Summary: The Strela Stealer malware, operated by the Hive0145 threat actor group, primarily targets victims in Europe through phishing emails disguised as legitimate invoice notifications. This campaign has evolved to include sophisticated techniques such as attachment hijacking and the use of stolen emails to enhance the effectiveness of their phishing efforts.
Threat Actor: Hive0145 | Hive0145
Victim: Various organizations in Europe | European organizations
Key Point :
- Hive0145 is financially motivated and has been active since late 2022, focusing on extracting email credentials from Microsoft Outlook and Mozilla Thunderbird.
- The group has shifted tactics to use stolen emails for phishing, enhancing the legitimacy of their campaigns.
- Strela Stealer employs advanced techniques such as polyglot files, signed binaries, and attachment hijacking to evade detection and increase infection rates.
- Recent campaigns have targeted Ukrainian victims, indicating a geographical expansion of their operations.
- Organizations in Italian, Spanish, German, and Ukrainian-speaking regions are at heightened risk of being targeted by Hive0145’s phishing campaigns.
<!—->
<!– –>


As of November 2024, IBM X-Force has tracked ongoing Hive0145 campaigns delivering Strela Stealer malware to victims throughout Europe – primarily Spain, Germany and Ukraine. The phishing emails used in these campaigns are real invoice notifications, which have been stolen through previously exfiltrated email credentials. Strela Stealer is designed to extract user credentials stored in Microsoft Outlook and Mozilla Thunderbird. During the past 18 months, the group tested various techniques to enhance its operation’s effectiveness. Hive0145 is likely to be a financially motivated initial access broker (IAB), active since late 2022 and potentially the sole operator of Strela Stealer. The continuous operational pace of Hive0145’s campaigns highlights an increased risk to potential victims across Europe.
Key Findings:
Hive0145 is an initial access broker focused on targeting victims throughout Europe
During the last 18 months, Strela Stealer has tested out a variety of techniques to improve its infection chain and extract email credentials
As of July 2024, Hive0145 began using stolen emails to further spread Strela Stealer
Hive0145 campaigns have increased in volume, with weekly campaigns as of 17 October 2024
As of early November 2024, Hive0145 began targeting Ukraine with stolen invoice emails
Hive0145 is potentially the sole operator of Strela Stealer
Background
Starting mid-April 2023, X-Force began tracking an increase in Hive0145 activity. Hive0145 is likely a financially motivated initial access broker (IAB) and potentially the sole operator of Strela Stealer. Strela Stealer is a malware designed to extract user email credentials stored in Microsoft Outlook and Mozilla Thunderbird, potentially leading to Business Email Compromise (BEC). IABs routinely gather credentials and other data that is sold to affiliate threat actors specializing in victim network exploitation. However, it remains unknown if Hive0145 has a specific partner network for selling the access gained through their campaigns.
Over the past year, Hive0145 has demonstrated proficiency in evolving tactics, techniques and procedures (TTPs) to target victims across Europe. Italian, Spanish, German and Ukrainian victims continue to receive weaponized attachments that entice the victim to open the file. The actor’s campaigns present the victim with fake invoices or receipts and often a short, generic message of urgency for victims to address. Upon loading the attached file, the victim unwittingly executes the infection chain leading to Strela Stealer malware.
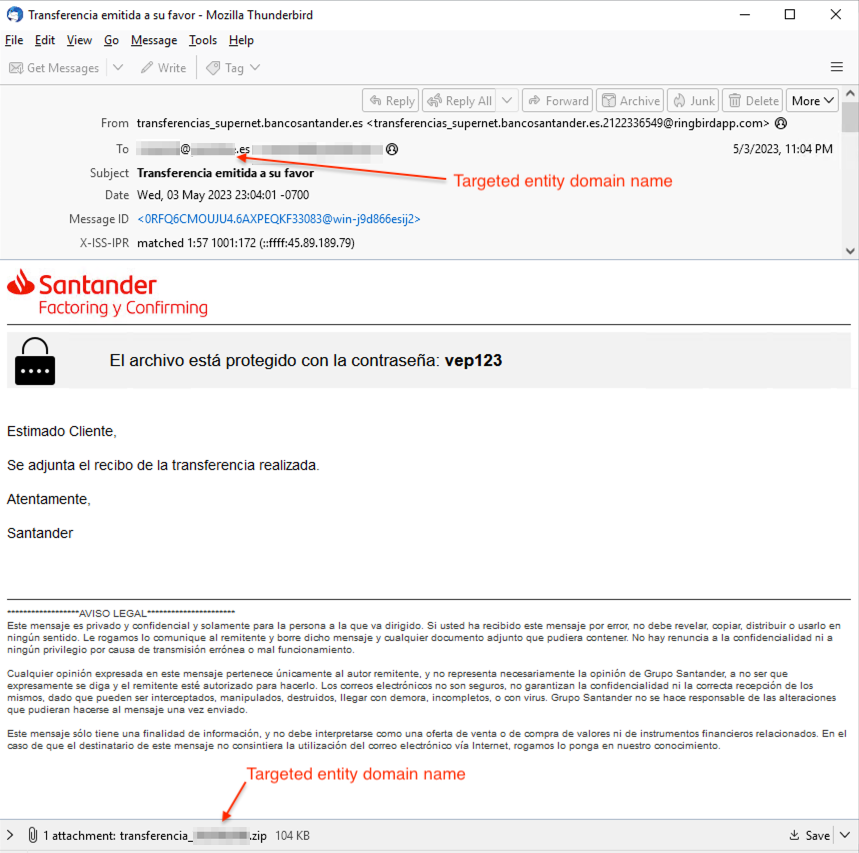
Figure 1 Banco Santander-themed email campaign
Hive0145 continued this pattern of using generic messages and fake invoices and receipts throughout the first half of 2024. However, by early July 2024, the group adopted a different approach and began weaponizing stolen emails of actual entities across financial, technology, manufacturing, media, e-commerce and other industries. The departure in simplicity indicates Hive0145’s shift in a maturing cyber operations capability.
