### #CyberSecurity #Phishing #FraudAlert
Summary: A financially motivated Chinese threat actor known as “SilkSpecter” is operating thousands of fake online stores to steal payment card details from shoppers in the U.S. and Europe, particularly during the Black Friday shopping season. The campaign has resulted in the creation of nearly 4,700 fraudulent domains impersonating well-known brands.
Threat Actor: SilkSpecter | SilkSpecter
Victim: Online Shoppers | Online Shoppers
Key Point :
- SilkSpecter operates 4,695 fraudulent domains impersonating popular brands, targeting Black Friday shoppers.
- The phishing sites use legitimate payment processors like Stripe to appear trustworthy while stealing credit card information.
- Tracking tools are employed to monitor visitor behavior and adjust tactics for increased effectiveness.
- The campaign utilizes Chinese IP addresses and domain registrars, indicating a likely origin from China.
- Shoppers are advised to only visit official brand websites and activate all available protection measures on their financial accounts.

A financially motivated Chinese threat actor dubbed “SilkSpecter” is using thousands of fake online stores to steal the payment card details of online shoppers in the U.S. and Europe.
The fraud campaign started in October 2024, offering steep discounts for the upcoming Black Friday shopping period that usually sees elevated shopping activity.
EclecticIQ threat researcher Arda Buyukkaya, who discovered the campaign, told BleepingComputer that, as of the publishing of their report, SilkSpecter operates 4,695 fraudulent domains.
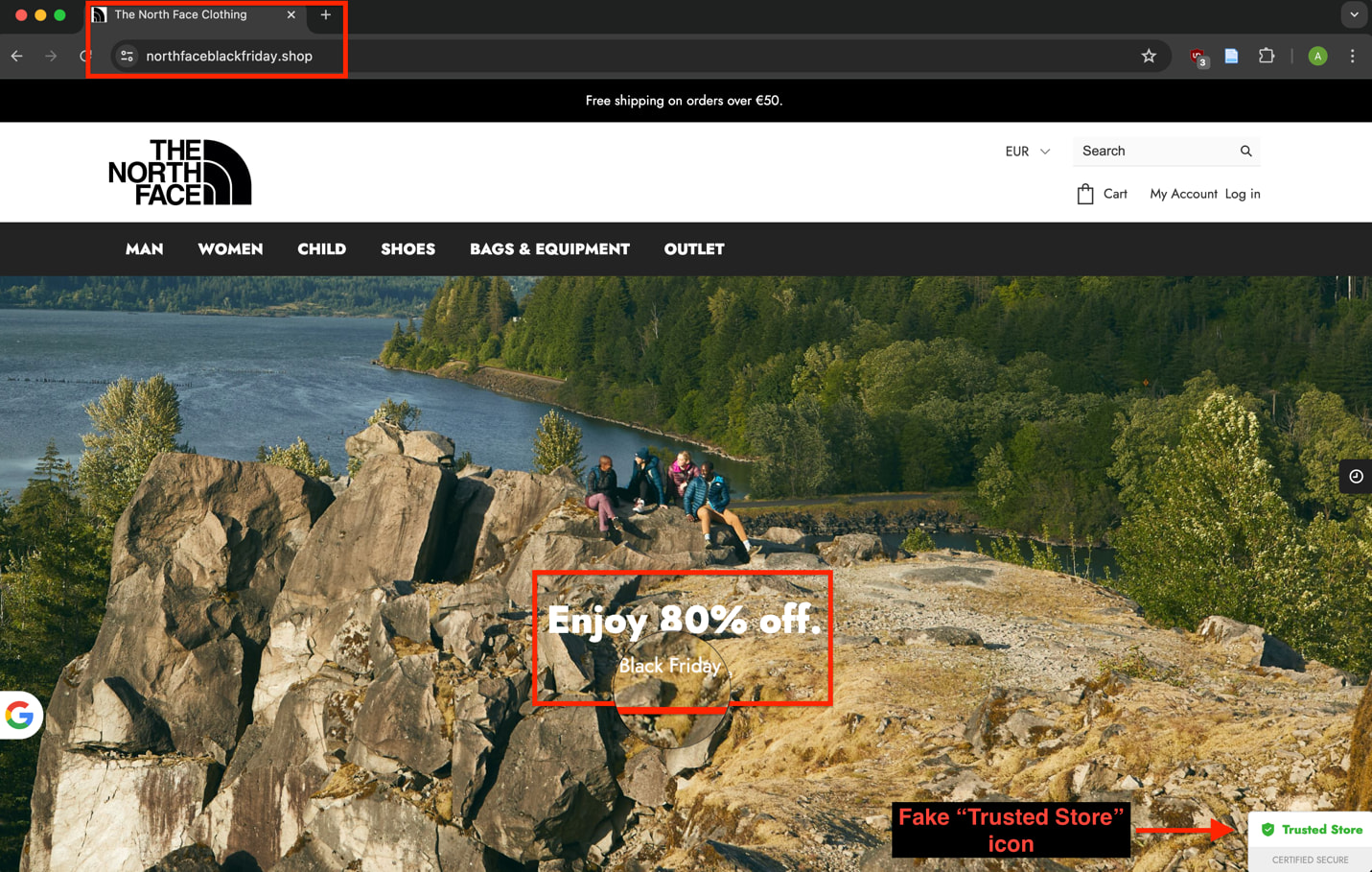
These sites impersonate well-known brands such as the North Face, Lidl, Bath & Body Works, L.L. Bean, Wayfair, Makita, IKEA, and Gardena.
In many cases, the domain names used in the campaign include the ‘Black Friday’ string, clearly targeting online shoppers looking for discount deals.
