We have been able to uncover a massive cryptocurrency scam involving more than a thousand websites handled by different affiliates linked to a program called Impulse Project, run by a threat actor named Impulse Team.
Key discoveries
- We have been able to uncover a massive cryptocurrency scam involving more than a thousand websites handled by different affiliates linked to a program called Impulse Project, run by a Russian-speaking threat actor named Impulse Team.
- The campaign has been running since at least 2021, and while there have been individual reports on portions of it, there hasn’t been a summary of the scam in its totality.
- Scammers have even created a copy of a known legitimate anti-scam website to trick unsuspecting users into trusting their fraudulent websites.
Executive summary
Cryptocurrencies have been a source of interest for several years now, attracting not only finance professionals, but also individuals who see an opportunity for “easy” money. Typically, cryptocurrencies such as Bitcoin see significant fluctuations in value over time, making them interesting for potential investors who want to profit from its changing values.
Yet the cryptocurrency industry itself can be difficult to understand even for investors who place large sums of money into cryptocurrency markets. This makes it an interesting sector for malicious actors who see opportunities in the cryptocurrency market, since it is always easier to scam an uninformed victim as opposed to one who knows how the market works. We’ve previously tackled cryptocurrency-related topics in several other blog entries in an effort to raise awareness and help protect users from these types of threats.
This blog entry begins with our investigation into a single website running a common cryptocurrency scam. However, as we dig deeper, we will show that this website was just one in a massive web of related fraudulent websites — making it perhaps one of the largest ever cryptocurrency scam campaigns — run by a Russian-speaking threat actor named “Impulse Team.”
We’ve discovered more than a thousand websites that share the same kind of fraudulent content, all connected through an affiliate program run by the Impulse Team called “Impulse Project.”
This massive campaign has likely resulted in thousands of people being scammed worldwide. The scam works via an advanced fee fraud that involves tricking victims into believing that they’ve won a certain amount of cryptocurrency. However, to get their rewards, the victims would need to pay a small amount to open an account on their website.
Note that all indicators of compromise have been shared with CloudFlare, who have acknowledged receiving it.
The initial investigation
Our investigation started with a private message being spread on Twitter by an account created for the sole purpose of luring people into visiting a specific website: varbytrade[.]com. (The account has since been closed.)
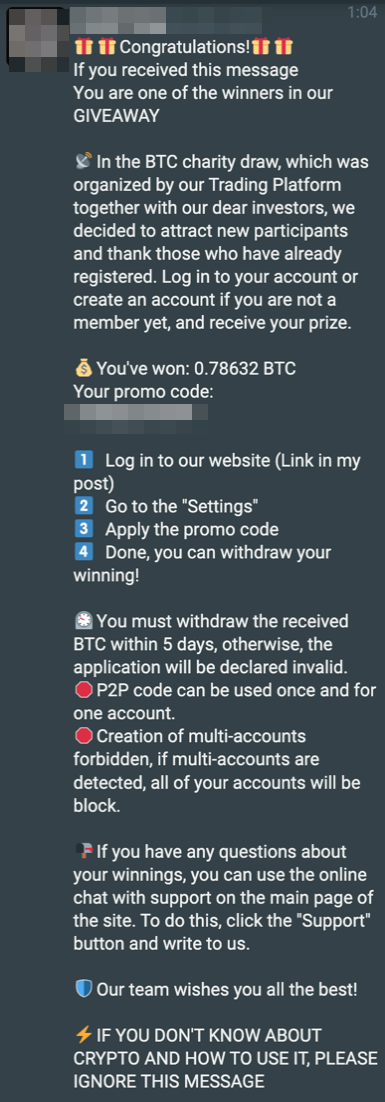
The screenshot in Figure 1 shows the scam perpetrator offering a large cryptocurrency reward amounting to 0.78632 bitcoin (BTC, or roughly US$27,763 at the time of writing), allegedly to attract new participants to the platform.
Once an account is created on the fraudulent platform, the user is requested to activate the account by making a small deposit in BTC, with a minimal amount of 0.01 BTC (approximately US$277 at the time of writing).
