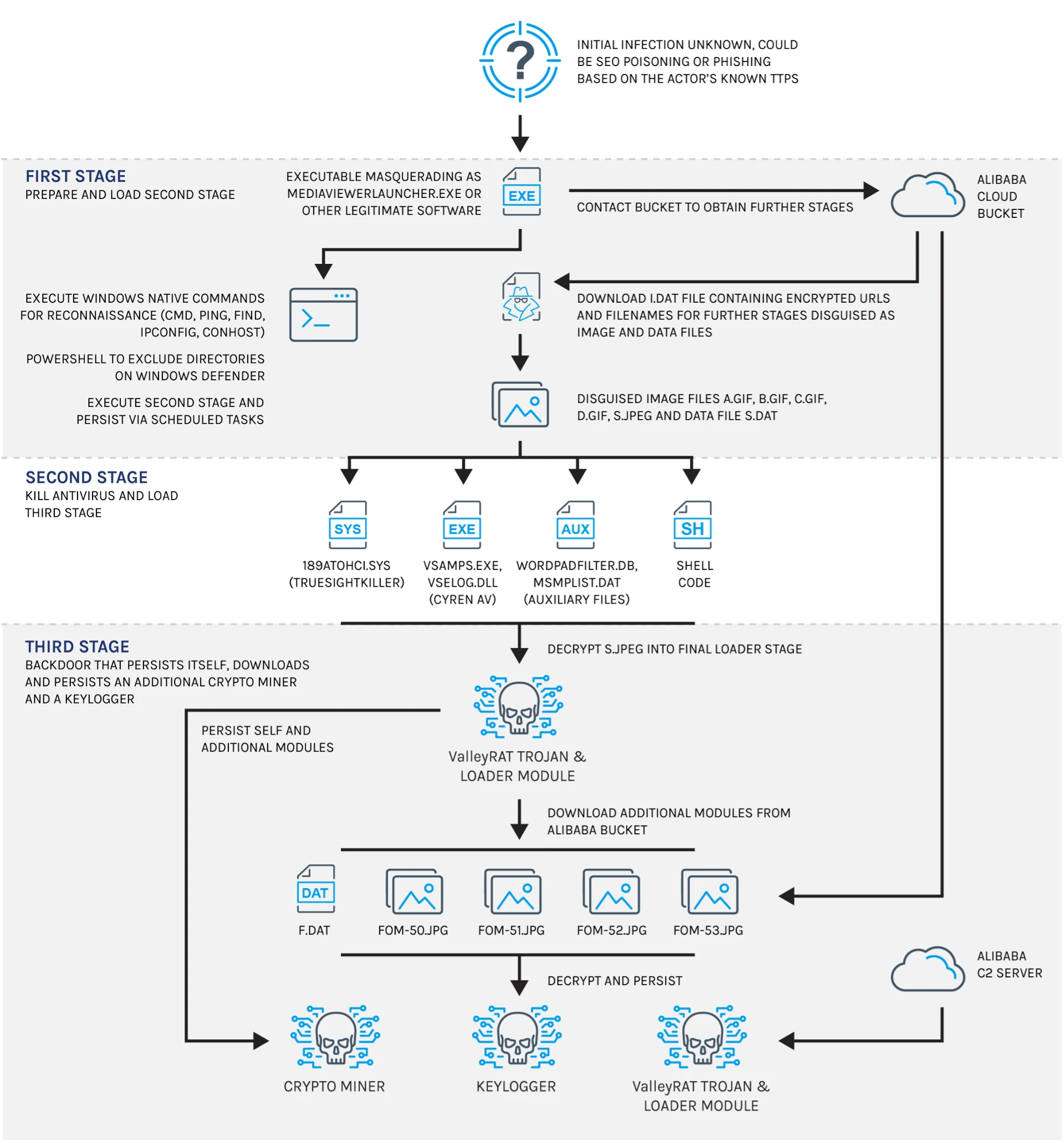
The article discusses a campaign by the China-based Advanced Persistent Threat (APT) group Silver Fox, which exploited vulnerabilities in Philips DICOM viewers to deploy malware such as a Remote Access Tool (RAT), keyloggers, and crypto miners targeting healthcare organizations. The healthcare sector remains a significant target for cyberattacks, necessitating robust security measures. Affected: healthcare sector, Philips DICOM viewers
Keypoints :
- Silver Fox APT exploits Philips DICOM viewers to deploy malware.
- Malware includes ValleyRAT (RAT), keyloggers, and crypto miners.
- HDOs are recommended to avoid downloading from untrusted sources and implement network segmentation.
- Campaign tactics involve phishing and watering hole attacks.
- Healthcare organizations are increasingly targeted due to vulnerabilities in medical applications.
- The identified malware cluster includes trojanized software and demonstrates advanced evasion techniques.
- Silver Fox has shown an evolution in tactics, targeting diverse sectors beyond healthcare.
- Initial infection stages utilize SEO poisoning and phishing methodologies.
- Malicious payloads utilize encrypted communications with command-and-control (C2) servers.
- IoCs for the campaign have been identified and are available for monitoring purposes.
MITRE Techniques :
- Tactic: Initial Access [TA0001] – Phishing (T1566): Silver Fox utilized phishing emails to distribute the trojanized DICOM viewer.
- Tactic: Execution [TA0002] – Command and Scripting Interpreter (T1059): PowerShell usage for executing commands and evading detection.
- Tactic: Persistence [TA0003] – Scheduled Task/Job (T1053): Creates Windows scheduled tasks to maintain persistence after reboots.
- Tactic: Privilege Escalation [TA0004] – Exploitation of Vulnerability (T exploits known vulnerabilities in applications).
- Tactic: Defense Evasion [TA0005] – Obfuscated Files or Information (T1027): Malware utilizes encryption and obfuscation to resist detection.
- Tactic: Impact [TA0005] – Resource Hijacking (T1496): Deployment of a crypto miner for financial gain on victim systems.
Indicator of Compromise :
- [File] MediaViewerLauncher.exe (SHA256: abd903bad26d190210954cac00f5d96d43fcb4a89823337e1669977b50a122f8)
- [File] MediaViewerLauncher.exe (SHA256: 6986a9a81b945e9ccfc434287bd9efd1daacc616a3104d05fd810b33d4d5d3f2)
- [File] i.dat (SHA256: 31adb4043339320c360d43686ace3736bac87df27dc309c7c544820acdb34a93)
- [File] OKSave.exe (SHA256: 48F258037BE0FFE663DA3BCD47DBA22094CC31940083D9E18A71882BDC1ECDB8)
- [Domain] vien3h.oss-cn-beijing.aliyuncs.com (Alibaba Cloud bucket hosting the malware)
Full Story: https://www.forescout.com/blog/healthcare-malware-hunt-part-1-silver-fox-apt-targets-philips-dicom-viewers/