earlier, even a relatively high detection rate isn’t necessarily a dealbreaker when it comes to junk-gun ransomware. Small businesses and individuals may not always have security products, or may not have configured them correctly, or may not adopt best practice when an alert is triggered – and many threat actors know this.

Figure 25: A user claims to be targeting “5-6 companies with no IT security at all”
Known ransomware and RaaS schemes
In addition to relatively unknown junk-gun ransomware, we also found better-known ransomware on the forums, albeit all relatively new or lower-tier families. We grouped these examples into three categories: builders or source code for sale or distribution; recruitment opportunities; and requests for assistance with development.
| Name | Date posted | Type | Price |
| Insane | January 2024 | Development request / affiliate recruitment | N/A |
| DJVU | January 2024 | Builder for sale | Unknown |
| Zeppelin | January 2024 | Source code | Unknown |
| Endurance | November 2023 | Affiliate recruitment / builder for sale | $850 |
| Chaos | June 2023 | Builder for sale | Unknown |
| Qilin | September 2023 | Affiliate recruitment | N/A |
| qBit | September 2023 | Builder for sale / development request | Unknown, released for free December 2023 |
| Black Snake | June 2023 | Affiliate recruitment | N/A |
| Hakuna Matata | July 2023 | Builder for sale/distribution | Unknown |
| LMAO | June 2023 | Builder for sale/distribution | Unknown |
| Unknown | July 2023 | Affiliate recruitment | N/A |
Table 2: Known ransomware on the four criminal forums we investigated