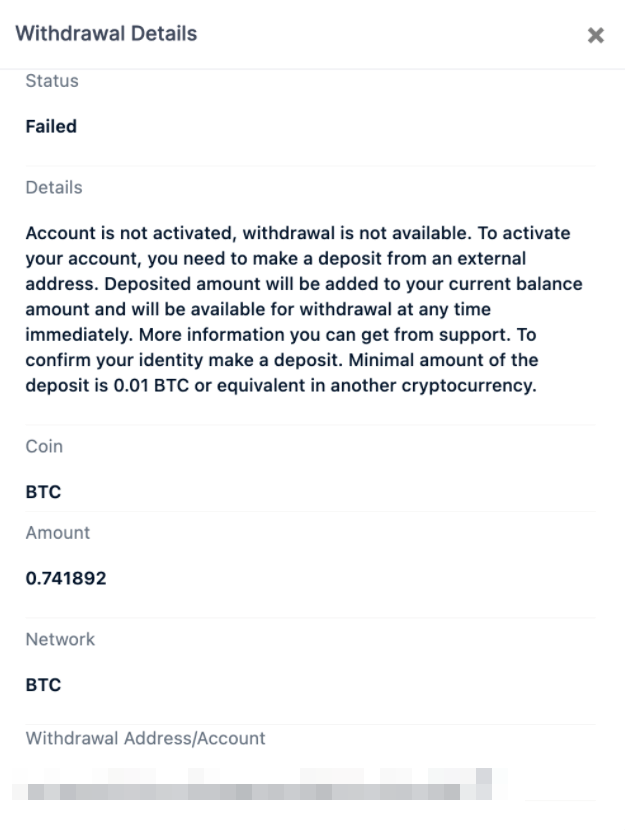
While relatively sizeable, the amount necessary to activate the account pales in comparison to what users would get in return. However, as expected, recipients never get anything in return when they pay the activation amount.
Closer examination found that the same individual registered a few other similar domain names, all of which showed the same web content as varbytrade[.]com:
- Harbytrade[.]com
- Jarbytrade[.]com
- Karbytrade[.]com
- Narbytrade[.]com
- Parbytrade[.]com
- Sarbytrade[.]com
In addition to being registered by the same person/s, the domains were registered the exact same day as varbytrade[.]com. The only difference between these sites were the slightly modified names and logos — with the rest of the content remaining exactly the same.

However, these six fraudulent websites conveying the same scam fraud were just the tip of the iceberg. We will examine the extent of the scam in the next section.
A constellation of websites
We kept digging further and discovered many websites — all with similar content —running the same fraud. While the websites show some variations in their templates, we are confident in mentioning that they are all linked.
Our investigation ended with over a thousand domains related to this fraud, created within the timeframe of January 2021 to May 2023. Furthermore, we found a few cryptocurrency-related fraudulent domains possibly connected to the authors being active as far back as 2016.

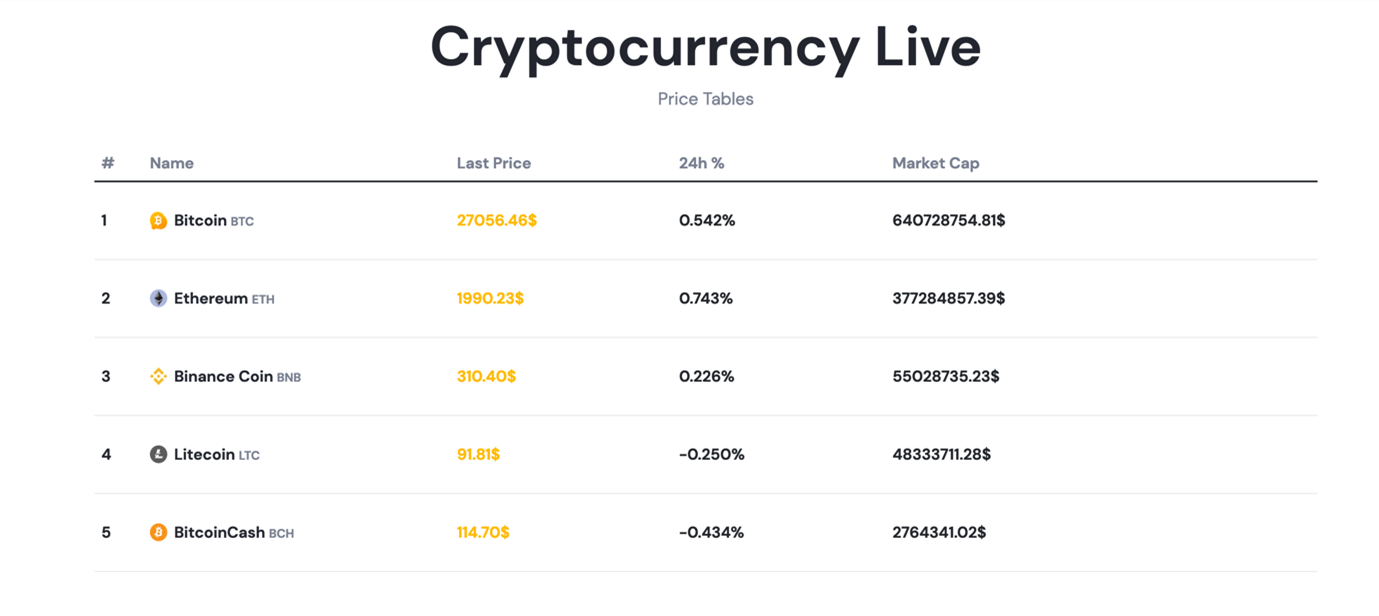
In terms of the website design, more content is generally shown on the first page to make it appear safe and legitimate to potential visitors. In addition, each of the websites had a section that showed the real-time prices of major cryptocurrencies, in an attempt to further mimic legitimate platforms.
