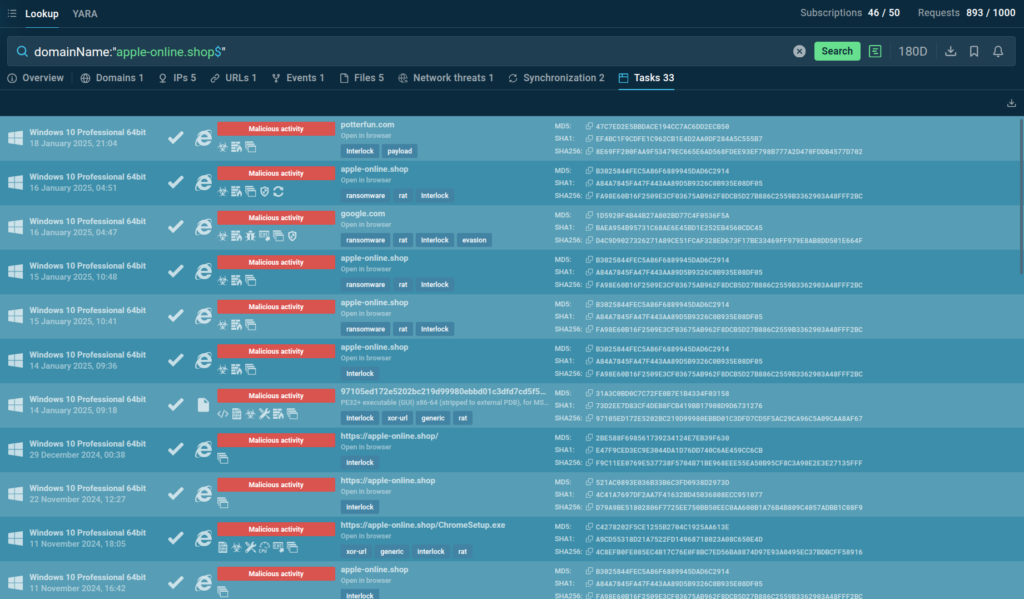
Ransomware attacks pose a significant threat to healthcare organizations, compromising sensitive patient data and disrupting critical services. ANY.RUN’s Interactive Sandbox and Threat Intelligence Lookup provide essential tools for identifying and analyzing these threats, as demonstrated through the Interlock ransomware case study. Affected: healthcare organizations, Interlock ransomware group
Keypoints :
- Ransomware attacks have increased in frequency and severity within the healthcare sector.
- ANY.RUN offers tools to help healthcare organizations analyze and respond to ransomware threats.
- Interlock ransomware group employs double-extortion tactics targeting healthcare facilities.
- Healthcare organizations face financial strain and operational disruptions due to ransomware incidents.
- ANY.RUN’s Interactive Sandbox allows for safe analysis of malware and threat intelligence.
MITRE Techniques :
- Initial Compromise (TA0001): Interlock uses Drive-by Compromise via phishing websites to gain access.
- Execution (TA0002): Fake updater files are executed, allowing attackers to control the victim’s system.
- Credential Access (TA0006): Custom stealer tools are employed to gather and exfiltrate access credentials.
- Lateral Movement (TA0008): Attackers use legitimate remote administration tools to spread across networks.
- Data Exfiltration (TA0010): Stolen data is transferred to the attackers’ infrastructure using Azure cloud storage.
Indicator of Compromise :
- [file name] upd_2327991.exe
- [file hash] 8d911ef72bdb4ec5b99b7548c0c89ffc8639068834a5e2b684c9d78504550927
- [file hash] 97105ed172e5202bc219d99980ebbd01c3dfd7cd5f5ac29ca96c5a09caa8af67
- [url] apple-online.shop
- Check the article for all found IoCs.
Full Research: https://any.run/cybersecurity-blog/cybersecurity-blog/interlock-ransomware-attack-analysis/