In today’s digital landscape, cyber threats are more prevalent than ever. Hackers often target vulnerable websites, leaving behind traces of their activities. For cybersecurity enthusiasts or those interested in understanding web vulnerabilities, Google Dorking can be a valuable tool. In this article, we will explore how to find hacked websites using specific Google search queries, commonly known as “Google Dorks.”
Understanding Google Dorking
Google Dorking is the practice of using advanced search queries to find specific information on the internet. This technique allows users to uncover hidden data that is not easily accessible through standard search engines. By using specific keywords and operators, one can filter search results to reveal sensitive information, including hacked websites.
Using Google Dork to Find Hacked Websites
One effective way to identify hacked websites is through the following Google Dork:
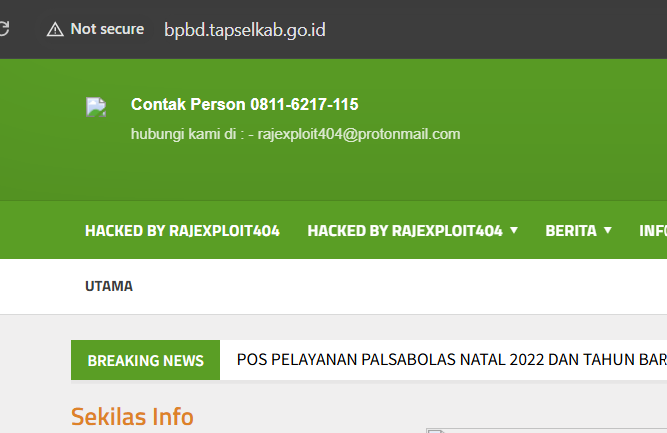
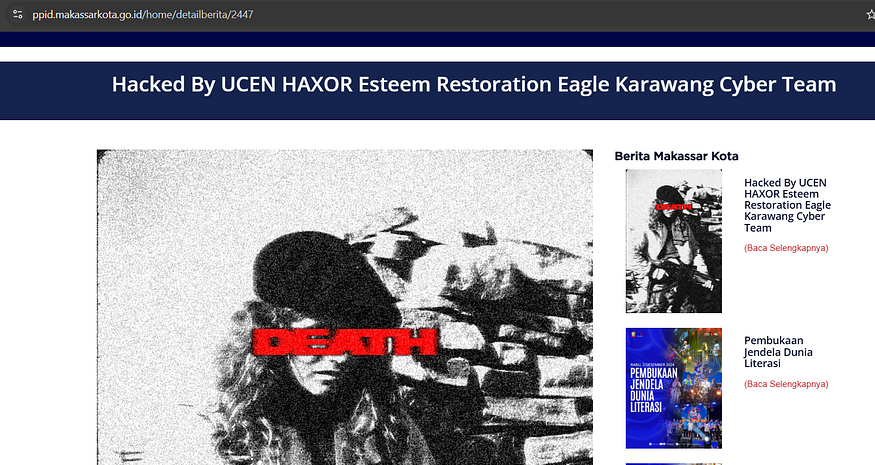
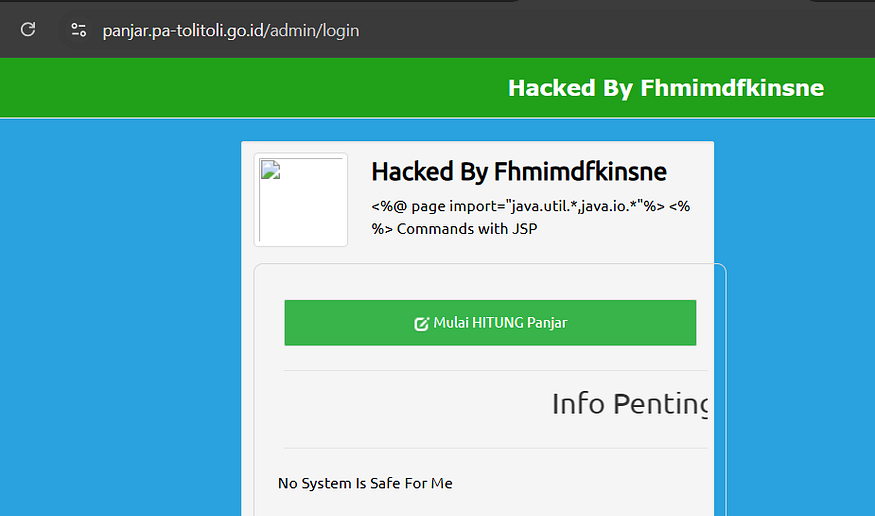
inurl:go.id intext:hacked intitle:hacked
Breaking Down the Query
- inurl:go.id: This part of the query specifies that we are only interested in websites that belong to the “.go.id” domain, which is typically associated with Indonesian government sites. By narrowing the search in this way, we can focus on a specific type of website.
