We analyze the latest changes in IcedID botnet from a campaign that abuses Google pay per click (PPC) ads to distribute IcedID via malvertising attacks.
After closely tracking the activities of the IcedID botnet, we have discovered some significant changes in its distribution methods. Since December 2022, we observed the abuse of Google pay per click (PPC) ads to distribute IcedID via malvertising attacks. This IcedID variant is detected by Trend Micro as TrojanSpy.Win64.ICEDID.SMYXCLGZ.
Advertising platforms like Google Ads enable businesses to display advertisements to target audiences for the purpose of boosting traffic and increasing sales. Malware distributors abuse the same functionality in a technique known as malvertising, wherein chosen keywords are hijacked to display malicious ads that lure unsuspecting search engine users to downloading malware.
In our investigation, malicious actors used malvertising to distribute the IcedID malware via cloned webpages of legitimate organizations and well-known applications. Recently, the Federal Bureau of Investigation (FBI) published a warning pertaining to how cybercriminals abuse search engine advertisement services to imitate legitimate brands and direct users to malicious sites for financial gain.
Our blog entry provides the technical details of IcedID botnet’s new distribution method and the new loader it uses.
Technical analysis
Organic search results are those generated by the Google PageRank algorithm, whereas Google Ads appear in more prominent locations above, beside, below, or with the organic search results. When these ads are hijacked by malicious actors via malvertising, they can lead users to malicious websites.
Targeted brands and applications
In our investigation, we discovered that IcedID distributors hijacked the keywords used by these brands and applications to display malicious ads:
- Adobe – A computer software company
- AnyDesk – A remote control application
- Brave Browser – A web browser
- Chase Bank – A banking application
- Discord – An instant messenger service
- Fortinet – A security company
- GoTo – A remote control application
- Libre Office – An open-source alternative to Microsoft Office
- OBS Project – A streaming application
- Ring – A home CCTV (closed-circuit) manufacturer
- Sandboxie – A virtualization/sandbox application
- Slack – An instant messaging application
- Teamviewer – A remote control application
- Thunderbird – An email client
- US Internal Revenue Service (IRS) – A US federal government body
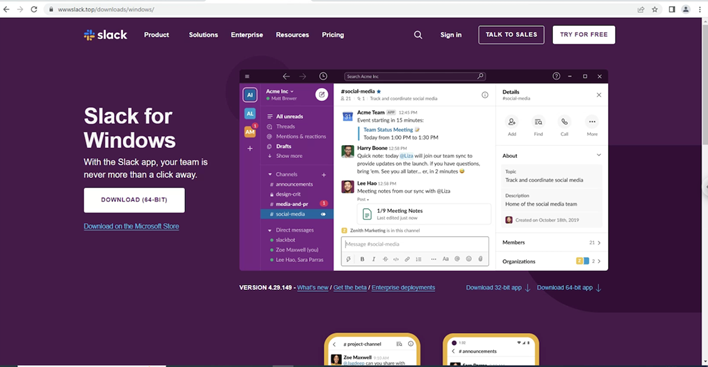
The malicious websites where victims are directed are made to look like their legitimate counterparts. Figure 1 shows a legitimate-looking malicious Slack webpage used by IcedID distributors to lure victims into downloading malware.
