
Today, I am interested in exploring one of the hacked websites.
Notified by: MrAstra
Date: Sat, 14 Dec 2024 04:59:30 +0000
URL: https://tourism.angelescity.gov.ph/deface.html
Country: Philippines
Sector: Tourism — This sector encompasses services related to travel, hospitality, and leisure activities, promoting destinations and experiences for visitors.
The Hacker embedded the web page named ‘deface.html’ to display a hacking message.
I used a tool from the following link https://www.hendryadrian.com/dashboard/ > Free Tools > Page Analyzer, to view the elements of the web page.

Alternatively, we can also analyze the page using the browser’s developer tools, although this may be time-consuming. Result:

There is nothing suspicious from the link.

However, from the images, there is evidence of a backdoor and web shell being implanted.


The backdoor was implanted on December 13th at 22:25
The hack occurred on the -1 day this post was made, and the website owner has already been notified.

What can we find ?
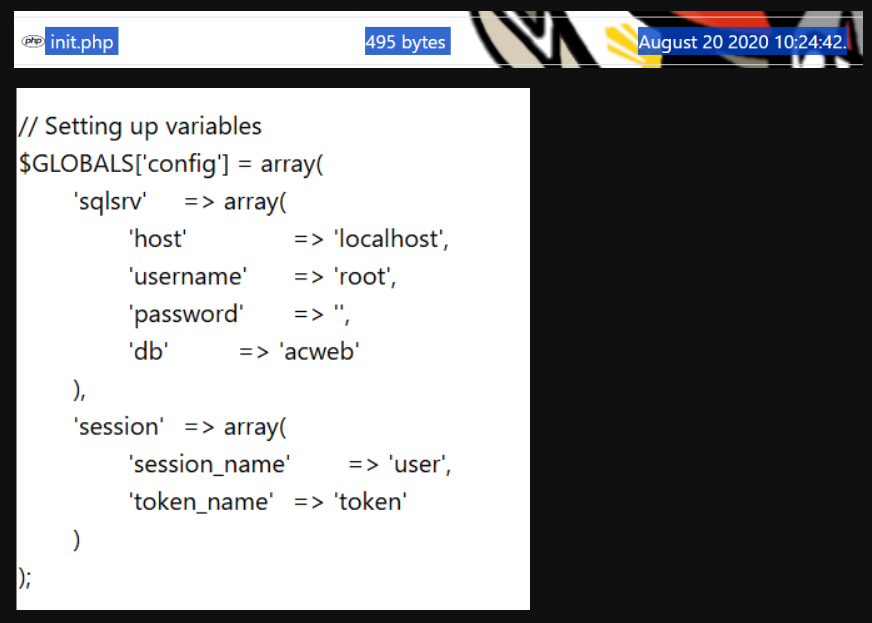
1. Weak Configuration
2. This encoded PHP script was found in all folders.

3. Missing Page
I am not sure if the entry point is from this page (https://tourism.angelescity.gov.ph/contact.php), but the contact form does not work because contact_process.php is missing.

4. This site is simple, but it makes excessive use of JavaScript.





5. Code Weakness.
This code found in core/init.php uses PHP’s spl_autoload_register function to automatically load classes without having to manually include the class files using require or include.

This code checks if a file corresponding to the provided class name exists in the classes directory. If it does, the file is included.
However, one of the main risks associated with autoloading is file inclusion vulnerabilities. If user input is not properly validated and is allowed to influence the class name, an attacker could exploit this to include unwanted files on the server, potentially leading to security breaches. It’s essential to sanitize and validate any user input that affects file inclusion to mitigate these risks.
Conclusion
This analysis revealed the presence of a backdoor and web shell, indicating a serious security breach. Key issues contributing to this vulnerability included weak configuration settings and a missing contact form page that suggests inadequate maintenance.
This exploration exposed critical weaknesses in the site’s coding practices, particularly the use of PHP’s autoloading feature without proper validation of user input, thereby potentially allowing attackers to exploit the server. The risks associated with insecure database access further highlight the need for robust coding standards and security protocols to prevent unauthorized access and manipulation.

Views: 0