The article discusses the significant increase in fake CAPTCHA websites and their misuse in cybercriminal activities like clipboard hijacking. This rise in fake CAPTCHAs aids in executing malicious commands on user systems. Notably, advanced threat actors are also adopting these tactics. Affected: websites, users, sectors related to cybersecurity
Keypoints :
- Fake CAPTCHA websites have nearly doubled in a few months.
- Cybercriminals are now actively employing clipboard hijacking tactics.
- Fake CAPTCHAs are commonly found on fraudulent web shops, news sites, and media websites.
- Advanced threat actors, including APT28 (Fancy Bear), are also using these techniques.
- A particular case involved an attempt to infect a user with Lumma Stealer malware through a fake CAPTCHA.
- Malware installation was facilitated via PowerShell commands, obfuscated to prevent detection.
- The payload included complex coding structures to hinder analysis and reverse engineering.
MITRE Techniques :
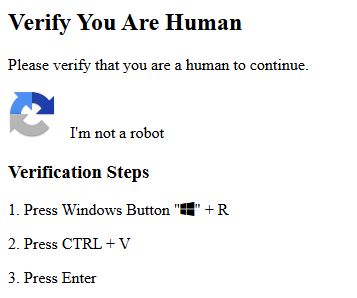
- Clipboard Hijacking (T1476) – A fake CAPTCHA prompts users to copy and paste clipboard contents into a command line.
- Powershell (T1059.001) – The command executed uses PowerShell to run a Base64-encoded script.
- Obfuscated Files or Information (T1027) – The malware script hides its true purpose through complex code and math operations.
- Command-Line Interface (T1059) – Commands are executed through the command line, allowing for script execution without user visibility.
Indicator of Compromise :
- [URL] https://findinmind[.]com/play.html
- [URL] https://eprime[.]shop/s6.mp3
- [URL] https://echoicedeals[.]shop/s6.mp3
- [URL] https://etrademart[.]shop/s6.mp3
- [URL] https://n.kliphirofey[.]shop/Nusku.jpeg
Full Story: https://www.threatdown.com/blog/more-cybercriminals-are-using-the-clipboard-hijacker-method/
Views: 4

 简体中文
简体中文 Nederlands
Nederlands Français
Français Bahasa Indonesia
Bahasa Indonesia 日本語
日本語 Português
Português