The Impulse Project affiliate program
All the websites we encountered belong to an affiliate program, called the Impulse Project, that was being advertised on a few Russian-speaking cybercriminal forums.
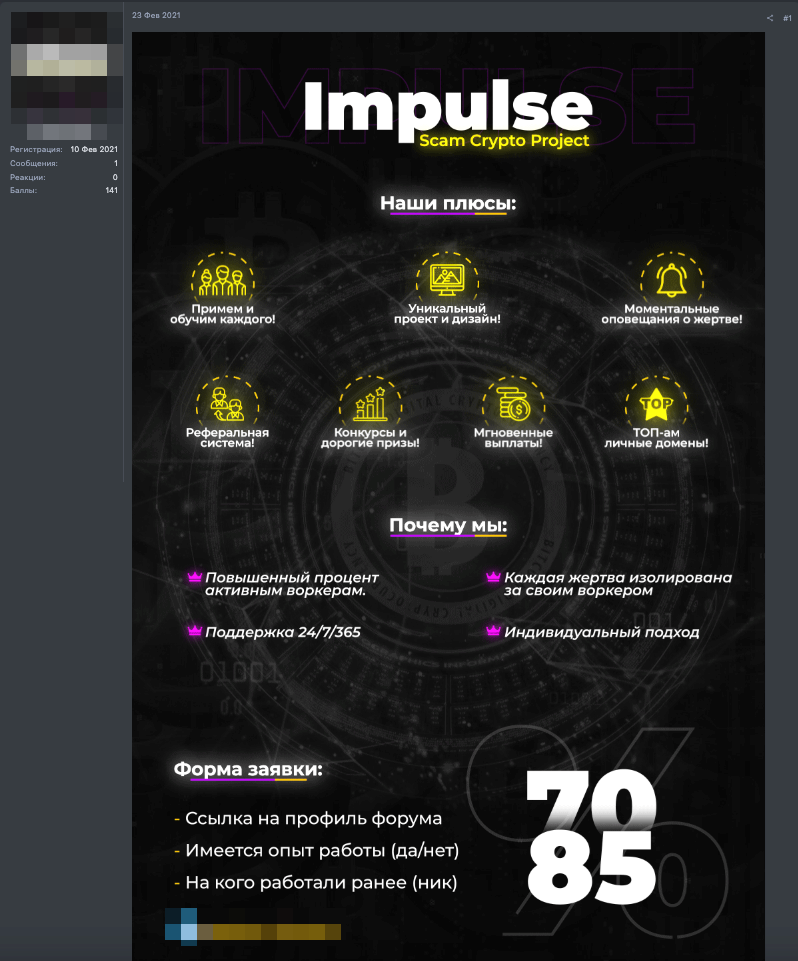
To become part of the project, new affiliates need to contact the Impulse Team and subscribe to the service. We couldn’t find information regarding the rates applied by the threat actor, but joining these types of programs typically requires a fee. Furthermore, a percentage of every fraudulent transaction goes to the masterminds.
Impulse Team provides several screen captures showing their interface, as shown in Figure 7. Screen captures of the main admin interface used by the Impulse Team are also shown.