Source: EclecticIQ
Stealing credit card information
SilkSpecter websites are well-designed and typically named after the impersonated brand to appear authentic at a quick glance. However, their sites usually use top-level domains like ‘.shop,’ ‘.store,’ ‘.vip,’ and ‘.top,’ which are not generally associated with large brands or trustworthy e-commerce sites.
Depending on the victim’s location, the website uses Google Translate to automatically adjust the language on the fraud sites accordingly.
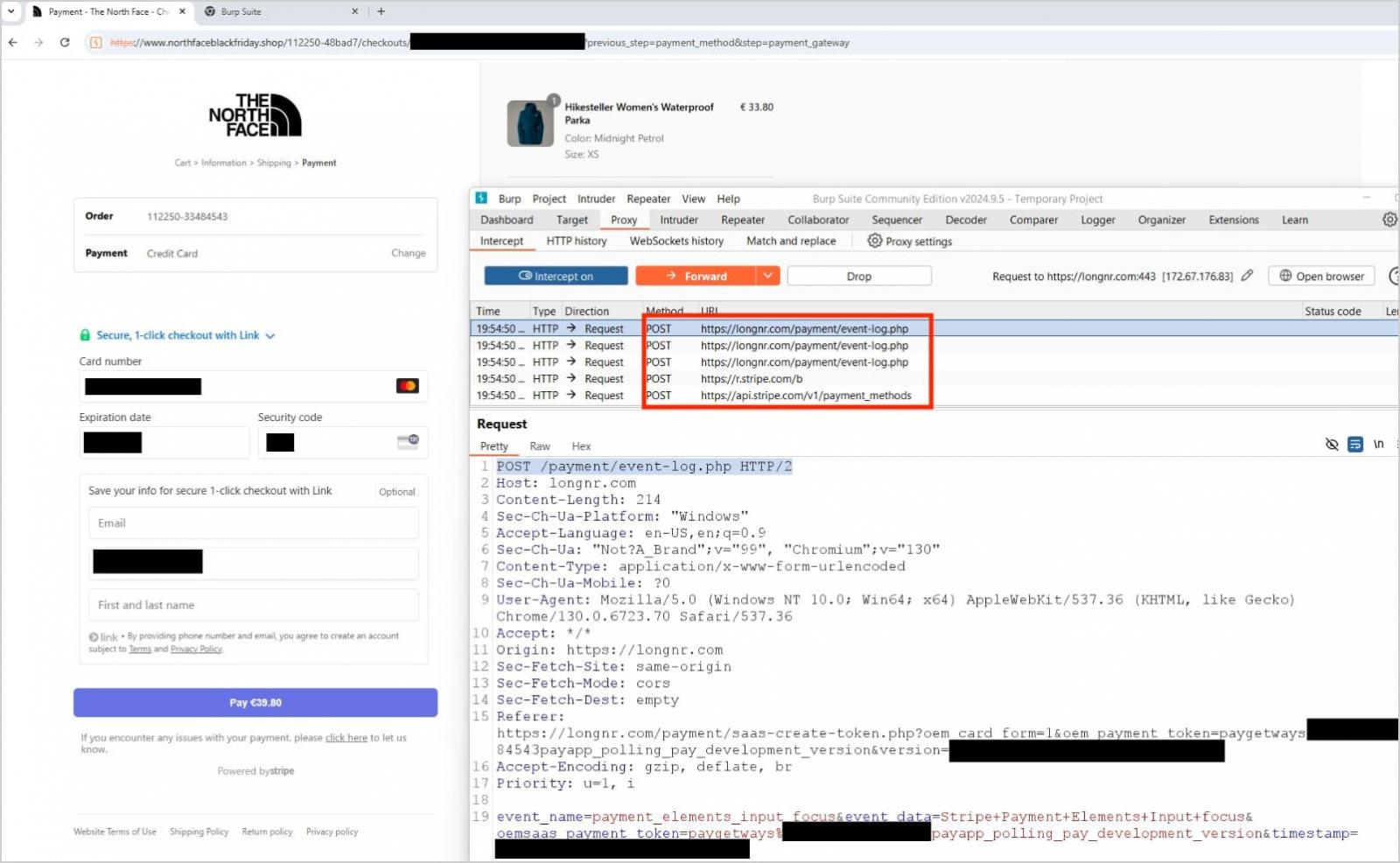
The phishing sites integrate Stripe, a legitimate and trusted payment processor, which adds to the site’s legitimacy while still allowing them to steal credit card information.
SilkSpecter also uses tracking tools like OpenReplay, TikTok Pixel, and Meta Pixel on the sites. These tools help them monitor visitor behavior and possibly adjust their tactics to increase the operation’s effectiveness.
When users attempt to purchase from those sites, they are redirected to a payment page that prompts them to enter their credit/debit card number, expiration date, and CVV code. A phone number is also requested at the final step.
Source: EclecticIQ
Apart from stealing the money for the order by abusing the Stripe service, the phishing kit also sends the entered card details to an attacker-controlled server.
EclecticIQ believes the phone number is stolen to be used later in voice or SMS phishing attacks required for handling two-factor authentication (2FA) prompts when exploiting the payment card data.
SilkSpecter is believed to be Chinese, based on their use of Chinese IP addresses and ASNs, Chinese domain registrars, linguistic evidence in the sites’ code, and previous use of the Chinese Software as a Service (SaaS) platform named “oemapps” (prior to Stripe).
BlackFriday shoppers are recommended only to visit official brand websites and avoid clicking on ads, links from social media posts, or promoted results on Google Search.
Finally, cardholders should activate all available protection measures on their financial accounts, including multi-factor authentication, and monitor their statements regularly.