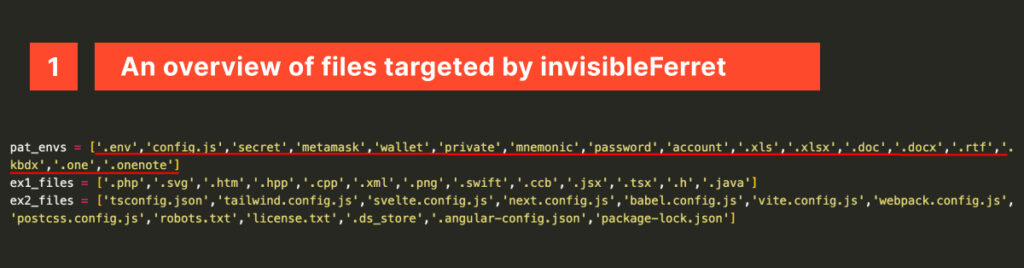
The article discusses the emergence of InvisibleFerret malware, which is being spread through fake job interviews targeting developers in the tech and cryptocurrency sectors. This malware is part of a broader campaign that includes other malware like BeaverTail. InvisibleFerret is designed to steal sensitive information and operates silently, making it difficult to detect. Affected: InvisibleFerret, BeaverTail
Keypoints :
- North Korean threat actors are using fake job interviews to distribute malware.
- InvisibleFerret is a Python-based malware that targets sensitive files and source code.
- BeaverTail acts as a loader for InvisibleFerret, downloading it as part of its operation.
- The malware employs various techniques to exfiltrate data from browsers and systems.
- Indicators of compromise (IoCs) were gathered during the analysis of the malware’s behavior.
MITRE Techniques :
- T1016 – System Network Configuration Discovery: The malware queries ip-api.com for geolocation information.
- T1571 – Application Layer Protocol: The malware uses unusual ports for communication with C2 servers.
- T1041 – Exfiltration Over Command and Control Channel: Data is exfiltrated using FTP and other methods.
- T1071 – Application Layer Protocol: The malware uses legitimate services for data exfiltration.
- T1056 – Input Capture: The malware captures keystrokes and clipboard data using pyHook.
Indicator of Compromise :
- [file name] p.zip
- [file hash] SHA256:47830f7007b4317dc8ce1b16f3ae79f9f7e964db456c34e00473fba94bb713eb
- [file hash] SHA256:6a104f07ab6c5711b6bc8bf6ff956ab8cd597a388002a966e980c5ec9678b5b0
- [ip address] 147[.]124[.]214[.]129
- [url] http://147[.]124[.]214[.]129:1244
- Check the article for all found IoCs.
Full Research: https://any.run/cybersecurity-blog/cybersecurity-blog/invisibleferret-malware-analysis/
Views: 8