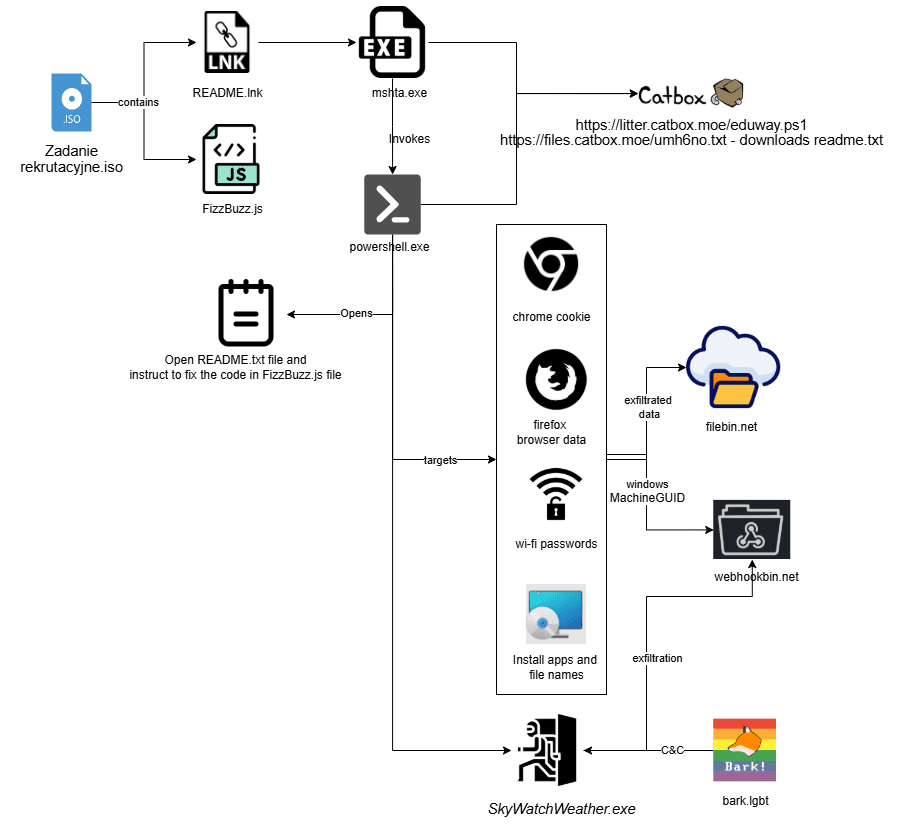
A targeted social engineering campaign has emerged, with a GitHub repository posing as a coding challenge aimed specifically at Polish-speaking developers. The campaign utilizes a malicious ISO file that, when executed, installs a backdoor called “FogDoor,” which collects sensitive information and communicates with a social media platform to execute commands. This evolving campaign now includes invoice-themed lures alongside recruitment scams to increase its range. Affected: Polish-speaking developers, social media platforms, recruitment sector
Keypoints :
- Campaign targets Polish-speaking developers with coding challenge disguise on GitHub.
- Malicious ISO file installs a backdoor named “FogDoor” via a PowerShell script.
- Backdoor steals browser cookies, saved credentials, and installed application details.
- Makes use of scheduled tasks for persistence and deletes traces post-exfiltration.
- Campaign has expanded to include invoice-themed lures alongside recruitment scams.
- Command retrieval is executed via social media instead of traditional C&C servers.
- Malware uses geofencing to target victims specifically in Poland.
- Stolen data is compressed and uploaded to file-sharing services for retrieval.
- Employs decoy tactics to maintain stealth while executing malicious actions.
- Continuous evolution in tactics indicates adaptability of the threat actor.
MITRE Techniques :
- Initial Access (TA0001): Spearphishing Attachment (T1566.001) – Malicious ISO file disguised as a recruitment task is delivered to victims.
- Execution (TA0002): User Execution (T1204) – Victim opens README.lnk, executing a malicious PowerShell script.
- Execution (TA0002): Command and Scripting Interpreter: PowerShell (T1059.001) – LNK file downloads and executes the PowerShell file.
- Execution (TA0002): System Binary Proxy Execution: Mshta (T1218.005) – mshta.exe executes malicious PowerShell commands.
- Persistence (TA0003): Scheduled Task/Job (T1053.005) – A scheduled task ensures the malware stays active.
- Credential Access (TA0006): OS Credential Dumping (T1003) – Script extracts Wi-Fi credentials.
- Credential Access (TA0006): Steal Web Session Cookie (T1539) – PowerShell script steals Chrome cookies and Firefox browser files.
- Discovery (TA0007): System Information Discovery (T1082) – Script collects system information and application lists.
- Collection (TA0009): Data from Local System (T1005) – Gathers Wi-Fi passwords, cookies, and file details.
- Collection (TA0009): Archive Collected Data (T1560) – Stolen data compressed into data.zip for exfiltration.
- Exfiltration (TA0010): Exfiltration Over Web Service (T1567.002) – Data is uploaded to filebin.net for exfiltration.
- Command and Control (TA0011): Web Service: Dead Drop Resolver (T1102.001) – FogDoor retrieves commands from social media profile.
- Command and Control (TA0011): Application Layer Protocol: Web Protocols (T1071.001) – Script communicates with WebhookBin for tracking.
Indicator of Compromise :
- [SHA-256] 82b649ae0a4cfe37c2a32ec2010bf7ef0e3236b540f85c8fbf15657d48d30d84
- [SHA-256] 8e565ba45c7624e8bc5dd92c1d0d3710f6a2b21d6c94742bb51fec07b4843ebd
- [SHA-256] 2b4bc80af0a0afac04da73e7da2779d3ab3ed8c460d2fb22d4034e1b2469f879
- [SHA-256] 33bc5fa9798219ba6d4e31f91ec23982596c409e0fd73e2c0c33c70538b7ec83
- [URL] hxxps://github.com/Rekrutacja-JS/FizzBuzz
Full Story: https://cyble.com/blog/fake-coding-challenges-steal-sensitive-data-via-fogdoor/