This article discusses a case of credit card theft on a WordPress site, where a suspicious domain was found in connection with a malicious script that captured credit card information. The findings indicate the presence of a fake credit card form designed to steal users’ data by masking itself as a legitimate part of the checkout process. Affected: WordPress site, customers’ sensitive data.
Keypoints :
- A client reported credit card theft after users purchased products on their WordPress website.
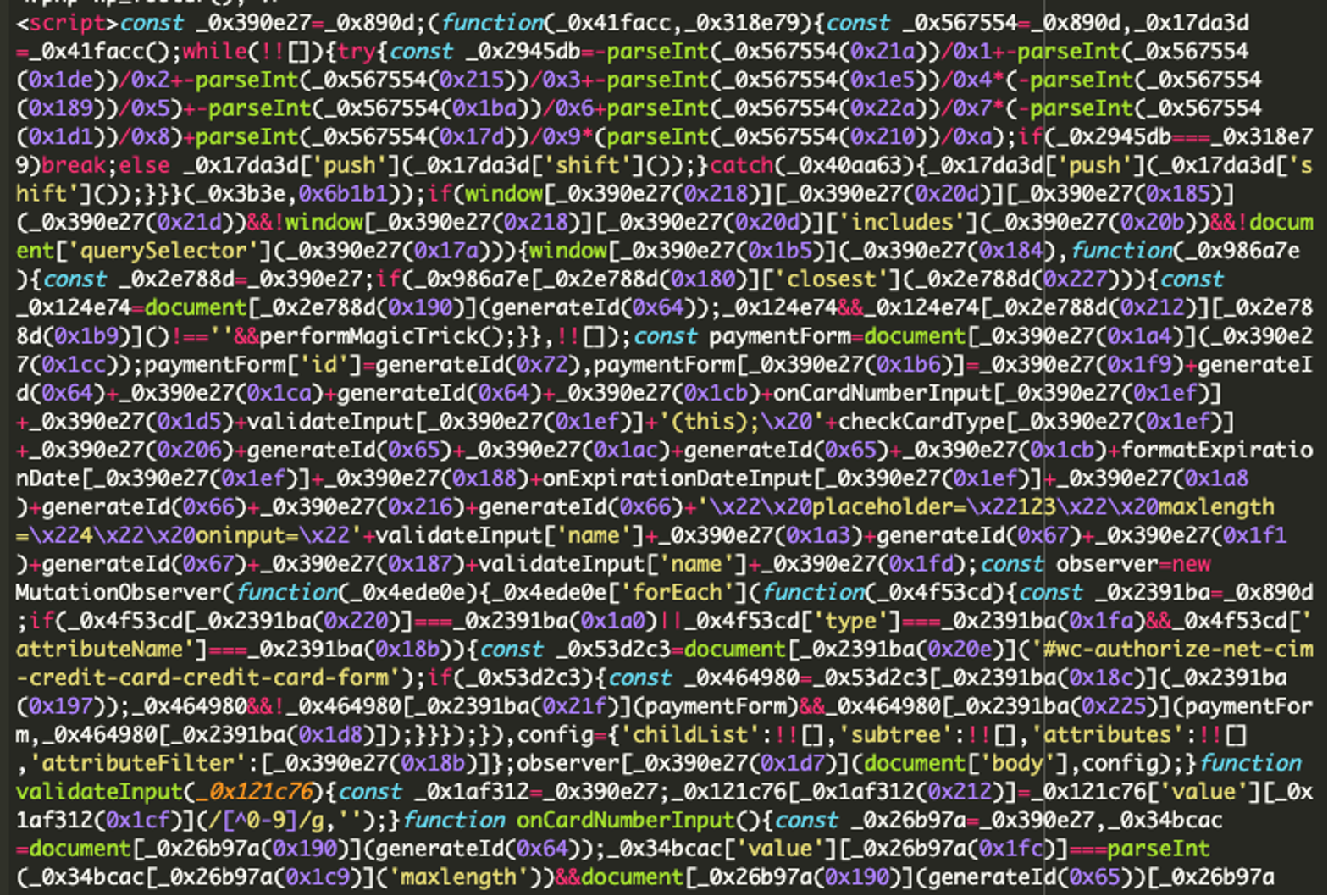
- A suspicious domain, italicfonts[.]org, was found on the checkout page.
- An obfuscated script in the footer.php file contained both the malicious domain and a fake credit card form.
- The skimmer captured credit card data and sent it to the attacker’s remote server.
- Credit card theft can severely damage a business’s reputation and financial standing.
- Mitigation strategies include keeping software updated, employing a web application firewall, and ensuring the use of strong passwords.
MITRE Techniques :
- T1071.001 – Application Layer Protocol: The attacker injects a script from the malicious domain italicfonts[.]org into the site’s checkout page.
- T1203 – Exploitation for Client Execution: The fake credit card form listens for input events and captures the inputted data.
- T1070.001 – Indicator Removal on Host: The obfuscated script aims to avoid detection by blending in with legitimate site content.
- T1041 – Exfiltration Over Command and Control Channel: Captured credit card details are sent to the attacker’s server using the compromised domain.
Indicator of Compromise :
- [Domain] italicfonts[.]org
Full Story: https://blog.sucuri.net/2025/04/fake-font-domain-used-to-skim-credit-card-data.html
Views: 32