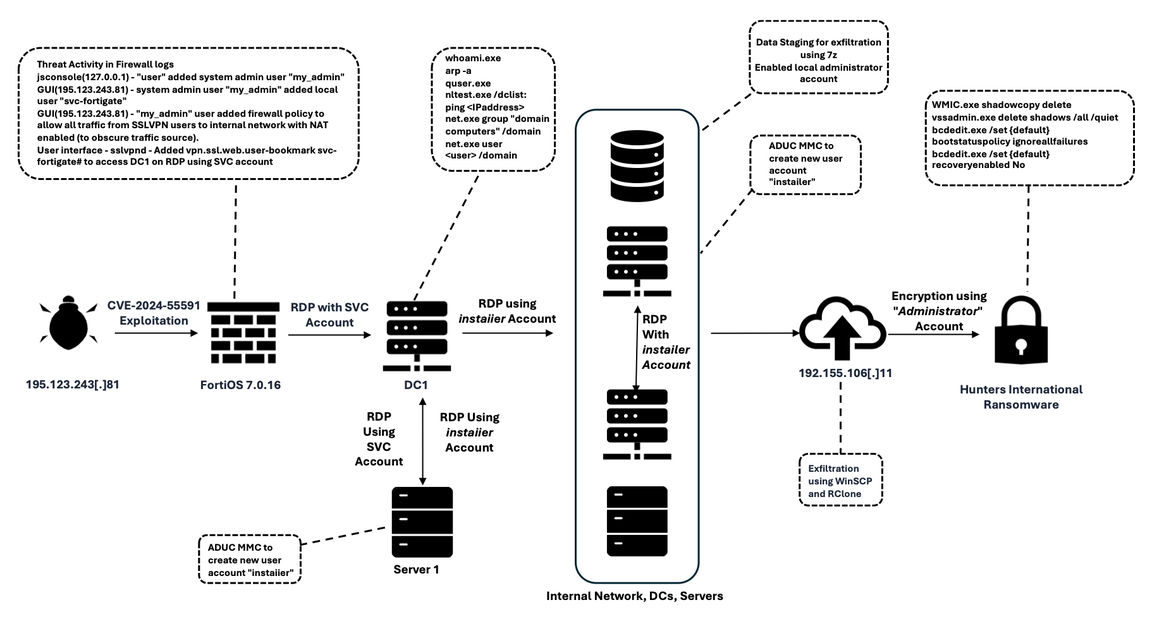
Summary: In February 2025, the eSentire Threat Response Unit (TRU) uncovered a sophisticated ransomware campaign by the Hunters International group against a retail organization, utilizing vulnerabilities in FortiOS for initial access. The attack involved the creation of a super admin account, lateral movement within the network, and the deployment of a new variant of ransomware designed to evade detection and prevent data recovery. This incident highlights the evolving tactics of ransomware groups and their use of advanced methods to maximize impact on their victims.
Affected: Retail organization
Keypoints :
- Initial access achieved by exploiting CVE-2024-55591 in Fortinet devices.
- Attackers created super admin accounts for lateral movement and deceptive user accounts for persistent access.
- Data exfiltration involved Rclone and WinSCP, followed by deployment of a stealthy Rust-based ransomware variant.
- Ransomware employed AES-256 encryption and executed commands to disable recovery options, ensuring data recovery was nearly impossible.
- Victims face a double-extortion threat, as exfiltrated data is posted on a dark web site if ransomware demands are not met.