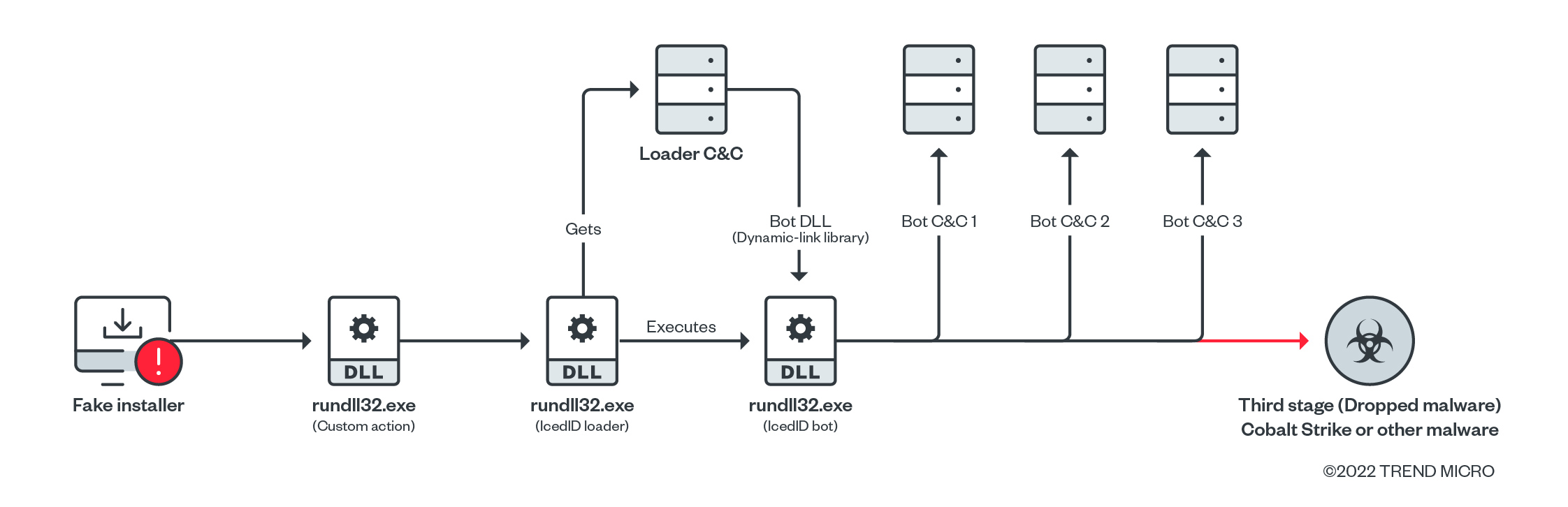
Infection chain
The overall infection flow involves delivering the initial loader, fetching the bot core, and ultimately, dropping the payload. The payload is typically a backdoor.
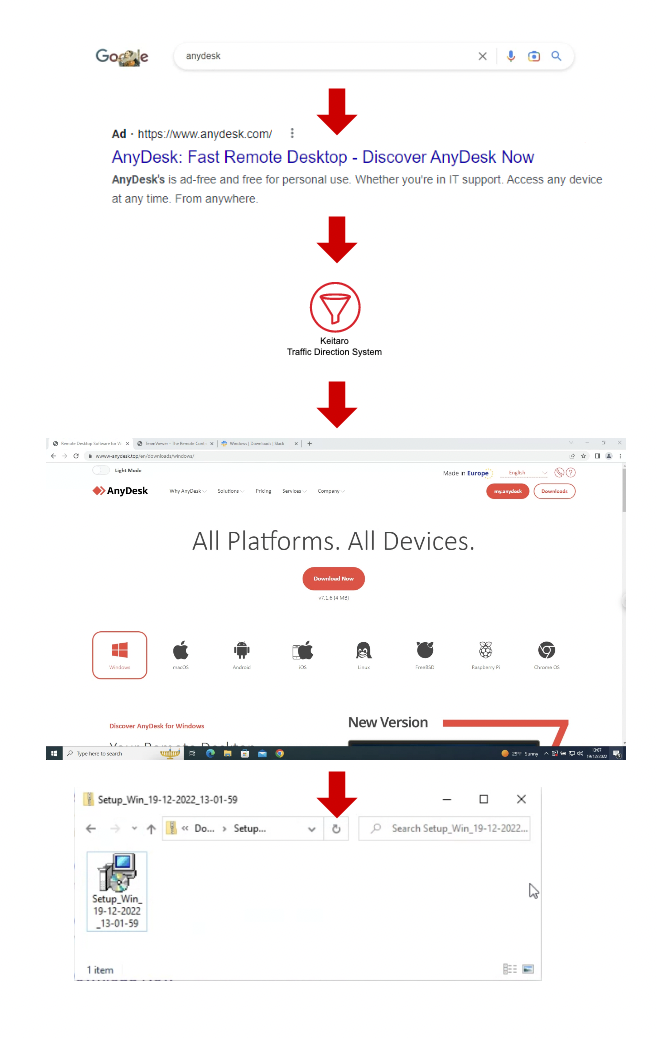
Infection via malvertising
- A user searches for an application by entering a search term on Google. In this particular example, the user wants to download the AnyDesk application and enters the search term “AnyDesk” on the Google search bar.