Attachment hijacking
In July 2024, X-Force observed a mid-campaign change in the emails being distributed by Hive0145, with the short and generic messages being replaced with what appeared to be legitimate stolen emails. The phishing emails exactly matched official invoice communication emails and, in some cases, still directly addressed the original recipients by name. X-Force was able to verify that the emails were in fact authentic invoice notifications from a variety of entities across financial, technology, manufacturing, media, e-commerce and other industries. It is likely that the group sourced the emails through previously exfiltrated credentials from their prior campaigns.
The concept of using stolen emails is not new, it was used extensively by the Emotet group and malware distributors such as Hive0118 (aka TA577), TA551 and TA570. In their campaigns, they leveraged thread hijacking, where new threads to stolen emails were used as a way to increase the appearance of legitimacy. The modified emails were sent to corresponding contacts of previous victims, making the final email look like a reply to the stolen email, thereby hijacking the email thread. The text the distributors add to the emails is often short replies, urging victims to look at the included attachments or URLs.
The technique employed by Hive0145 differs from thread-hijacking in that rather than adding a reply message to the stolen email, the original contents remain largely unmodified and only the attachment is switched to include a malicious payload using the original filename (without the original extension). Within the email body, Hive0145 also replaces both the local part and the domain of the original email sender with that of the new phishing victim to custom-tailor the email. The emails with hijacked