Note that we include ‘yasmha’ in the junk-gun ransomware section, rather than this one, because the poster explicitly stated that it is a variant of Yashma ransomware (the spelling mistake appears to be deliberate, or at least consistent across multiple posts). Conversely, the threat actors offering builders and source code for DJVU (a variant of STOP), Zeppelin, Endurance, Chaos (the predecessor to Yashma), qBit, Hakuna Matata, and LMAO (a variant of Chaos) did not state that their products are novel, customized variants.
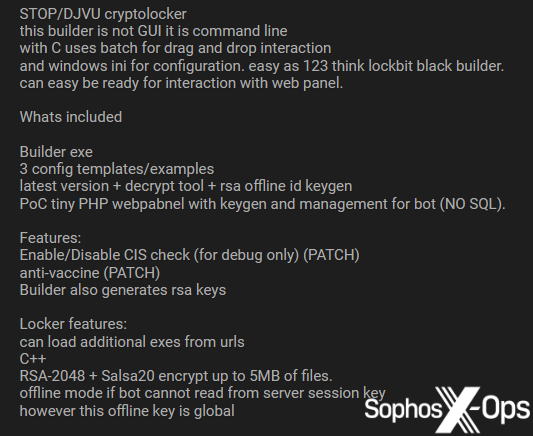
Figure 26: An advert for DJVU ransomware on a criminal forum
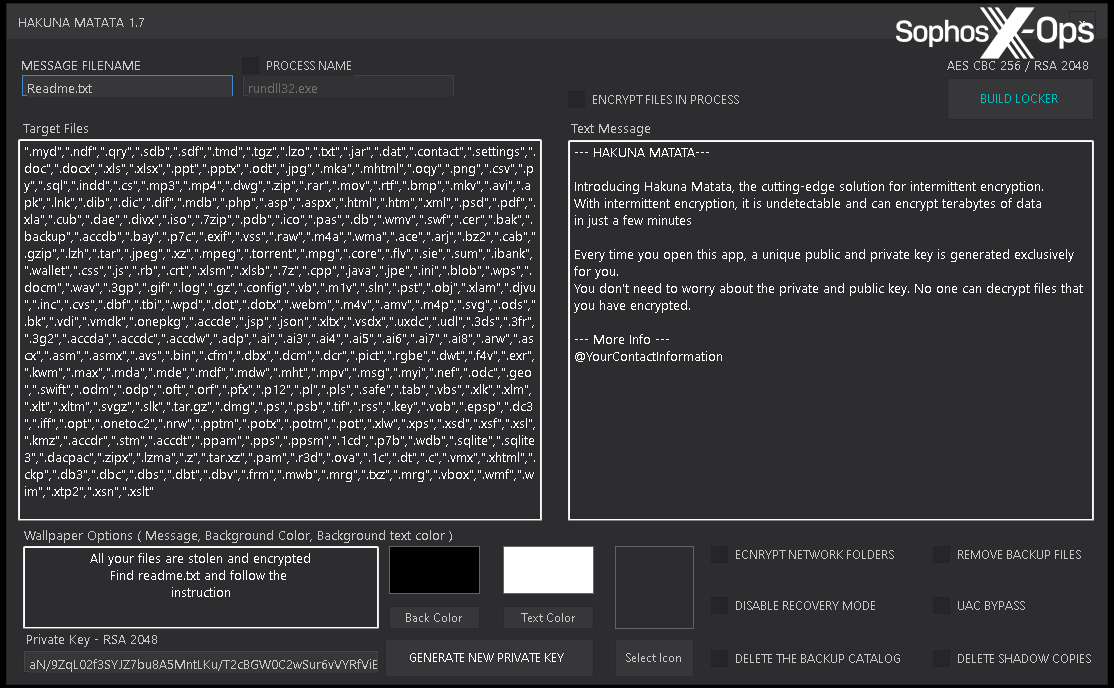
Figure 27: A screenshot of the Hakuna Matata ransomware builder, which was offered for sale/distribution on a forum
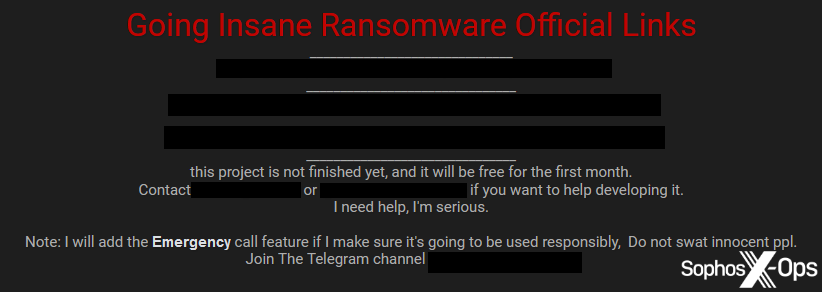
Figure 28: A promotional post for Insane ransomware, including a request for development assistance
Figure 29: Insane’s leak site, with a notably garish old-school aesthetic
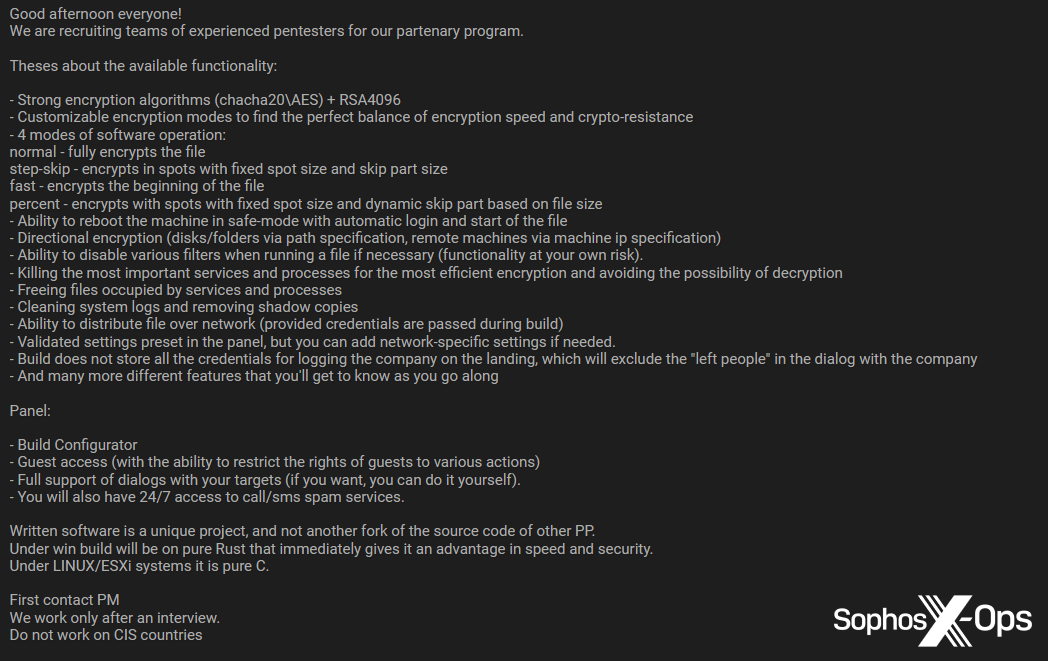
Figure 30: A recruitment advert by the Qilin ransomware gang. Note the use of the term “pentesters”, which threat actors often use as a euphemism for affiliates and/or IABs on criminal forums
Finally, we also observed a recruitment campaign by an as-yet-unknown ransomware family, TrapTight.
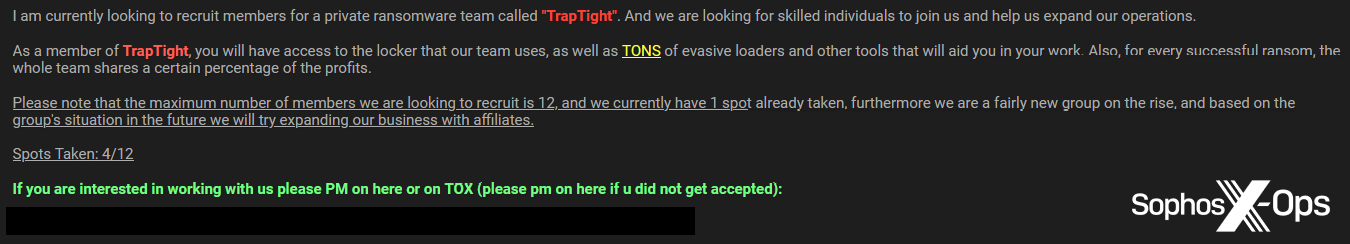
Figure 31: A recruitment campaign by a new ‘start-up’ ransomware family, TrapTight
And another by an unnamed ransomware gang:
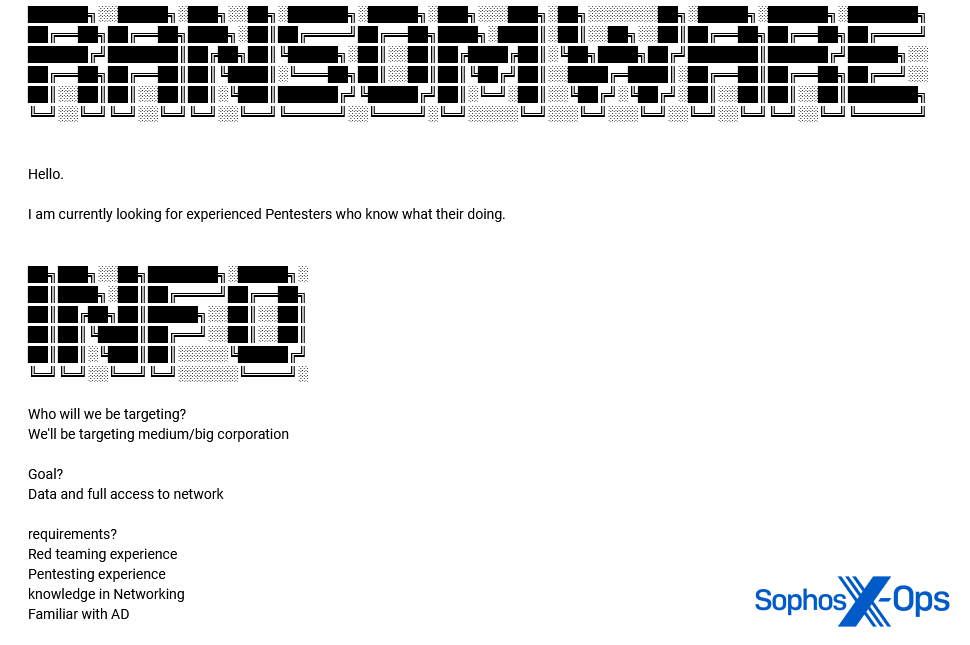
Figure 32: An unnamed ransomware family seeks “pentesters” to target “medium/big corporation” [sic]
Threat actors on lower-tier criminal forums therefore seem to have a few options when it comes to getting involved in ransomware. The cheapest, most common, and most straightforward route appears to be the ‘self-starter’ approach: purchasing junk-gun ransomware for a one-off price, and deploying it as they see fit. Alternatively, threat actors could purchase a builder for a better-known ransomware variant – something that has been tried and tested already in real-world attacks.