- A malicious ad for the AnyDesk application that leads to a malicious website is displayed above the organic search results.
- IcedID actors abuse the legitimate Keitaro Traffic Direction System (TDS), to filter researcher and sandbox traffic. The victim is then redirected to a malicious website.
- Once the user selects the “Download” button, it downloads a malicious Microsoft Software Installer (MSI) or Windows Installer file inside a ZIP file in the user’s system.
The new IcedID botnet loader
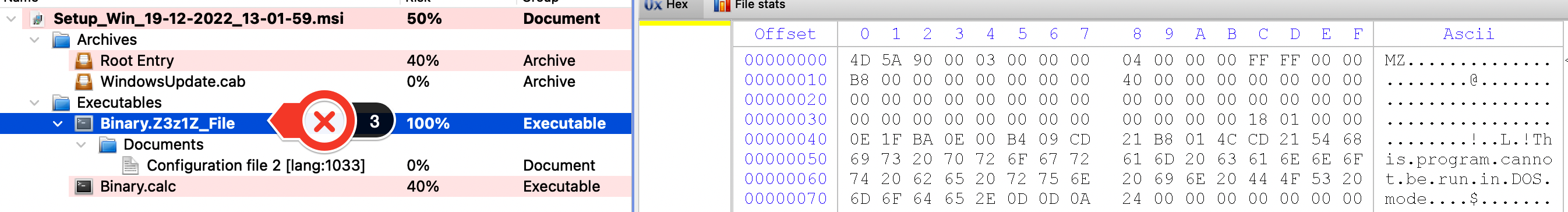
In this campaign, the loader is dropped via an MSI file, which is atypical for IcedID.
The installer drops several files and invokes the “init” export function via rundll32.exe, which then executes the malicious loader routine.
This “loader” DLL has the following characteristics:
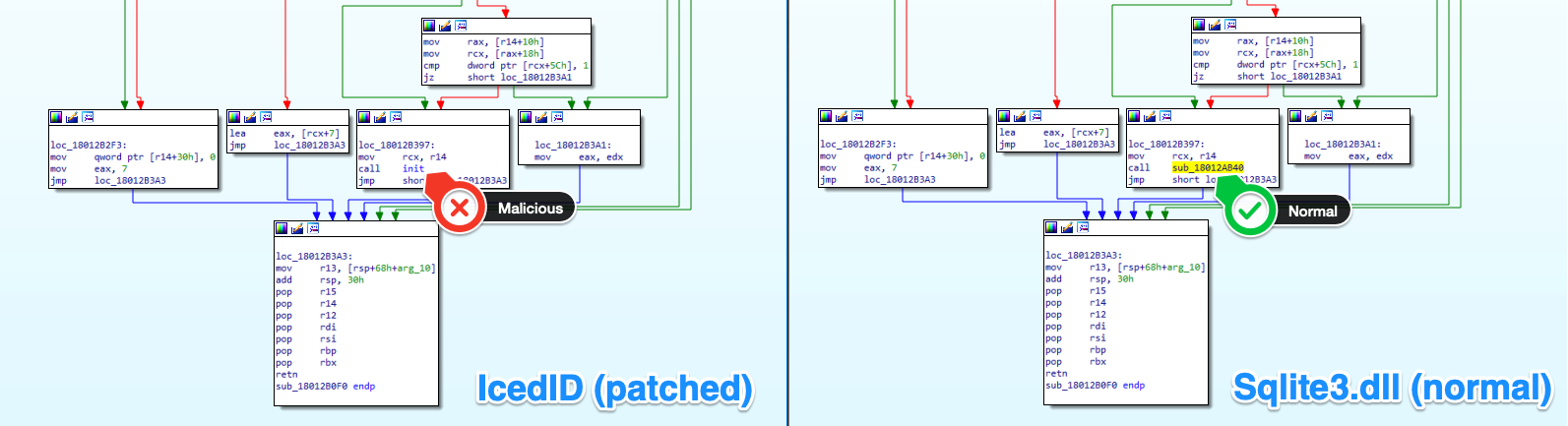
- The authors have taken a legitimate DLL and replaced a single legitimate function with the malicious loader function using the “init” export function name at the last ordinal.