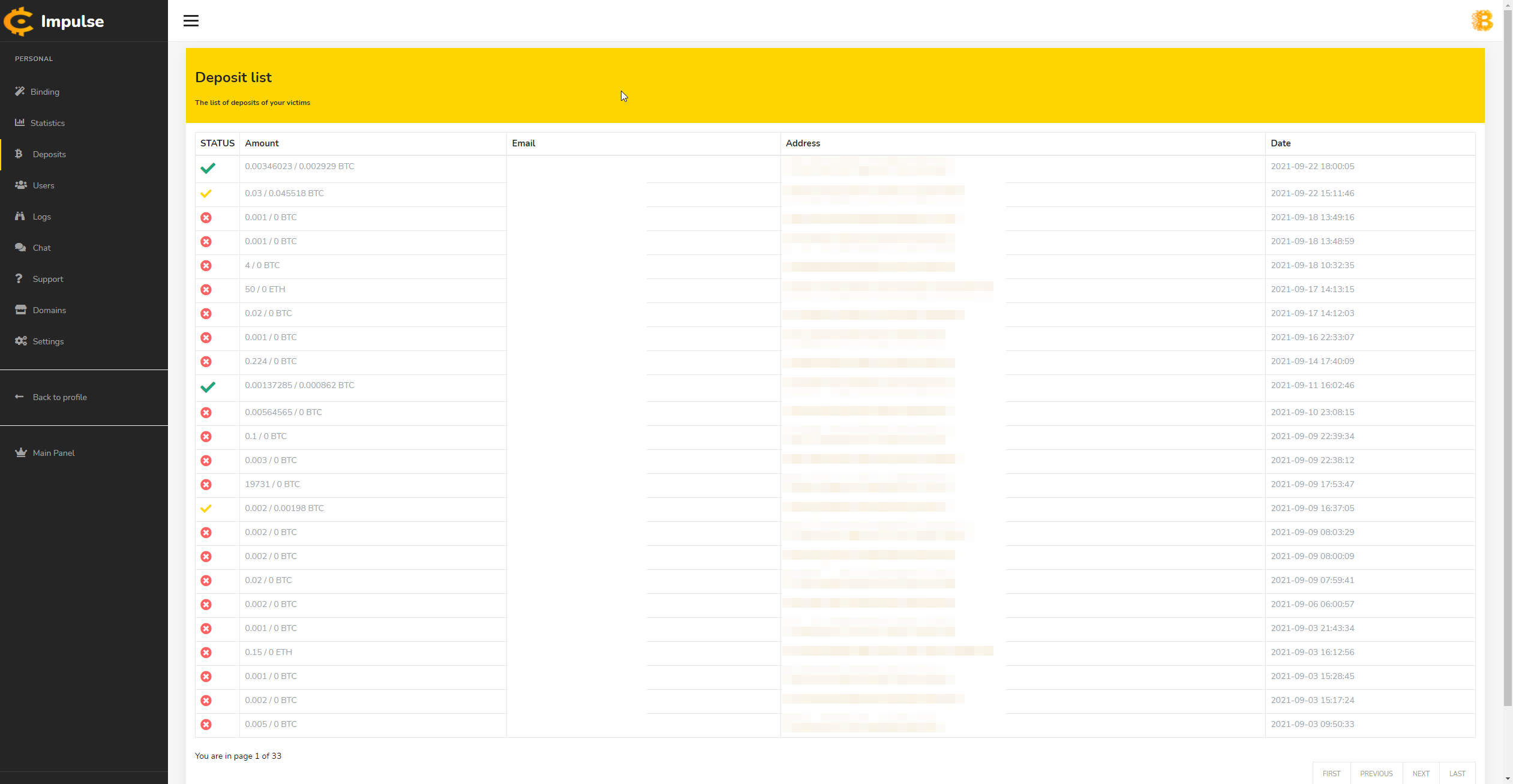
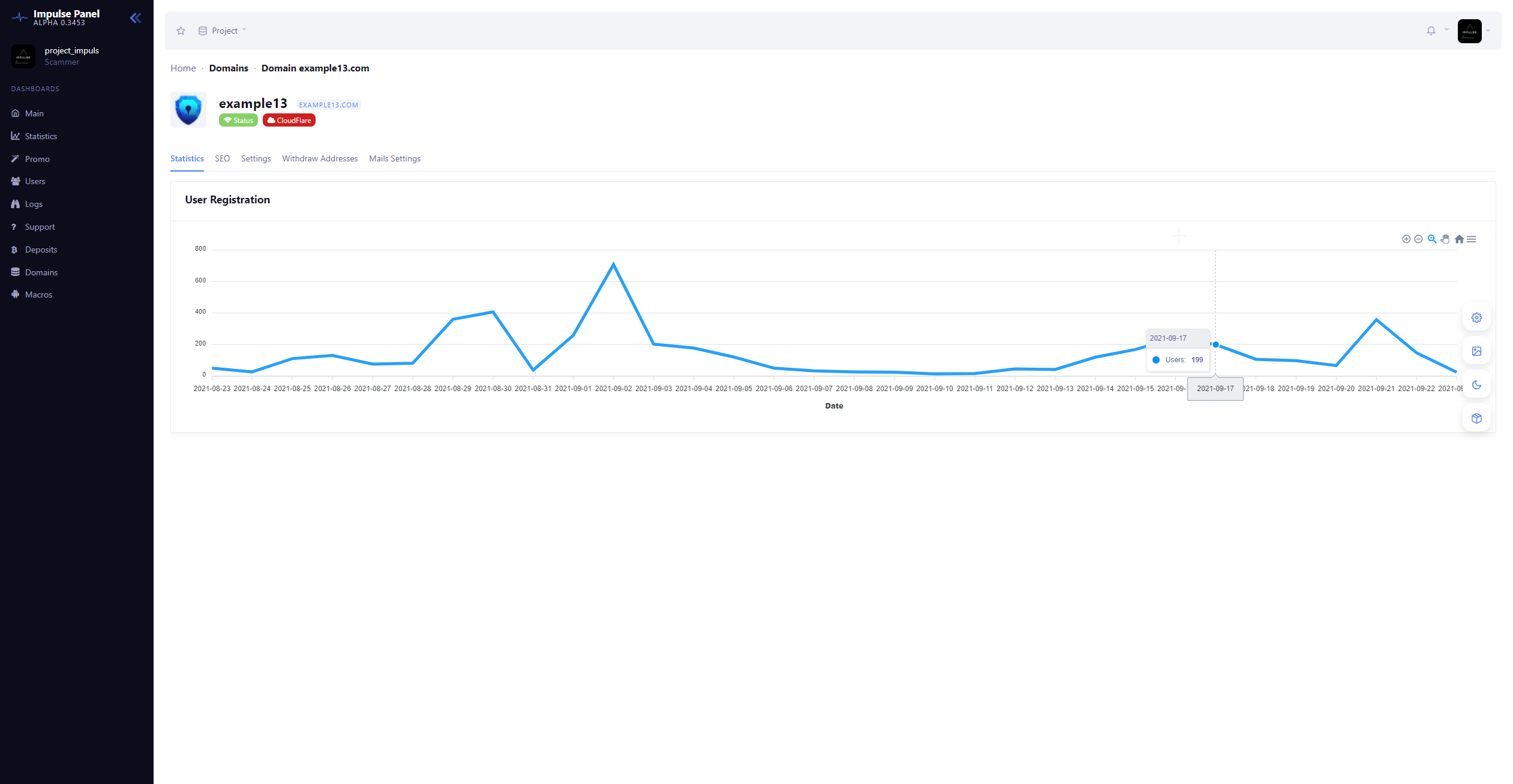
Affiliates need to register the domain names themselves before giving them to the Impulse Team. This is the reason for the many different registration methods for domain names. Once the affiliates have their domains, they are configured with scripts provided by the Impulse Team that are used for CloudFlare services.
Affiliates get one database for their websites. This means that if a victim creates an account on one website, the credentials also work for all the other websites used by the affiliate. This provides additional evidence that the affiliates run their own operation separately from each other.
The scam-doc fake website
During our investigation, we were able to find one website that did not correspond to the others.