attachments are then sent out in mass phishing campaigns. Hive0145 also appears to carefully consider the hijacked emails by only selecting ones referring to invoices and containing attachments. X-Force has observed the attachment hijacking technique since mid-2024 in campaigns targeting German, Spanish and Ukrainian speakers.
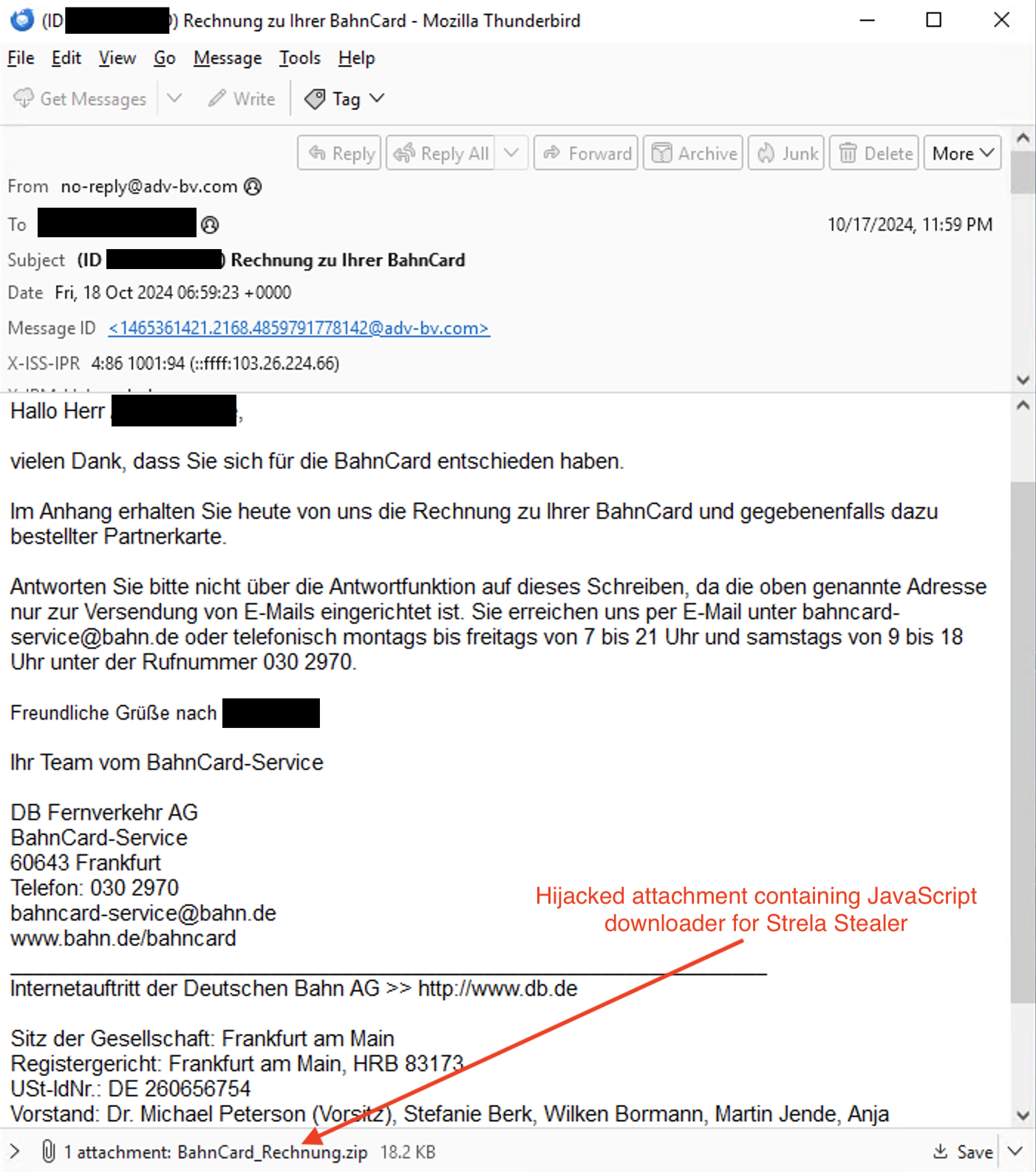
Figure 2 Example of original stolen email of a Deutsche Bahn invoice with hijacked attachment
Late 2024 campaign
The July 2024 campaign began to reveal low volumes of email delivery throughout the week of 8 July. Hive0145 appeared to take a short break before returning with a larger campaign the week of 22 July, followed by a period of inactivity. Starting mid-October 2024, Hive0145 returned with a widespread attachment hijacking campaign targeting Spanish, German and Ukrainian victims. Unlike the brief July campaign, this one has continued sending out notable volumes of emails with the majority sent during weekdays.
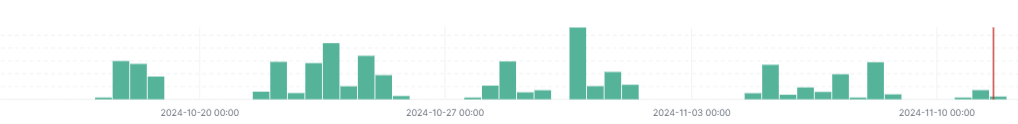
Figure 3 The ongoing late-October 2024 campaign
Emails stolen across financial, technology, manufacturing, media, e-commerce and other industries continue to be weaponized as of early November 2024, in one of the largest observed Hive0145 campaigns to date. In the ongoing campaign, the victim receives an archive containing a heavily obfuscated JavaScript file that downloads and executes a crypted Strela Stealer DLL. As of 7 November 2024, Hive0145 is including Ukrainian speakers in the ongoing campaign signaling a significant development compared to previously observed victimology.
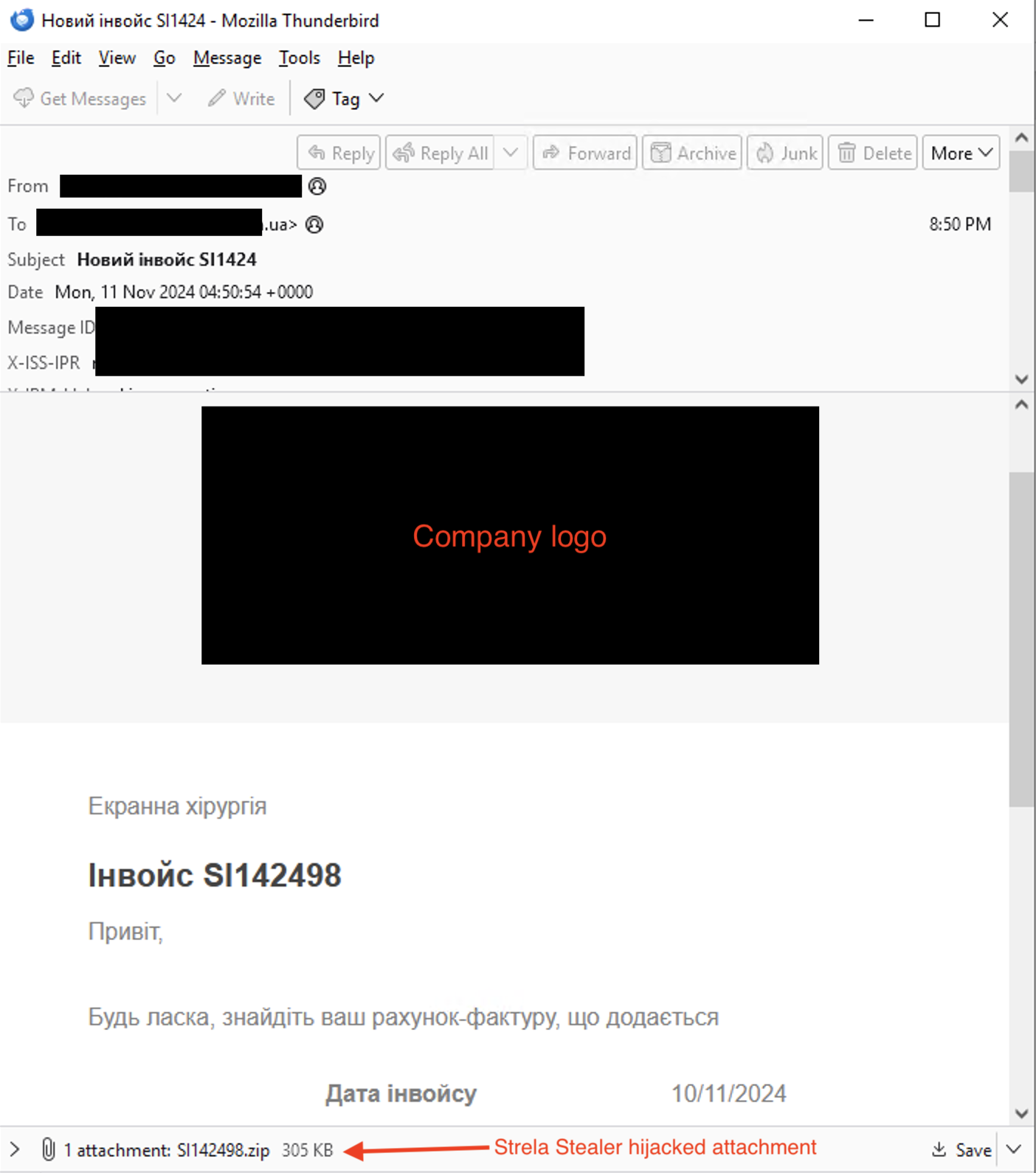
Figure 4 Example of the original stolen email of an invoice targeting Ukraine
