GorillaBot is a newly discovered Mirai-based botnet known for launching over 300,000 attacks in more than 100 countries. This botnet employs sophisticated evasion techniques and secure communication methods with its command-and-control servers. It presents a significant threat to various sectors, highlighting the urgent need for cybersecurity responses. Affected: telecommunications, financial institutions, education sector
Keypoints :
- GorillaBot is based on Mirai’s code but includes custom encryption and evasion techniques.
- It has been linked to over 300,000 attacks across more than 100 countries.
- The botnet utilizes raw TCP sockets for command-and-control communication.
- It employs anti-debugging and anti-analysis techniques to detect its operating environment.
- The malware authenticates to its C2 server with a SHA-256-based token.
- Commands are hashed and passed to a Mirai-style function for execution.
MITRE Techniques :
- T1071.001 – Application Layer Protocol: GorillaBot utilizes raw TCP sockets for C2 communication.
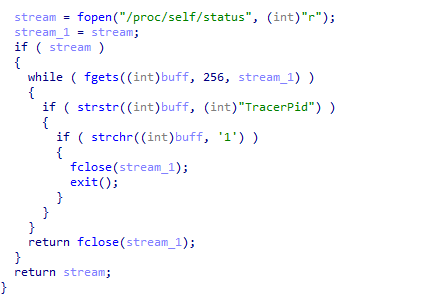
- T1070.001 – Indicator Removal on Host: The bot checks for debugging tools and exits in suspicious environments.
- T1583.001 – Acquire Infrastructure: The bot performs various checks to confirm its environment as legitimate.
- T1040 – Network Sniffing: Utilizes encrypted communication with C2 servers.
- T1553.001 – Credentials from Password Stores: SHA-256-based authentication is used to authenticate with C2 servers.
Indicator of Compromise :
- [Hash] b482c95223df33f43b7cfd6a0d95a44cc25698bf752c4e716acbc1ac54195b55
- [URL] http://193[.]143[.]1[.]70
- [URL] http://193[.]143[.]1[.]59
Full Story: https://any.run/cybersecurity-blog/cybersecurity-blog/gorillabot-malware-analysis/