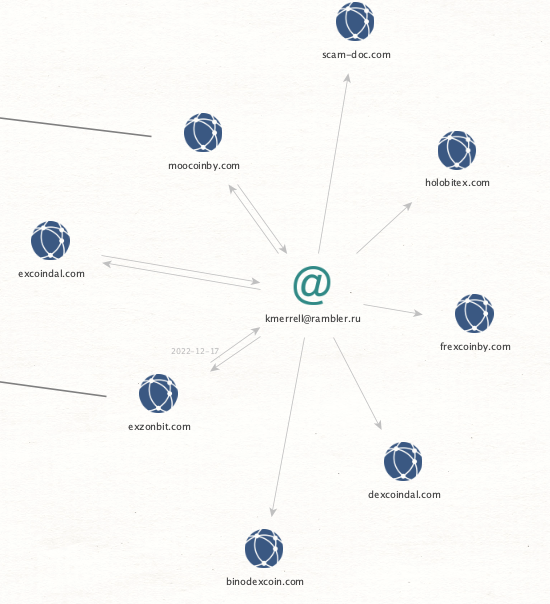
A domain named scam-doc[.]com, a spoof of a legitimate web tool (scamdoc.com) that checks website authenticity, had been registered by an email address that was also used to register some of the other cryptocurrency scam websites. Although it was already offline at the time of investigation, we were able to find its previous content via archive.org:
![Figure 10. Fraudulent scam-doc[.]com website (top) impersonating the legitimate scamdoc.com (bottom)](https://www.trendmicro.com/content/dam/trendmicro/global/en/research/23/f/impulse-team-massive-years-long-mostly-undetected-cryptocurrency-scam/impulseproject10a.png)
![Figure 10. Fraudulent scam-doc[.]com website (top) impersonating the legitimate scamdoc.com (bottom)](https://www.trendmicro.com/content/dam/trendmicro/global/en/research/23/f/impulse-team-massive-years-long-mostly-undetected-cryptocurrency-scam/impulseproject10b.png)
![Figure 10. Fraudulent scam-doc[.]com website (top) impersonating the legitimate scamdoc.com (bottom)](https://www.trendmicro.com/content/dam/trendmicro/global/en/research/23/f/impulse-team-massive-years-long-mostly-undetected-cryptocurrency-scam/impulseproject10c2.png)
As shown in Figure 10, although the images on the website cannot be seen because they’re being accessed via an archive, the fraudulent website reproduces aspects of the legitimate one, such as the banner text. More interestingly, the website shows a trust score for various websites, some being legitimate, but others being fraudulent.
While we have not been able to find emails or advertisements for the fraudulent scam-doc[.]com website, we highly suspect it has been used to entice unsuspecting users to bogus websites controlled by the cybercriminals by making them believe they are accessing a highly-trusted web tool.
As a sidenote, the websites shown with high trust levels are not only cryptocurrency scams, but also casino websites. We can only suppose that either the same cybercriminals run operations involving both or that several different cybercriminals share the scam-doc[.]com site.
The fraudulent page was online from December 2021 to July 2022 without any change in content.