Hive0145’s increased volume of delivery using attachment hijacking with a steady supply of freshly stolen emails may suggest the group has adopted automation for harvesting, weaponizing, packaging and sending their phishing emails. The group continues to show a preference for widespread exploitation of Spanish, German and Ukrainian victims throughout Europe.
Evolving techniques
Hive0145 stands out among other malware distributors for their level of effort to adopt increasingly sophisticated methods of delivering Strela Stealer. The level of sophistication reflects on other successful mass distributors of malware such as Emotet, Pikabot and Qakbot, which often led to the deployment of ransomware. Below is a breakdown of notable techniques used by Hive0145 over time, with some being briefly tested and others fully adopted.
Polyglots
The first Strela Stealer campaigns observed by X-Force made use of polyglot files, as first reported in a blog by DCSO (Deutsche Cyber-Sicherheitsorganisation) in late 2022. These files have multiple valid formats and can be parsed by different applications. The same file could be rendered as both HTML to display a decoy invoice as well as be a valid DLL, implementing Strela Stealer. This is a rather uncommon technique for attempting to bypass security solutions.
Signed binaries
Multiple campaigns throughout 2023 made use of valid code signing certificates for the malicious Strela Stealer binaries. For example, campaigns targeting Spanish-speaking victims dating back to April 2023 contained payloads with a valid certificate signed by Tecfinance Informatica E Projetos De Sistemas Ltda, a software company in Brazil.
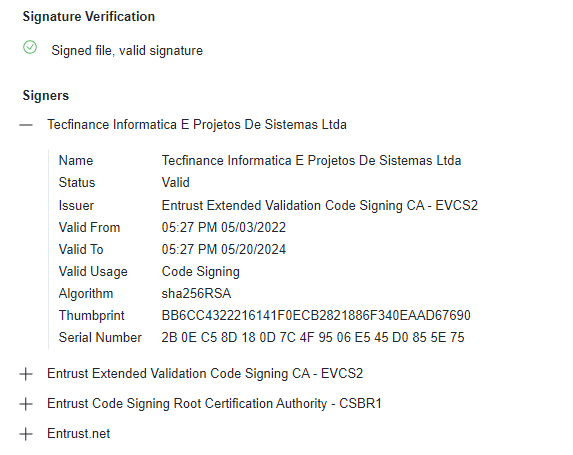
Figure 5 Brazilian company certificate used in 2023 campaigns
On 5 May 2024, X-Force took steps to inform relevant parties of the finding, and the certificate has since been revoked.