On the other hand, if a threat actor is looking to develop ransomware themselves, or to join an affiliate scheme, but is not skilled or experienced enough to apply to the big leagues, they can seek employment with known secondary ransomware families, possibly as a precursor to joining better-known schemes. Or, if that’s too much of a stretch, they could apply to join a brand-new family like TrapTight.
Intentions, tutorials, and targets
While it’s often difficult to ascertain if threat actors have used junk-gun ransomware in the wild, it is clear that some have ambitions to do so. For instance, one individual claimed to have bought the Nevermore builder, and was looking to “ransom any computer/server with important files either owned by companies or individuals.” The threat actor went on to say that they were considering looking on Shodan – a search engine which indexes service banners, allowing users to find specified kinds of devices and services – to identify vulnerable RDP and SSH servers, an approach similar to that an IAB might take.
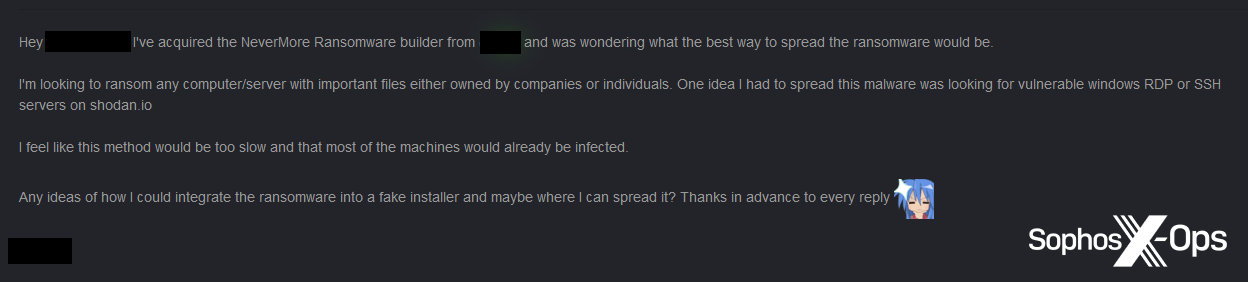
Figure 33: A user seeks to spread the Nevermore ransomware
This interest in target selection is something we saw elsewhere, too; one user sought advice on how to identify “a suitable target…I’ve considered highschools [sic] / universities” and asked for tips on “possible targets, in terms of possible gain, lack of backups, chance of foothold.”
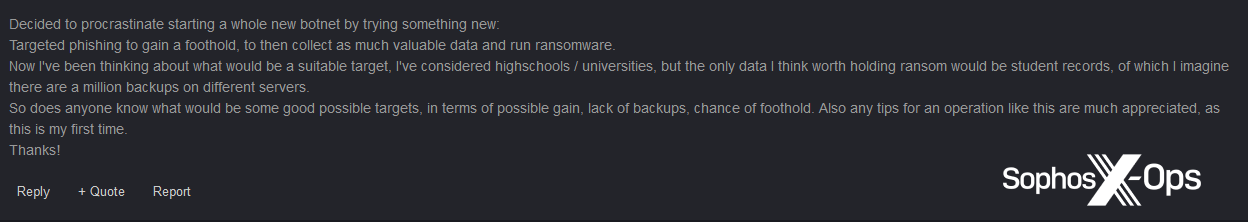
Figure 34: A forum user asks for tips on identifying targets
Another user said that they had already compromised a network, but had “never deployed a ransomware [sic] before” and asked other forum users for advice or a “tutorial.”
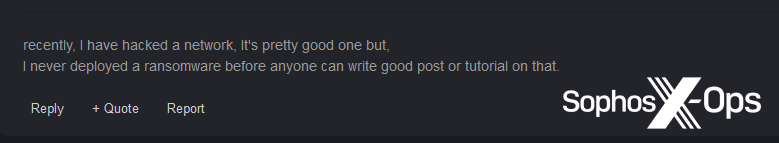
Figure 35: After compromising a network, a user confesses that they don’t know how to deploy ransomware
A user on another forum had a similar issue:
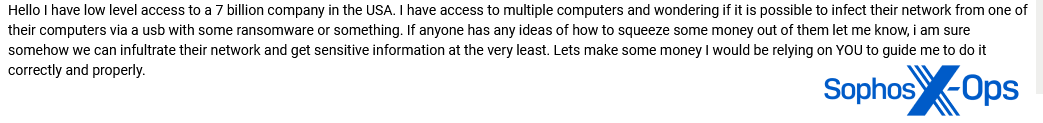
Figure 36: A user claims to have access to a company, but asks for assistance on distributing ransomware
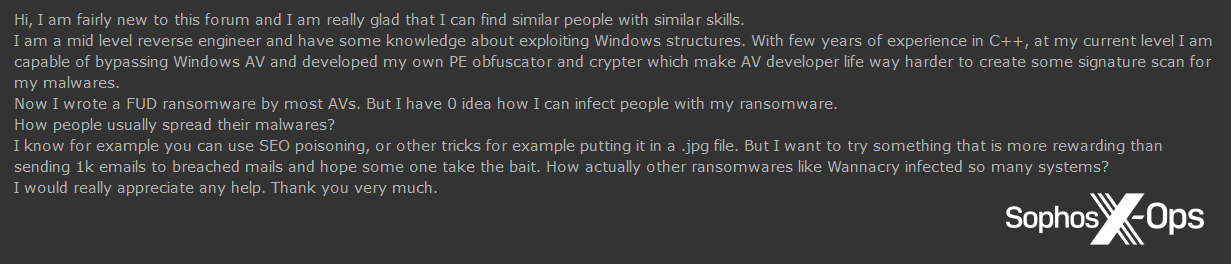
Figure 37: A user (who claims to be relatively knowledgeable) asks for help on how to “infect people with my ransomware”
On the subject of guidance, we observed multiple users requesting and sharing copies of so-called “ransomware manuals”, including guides written by Bassterlord, a prominent ransomware operator and IAB, and the “Conti manuals”, leaked in 2021. Evidently, such users are seeking to learn from, and emulate, prominent ransomware actors.
