A new advanced persistent threat (APT) group dubbed “Unfading Sea Haze” has been trailing its sights on various organizations based in countries surrounding the South China Sea. As it turns out, the group has been active since at least 2018 and targeted eight known victims, mostly military and government entities, in support of Chinese interests so far.
Bitdefender Labs published a list of indicators of compromise (IoCs) related to this attack. The WhoisXML API research team expanded the list comprising 21 domain names (some of which were extracted from subdomains) and 13 IP addresses and uncovered:
- 758 email-connected domains, one of which turned out to be malicious
- 16 additional IP addresses, 11 of which were associated with threats
- 272 IP-connected domains, 73 of which turned out to be malicious
- 253 string-connected domains
Note that this post contains only a preview of our findings. The full research, including a sample of the additional artifacts obtained from our analysis are available for download from our website.
More on the Unfading Sea Haze IoCs
We began our in-depth analysis by subjecting the 21 domains identified as IoCs to a bulk WHOIS lookup, which revealed that:
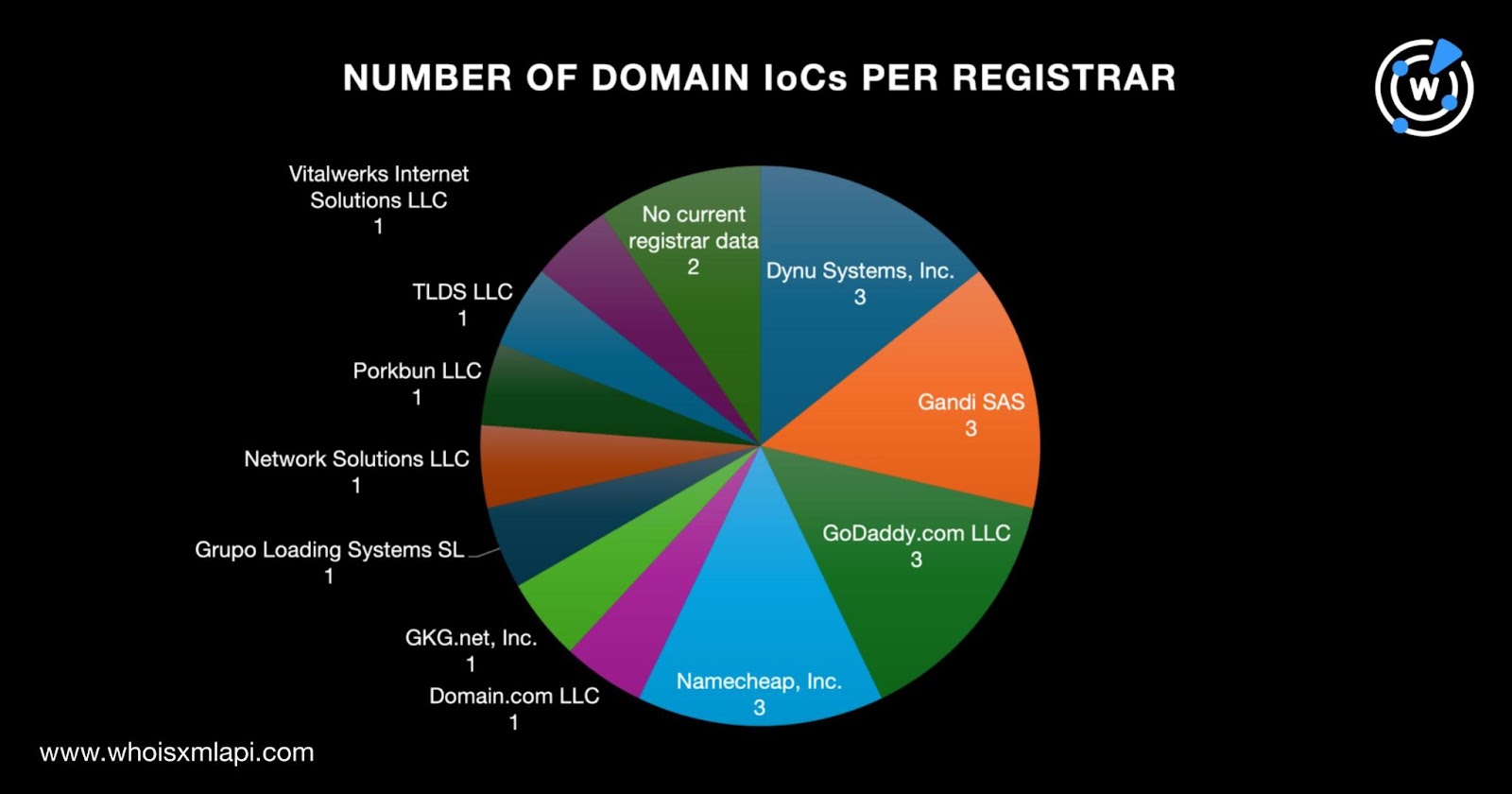
- The domain IoCs were spread across 11 registrars topped by Dynu Systems, Inc.; Gandi SAS; GoDaddy.com LLC; and Namecheap, Inc., which accounted for three domains each. Domain.com LLC; GKG.net, Inc.; Grupo Loading Systems SL; Network Solutions LLC; Porkbun LLC; TLDS LLC; and Vitalwerks Internet Solutions LLC, meanwhile, accounted for one domain IoC each. Finally, two domain IoCs did not have registrars in their current WHOIS records.
