One of the primary propagation methods for Darkgate is phishing emails. By hijacking email accounts, distributing malicious attachment and it propagate itself to a wider network of potential victims. Darkgate uses some of the most common attachment filetypes such as XLSX, HTML and PDF. It is often designed to be stealthy and persistent, making it challenging to detect and remove. It may result in the loss of personal data, financial loss through fraud or extortion, and compromise of sensitive information.
This post provides a detailed examination of a recent Darkgate campaign identified by Forcepoint’s X-Labs research team. The campaign commences with the initiation of attacks via a compromised email, featuring an invoice purportedly from ‘Intuit Quickbooks’ in PDF format. It prompts users to install Java to view the invoice, providing a link. Upon clicking the link, users are redirected to a geofenced URL where they inadvertently download the subsequent stage payload.
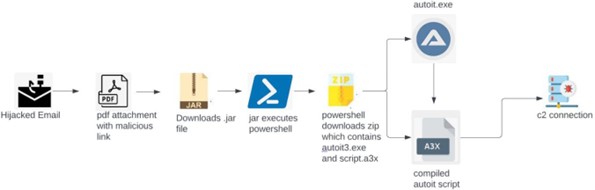
Image 1 – Attack Chain
Through a comprehensive analysis of a suspicious PDF file named “may-document_[number].pdf”, it reveals an invoice document containing an XObject large image with an embedded hyperlink. Upon user interaction with the hyperlink, it triggers the download of a malicious .jar (Java Archive) file.
The URLs associated with this malicious activity follow a historical pattern, featuring domains and single paths reminiscent of those previously utilized by QakBot threat actors.
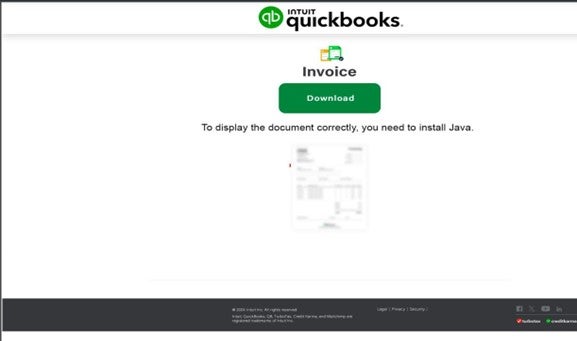
Image 2 – PDF attachment
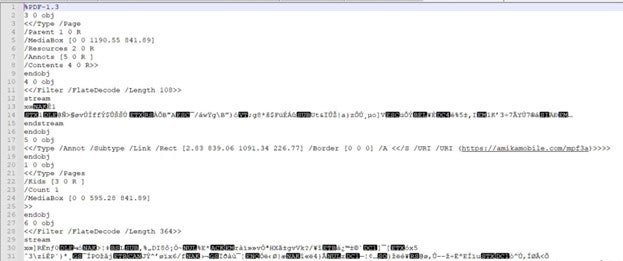
Image 3 – Static view of URL inside PDF
When inspecting the subsequently downloaded JAR file using JD-GUI, it revealed a .PNG file and a
<random-name>.class file. Within this class file, there exists a Java function aiming to download a .ZIP file to the directory ‘C:\Downloads\’ through an obfuscated ‘curl.exe’ command. Upon successful download of the ZIP file, it triggers PowerShell to extract its contents using the ‘expand-archive’ command.