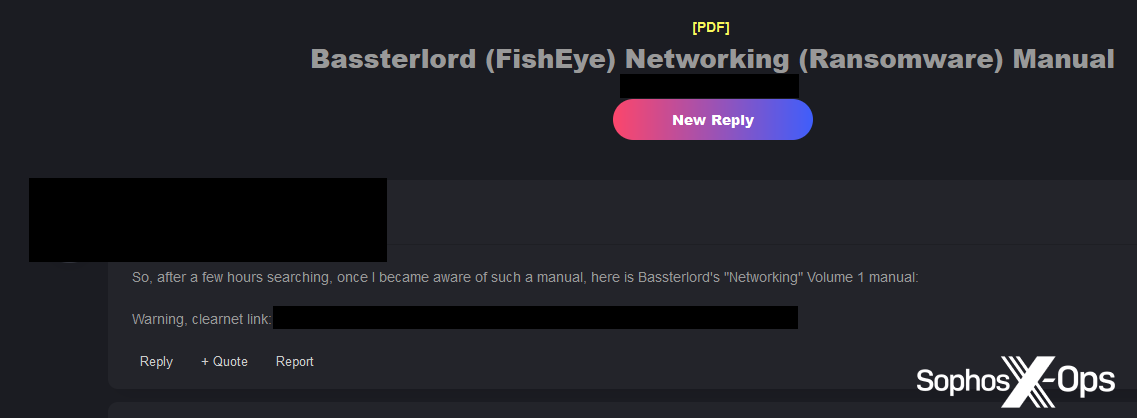
Figure 38: A user shares a copy of one of Bassterlord’s manuals
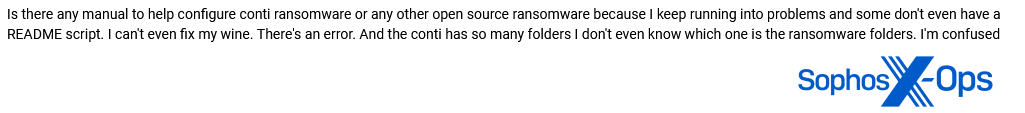
Figure 39: A user confesses to being “confused” about how to configure ransomware and asks for a manual
In other cases, users created and shared their own guides:
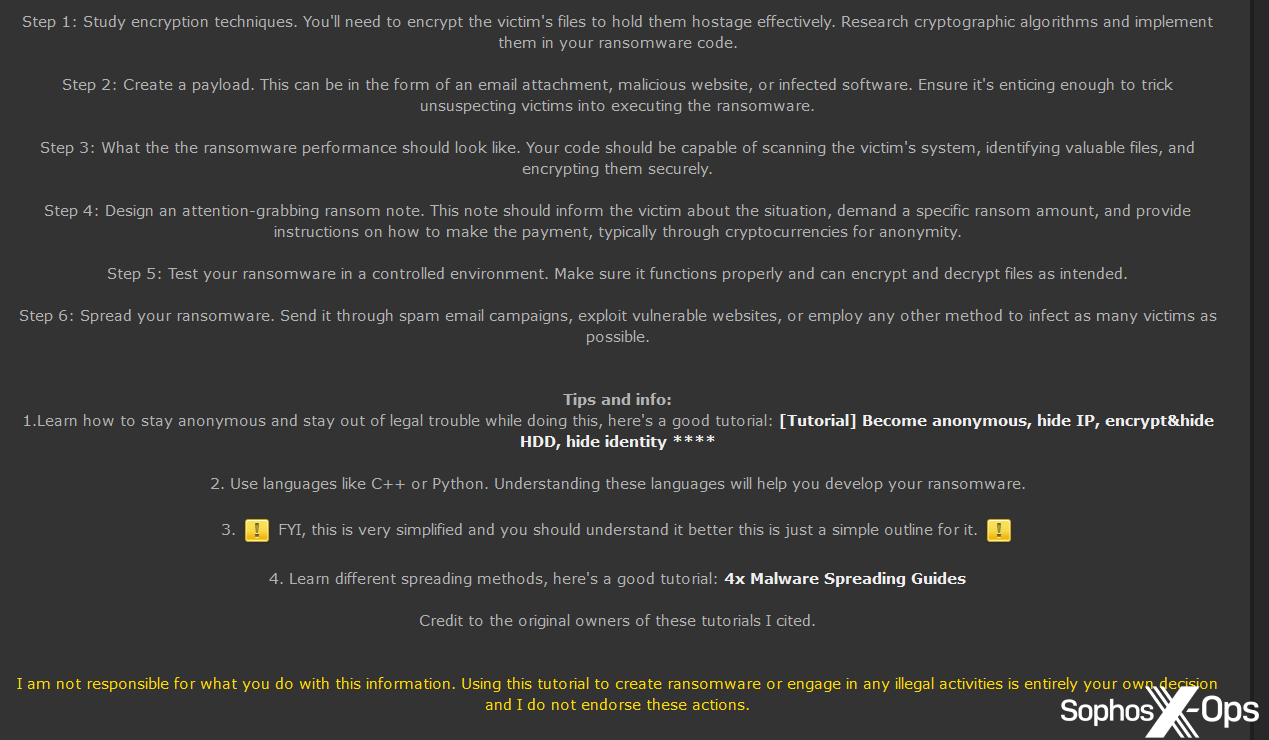
Figure 40: A user shares their own guide on developing and spreading ransomware
Some users explicitly advocated targeting small businesses and individuals, and sought tips on how to contact them after ransomware deployment; how much money to ask for and in what cryptocurrency; and how to launder the proceeds.
