The evolution of the ransomware landscape has seen a shift from the more traditional approach involving Windows payloads to ones targeting other platforms, most notably Linux. In this shift, ransomware operators are shortening the time gaps between different payload releases and bringing feature parity across diverse platforms.
Strategically dipping into code from well known ransomware families such as Conti, Babuk, or Lockbit, ransomware operators are reusing and modifying codebases to create novel attack techniques. As more cases of this come to light, it is critical for security teams to stay vigilant and adaptive in their defenses.
In this post, we highlight several recent ransomware families that have unleashed their Linux/ESXi-focused payloads shortly upon launch of their operations. Understanding the capabilities of these payloads is an important step in gauging future risk and key to enabling security teams to prepare their defenses accordingly.

The Rise of the Linux Ransomware Threat
Looking back just four or five years, prominent ransomware operators’ primary focus was devices running Windows. Non-Windows flavors of their payloads required extra skill and time to develop and release. Such is not the case now, with languages like Rust and Go allowing for quick multi-platform ports for eager malware developers.
The state of the threat landscape as we see it today includes ransomware operators releasing payloads for multiple platforms simultaneously. In this approach, there are no longer significant gaps of time between the usual Windows-targeted payloads and the Linux-focused and/or ESXi payloads. In addition, it is now standard for payloads across platforms to exhibit feature parity. Out of the gate, these Linux and ESXi-focused lockers contain all the requisite functionality of their Windows counterparts.
Modern ransomware operators are also increasingly reusing builders and code (sometimes leaked) or modifying codebases to suit their needs while maintaining the primary code as a model. Security researchers note that the primary families from which these have been derived are Conti, Babuk, LockBit. These variants are capable of targeting both Linux and VMWare ESXi environments, with the aim of encrypting the virtual machines (VMs) hosted on ESXi servers that are often crucial to business operations and services.
Typically, attackers exploit vulnerabilities in ESXi, weak credentials, or other security vulnerabilities to gain access to the virtualized environment. The ability to efficiently target and encrypt virtual machines is highly attractive to ransomware operators. Fully-virtualized infrastructure can be encrypted and compromised in minutes with the right, and robust, payloads.
MONTI Locker
MONTI locker has a history going back to mid-2022, with a number of attacks on VMware ESXi servers.
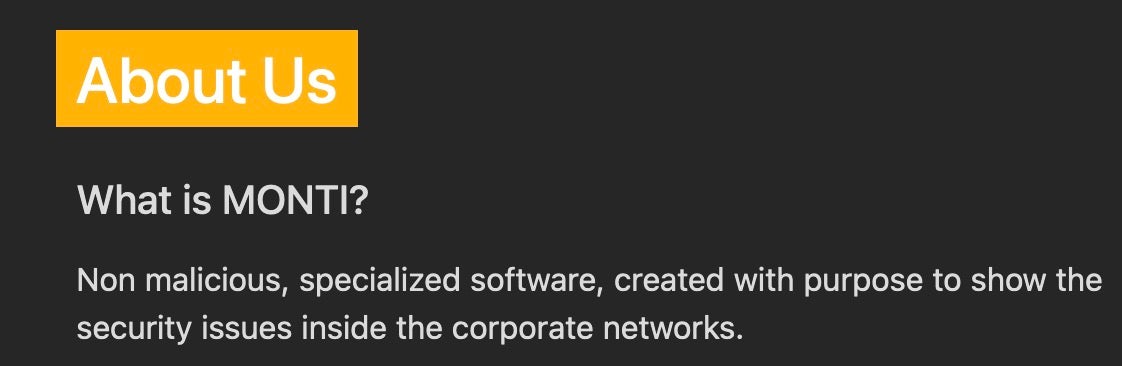
The most recent versions of MONTI ESXI Ransomware support a variety of command-line arguments, many of which are carryovers from Conti, from which MONTI Locker borrows code. The operators behind MONTI Locker have shown signs of moving in a more bespoke direction as of late, however.
Researchers recently documented a sample that appears to shed the old Conti-based encryptor along with a few of the command-line parameters. These more recent samples have removed the --size, --log and --vmlist parameters.