Of note, a mid-2023 Italy-targeted campaign used a different certificate:
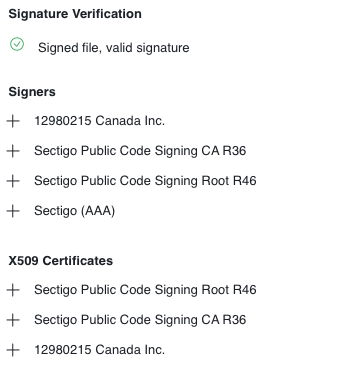
Figure 6 Another stolen certificate used in mid-2023 to target Italian victims
Targeted phishing
Strela Stealer phishing campaigns also tailored filenames to include targeted domain names. The file names are often identical to the name of the organization or company, potentially in an attempt to generate authenticity. The example below is a phishing email from 2023 posing as an invoice or payment receipt.
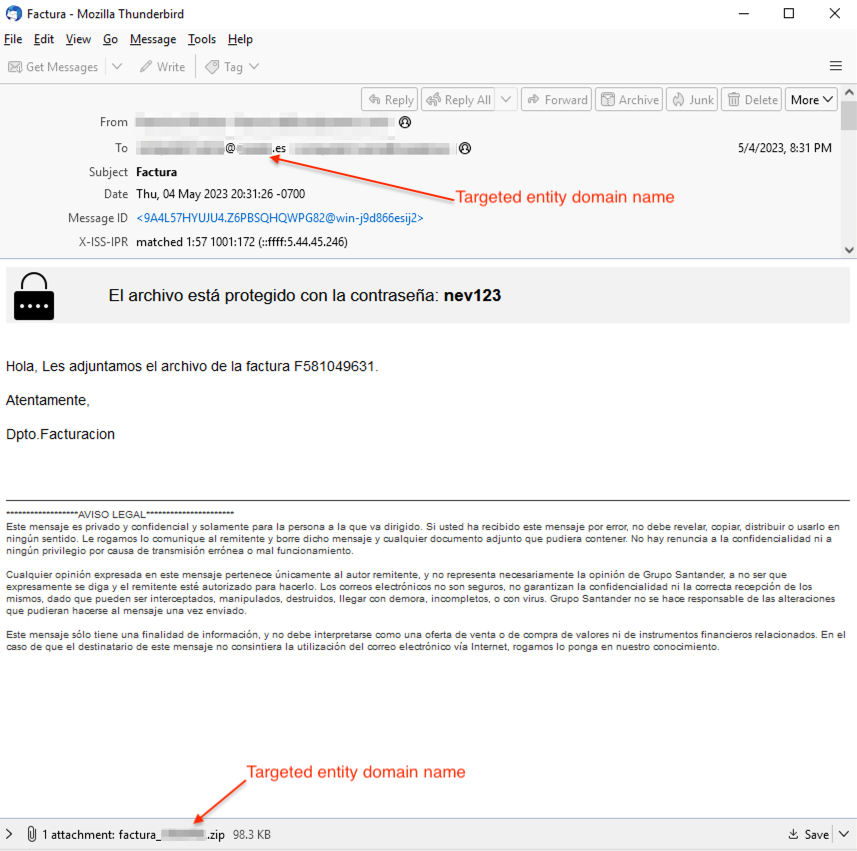
Figure 7 Factura-themed email campaign
As the email suggests, the attachments are encrypted ZIP files, with passwords slightly differing between every email. Threat actors encrypt email attachments since basic email filtering and sandbox solutions often cannot inspect or detonate those files.
Strela Stealer has also used uncommon extensions for their PE executable files such as .com instead of .exe:
Scroll to view full table
This makes use of a condition in Microsoft Windows operating systems where three different extensions can be used to mark a file as executable: .exe, .com, and .pif.
If the content is an executable PE file, Microsoft Windows will run it automatically once opened. By using the more uncommon and unknown extensions, the campaign may evade simple anti-virus solutions or victim suspicion. Earlier campaigns with the same payloads were also observed to make use of the .pif extension.
Packing, obfuscation and crypting
Apart from directly attached ZIP archives with the malicious executables, Strela Stealer campaigns also often use obfuscated scripts such as Batch, JavaScript or PowerShell to download or drop their payload.
Campaigns throughout 2024 mainly relied on these obfuscated scripts to run a PowerShell command to connect to a WebDAV server and download and execute a crypted DLL:
Scroll to view full table
The WebDAV staging servers host a large number of DLLs, with different names and hashes. They appear to have been built using a crypter X-Force identifies as “Stellar Crypter,” which has likely been in use exclusively by Hive0145 since at least May 2023. The malicious binaries identified as “Stellar Loader” contain the encrypted Strela Stealer payload.
Stellar Loader
Stellar Loader is a crypter that has been in use since at least April 2023 and is predominantly a precursor to follow on Strela Stealer payloads. Stellar samples are usually highly obfuscated and make use of techniques such as control flow obfuscation and include large amounts of junk instructions to hinder analysis and signature creation. Stellar’s payload is XOR encrypted and stored in the .data section of the Stellar loader binary. The encrypted payload data is preceded by the XOR key which, in recent samples, consists solely of upper and lowercase letters and can be thousands of characters long.