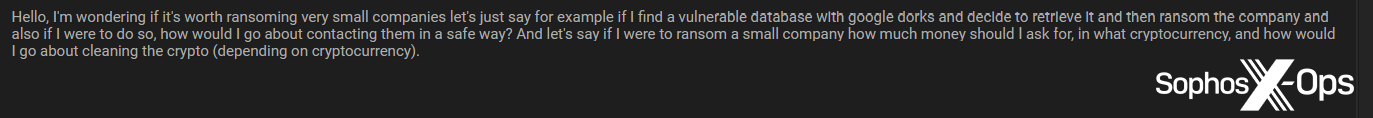
Figure 41: A user seeks advice on how to target small businesses
Another user, in response to a peer contending that “normal computer users” would not pay ransoms, argued: “I believe it is reverse [sic]…big techs wont [sic] pay…but some normies do.”
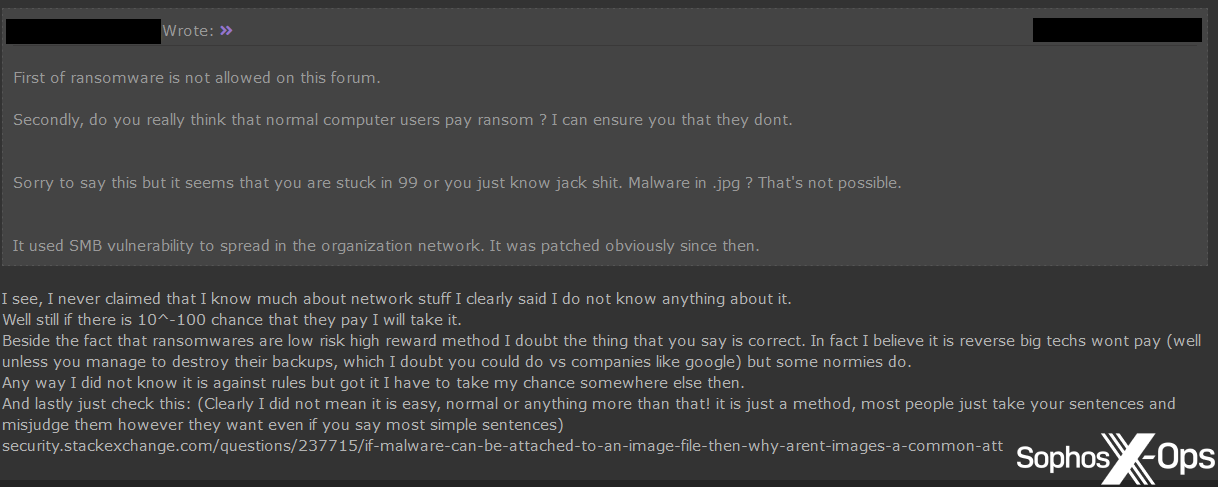
Figure 42: As part of a spirited debate on a criminal forum, a user argues that “big techs wont [sic] pay…but some normies do”
One ransomware developer took a more aggressive approach. In their advert, they noted that “there is no decryption key…once payment is made block the person.” They go on to say that this ransomware is “designed…to target specific people such as Scammers, Low Life’s [sic], etc…”
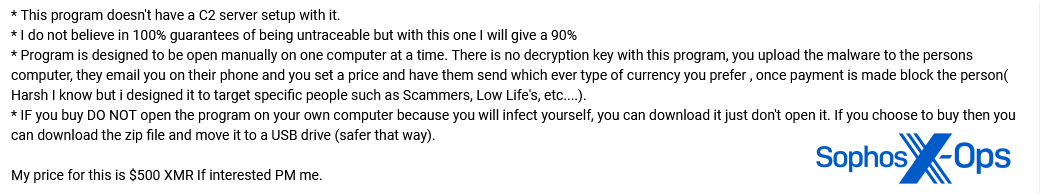
Figure 43: A junk-gun ransomware developer notes that their product includes no possibility of decryption – in other words, victims can pay, but will not be able to recover their files
In another particularly interesting post, the developer behind Nevermore suggested an alternative approach to orthodox infection strategies: physical access. They advocated putting ransomware on a USB stick; obtaining access to a device (“it could be that annoying neighbor or someone that you work for”); turning off any security products; and then executing the ransomware. “As long as you avoid witnesses and cameras”, the threat actor went on to say, “there is no [sic] much evidence to be used against you.”
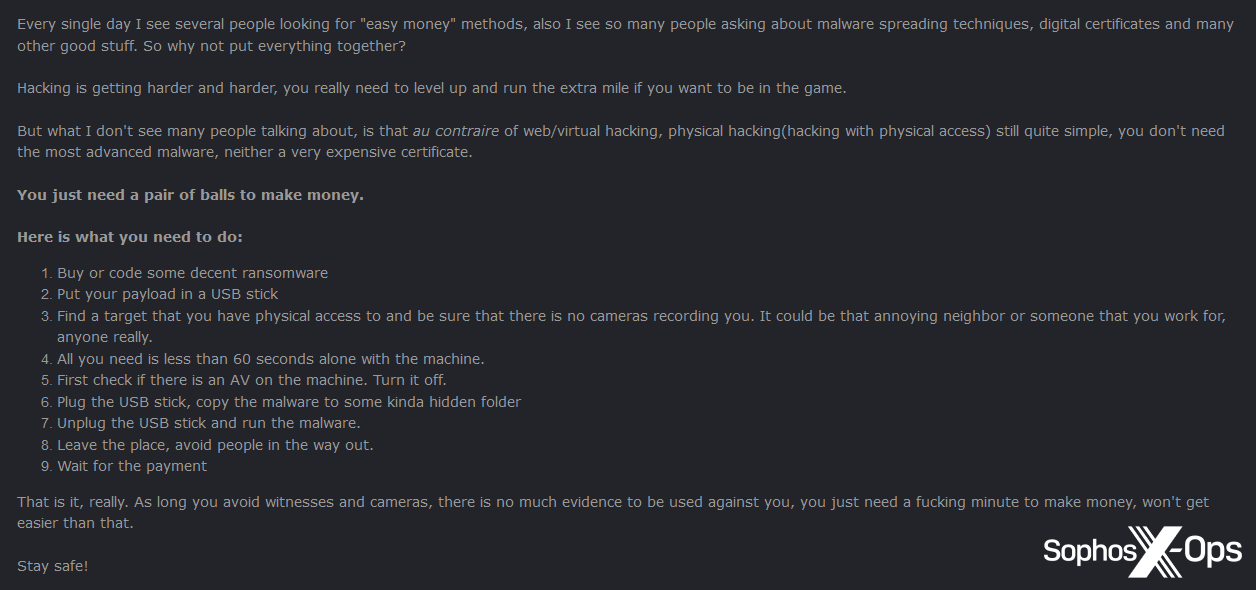
Figure 44: The Nevermore developer suggests combining physical access with ransomware for “easy money”
A user commented that this approach “would be valid only on small corps, [too risky] to try it on any medium sized company”, and suggested combining this tactic with social engineering to gain access to premises.
