The article discusses the evolution of the Gayfemboy botnet, which has transformed from a basic Mirai variant into a sophisticated threat utilizing multiple vulnerabilities, including 0day exploits. It highlights the botnet’s growth, its active presence, and the aggressive tactics employed by its developers. Affected Platform: Mirai, Four-Faith Industrial Router, Neterbit Router, Vimar Smart Home Device
Keypoints :
- Gayfemboy botnet was first discovered in February 2024.
- Initially, it was a simple UPX-packed variant of Mirai.
- Developers rapidly iterated on the botnet, integrating Nday and 0day vulnerabilities.
- As of November 2024, it exploits vulnerabilities in Four-Faith Industrial Routers and other devices.
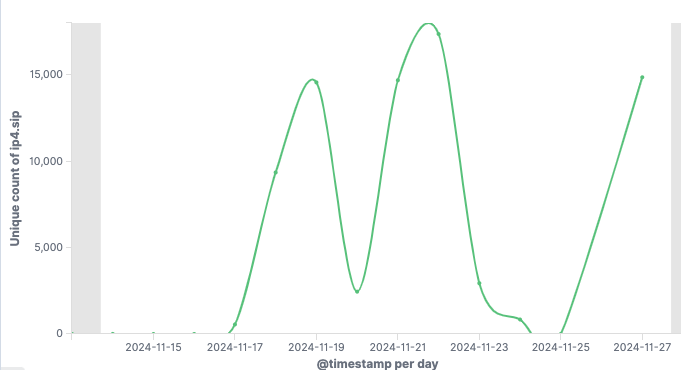
- Gayfemboy has over 40 active groups with more than 15,000 daily active nodes.
- The botnet has targeted various industries globally, with significant activity in China, the US, and Europe.
- It has engaged in DDoS attacks against entities that registered its C2 domains.
- Gayfemboy utilizes over 20 vulnerabilities and Telnet weak passwords for propagation.
- It has a unique command structure and has modified the Mirai codebase.
MITRE Techniques :
- T1071.001 – Application Layer Protocol: Utilized HTTP for command and control communication.
- T1210 – Exploitation of Remote Services: Exploited vulnerabilities in routers and smart devices.
- T1499 – Endpoint Denial of Service: Conducted DDoS attacks against registered domains.
- T1203 – Exploitation for Client Execution: Leveraged 0day vulnerabilities for propagation.
- T1070.001 – Indicator Removal on Host: Attempts to hide malicious processes from system monitoring.
Indicator of Compromise :
- [IP Address] 123.249.103.79
- [IP Address] 176.97.210.250
- [IP Address] 198.98.54.234
- [Domain] meowware[.]ddns[.]net
- [File Hash] 3287158c35c93a23b79b1fbb7c0e886725df5faa
- Check the article for all found IoCs.
Full Research: https://blog.xlab.qianxin.com/gayfemboy/
Views: 2