Available command-line parameters for MONTI Locker include:
| Argument | Function |
| — path | Path to file / volumes |
| –whitelist | List of virtual machines to skip (can accept .txt file input) |
| –vmkill | Toggle termination of virtual machines |
| –vmlist | Accepts a list (.txt file) of virtual machine names |
| –detach | Detach from the screen/terminal |
| –log | Create a log file |
| –prockiller | Toggles termination of processes with handles open on targeted files (for encryption) |
| –size | Partial file encryption, toggles percentages between 10 and 50 |
| –world-id= | Targeting specific World IDs within VMWare |
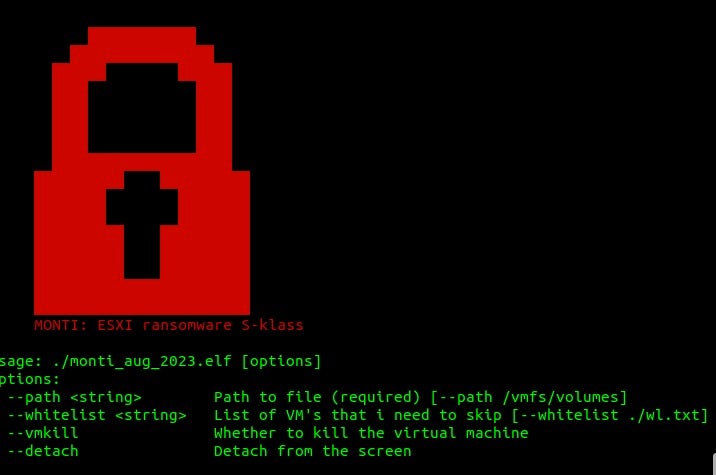
Also of note is MONTI Locker’s ability to update the MOTD file (Message of the Day) on affected servers. This file (/etc/motd) controls what users see upon login to vCenter, for example. Post-infection, servers encrypted with MONTI Locker will display the configured ransom note.
MONTI Locker’s overall attack volume is lower than some of the other threats in this post. Their targeting is quite selective, and they are adept at playing the long game when it comes to the overall lifespan of their infection campaigns. As we will note with Akira, it will be interesting to see how MONTI Locker evolves outside of Conti as well as how quickly those changes will come to fruition.
Akira Ransomware
Linux variants of the Akira ransomware family have been observed since June of 2023 though the broader operations go back to April. Initial delivery of Akira ransomware occurs via exploitation of vulnerable, publicly available, services and applications. The group has also been known to target weaknesses in multi factor authentication (or a lack there-of) . Akira attackers do not discriminate when it comes to victimology. As of this writing, they have targeted educational institutions as well as those in the financial, manufacturing, real estate, and medical industries.

Traditionally, Akira ransomware payloads are borrowed from Conti. The Linux versions of Akira ransomware use the Crypto++ library to handle encryption on devices. Akira provides a short command set that does not include any options to shutdown VMs prior to encryption. They do, however, allow the attacker some control over speed of encryption and the likelihood of practical recovery by the victim via the -n parameter. The greater that value, the more of the file gets encrypted, meaning slower speed and a lower likelihood of the victim recovering without proper decryption tools.
Available command-line parameters for Akira include:
| Argument | Function |
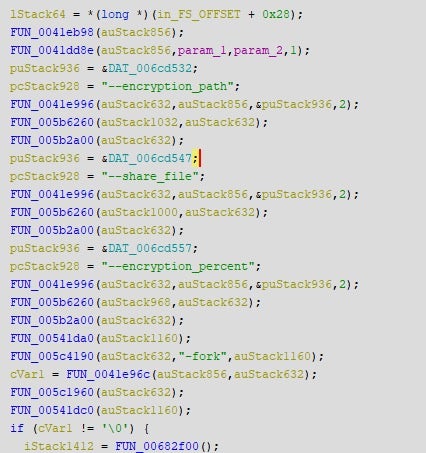
| — encryption_path, -p | Path to file / folders |
| –encryption_percent, -n | Partial encryption, sets percentage of file to be encrypted |
| –share_file, -s | Shared-drive path (on network) to be encrypted |
| –fork | Spawn a child process for encryption |
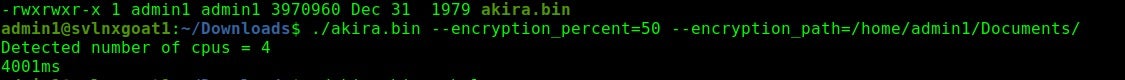
Akira is often recognized by their retro-style branding and themes. The operators have past interactions with Conti and the Conti source code is peppered throughout that of Akira. It will be interesting to monitor and see how their non-Windows payloads evolve over time, and if and how much they will deviate from the Conti base.