The Nevermore developer agreed, adding that “you would be surprised with [sic] the number of people that leave their laptop/pc alone and unlocked and go to the bathroom.”
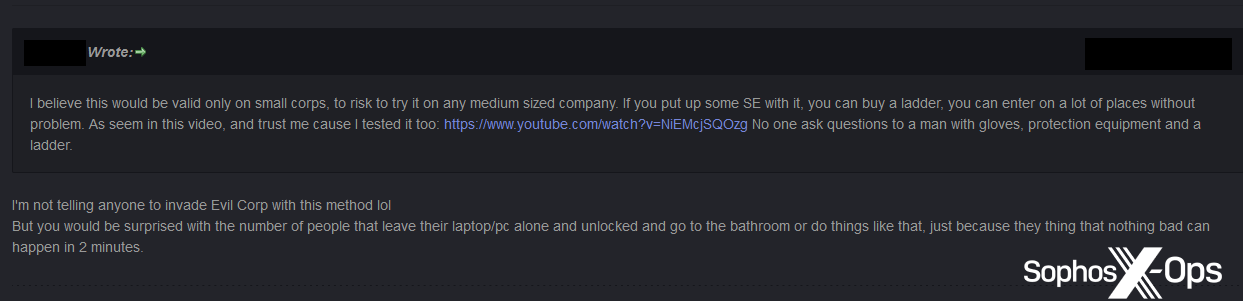
Figure 45: Forum users discuss possible approaches for ‘physical access ransomware’
Aspirations
While the forums we investigated for this research are frequented by lower-tier threat actors, we observed an interesting nuance. Below the buyers and sellers of junk-gun ransomware, there is an even lower tier – those who are still not yet at the stage of developing their own ransomware, but aspire to do so.
We noted several instances of users soliciting tips on which languages to use, or people who had begun coding ransomware projects but, as in one of the examples below, were “confused about what to do next.”
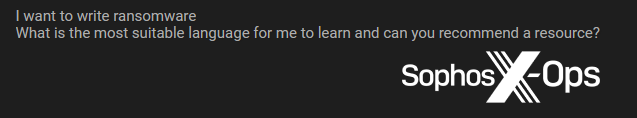
Figure 46: A user seeks advice on “the most suitable language” for developing ransomware
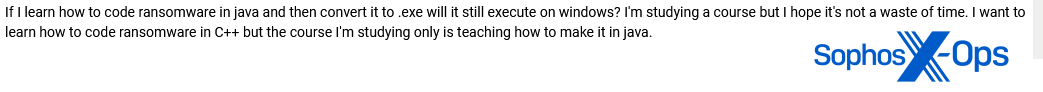
Figure 47: A user wonders if writing ransomware in Java is worthwhile
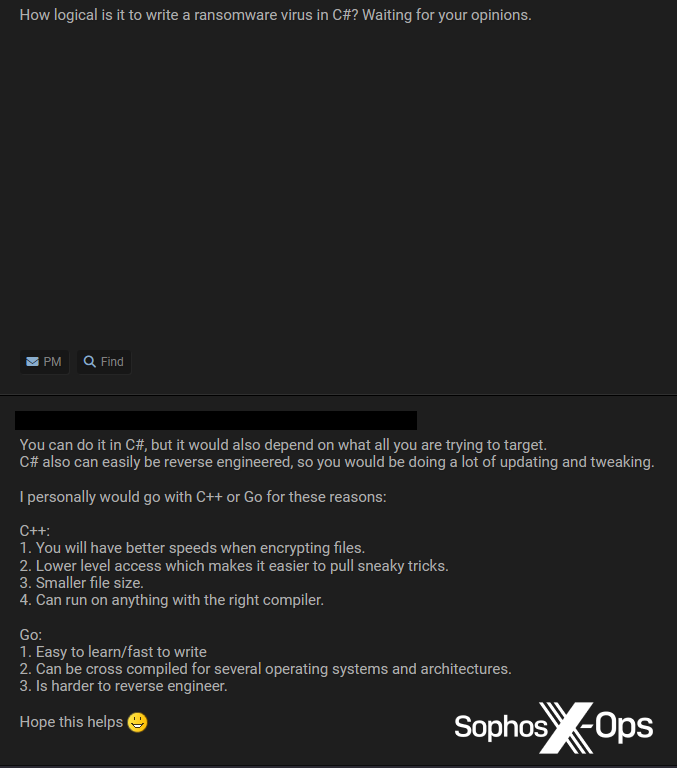
Figure 48: Users debate the relative merits of writing ransomware in C#. Interestingly, we also observed some users advising others to use Python, although the reception to that suggestion was mixed
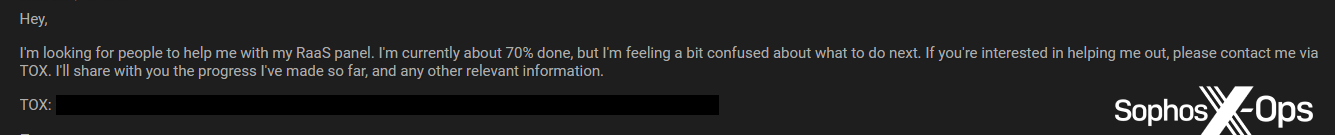
Figure 49: A user asks for help with developing their “RaaS panel”
In a few instances we also saw users who had an idea for different projects, but weren’t sure if they were feasible.