-
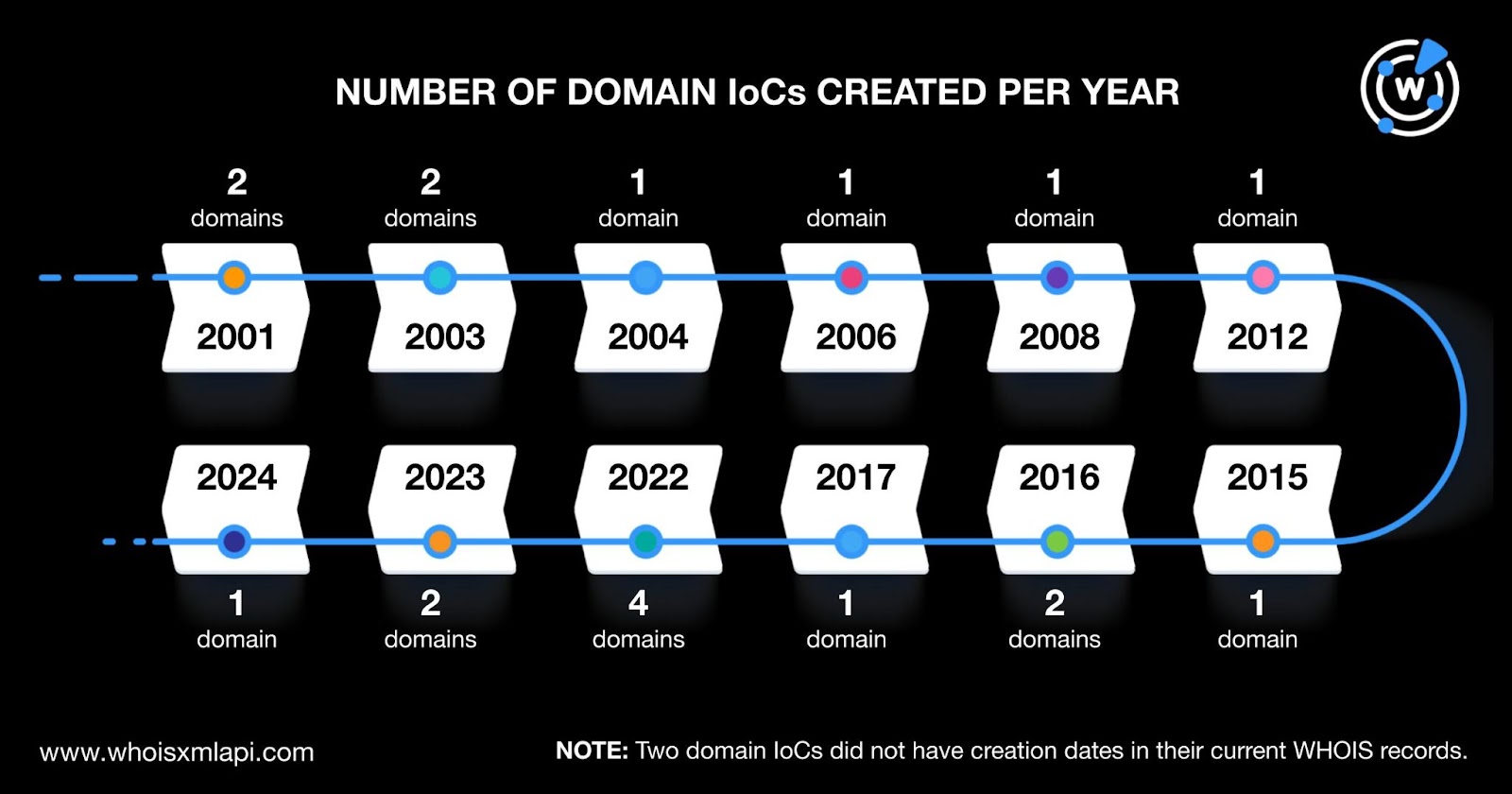
Unfading Sea Haze did not discriminate in terms of domain age, using old and new alike. They were created between 2001 and 2024. Specifically, four domain IoCs were created in 2022; two each in 2001, 2003, 2016, and 2023; and one each in 2004, 2006, 2008, 2012, 2015, 2017, and 2024.
-
The U.S. topped the list of registrant countries, accounting for 13 of the domain IoCs. Iceland took the second spot with three domains. One domain IoC was registered in the U.K. Four domains, however, did not have registrant countries in their current WHOIS records.

