THE CONNECTIONS TO THE RUSSIA-UKRAINE WARFARE
In 2021, Anonymous declared a cyber war against Russia after the Ukraine invasion, with similar tactics seen in the Israel-Hamas conflict. Main attacks:
- Denial of Service Attacks: These attacks flood websites with excessive traffic, rendering them unavailable to legitimate users for extended periods.
- Propaganda and Misinformation: Perpetrators can easily use social media, often with the help of sophisticated bot networks, to spread false information, influence opinions, and damage reputations. This tactic is accessible to individuals with minimal technical knowledge.
- Cyber Espionage: State actors and cybercriminals may infiltrate networks to monitor communications, access valuable trade secrets and employ social engineering tactics.
- Hacking: Concerts revolve around personal information exposure, potentially leading to harassment, more cyberattacks, and an elevated risk of phishing and malware distribution.
- Defacing: Hackers often vandalize websites to convey political messages, usually using SQL injections to manipulate site content, but these attacks typically do not result in data theft.
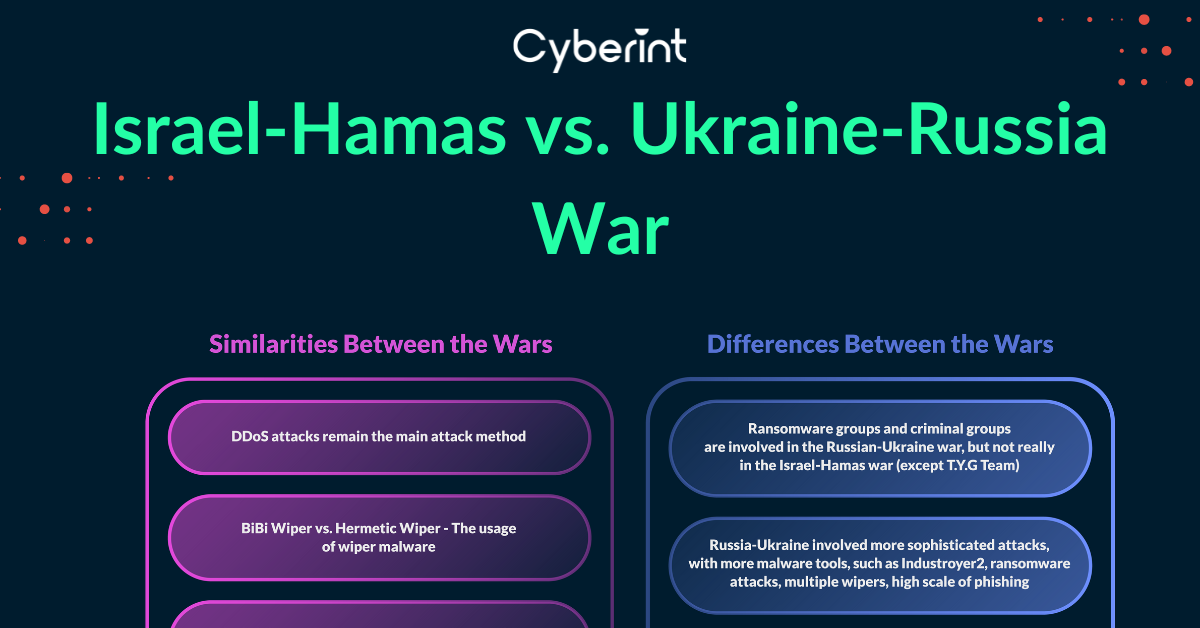
We saw the involvement of Russian and Ukrainians threat actors in the war of Israel Hamas, focusing on Hacktivists mostly from the Hamas and its supporters side, and a bit state sponsored groups. The biggest difference between the wars in the cyber field, is the involvement of other group types, such as crime syndicate groups (Ransomware), and other criminals.
Global Involvement The Russia-Ukraine war has drawn more global attention and involvement due to its impact on European security and international relations. The Israel-Hamas conflict, while receiving international attention, is more regionally focused.
HERMETICWIPER VS. BIBI WIPER AND OTHER MALWARE
Destructive malware has seen extensive use by Russian threat groups, particularly following Russia’s invasion of Ukraine in February 2022, with notable wiper malware such as DoubleZero, HermeticWiper, IsaacWiper, WhisperKill, WhisperGate, CaddyWiper, and AcidRain being employed.