- The first character of each legitimate export function in the IcedID loader is replaced with the letter “h.”
- The reference to the malicious function is a patched legitimate function.
The resulting malicious file is almost identical to the legitimate version. This can prove to be challenging for machine learning (ML) detection solutions.
On the surface, the malicious IcedID and legitimate sqlite3.dll files look almost identical. Figure 4 shows a side-by-side comparison of these files using the PortEx Analyzer tool, which was developed by security researcher Karsten Hahn. The tool allows us to quickly visualize the structure of the portable executable (PE) files, and, in this case, assess the similarity of files.
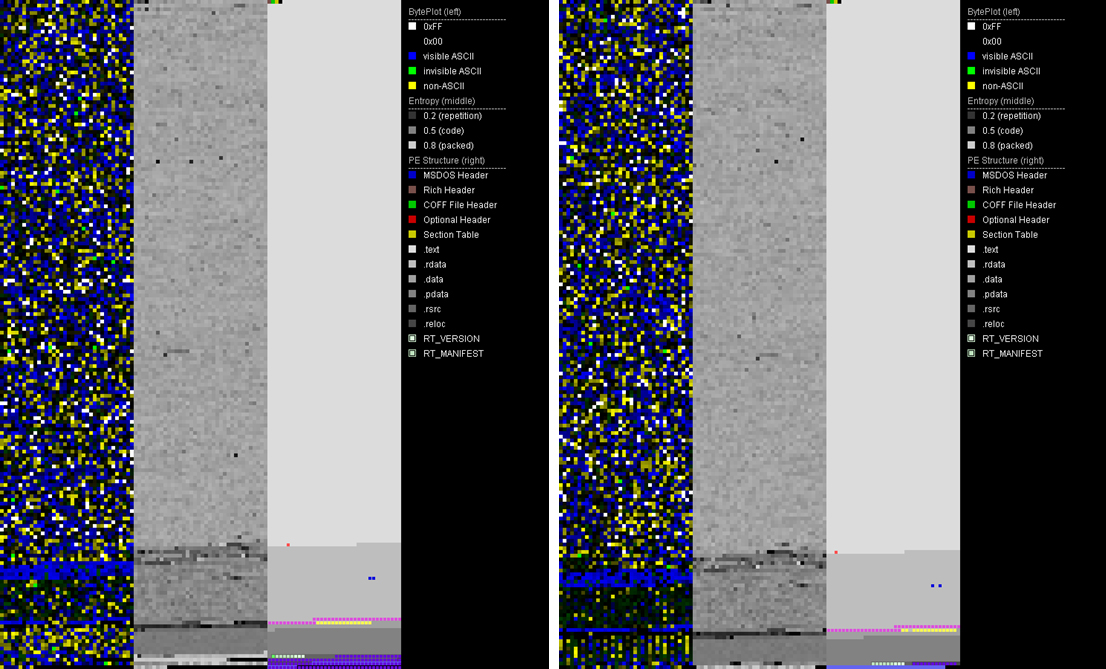
For this reason, we hypothesize that this is an attack on two types of malware detection technologies:
- Machine learning detection engines
- Whitelisting systems
Tampered DLL files functioning as IcedID loaders
We have observed that some of the files that have been modified to act as IcedID loaders are well-known and widely used libraries.