A bulk IP geolocation lookup for the 13 IP addresses tagged as IoCs showed that:
- The IP address IoCs originated from five countries led by Singapore and the U.S., which accounted for five IP addresses each. One IP address IoC each was geolocated in China, the Netherlands, and Turkey.

-
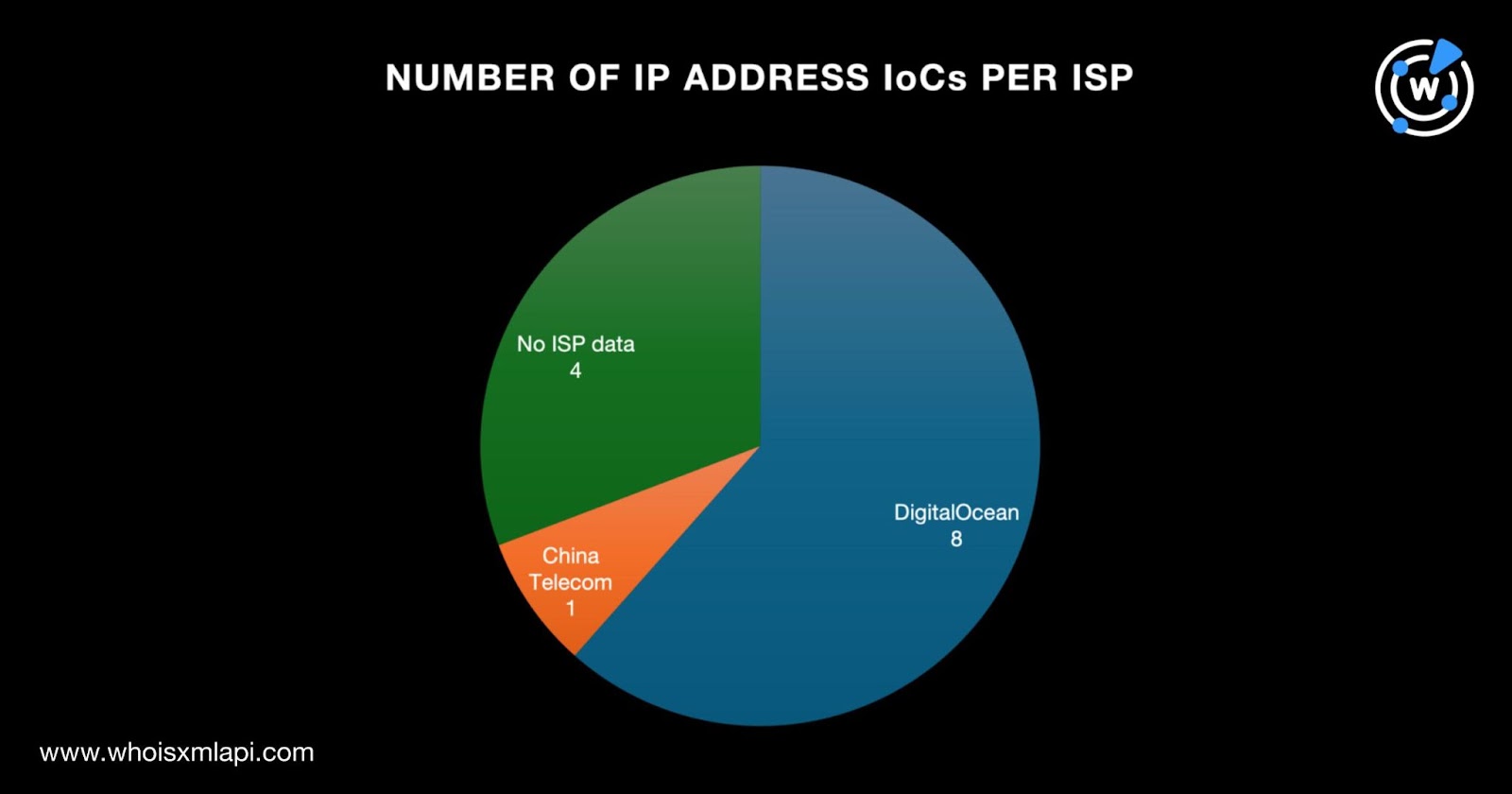
DigitalOcean led the pack of ISPs, accounting for eight of the IP address IoCs. One IP address was administered by China Telecom. Finally, four of the IoCs did not have ISPs in their A records.
This post only contains a snapshot of the full research. You can download the complete findings and a sample of the additional artifacts found on our website or contact us to discuss your intelligence needs for threat detection and response or other cybersecurity use cases.
Disclaimer: We take a cautionary stance toward threat detection and aim to provide relevant information to help protect against potential dangers. Consequently, it is possible that some entities identified as “threats” or “malicious” may eventually be deemed harmless upon further investigation or changes in context. We strongly recommend conducting supplementary investigations to corroborate the information provided herein.
Source: Original Post