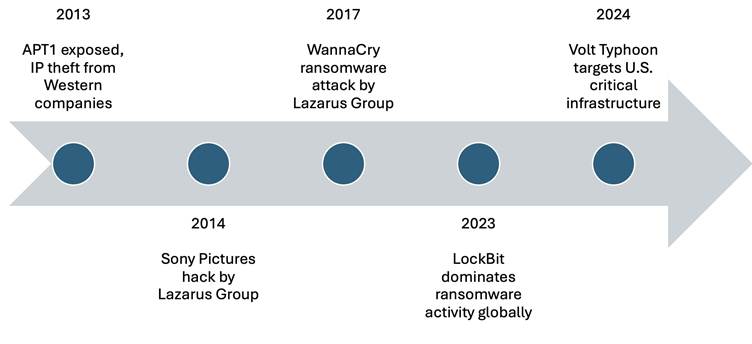
The article explores the merging tactics of nation-state actors and organized cybercriminals, highlighting their shared methods and objectives in the evolving cyber threat landscape. It emphasizes the implications for global cybersecurity as both groups increasingly adopt similar strategies. Affected: Russia’s APT28, China’s APT10, Volt Typhoon, APT29, APT33, Lazarus Group, REvil, DarkSide, BianLian
Keypoints :
- The distinction between nation-state actors and organized cybercriminals is becoming less clear.
- Nation-state actors typically pursue geopolitical objectives, while organized cybercriminals focus on financial gain.
- Groups like Russia’s APT28 and China’s APT10 target governmental networks for intelligence gathering.
- Cybercriminals leverage Ransomware-as-a-Service (RaaS) for extortion and theft.
- There is a growing convergence of tactics between state actors and cybercriminals.
- Artificial intelligence is increasingly used by both groups to enhance attack effectiveness.
- Attribution of cyber attacks is complicated by shared techniques and tools.
- International cooperation is essential to bolster defenses against these evolving threats.
MITRE Techniques :
- Initial Access (T1078) – Phishing and supply chain attacks are used to gain initial access to target networks.
- Execution (T1203) – Exploit kits and social engineering tactics are employed to execute malicious payloads.
- Persistence (T1543) – Advanced evasion tactics, including fileless malware and rootkits, are utilized for maintaining access.
- Command and Control (T1071) – Encrypted channels and cloud services are leveraged for stealthy communication.
- Exfiltration (T1041) – Data is exfiltrated using various methods, including custom-built malware for long-term operations.
Full Research: https://gbhackers.com/how-nation-state-actors-and-organised-hackers/