Trigona Linux Locker
Trigona is a ransomware family first observed in June 2022. A multi-extortion group, Trigona hosts a public blog of victims as well as their stolen data. Their malware payloads have been observed on Windows and Linux.

Of all the families discussed here, Trigona had the longest gap between releases of their original Windows payloads and the Linux-focused versions of their ransomware. While Trigona has the widest gap between releases of their Windows and Linux payloads, they are in no way behind other ransomware families.
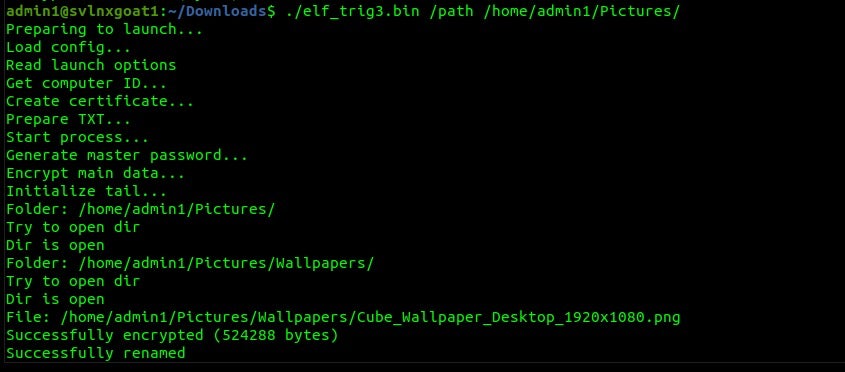
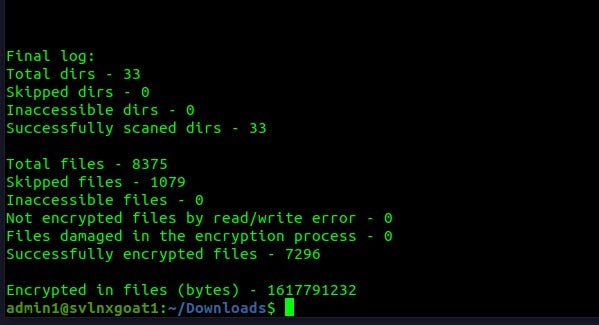
Trigona’s Linux-focused payloads are lean and efficient and they include the most robust logging and testing-output options across the families discussed in this post. The group is aggressive with their campaigns and demands and we continue to monitor as the group updates their tools for these and potentially other platforms.
The /erase option with Trigona is available on both Windows and Linux variants. This option is oft-overlooked, yet it perhaps should not be. Security teams should be aware that this option allows for the ransomware to function as a wiper of sorts.
With the Trigona payloads, the /erase option will fully delete the file, making it essentially non-recoverable. This behavior is somewhat tailorable with the combined use of the /full option. Without the latter, only the first 512KB of a given file will be overwritten with NULL bytes. When combined with the /full parameter, the entire contents of the file will be overwritten. Files affected as such will be given the ._erased extension as opposed to the usual ._locked extension.