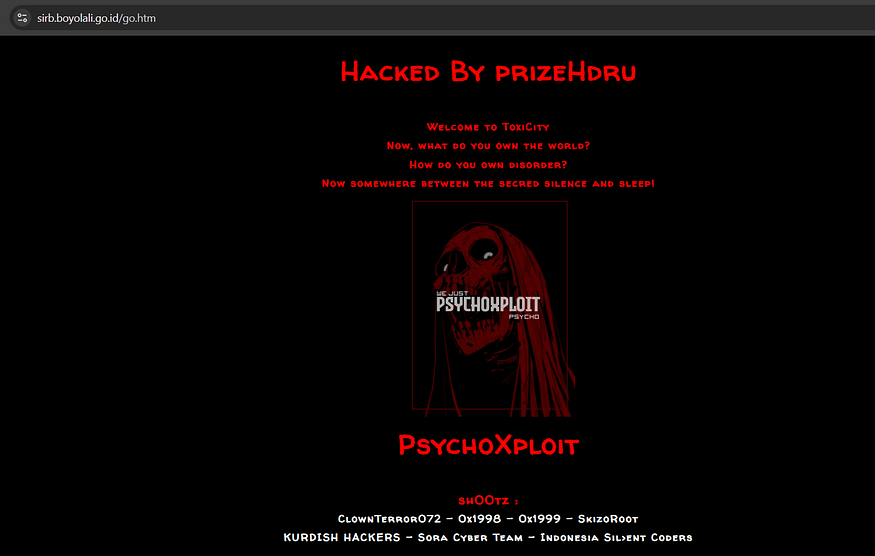
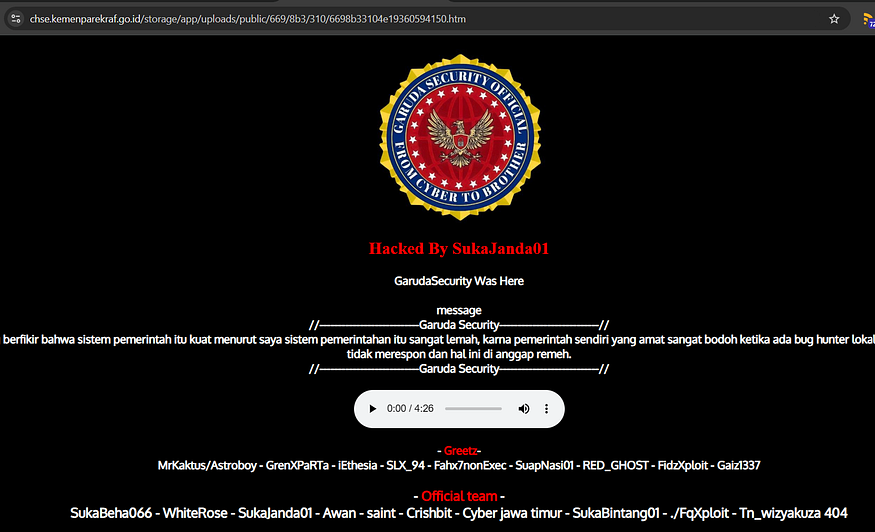
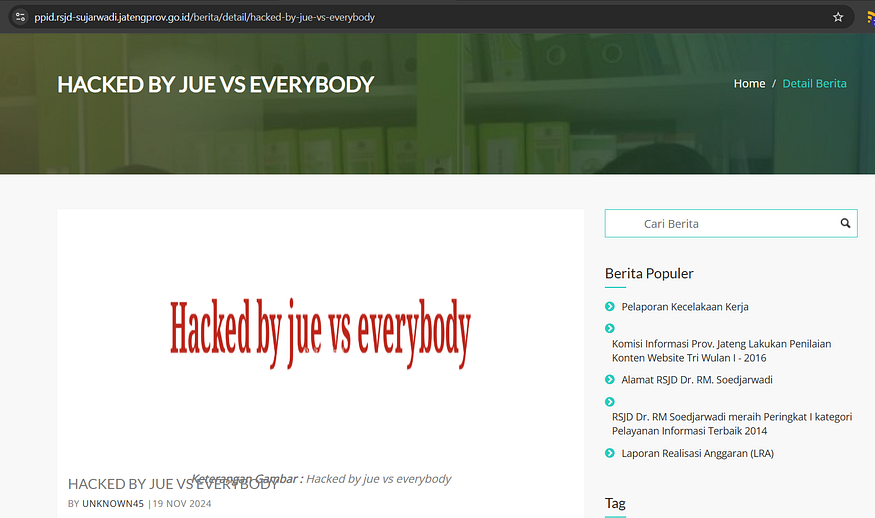
- intext:hacked: This indicates that we want to find pages containing the word “hacked” in their content. This could be in a message left by the hacker or any other indication that the site has been compromised.
- intitle:hacked: This part of the query looks for the word “hacked” in the title of the web pages. Many times, hackers modify the title of the hacked pages to reflect their actions, making it easier to identify them.
Step-by-Step Guide to Finding Hacked Sites
- Open Google: Launch your preferred web browser and navigate to the Google search engine.
- Enter the Dork: Copy and paste the Google Dork provided above into the search bar.
- Analyze Results: Review the search results carefully. Look for pages that clearly indicate they have been compromised. You may find messages from hackers or notices of defacement.
- Record Findings: If you are conducting research or monitoring cybersecurity, make sure to document your findings. Take screenshots or save URLs for future reference.
- Report Hacked Sites: If you’re involved in cybersecurity, consider reporting any hacked sites you discover to help the respective organizations address the vulnerabilities.
Ethical Considerations
While Google Dorking can be a powerful tool for identifying vulnerabilities, it is crucial to approach this practice ethically. Use this knowledge for educational purposes, to enhance cybersecurity measures, or to inform the affected parties. Unauthorized access or exploitation of hacked sites is illegal and unethical.
Conclusion
Google Dorking is an invaluable technique for uncovering hacked websites and enhancing our understanding of cybersecurity threats. By using targeted search queries, such as “inurl:go.id intext:hacked intitle:hacked,” individuals can quickly identify compromised sites and take appropriate action. Remember to approach this practice with responsibility and use your findings to support web safety. Happy searching!



https://medium.com/@harboot/finding-hacked-websites-using-google-dork-b476d809374a