Social network activities
So far, we’ve shown screenshots of the fraudulent activity being served on Twitter. However, this is not the only platform the threat actors use to advertise their operations — we also found online videos and ads on other social networks such as TikTok.
Advertising for the fraudulent websites is done by the affiliates themselves, which explains why different methods were being used. Figures 11 and 12 show a couple of examples of this.
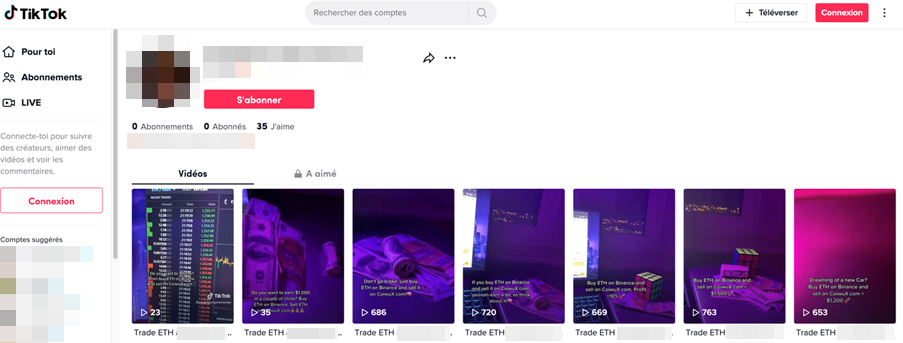
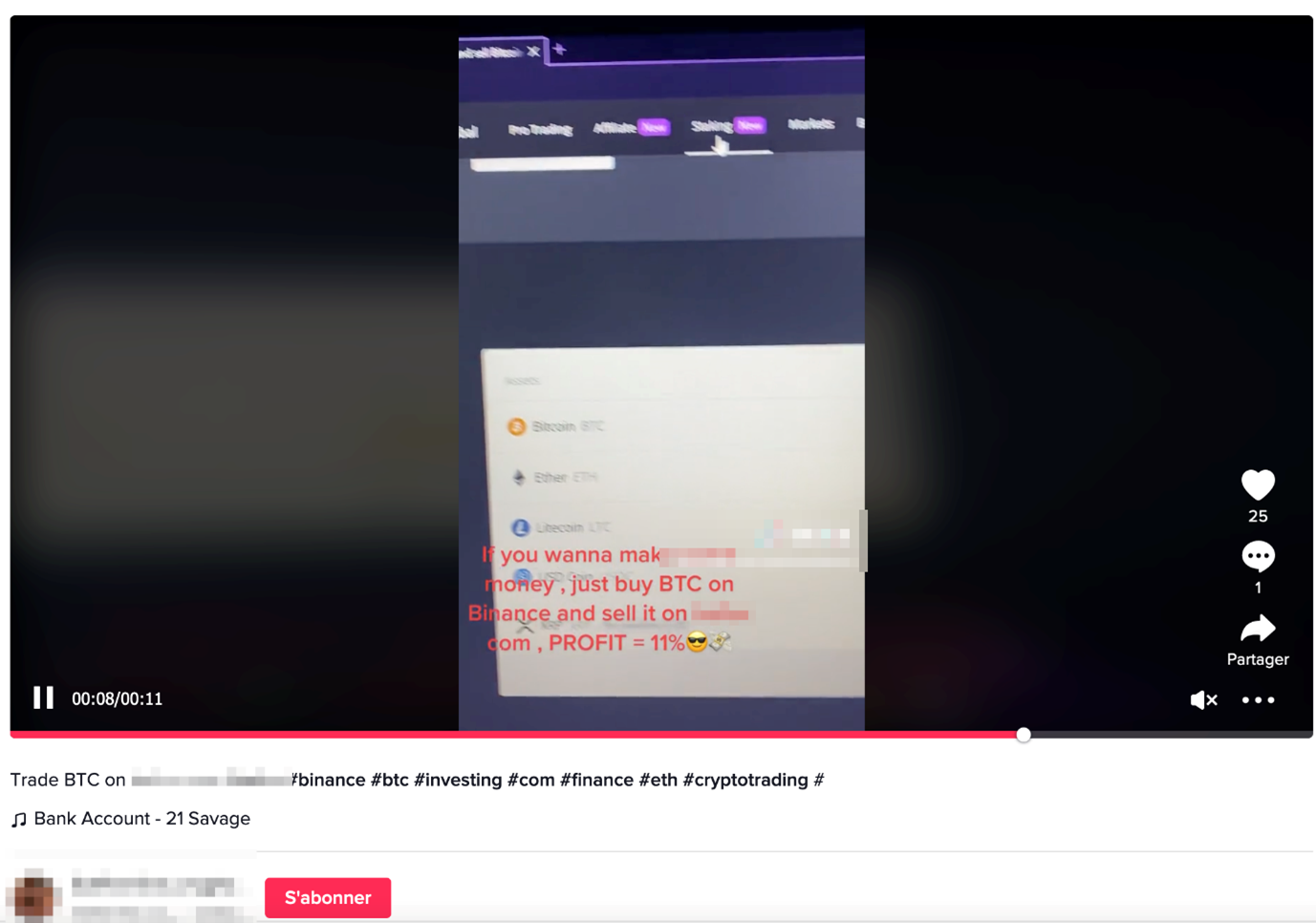
One (or several) affiliates also used the social networking site Mastodon to heavily promote their scam websites, as reported in May 2023 by Brian Krebs. In this article, Renaud Chaput, a freelance programmer working on the Mastodon project infrastructure, reports heavy spamming of some Mastodon servers via private messages advertising for over a hundred different scam websites. Mr. Chaput, who was kind enough to provide us with information when we reached out him, explained that he had seen hundreds of email accounts register Mastodon accounts within minutes before proceeding to send the scam messages.
This massive scam campaign has been reported several times before, but smaller in scope. Since discussions of the scam usually happen on cryptocurrency or scam websites, people can provide information on these schemes, but only for the part they’ve seen. It usually results in the reporting of up to a few dozen websites at a time, but with most people being unable to connect them to the rest of the scam campaign.
Some users and websites have done a good job of investigating these scams, such as Fake Website Buster or in a bitcointalk.org conversation exposing nearly 180 websites from the scam. Yet this is only just a portion of the total, as new fraudulent websites are created weekly and our evidence shows that over a thousand have already been created as of the time of writing.
Financial losses for victims
We were able to access a public Telegram channel that serves as a logging system for the Impulse Project scam. This channel is being fed by bots who add messages as soon as a victim deposits a cryptocurrency payment.
