In September 2024, Russian companies faced a series of coordinated attacks linked to two hacktivist groups, Head Mare and Twelve. The investigation revealed a blend of new and familiar tactics, techniques, and procedures (TTPs) employed in these attacks, with indications of collaboration and tool-sharing between the groups. Key tools included the CobInt backdoor and the PhantomJitter backdoor, while traditional exploits like phishing and software vulnerabilities were also utilized. Affected: Russian companies, cyber environment
Keypoints :
- A series of attacks targeting Russian companies revealed tactics from hacktivist groups Head Mare and Twelve.
- Evidence suggests potential collaboration and shared tools between Head Mare and Twelve.
- New tools utilized include CobInt and PhantomJitter, alongside existing tools like mimikatz and ADRecon.
- Attacks refined to exploit trusted contractor relationships, along with software vulnerabilities.
- Persistence methods evolved, with attackers creating privileged local users on servers.
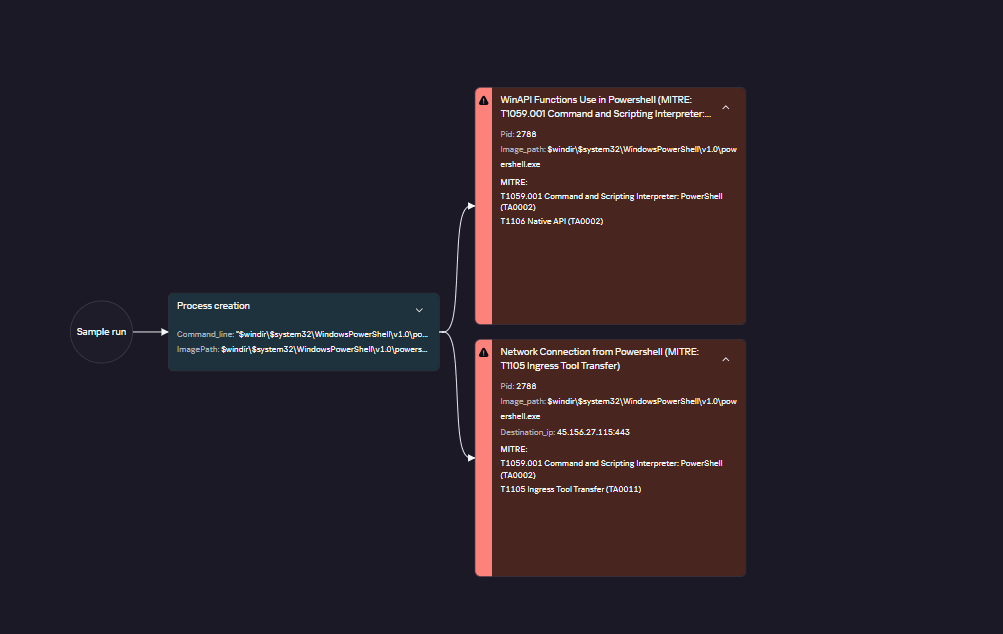
- Masquerading techniques were employed to evade detection.
- Data exfiltration executed using rclone, exploiting specific file paths and extensions.
- Final encryption of data was performed using LockBit 3.0 and Babuk ransomware.
- Indicators of compromise link back to shared command-and-control servers and overlapping infrastructure.
MITRE Techniques :
- T1199 – Trusted Relationship: Exploited trusted relationships with contractors to gain access.
- T1078 – Valid Accounts: Used compromised accounts to execute commands with elevated privileges.
- T1655 – Masquerading: Renamed utility executables to imitate legitimate system files for evasion.
Indicator of Compromise :
- [Domain] 360nvidia.com
- [IP] 45.156.27.115
- [IP] 45.156.21.148
- [IP] 185.158.248.107
- [File Path] C:ProgramDataMicrosoftDrivemcdrive.ps1
Full Story: https://securelist.com/head-mare-twelve-collaboration/115887/
Views: 29