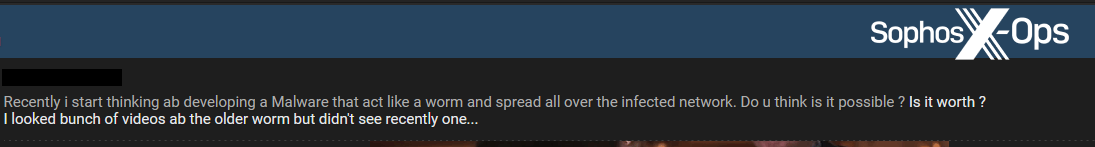
Figure 50: A user solicits opinions on worm-based ransomware
In other cases, users who had presumably overcome these hurdles to create working code were still at a loss as to the next stage. These users asked for advice on how to licence their malware, how much to sell it for – and even how to sell it in the first place.
Figure 51: A user asks for help in understanding how malware licencing works. One response, interestingly, draws parallels with prominent tech firms
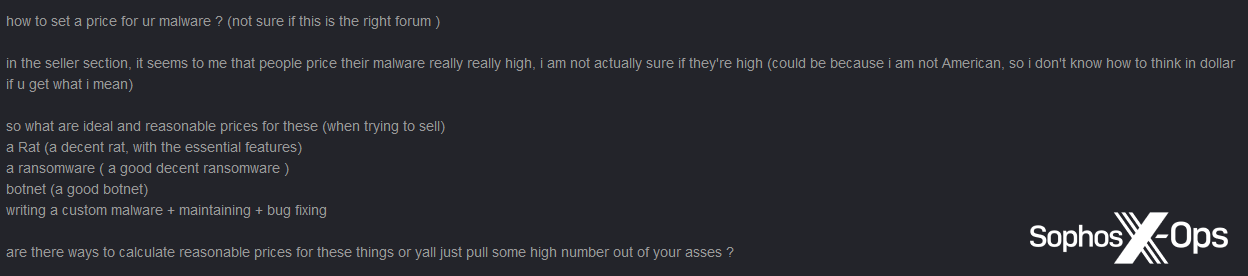
Figure 52: A user wonders “how to set a price for…malware”
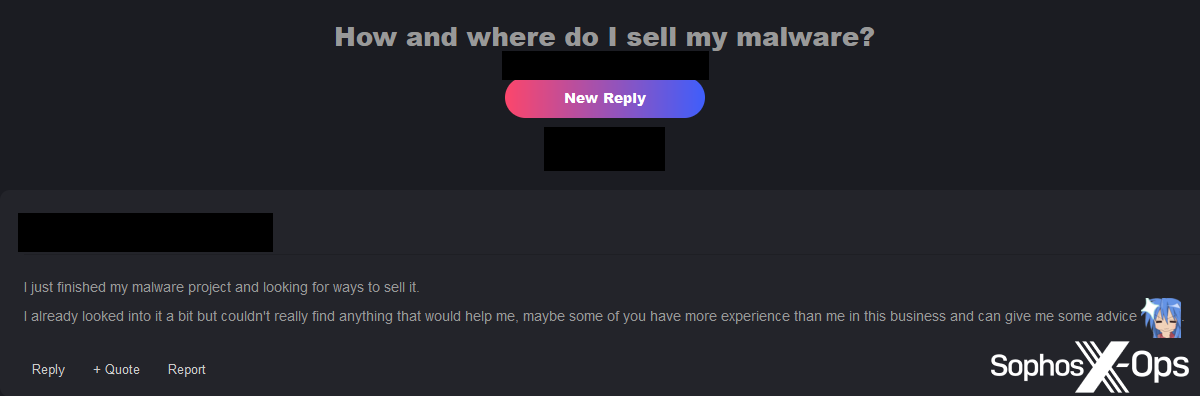
Figure 53: This user was confused about how to start selling their malware, let alone set a price or figure out a licencing model
Tracking tiers
While it’s no surprise that there are ‘script kiddies’ on criminal forums, this sub-tier of would-be ransomware actors is still noteworthy. On higher-profile, Russian-language cybercrime forums – those frequented by prominent and prolific IABs, malware developers, and ransomware affiliates – the questions shown above would be at best ignored, and at worst ridiculed. (And might, of course, fall foul of the ban on commercial ransomware posts on some major forums following the 2021 Colonial Pipeline attack – although many users have circumvented the ban, and the extent to which it is observed and enforced appears to vary).
But on the forums we’ve discussed here, users are less apprehensive about revealing their ignorance, because those sites cater almost exclusively to less-skilled threat actors. There’s a tacit understanding that these are not gatherings of the elite, or even of professionals, but are instead intended for individuals who aspire to develop their abilities, to the point where they can acquire a piece of the pie for themselves.
While much criminal marketplace research focuses, not unreasonably, on higher-tier Russian-language sites (a topic for another article, but Russian – specifically fenya – is arguably the prestige language in the cybercrime underground), there’s also a benefit to monitoring lower-tier, English-language forums. Sites like this may well produce the next generation of threat actors. The relatively low-quality ideas and projects featured on them now could evolve into more sophisticated threats over time, as threat actors’ capabilities and confidence grow.
There’s also an argument that lower-tier English-language forums may serve as the first step of a career development path for some threat actors. The graphic below illustrates the tiers we observed in our investigation, and how a threat actor might advance through them. Users begin by asking basic questions, and trying to code rudimentary ransomware and malware themselves. They may then graduate to buying junk-gun ransomware, or developing, sharing, and selling it – perhaps, as we saw with Loni, with ambitions to eventually turn their projects into more complex schemes.