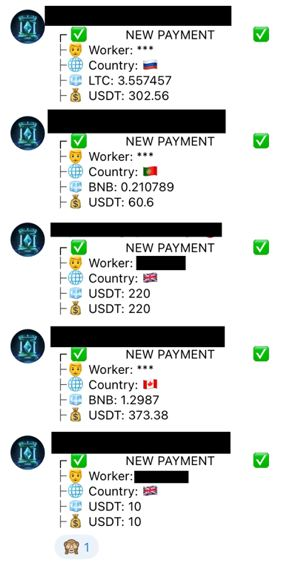
The channel was created in October 2022, yet only started showing cryptocurrency transactions beginning December 24, 2022.
Between December 24, 2022, and March 8, 2023, the sum of all transactions represents a little over US$5,000,000 held as USDT (Tether).
Seeing some of the amounts sent through single transactions, we suspect that the Impulse Team manipulates bots to provide fake numbers, probably to attract more affiliates by showing them the channel and making them believe they will earn plenty of money within a short span of time.
One comment from a Bitcoinabuse user, which we could not confirm, mentions one Bitcoin wallet belonging to the Jarbytrade website:
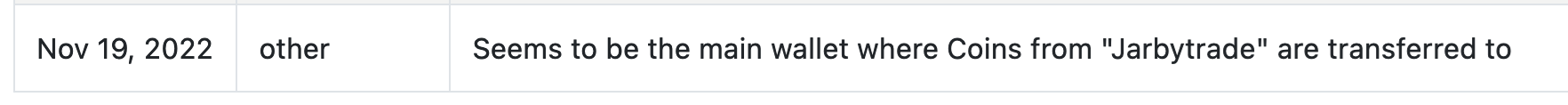
This wallet has received about US$500,000 worth of BTC (converted at the time of writing this report). However, we couldn’t confirm if this wallet is indeed associated with the affiliate running the Jarbytrade part of the fraud.
Conclusion
In this blog entry, we want to expose the massive infrastructure that the threat actor known as Impulse Team uses to run their Impulse Project cryptocurrency scam. The threat actor streamlines operations for its affiliates by providing hosting and infrastructure so they can run these scam websites on their own. Affiliates are then able to concentrate on other aspects of the operation, such as running their own advertising campaigns.
This benefits both the Impulse Team, who is able to earn from its affiliates either by earning a percentage of profits or by being paid directly by the affiliates, and the affiliates themselves, who now have access to resources to run these scam operations.
Recommendations
Users should always be wary of online ads, especially if they are being sent directly through private messages and social media. Approach online ads with a healthy dose of skepticism (if something seems too good to be true, it probably is) will help users avoid being scammed by these types of operations. Furthermore, it should be standard best practice to always check the credibility of the website or platform where the ad is displayed. Users should stick to reputable and well-known platforms that have established trust.
Other best practices:
- Do research on the product or service. Before making any purchase, users should do their due diligence and research the product or service being advertised. Reviews, ratings, and feedback from other customers can help users get a sense of its reliability.
- Avoid clicking on suspicious links. People should be cautious when clicking on ads that redirect unknown websites. Hovering over the links to view the URL can help confirm if they lead to a legitimate destination.
- Be aware of phishing attempts. Fraudulent ads may try to trick people into providing personal information or login credentials. Users should avoid sharing sensitive details through online ads or suspicious links.
- Be skeptical of “low risk-high return” investment opportunities. If an investment opportunity seems too good to be true, it probably is. Conduct thorough research and verification before investing your money.
- Be aware of emerging tactics. Stay informed about the latest strategies employed by scammers, such as the use of group chats and the identification of fake platforms. By acquiring an understanding of how these scams operate, individuals can enhance their ability to recognize warning signs and protect themselves from becoming victims.
Vigilance and common sense are crucial when dealing with online ads. If something feels off or suspicious, it’s best to err on the side of caution and avoid engaging with the ad altogether.
As always, Trend Micro will keep disclosing these types of cybercrime activities as we have always done.
Indicators of Compromise
The indicators of compromise for this entry can be found here.
Source: https://www.trendmicro.com/en_us/research/23/f/impulse-team-massive-cryptocurrency-scam.html
Views: 0

 简体中文
简体中文 Nederlands
Nederlands Français
Français Bahasa Indonesia
Bahasa Indonesia 日本語
日本語 Português
Português