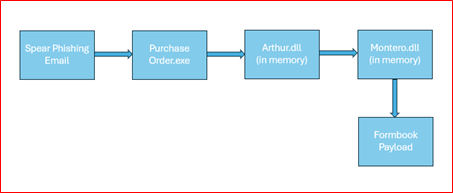
A recent phishing campaign has been identified that delivers Formbook stealers via email attachments. This variant employs multiple evasion techniques and utilizes steganography to conceal malicious files. The attack unfolds in three stages, ultimately leading to a final payload that executes stealthily on the victim’s system. Affected Platform: Windows
Keypoints :
- The phishing campaign uses spear phishing emails with malicious attachments.
- Formbook has evolved since 2016, being sold as Malware as a Service.
- The attack consists of three stages: Purchase Order.exe, Arthur.dll, and Montero.dll.
- Steganography is used to hide malicious files within images.
- The malware employs various evasion techniques to avoid detection.
- It creates a mutex to ensure only one instance runs to evade detection.
- Final payload is executed using process hollowing techniques.
MITRE Techniques :
- Initial Access: T1566.001 – Spear phishing Attachment: The malware is delivered through spear phishing emails with attachments.
- Execution: T1059.001 – Command and Scripting Interpreter: PowerShell: Used to execute commands and scripts.
- Execution: T1053.005 – Scheduled Task/Job: Scheduled Task: The malware creates scheduled tasks for persistence.
- Persistence: T1053.005 – Scheduled Task/Job: Scheduled Task: Maintains persistence through scheduled tasks.
- Defense Evasion: T1027.003 – Obfuscated Files or Information: Steganography: Uses steganography to hide malicious files.
- Defense Evasion: T1036 – Masquerading: The malware masquerades its true nature to avoid detection.
- Defense Evasion: T1497 – Virtualization/Sandbox Evasion: Implements techniques to evade detection in virtual environments.
- Defense Evasion: T1055.012 – Process Injection: Process Hollowing: Executes the final payload through process hollowing.
- Discovery: T1082 – System Information Discovery: Gathers information about the system.
- Discovery: T1083 – File and Directory Discovery: Scans for files and directories on the system.
- Discovery: T1057 – Process Discovery: Identifies running processes on the system.
Indicator of Compromise :
- [file hash] 6A9F890C529C410FA32793F496E7F200
- [file hash] 0DA34A44EE4876DD5E35939AF02F1D32
- [file hash] D751816C3673935BF989716ABD0DAB21
- [file hash] F8EC1BE3F2BD8269DB033375ED1A841E
- Check the article for all found IoCs.
Full Research: https://www.seqrite.com/blog/formbook-phishing-campaign-analysis/
Views: 11