HermeticWiper, a newly identified destructive malware variant, is designed to infiltrate Windows devices and incapacitate them by destroying files, corrupting the Master Boot Record (MBR), and affecting physical drives of Ukrainian organizations. Notably, HermeticWiper shares similarities with WhisperGate, a previous wiper-style threat utilized in cyberattacks against Ukraine. Moreover, HermeticWiper is associated with PartyTicket, a decoy ransomware often deployed alongside wiper threats.
HOW DO THESE THREATS DIFFER?
Unlike BIBI WIPER, HermeticWiper does not establish communication with remote Command & Control (C2) servers for data exfiltration, employ reversible encryption algorithms, or use ransom notes to coerce victims into making payments. Instead, it causes harm by overwriting files with useless data, impacting both the data and the operating system.
The code base of HermeticWiper indicates a deep understanding of volume formats and their handling, despite differences in code quality. Both campaigns, however, have had a devastating impact on all systems where they were executed.
Additionally, HermeticWiper incorporates a decoy ransomware, PartyTicket, as part of its strategy.
INDUSTROYER2
In April 2022, researchers identified Industroyer2, a malware specifically crafted to target industrial control systems within Ukraine’s energy grid. It marked an advancement of the same malware that disrupted Kyiv’s power grid in 2016, albeit for a brief period. As of now, this stands as the sole publicly disclosed instance of malware potentially designed to induce a physical impact in Ukraine (it’s important to note that many potentially impactful cyber incidents remain undisclosed due to their classified nature).
Incident responders successfully neutralized the Industroyer2 malware before its pre-programmed timer could activate. This incident underscores the potential of cyber operations to inflict physical damage, but it also highlights their limitations, as the impact was thwarted before any harm could occur, negating potentially years of malware development.
ACTIVITY VOLUME: RUSSIA-UKRAINE VS. ISRAEL-HAMAS
The cyber attacks conducted by Russia and Ukraine involved a greater volume of activities, especially from the Russian side, including increased usage of malware, phishing, and disruptions to communication and internet infrastructure compared to the cyber warfare between Hamas and Israel.
Moreover, throughout this period, Russian state actors and affiliated threat actors persistently tried to compromise Ukrainian communication, transportation, energy, defense, administrative, and diplomatic systems and services. Additionally, Russia’s Federal Security Service (FSB) groups have been engaged in cyberattacks and intelligence activities targeting Ukraine.
On March 9 alone, the Quad9 malware-blocking recursive resolver intercepted and mitigated 4.6 million attacks against computers and phones in Ukraine and Poland, surpassing the European average by more than ten times. Cybersecurity experts observed a notable increase in phishing and malware attacks against Ukrainians through the blocked DNS queries originating from Ukraine. They also highlighted that the Polish numbers were elevated due to the presence of 70%, or 1.4 million, Ukrainian refugees in Poland at that time.
SOCIAL MEDIA & OPEN SOURCES
Before the outbreak of hostilities, Russia made numerous efforts to create a pretext for war. These efforts included multiple information operations on platforms like Telegram and Twitter, attempting to portray Ukraine as the aggressor while framing Russia as acting in self-defense. Across both traditional and social media, Ukraine and the US faced accusations of clandestinely developing biological weapons in undisclosed laboratories—a narrative recycled from the 1980s and previously used during Russia’s invasion of Georgia in 2008.
Additionally, videos depicting alleged Ukrainian sabotage of Russian targets and supposed shelling of a kindergarten by Ukraine emerged online just days before Russia’s invasion. However, these attempts to influence public perception were swiftly debunked by the Open Source Intelligence community through forensic analyses of the material. The US intelligence community also proactively countered Russian narratives in an effort to preemptively debunk them.
On the other hand, Since the Hamas attack on Israel on October 7, and even more so since the start of the Israeli strikes on Gaza, social networks have been accused of siding either with the Palestinians or, more often, with Israel. There have been accusations of “censorship” or, at the very least, unequal treatment. As early as October 10, Elon Musk, the chairman of X (formerly Twitter), posted a meme on his personal account mocking the “mainstream media,” which, he claimed, simultaneously accused his platform of being “an anti-Semitic cesspool” and “a Zionist propaganda machine.”
Source: https://cyberint.com/blog/research/israel-hamas-vs-ukraine-russia-war/
Views: 0