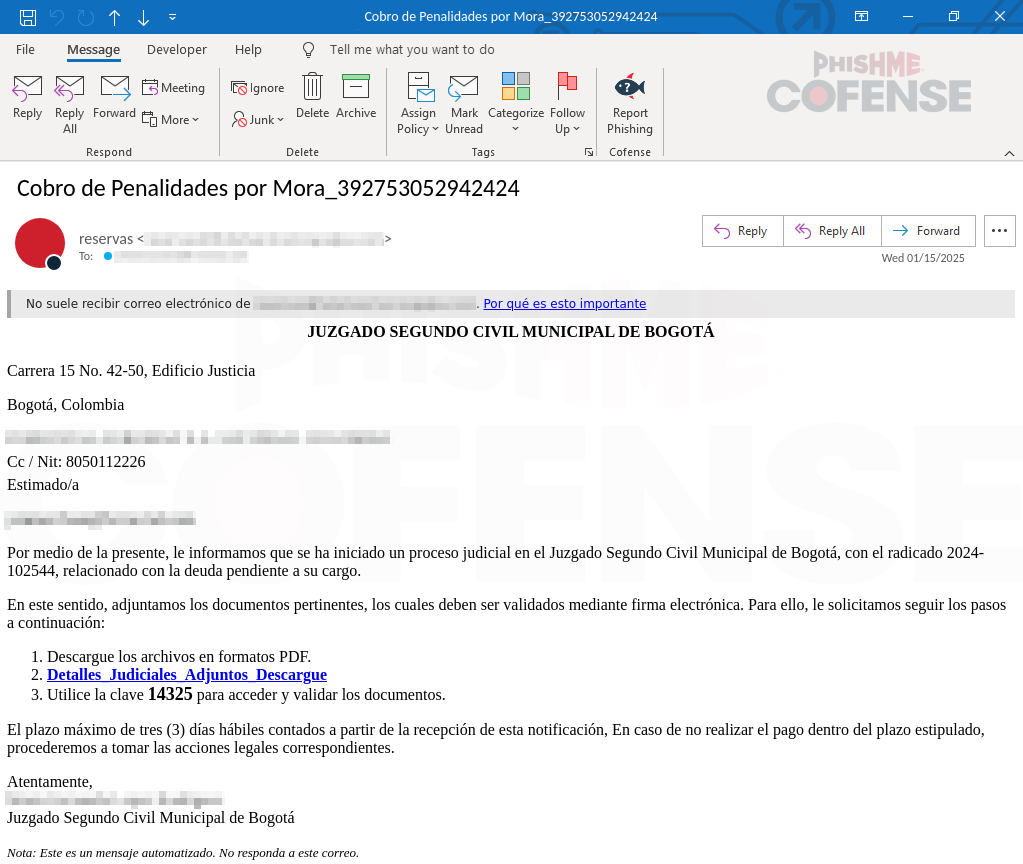
This article discusses a sophisticated wave of attacks targeting organizations in Latin America, employing legal-themed emails to distribute McSapphireRAT. The malicious strategy includes bypassing traditional security measures and leveraging social engineering tactics to deceive recipients. Affected: organizations in Latin America, critical infrastructure sectors
Keypoints :
- New wave of attacks utilizing judicial receipts for legal processes.
- SapphireRAT executed via seemingly legitimate legal documents.
- Social engineering tactics are used to deceive recipients into executing the malicious payload.
- Emails are designed to create a sense of urgency with subject lines suggesting legal consequences.
- Malicious URLs redirect recipients to domains hosting the malware.
- Attackers use .rar files to distribute the SapphireRAT payload.
- Malware evades detection by injecting malicious code into legitimate Windows processes.
- SapphireRAT establishes persistent access through task scheduling and modified files in the AppData directory.
- The attack underscores the need for heightened vigilance and robust security protocols.
MITRE Techniques :
- T1071.001: Application Layer Protocol: Web Protocols – The malware communicates with remote servers over HTTP.
- T1045: Software Packing – The SapphireRAT is packed to evade detection during initial deployment.
- T1055: Process Injection – SapphireRAT injects code into legitimate processes like regsvr32.exe.
- T1070.001: Indicator Removal on Host: File Deletion – The malware modifies or deletes indicators of compromise during execution.
- T1547.001: Boot or Logon Autostart Execution: Registry – SapphireRAT schedules tasks to maintain persistence through the Windows Task Scheduler.
Indicator of Compromise :
- File Name: Documentos_Del_Caso_9.rar; MD5: ddc37a23988a9c86cd4bb0f85a6673965; SHA256: 582ca9b2b5b8f8e5f79185f60a6893ec782527e464f037360678fc61e513dcd; Size: 104,216 bytes
- File Name: ad48273605918347192073865182749015637294826479518002.part1.rar; MD5: 68eacfa360f5936cc121ea64cbafa6d9d2fbc247f3f5e8bec0f7a282b6ea1a0d; Size: 1,000,000 bytes
- File Name: ad48273605918347192073865182749015637294826479518002.part2.rar; MD5: 63d7ff161cf9fb13c69e73d95b5f6d3206c1d2ea250d4c6453675091b106415; Size: 406,457 bytes
- File Name: ad48273605918347192073865182749015637294826479518002.exe; MD5: e2909ce9f9acf027481cba55c71f8253da32159b27065337a699264da4778b7; Size: 224,306 bytes
- URL: hXXps://upload[.]nolog[.]cz/download/a54ffb1804fb1044/#cL79FplBdUu45QNDY_iS6A93