Upon execution, Stellar Loader decrypts the payload data using XOR and the stored key. The decryption process may also involve an additional round of XOR using a hardcoded single-byte key. As part of the Stellar Loader code’s obfuscation, the decryption algorithm within the code is often expanded to include hundreds of operations. However, the vast majority of these operations cancel each other out, and what appears as a complex algorithm can be reduced down to a simple XOR operation. The screenshot below shows a version of Stellar Loader with minimal obfuscation, where the structure of the loader code and decryption algorithm can be easily seen.
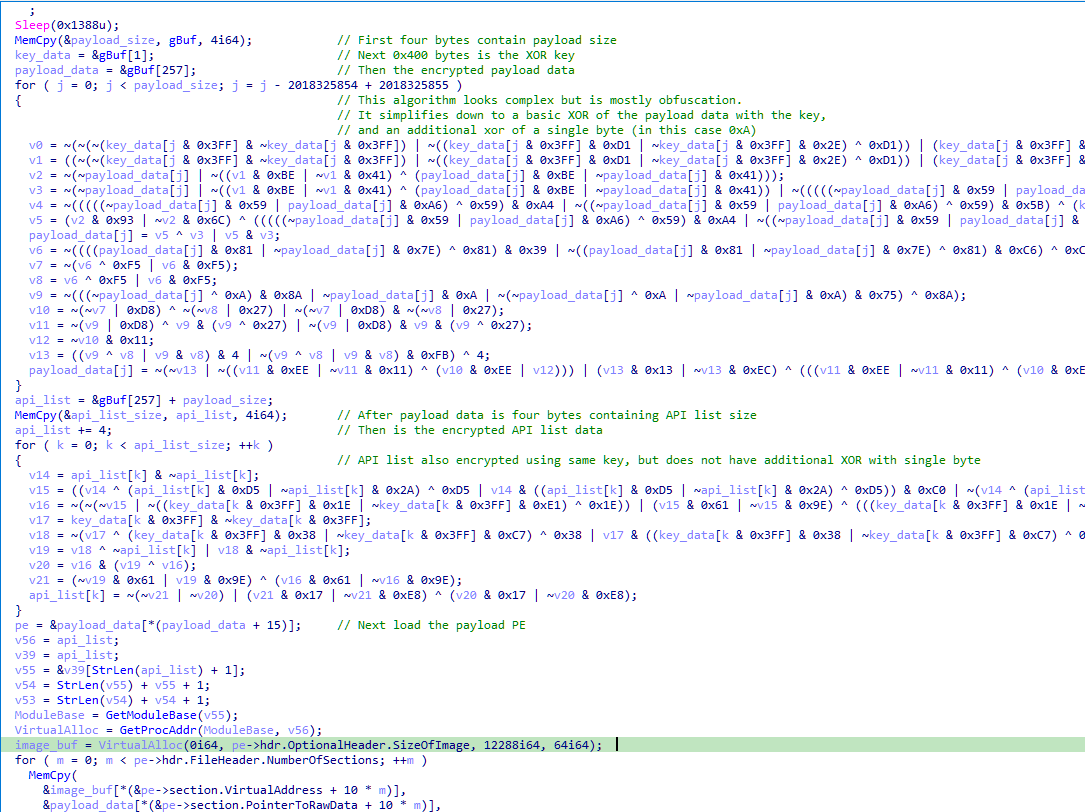
In more recent versions of the loader, the encrypted payload data is followed by an additional encrypted block containing a list of API names required by the loader code, such as VirtualAlloc. The loader decrypts this block using the same key as the payload but without the additional single-byte XOR. The loader can then use the API names in the block to retrieve the corresponding API addresses.
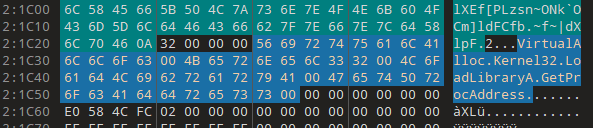
Once the payload and API list have been decrypted, Stellar allocates space in memory using VirtualAlloc and maps the payload PE at the allocated address. It then performs the standard PE loading steps, such as loading its imports and processing any relocation sections (.relocs), and finally, it executes the payload at its entry point address.
Strela Stealer
Strela Stealer changed little in functionality over the past two years. Starting with the initial version reported on by DCSO in late 2022, the main objective of the stealer is to exfiltrate email credentials from two common email clients: Microsoft Outlook and Thunderbird. This is consistent across all variants, however, the latest variant does support more registry keys to search for Microsoft Outlook credentials than prior versions.