Available command-line parameters for Trigona include:
| Argument | Function |
| /full | Full file encryption (as opposed to the first 512KB) |
| /sleep | Sets number of seconds to wait before full execution |
| /fast | Partial encryption |
| /erase | Overwrite data (wipe). |
| /is_testing | Sets testing/debugging flag |
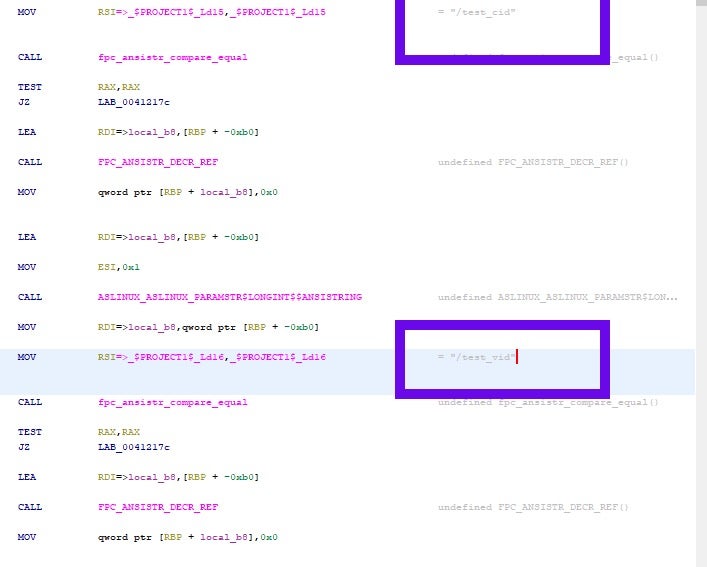
| /test_cid | Force use of specific Computer ID (for testing and debugging) |
| /test_vid | Force use of specific Victim ID (for testing and debugging) |
| /allow_system | Toggle encryption of system paths |
| /shdwn | Force the shutdown of system once encryption completes |
| /path | Required – Sets target path to encrypt |
| /log | Specify path for log file |
Abyss Locker
Abyss Locker ransomware operations emerged in March 2023, aggressively targeting VMware ESXi environments. Initial delivery of Abyss Locker payloads occurs through various means including phishing email or exploitation of vulnerable, publicly available services and applications.

Abyss Locker payloads for Linux, are derived from the Babuk codebase and function in a very similar fashion. In addition, the encryption features in Abyss are based on those found in HelloKitty ransomware. At this time, it is not known how formal cooperation occurs between Abyss Locker, HelloKitty, and Vice Society. Abyss Locker contains calls specific to the esxcli command-line tool which is used for management of virtual devices.
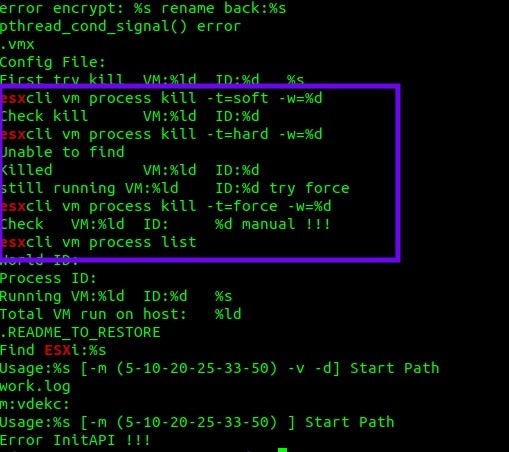
Abyss Locker uses the esxcli command-line tool and allows for multiple modes of virtual machine and process termination.
esxcli vm process list esxcli vm process kill -t=force -w=%d esxcli vm process kill -t=hard -w=%d esxcli vm process kill -t=soft -w=%d
These commands affect how ‘graceful’ the shutdown of targeted VMs will be. As per VMware’s documentation, the soft option is typically most desired. The hard option performs an immediate shutdown (assuming privilege) while the force option should only be used as a last resort. Abyss will make use of any and all of these if needed.
Available command-line parameters for Abyss Locker include:
| Argument | Function |
| -m | Partial encryption (5-10-20-25-33-50) |
| -v | verbose |
| -d | Switch to daemon |
| Start <path> | Path to start encryption in |
-v creates a verbose “work.log” file showing the chosen encryption modes and benchmarks around the timing of encryption for each file encountered.