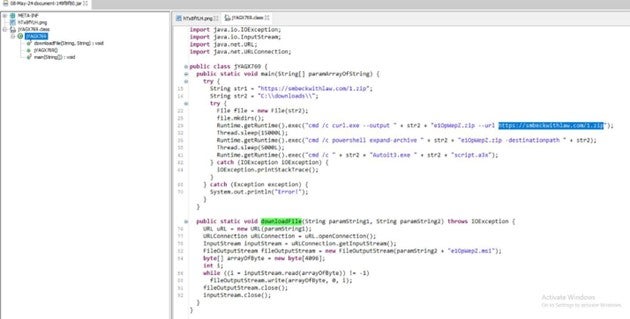
Image 4 – JAR Class file
The JAR’s class file additionally features another function designed to download and store files with the
.MSI extension. Upon extraction of the downloaded ZIP file, it reveals ‘autoit3.exe’ and a compiled AutoIt script with the ‘.a3x’ extension. Subsequently, the JAR file executes an obfuscated ‘cmd /c’ command to run this compiled AutoIt script. It’s noteworthy that DarkGate has a history of leveraging AutoIt in its previous campaigns. The script appears to have been compiled with AutoIt version 3.26 or later, as indicated by the header ‘AU3!EA06’.
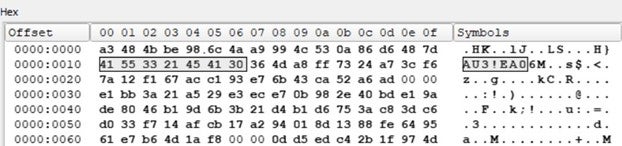
Image 5 – Autoit compiled script
The decompiled script reveals obfuscated AutoIt functions such as BITXOR and BinaryToString(), which are employed to obscure the script’s functionality. It attempts to store a large stream of data in a local variable through concatenation operations. Additionally, DLLSTRUCTCREATE() and DLLSTRUCTSETDATA() functions are utilized to create a structure and load bytes into memory, likely for manipulation or interaction with system resources.
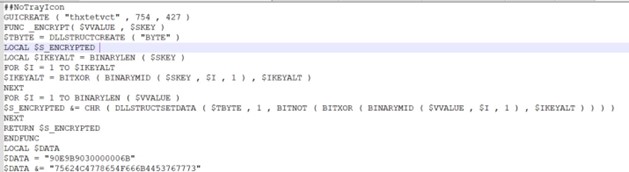
Image 6.1 – Decompiled autoit
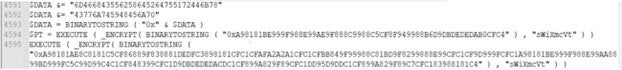
Image 6.2 – Decompiled autoit
This malicious autoit script further executes actual shell code in memory and perform connection with remote C&C botnet server.
Conclusion:
The Darkgate campaign, dissected by the Forcepoint research team, begins with phishing emails posing as QuickBooks invoices, urging users to install Java. Clicking the embedded link leads to a geofenced URL, unwittingly downloading a malicious JAR file. Further analysis uncovers a complex structure within the JAR file, including commands to download additional payloads, such as an AutoIt script. This script compiled with AutoIt, employs obfuscation techniques to conceal its functionality, executing shell code and establishing connections with remote Command and Control servers. The campaign’s use of historical URL patterns and sophisticated malware techniques underscores its advanced nature and highlights the ongoing threat posed by Darkgate.
Protection statement
Forcepoint customers are protected against this threat at the following stages of attack:
- Stage 2 (Lure) – Malicious attachments associated with these attacks are identified and blocked.
- Stage 5 (Dropper File) – The dropper files are added to Forcepoint malicious database and are blocked.
- Stage 6 (Call Home) – Blocked C&C domain
IOCs
Initial Stage URLs:
- afarm[.]net/uvz2q
- affixio[.]com/emh0c
- affiliatebash[.]com/myu0f
- afcmanager[.]net/jxk6m
- adventsales[.]co[.]uk/iuw8a
- amikamobile[.]com/ayu4d
- adztrk[.]com/ixi7r
- aerospaceavenue[.]com/cnz8g
- amishwoods[.]com/jwa4v
Second stage URL:
- smbeckwithlaw[.]com/1[.]zip
C2:
- kindupdates[.]com
https://www.forcepoint.com/blog/x-labs/phishing-script-inside-darkgate-campaign