Strela Stealer runs two functions tasked with stealing credentials from two email clients:
Scroll to view full table
For Outlook, Strela Stealer specifically looks for the registry values:
- IMAP Server
- IMAP User
- IMAP Password – decrypted using CryptUnprotectData()
The data is formatted and prepended with the string “FF” or “OL” for Thunderbird data and Outlook data, respectively. Next, it is also encrypted with a static XOR key, which represents a GUID string such as:
Scroll to view full table
Then, Strela Stealer sends a POST request for each email client to its hardcoded C2 server:
Scroll to view full table
The response is decrypted via the same XOR key above. Strela Stealer continues to send out POST requests in 1-second intervals until a request fails or it receives back the string “KH” (2023 versions), “ANTIROK” (2024 versions) or “CHOLLIMA” (Nov. 2024 versions).
As of October 2024, Strela Stealer also includes two more exfiltration functions. The first gathers system information on the host and writes it to a file via the command:

The second exfiltration function uses COM objects to enumerate the list of installed applications from the “AppsFolder” (a virtual folder, displayed as “Applications”) on the victim machine.
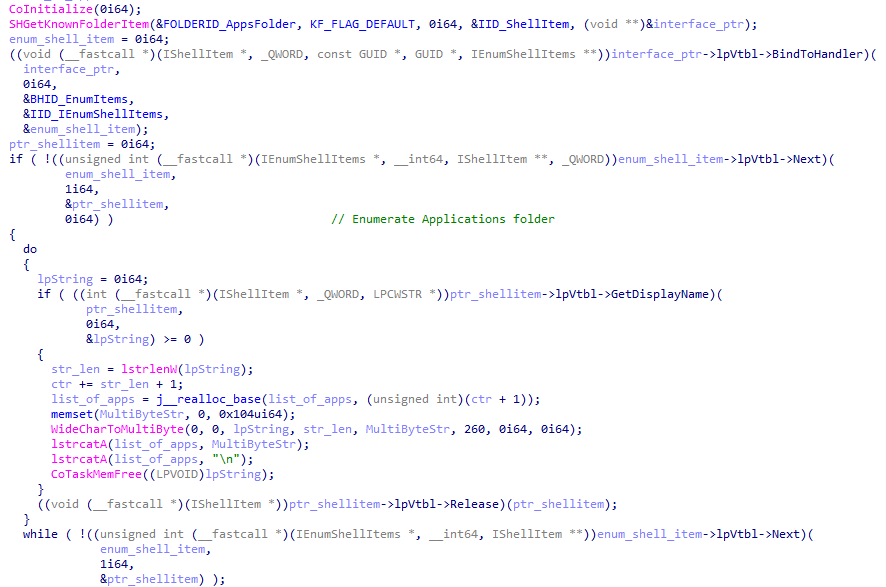
The dropped file, as well as the list of installed applications, are read and encrypted before exfiltration in the same fashion as the others. They are sent to the C2 server with identifiers “SI” and “LA” respectively.
Language checks
Strela Stealer started to implement language checks by verifying the keyboard language on the victim host. Versions throughout 2024 only run on hosts with one of the following keyboard languages:
- Spanish
- German
- Catalan
- Polish
- Italian
- Basque
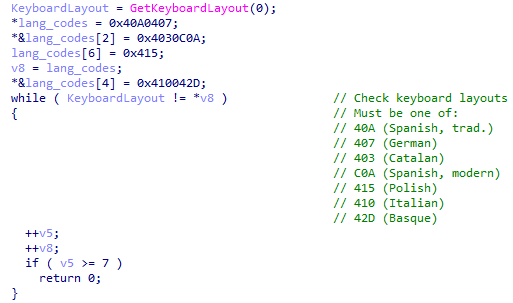
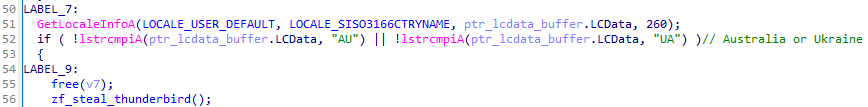
In early November, Hive0145 started distributing stolen Ukrainian emails as well and modified the language verification logic slightly, adding Ukrainian (0x422) to the list of keyboard layouts. In addition, the developers switched to using the GetKeyboardLayoutList API to cover all installed keyboard layouts. If none of the languages match, Strela Stealer has a secondary check comparing the result of the user’s default locale from GetLocaleInfoA against “AU” and “UA”, which are the codes for Australia and Ukraine. It is possible that the developer was not sure of the endianness of the returned value and did not intend to target Australia. Overall, these changes increase the scope of machines available for a Strela Stealer infection.
Previously the malware would display an unobtrusive error message to the user after running in order to not raise any suspicion. It states that the file was corrupted and not able to be opened, in the language depending on the installed keyboard. The latest versions use the more universal error message “Err 100”, which is shown after 5 seconds from the beginning of execution.
