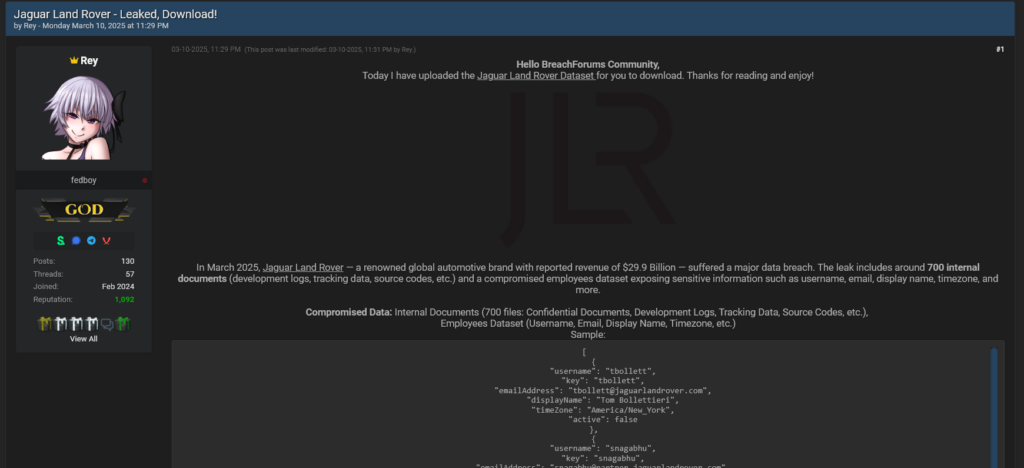
In a significant data breach, the HELLCAT ransomware group has leaked gigabytes of sensitive data from Jaguar Land Rover (JLR), exploiting compromised Jira credentials harvested from infected employees. This attack highlights the ongoing threat of infostealer malware and its capability to enable long-term exploitation of credentials. Affected: Jaguar Land Rover, LG Electronics, infostealer malware victims
Keypoints :
- HELLCAT ransomware group claimed responsibility for a data breach at Jaguar Land Rover (JLR).
- The breach involved the leakage of sensitive data, including proprietary documents and employee information.
- Attackers exploited compromised Jira credentials from an individual at LG Electronics.
- Rey, a known threat actor, used infostealer malware to harvest credentials.
- A second actor known as “APTS” later claimed to have accessed JLR’s systems using older credentials from 2021.
- The leak reveals the ongoing threat posed by infostealer malware and its ability to retain the utility of compromised credentials over years.
- The breach highlights the need for better credential management and security practices by organizations.
MITRE Techniques :
- Credential Dumping (T1003) – The threat actors harvested Jira credentials from compromised employees using infostealer malware.
- Exploitation of Remote Services (T1210) – Compromised credentials were used to gain unauthorized access to JLR’s systems.
- Command and Control (T1071) – Used to manage the bots and exfiltrate data from compromised systems.
Indicator of Compromise :
- [Email Address] on@lge.com