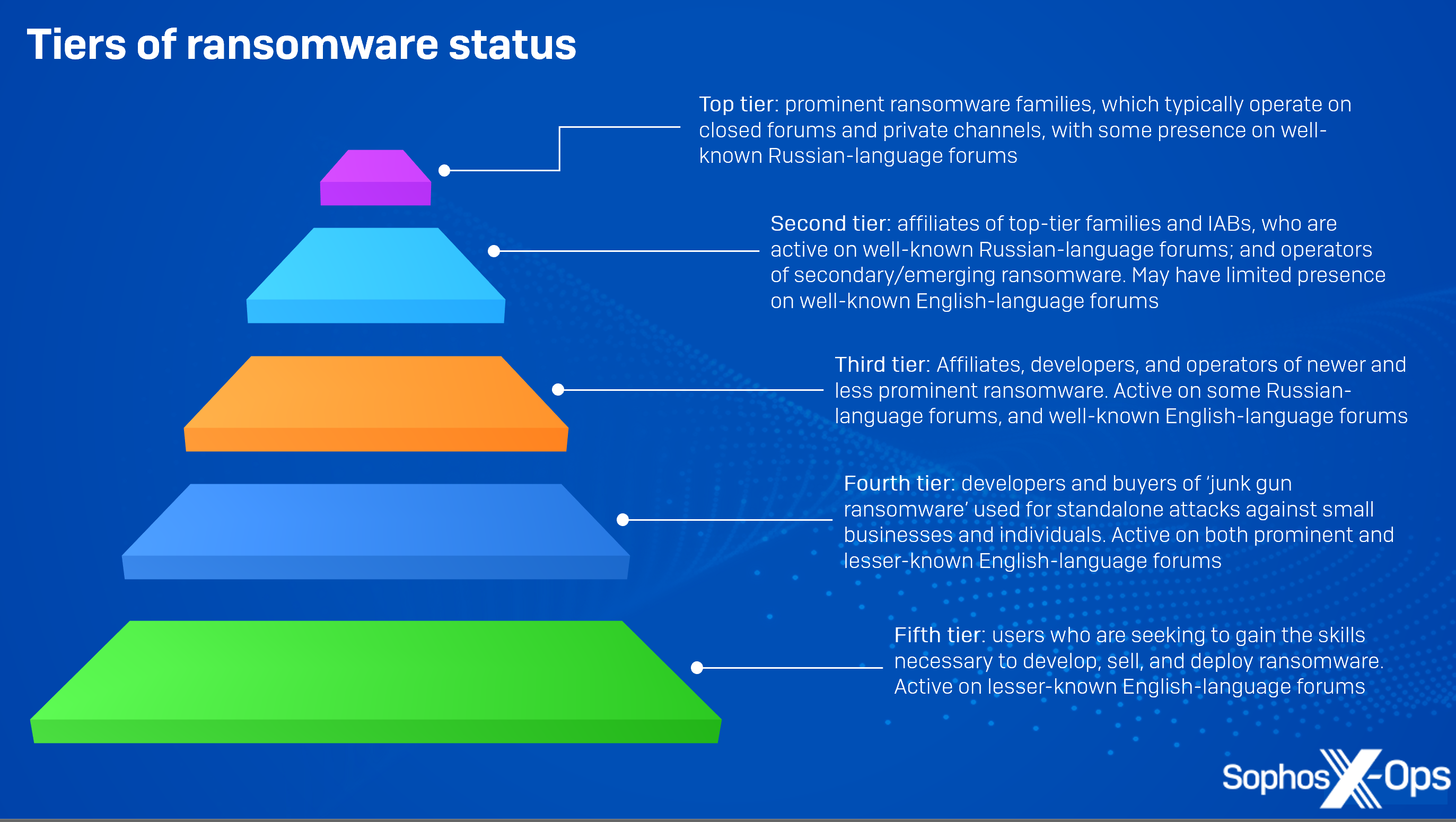
Figure 54: An illustration of the various tiers of capability, ambition, and potential career development for ransomware actors
Above that tier are recruitment and development opportunities with emerging and secondary ransomware families – which have organized RaaS schemes; tried-and-tested malware; pre-existing infrastructure; and a proven track record of real-world attacks. And then, at the apex, are the prominent, household-name ransomware groups – the tier to which threat actors can aspire once they’ve paid their dues, gained experience, and made a name for themselves.
It’s therefore important to view junk-gun ransomware not just as an interesting phenomenon in and of itself, but as a component of the wider ransomware ecosystem, and as a potential route to bigger and better opportunities for its creators, buyers, and users. As such, it’s worthwhile tracking junk-gun ransomware and the individuals involved with it. Not only do they pose a threat to small businesses and individuals now, but as time goes on, at least some of them will likely become increasingly capable of inflicting damage on a larger scale.
Conclusion
Because junk-gun ransomware seems to be a nascent development, we’ll be keeping an eye on it. It may signal a move towards a further fracturing of the ransomware market, and perhaps even impending market saturation. Or it may be that ransomware continues to shift into several distinct tiers: high-profile groups target high-profile organizations, while the ‘scraps’ – small businesses and individuals – are left for lower-tier threat actors. Those lower-tier actors, who are currently making and selling junk-gun ransomware, may in time ‘move up the ranks’ and be recruited as developers or affiliates by larger, more professional outfits.
To some extent, junk-gun ransomware is likely also simply a reflection of capitalism in action. Like any other market, supply will expand to meet demand, and would-be profiteers will flock to whatever services and products are generating the most money – and carve out niches for themselves as they do so. While we focused on ransomware for this research, it’s likely the same story for infostealers, RATs, and cryptominers: lower-quality products and actors at the bottom of the pile, hoping to eventually filter through to the top.
What is clear, however, is that junk-gun ransomware poses unique challenges to small businesses, the wider public, and the security community. We observed threat actors explicitly referring to attacks against smaller companies and individuals – even as they tried to determine which types of company to target, and how much ransom to demand – because such targets are typically less well-defended, less informed, and less prepared.
Meanwhile, junk-gun ransomware presents the security industry with several problems. It’s difficult to obtain samples of junk-gun ransomware; to determine the extent to which it has been used in the wild; and to track new variants. Threat actors will also sometimes adopt the ‘brand names’ of known ransomware families, possibly to exploit their reputations – something which can cause confusion amongst researchers. Crucially, there’s also less threat intelligence about junk-gun ransomware, because the forums on which it proliferates are not always heavily monitored by researchers – resulting in an intelligence gap. Of course, both businesses and security researchers must devote time and resources to tracking numerous threats, some higher priority than others, and which vary according to risk profiles, sectors, geography, and other factors – so there’s a balance to be struck.
However, tracking junk-gun ransomware, and those who are, at least currently, on the periphery of the ransomware ecosystem, can provide valuable insights into both individual threats, and potential future trends in the wider threat landscape. Monitoring specific ransomware variants can help to protect small businesses and individuals now, while tracking sellers, buyers, and capabilities can provide insight into the development of threats and threat actors over time.
https://news.sophos.com/en-us/2024/04/17/junk-gun-ransomware-peashooters-can-still-pack-a-punch