.NET variant
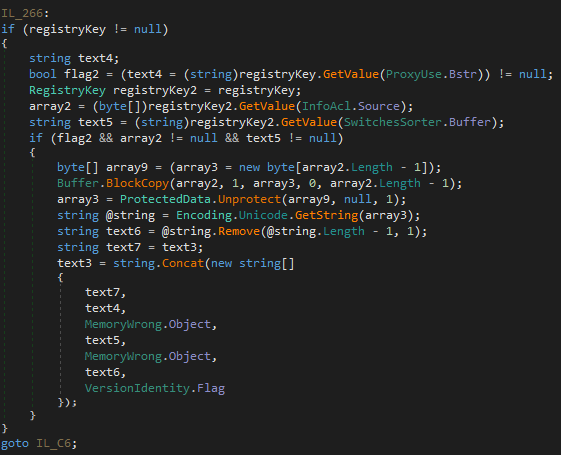
In June 2023, X-Force observed a single Italy-targeted Hive0145 campaign delivering a new Strela Stealer variant that was completely rewritten in .NET. Similar to campaigns before it also made use of valid code signing certificates. Re-implementing malware in a different language shows a significant effort by the threat actor. In order to conceal strings, function names and control flow, the developers made use of the commercial “Aldaray Rummage Obfuscator” for .NET. The screenshot below shows the code used to access and unprotect IMAP credentials from Microsoft Outlook registry keys.
Notably, the commercial obfuscator does include a watermark for the license, which was observed as:
Scroll to view full table
The sample above displays the following error message in Italian:
Scroll to view full table
Hive0145 objectives
Hive0145’s focus on harvesting email credentials sets them apart from other operators of stealer or botnet malware, which are often commoditized and target a broader range of credentials and data, or facilitate follow-on payloads intended for initial access. Hive0145’s use of stolen emails for attachment hijacking is an indicator that a portion of stolen email credentials may be used to harvest legitimate emails for further distribution. Both stolen and actor-created emails used by Hive0145 predominantly feature invoices as themes, which points towards potential financial motivation. It is possible that Hive0145 may sell stolen emails to affiliate partners for the purposes of further business email compromise.
Conclusion:
Hive0145 is a rapidly maturing cyber criminal threat actor and seeks to infect victims with the intention of gaining valid email credentials. Observations suggest that the theft of email credentials, through initial campaigns, led to further theft of valid emails used in subsequent attachment hijacking campaigns. Stela Stealer malware continues to be an effective tool for Hive0145 to extract email credentials.
The wide variety of industries emulated by Hive0145’s email campaigns increases the potential risk of being targeted for commercial organizations throughout Europe. Of note, organizations in Italian, Spanish, German, or Ukrainian-speaking regions may be at more immediate risk of a Hive0145 campaign. X-Force recommends heightened vigilance surrounding email attachments received and careful review of the expected file type delivered.
Recommendations:
X-Force recommends organizations:
- Exercise caution with emails and ZIP archive attachments
- Consider changing the default application for Javascript/JScript/VBScript files to Notepad
- Monitor rundll32.exe processes executing remotely hosted DLLs
- Install and configure endpoint security software
- Update relevant network security monitoring rules
- Educate staff on the potential threats to the organization
Scroll to view full table
More from Threat Intelligence


October 16, 2024
Hive0147 serving juicy Picanha with a side of Mekotio
17 min read – IBM X-Force tracks multiple threat actors operating within the flourishing Latin American (LATAM) threat landscape. X-Force has observed Hive0147 to be one of the most active threat groups operating in the region, targeting employee inboxes at scale, with a primary focus on phishing and malware distribution. After a 3-month break, Hive0147 returned in July with even larger campaign volumes, and the debut of a new malicious downloader X-Force named “Picanha,” likely under continued development, deploying the Mekotio banking trojan. Hive0147…


September 26, 2024
FYSA – Critical RCE Flaw in GNU-Linux Systems
2 min read – Summary The first of a series of blog posts has been published detailing a vulnerability in the Common Unix Printing System (CUPS), which purportedly allows attackers to gain remote access to UNIX-based systems. The vulnerability, which affects various UNIX-based operating systems, can be exploited by sending a specially crafted HTTP request to the CUPS service. Threat Topography Threat Type: Remote code execution vulnerability in CUPS service Industries Impacted: UNIX-based systems across various industries, including but not limited to, finance, healthcare,…


July 26, 2024
Hive0137 and AI-supplemented malware distribution
12 min read – IBM X-Force tracks dozens of threat actor groups. One group in particular, tracked by X-Force as Hive0137, has been a highly active malware distributor since at least October 2023. Nominated by X-Force as having the “Most Complex Infection Chain” in a campaign in 2023, Hive0137 campaigns deliver DarkGate, NetSupport, T34-Loader and Pikabot malware payloads, some of which are likely used for initial access in ransomware attacks. The crypters used in the infection chains also suggest a close relationship with former…
Topic updates
Get email updates and stay ahead of the latest threats to the security landscape, thought leadership and research.
Subscribe today
Source: https://securityintelligence.com/x-force/strela-stealer-todays-invoice-tomorrows-phish