Threat Actor: Unknown | Unknown
Victim: Italian Red Cross | Italian Red Cross
Price: Not specified
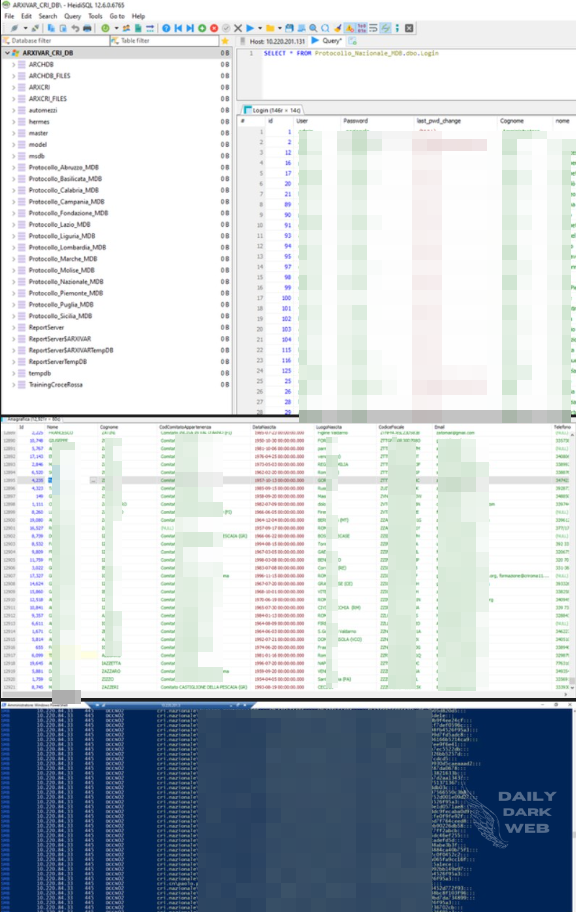
Exfiltrated Data Type: Internal source codes, databases, backups, and more
Additional Information:
- The breach into the Italian Red Cross network was executed by an unknown threat actor.
- The threat actor gained access to the network using a simple PHP shell and became the administrator of the company’s Active Directory.
- The breach did not involve sophisticated techniques and took advantage of vulnerable machines accessed from outside.
- The ‘master’ password, ‘Sviluppo.1864’ or ‘Sviluppo.1864!’, was widely used across local and network accounts.
- The breach occurred during the company’s nighttime activity, making it easier to execute without detection.
- A large amount of internal and non-internal videos, totaling 13TB, were discovered but excluded from the data dump.
- The breach resulted in access to internal source codes, databases, backups, and more.
- Ransomware was deliberately avoided by the threat actor.
- The threat actor encouraged others to mirror the data and hinted at a hidden backdoor for future access upon request.
Recently, there was claims a breach into the Italian Red Cross network, where the threat actor managed to infiltrate despite the presence of EDR/XDR technology, particularly Trend Micro Apex One, which proved ineffective in detecting or blocking the breach. With just a simple PHP shell, the threat actor gained access to the network and easily became the administrator of the company’s Active Directory.
Surprisingly, the breach did not involve sophisticated techniques like kerberoast or s4u, and the machines accessed from outside were vulnerable to various known exploits, facilitating Local Privilege Escalation (LPE). The threat actor discovered that the ‘master’ password, ‘Sviluppo.1864′ or ‘Sviluppo.1864!’, was widely used across local and network accounts.
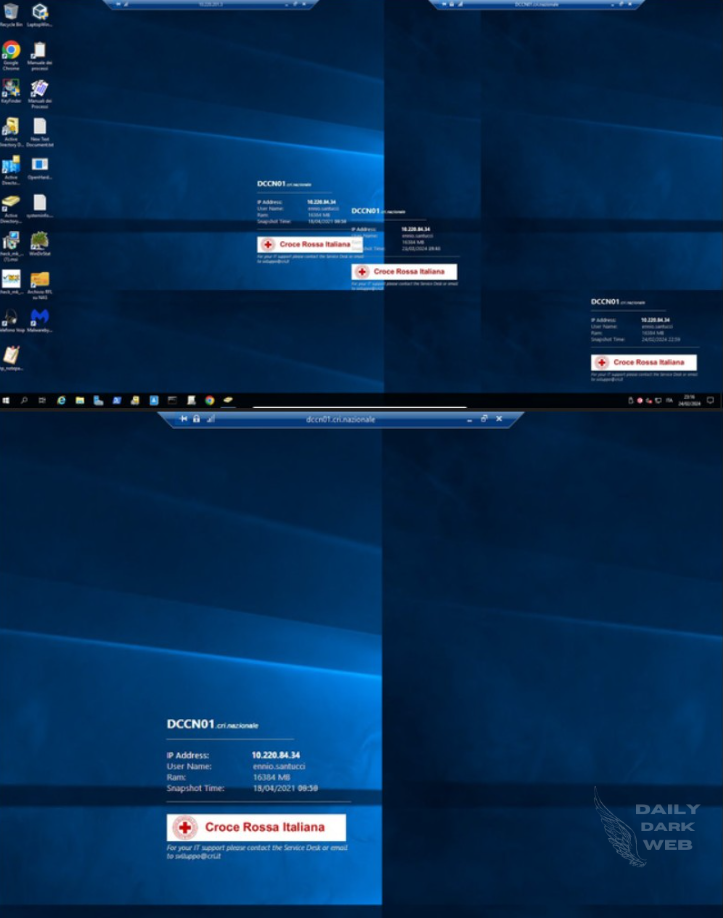
Taking advantage of the company’s nighttime activity, as the EDR system sent alerts/events to the internal JIRA system, the breach was executed without much difficulty. The only hiccup occurred when the threat acto rstumbled upon 13TB of internal and non-internal videos, which were excluded from the data dump to avoid causing disruptions.
The breach yielded access to internal source codes, databases, backups, and more, but ransomware was deliberately avoided as the threat actor considered it unnecessary and amateurish. As a parting note, the threat actor encouraged others to mirror the data, citing issues with DMCA and Gofile’s policies. Additionally, a hidden backdoor for future access was hinted at, available upon request via private message.