The article discusses the InvisibleFerret malware, associated with North Korean threat actors, exploiting fake job interviews to distribute itself. This malware targets sensitive files, source code, and user data in technological, financial, and cryptocurrency sectors, demonstrating high levels of sophistication and stealth. Affected: technological sector, financial sector, cryptocurrency sector
Keypoints :
- North Korean activity observed using fake job interviews to spread malware.
- InvisibleFerret is part of a coordinated attack involving multiple malware families.
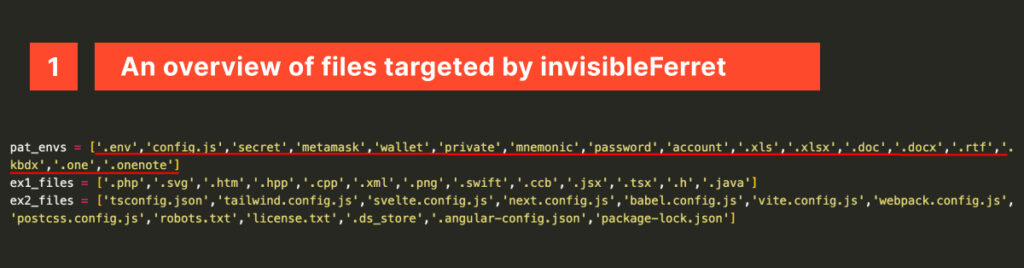
- Targets developers and steals sensitive data, wallets, and source code.
- Infiltrates systems via disguised coding challenges or video call software.
- Utilizes staged malware distribution through BeaverTail, a loader written in obfuscated JavaScript.
- Operates silently without generating logs, complicating detection.
- Exfiltrates data using unconventional methods while disguising legitimate traffic.
- Employs Python-based malware with numerous functions and complex architecture.
- Targets browser data, extensions, and password managers for exfiltration.
- Utilizes Telegram for data transfer, revealing sensitive bot tokens.
- Features a keylogger to capture user inputs and clipboard contents.
- Malware aims to run commands and download subsequent malware stages.
- Indicators of compromise (IOCs) include specific IPs, URLs, and file hashes.
MITRE Techniques :
- T1016 – System Network Configuration Discovery: Queries ip-api.com for victim geolocation.
- T1571 – Application Layer Protocol: Uses unusual ports for C2 servers (port 1244 and 1245).
- T1041 – Exfiltration Over Command and Control Channel: Leverages FTP for data exfiltration.
- T1071.001 – Application Layer Protocol: Sends data to Telegram using its Bot API.
- T1086 – PowerShell: Executes various commands to run and manage malware.
- T1113 – Screen Capture: Monitors clipboard and keystrokes with pyHook on Windows.
Indicator of Compromise :
- [SHA256] 47830f7007b4317dc8ce1b16f3ae79f9f7e964db456c34e00473fba94bb713eb
- [SHA256] 6a104f07ab6c5711b6bc8bf6ff956ab8cd597a388002a966e980c5ec9678b5b0
- [Filename] p.zip
- [IPV4] 147[.]124[.]214[.]129
- [URL] http://147[.]124[.]214[.]129:1244
Full Story: https://any.run/cybersecurity-blog/invisibleferret-malware-analysis
Views: 16

 简体中文
简体中文 Nederlands
Nederlands Français
Français Bahasa Indonesia
Bahasa Indonesia 日本語
日本語 Português
Português