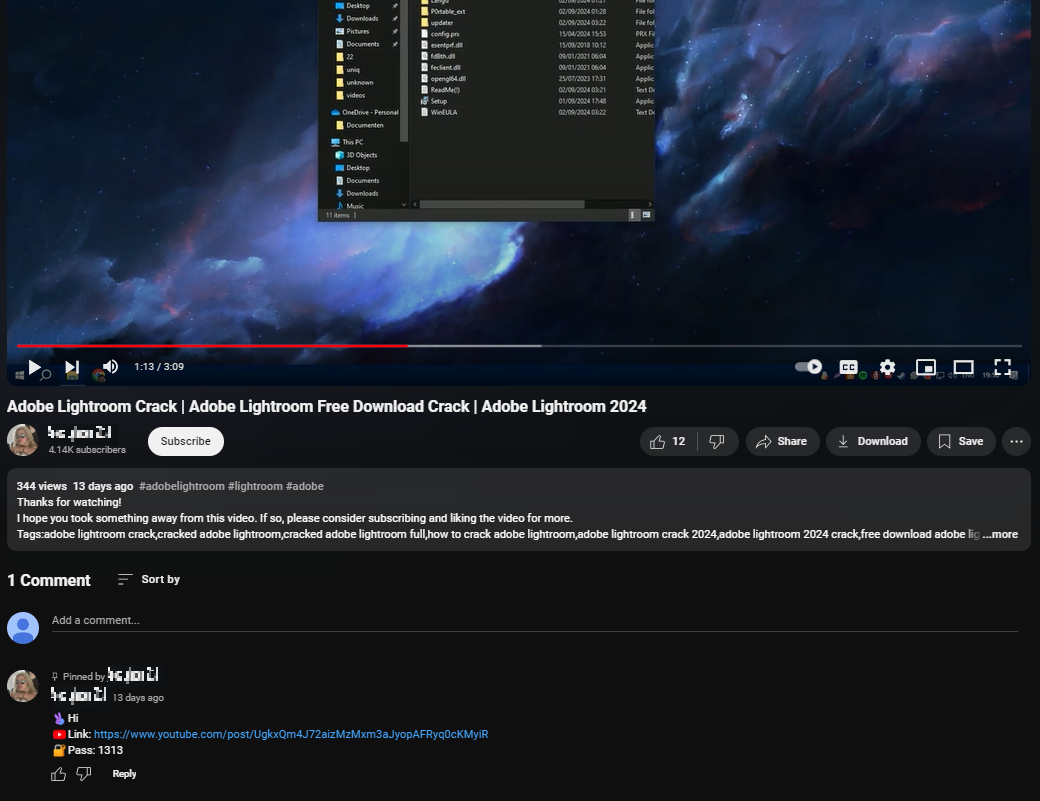
This article discusses the tactics used by attackers to distribute fake installers via trusted platforms like YouTube and file hosting services. By employing encryption and social engineering, these attackers aim to evade detection and steal sensitive browser data from unsuspecting users. Affected: YouTube, Mediafire, Mega.nz, OpenSea, SoundCloud
Keypoints :
- Attackers exploit user trust by using platforms like YouTube to share fake installer links.
- Reputable file hosting services, such as Mediafire and Mega.nz, are used to obscure the malware’s origin.
- Malicious downloads are often password-protected and encoded, complicating analysis in security environments.
- Once installed, malware collects sensitive data from web browsers, posing serious risks to personal information.
- Users are often lured into downloading these threats while searching for pirated software.
MITRE Techniques :
- Credential Dumping (T1003) – Malware collects sensitive data from web browsers to steal credentials.
- Process Injection (T1055) – The malware injects its code into legitimate processes to evade detection.
- Obfuscated Files or Information (T1027) – The malware uses password-protected files and obfuscation techniques to hinder analysis.
- Command and Control (C2) (T1071) – The malware establishes connections to multiple command and control addresses.
- Domain Generation Algorithm (DGA) (T1483) – The malware queries DGA domains to evade detection.
Indicator of Compromise :
- [url] hxxps://mega[.]nz
- [url] hxxps://mediafire[.]com
- [url] hxxps://opensea[.]io
- [url] hxxps://soundcloud[.]com
- Check the article for all found IoCs.
Full Research: https://www.trendmicro.com/en_us/research/25/a/how-cracks-and-installers-bring-malware-to-your-device.html