### #PhishingExploitation #CloudTrustManipulation #SocialEngineeringTactics
Summary: A recent phishing campaign has demonstrated how attackers exploit trusted platforms like Google Docs and Weebly to bypass security measures and deceive victims in the telecommunications and financial sectors. By embedding malicious links and creating fake login pages, these threat actors have refined their tactics to enhance the credibility of their schemes.
Threat Actor: Financially motivated threat actors | financially motivated threat actors
Victim: Telecommunications and financial sectors | telecommunications and financial sectors
Key Point :
- Attackers used Google Docs to deliver phishing links, effectively bypassing standard email filters.
- Fake login pages hosted on Weebly mimicked well-known brands to deceive victims into providing sensitive information.
- Legitimate tracking tools were embedded to monitor user interactions, allowing attackers to refine future phishing attempts.
- SIM swapping attacks were initiated by harvesting telecom credentials, enabling the bypass of SMS-based MFA protections.
- Recommendations include adopting app-based MFA, proactive monitoring, and user education to combat such sophisticated campaigns.
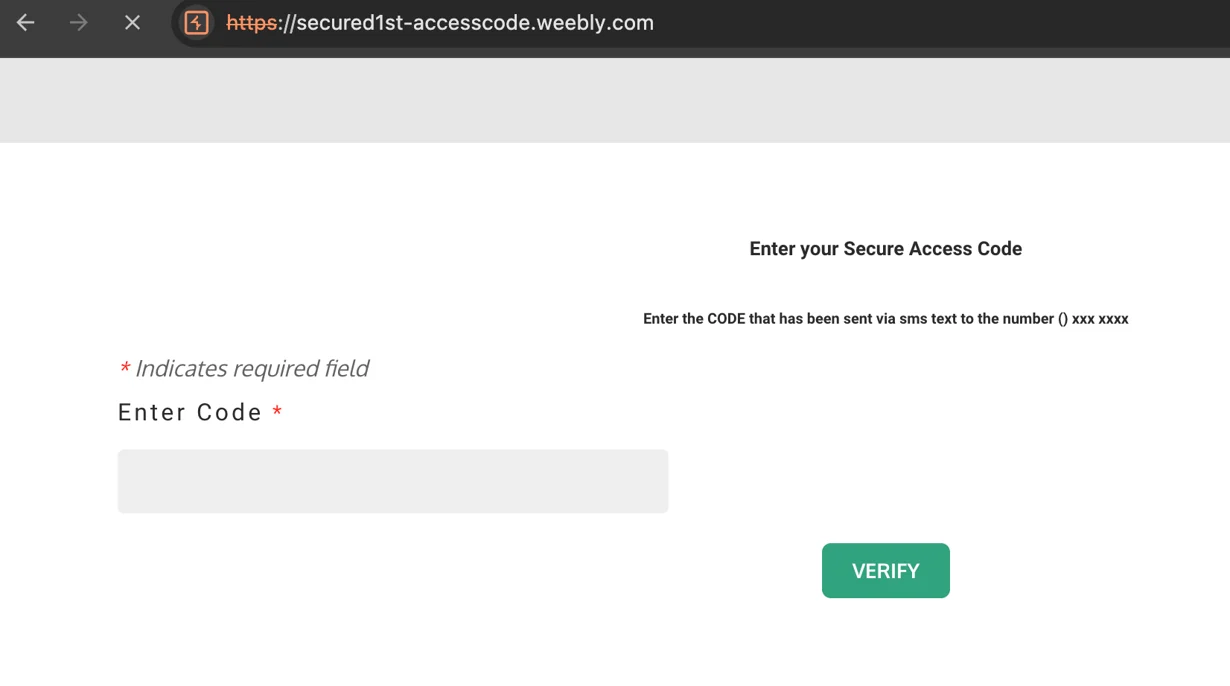
A recent phishing campaign, uncovered by EclecticIQ researchers, highlights the lengths attackers will go to exploit trusted platforms and infrastructure. Financially motivated threat actors targeted the telecommunications and financial sectors using Google Docs to deliver phishing links and Weebly to host fake login pages. This strategic combination of legitimate platforms allowed attackers to bypass standard email filters and endpoint defenses, enhancing the credibility of their malicious schemes.
The attackers’ approach relied on embedding malicious links in Google Docs presentations, which redirected victims to phishing sites hosted on Weebly. EclecticIQ’s report explains, “By using Google’s trusted domain for initial delivery, attackers bypassed standard email filters and endpoint protections, leveraging reputable platforms to evade detection and increase user trust.”
On Weebly, the phishing pages mimicked the login screens of prominent brands, including AT&T and financial institutions in the U.S. and Canada. These carefully tailored pages aimed to deceive victims into entering their login credentials, multi-factor authentication (MFA) codes, and other sensitive information.
By leveraging Google Docs and Weebly, attackers were able to obscure their malicious intent. The report highlights, “Google Docs-hosted files are less likely to be flagged as malicious from anti phishing tools compared to traditional phishing methods.” Similarly, the legitimate appearance of Weebly-hosted domains further reduced scrutiny.
Adding to the campaign’s sophistication, attackers embedded legitimate tracking tools like Sentry.io and Datadog to monitor user interactions. This allowed them to gather metrics such as timestamps, IP addresses, and geolocation data. “These insights enabled attackers to refine their phishing attempts, tailoring future campaigns for greater success,” the report stated.
In some cases, the attackers went beyond phishing. By harvesting telecom credentials, they initiated SIM swapping attacks to intercept SMS-based MFA codes. This technique enabled them to bypass traditional MFA protections and maintain prolonged access to compromised accounts. The report stresses the importance of adopting app-based or hardware-based MFA to mitigate these risks.
EclecticIQ emphasizes the need for robust security measures to counter such sophisticated campaigns. Key recommendations include:
- Enhanced MFA Solutions: Replace SMS-based MFA with app-based or hardware-based alternatives to mitigate SIM-swapping risks.
- Proactive Monitoring: Use advanced detection tools to identify malicious activity on legitimate platforms like Google Docs and Weebly.
- User Education: Train employees to recognize phishing tactics, especially those exploiting trusted platforms.
As EclecticIQ’s report concludes, “This deliberate shift toward leveraging cloud-based collaboration tools as entry points makes detection more challenging, allowing attackers to broaden their scope beyond initial targets.”
Related Posts:
Source: https://securityonline.info/google-docs-and-weebly-weaponized-in-new-phishing-scheme