| DLL name | Description |
| tcl86.dll | A library component of ActiveState’s TCL (Tool Command Language) Programming Language Interpreter |
| sqlite3.dll | A library component of SQLite database |
| ConEmuTh.x64.dll | A plugin for Far Manager |
| libcurl.dll | A CURL library |
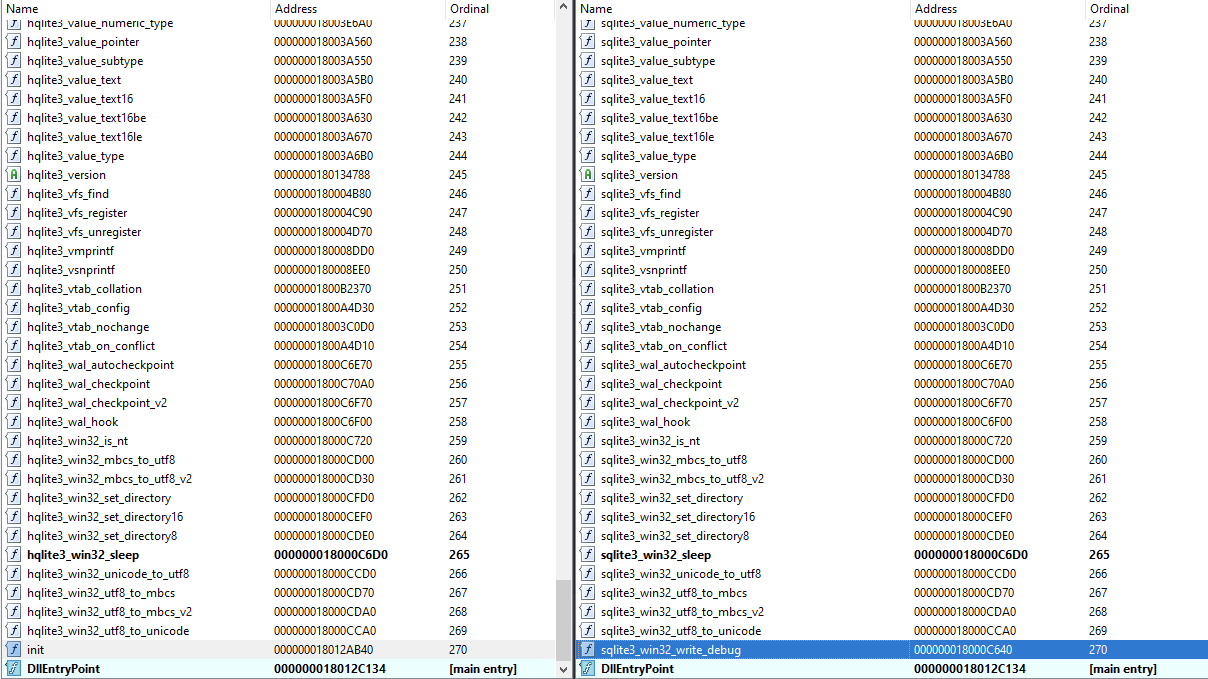
In sqlite3.dll, we observed that the function at ordinal 270 “sqlite3_win32_write_debug” has been replaced with the malicious “init” function in the IcedID loader.
This is the case across the modified DLL files listed above: The export function at the last ordinal is replaced with the malicious “init” function.
Further investigation shows that the structure of the file is identical.
Execution
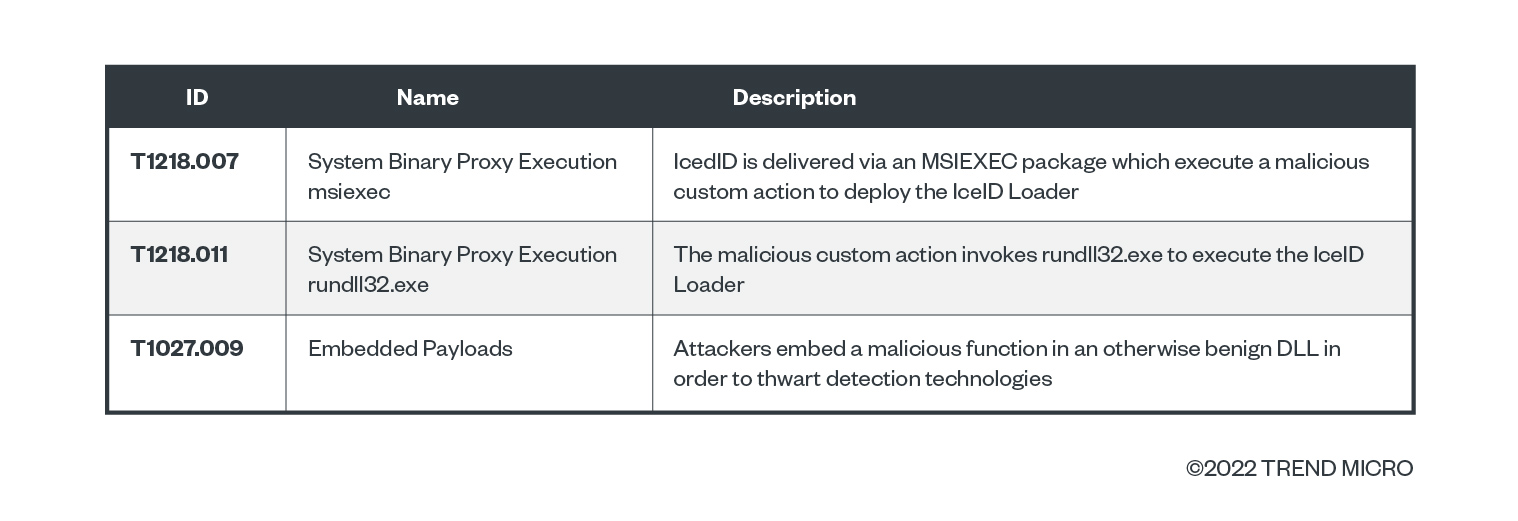
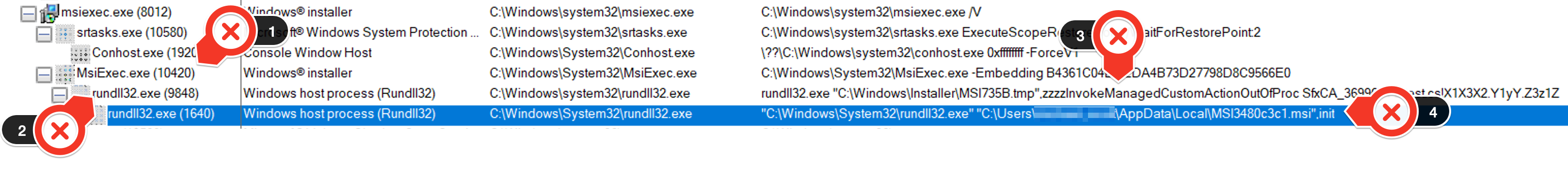
- “MsiExec.exe” executes (parent process) (MITRE ID T1218.007 – System Binary Proxy Execution: msiexec)
- “rundll32.exe” is spawned (MITRE ID T1218.011 – System Binary Proxy Execution: rundll32.exe)
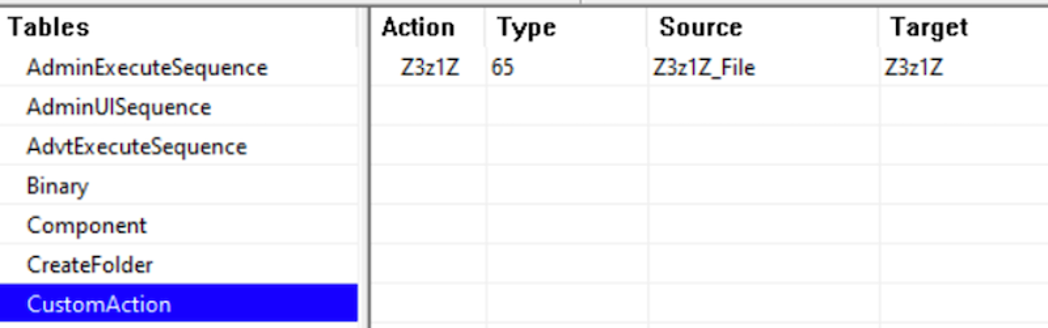
- “rundll32.exe” runs the custom action “Z3z1Z” via “zzzzInvokeManagedCustomActionOutOfProc” (MITRE ID T1218.011 – System Binary Proxy Execution: rundll32.exe)
- The custom action spawns a second “rundll32.exe” to run the IcedID loader “MSI3480c3c1.msi” with the “init” export function (MITRE IDs T1027.009 – Embedded Payloads and T1218.011 – System Binary Proxy Execution: rundll32.exe)
Conclusion
IcedID is a noteworthy malware family that is capable of delivering other payloads, including Cobalt Strike and other malware. IcedID enables attackers to perform highly impactful follow through attacks that lead to total system compromise, such as data theft and crippling ransomware. The use of malvertising and an evasive loader is a reminder of why it’s important for businesses to deploy layered security solutions that include custom sandboxing, predictive machine learning, behavior monitoring and file and web reputation detection capabilities. Users can also consider the use of ad blockers to help thwart malveritising attacks.
Indicators Of Compromise (IOCs)
The indicators of compromise can be accessed via this text file.
Mitre ATT&CK