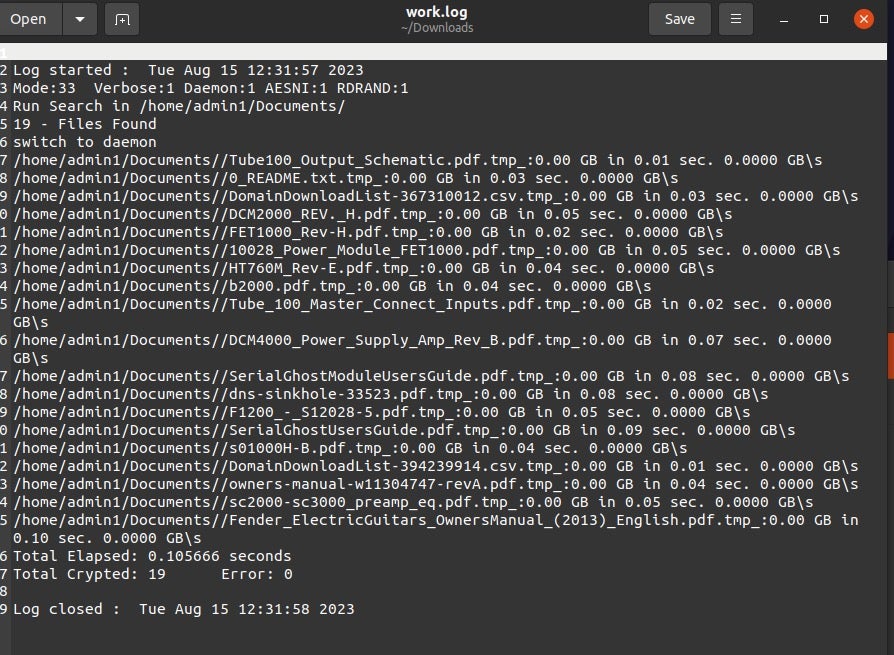
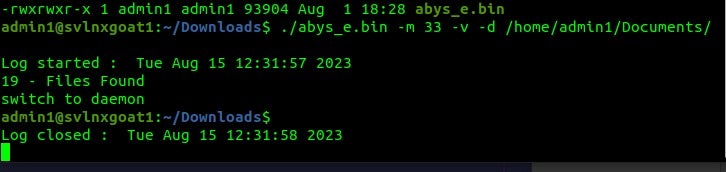
Abyss Locker’s payloads are speedy and efficient in terms of just how quickly the devices are encrypted overall. As this group continues to tweak their payloads, we expect to see more of them appearing in custom-branded, Vice Society-style campaigns.
Conclusion
In this post, we have examined several prominent Linux and VMWare ESXi-focused ransomware families, diving into the usage and command-line syntax of the specific payloads. By highlighting the understood lineage where possible and focusing on the parameters available, security teams can get a “hands-on, look and feel” for the payloads, enhancing their threat detection capabilities.
The divergence of attacks using Windows payloads to those targeting other platforms signals how the ransomware landscape continues to evolve. As threat actors continue to iterate on their strategies to evade detection, it is critical for security leaders to stay ahead of these trends.
Enterprises globally trust SentinelOne for strong preventative and detection controls required to combat increasingly sophisticated threats. SentinelOne’s Singularity™ Platform is capable of both detecting and preventing the malicious behaviors associated with the threats described in this post. To learn more about Singularity™, contact us today or book a demo to see it in action.
Linux Ransomware File Samples
MONTI Locker
a0c9dd3f3e3d0e2cd5d1da06b3aac019cdbc74ef
f1c0054bc76e8753d4331a881cdf9156dd8b812a
Akira
9180ea8ba0cdfe0a769089977ed8396a68761b40
Trigona
0144800f67ef22f25f710d181954869f1d11d471
55f47e767dd5fdd1a54a0b777b00ffb473acd329
62e4537a0a56de7d4020829d6463aa0b28843022
Abyss Locker
40ceb71d12954a5e986737831b70ac669e8b439e
Views: 5