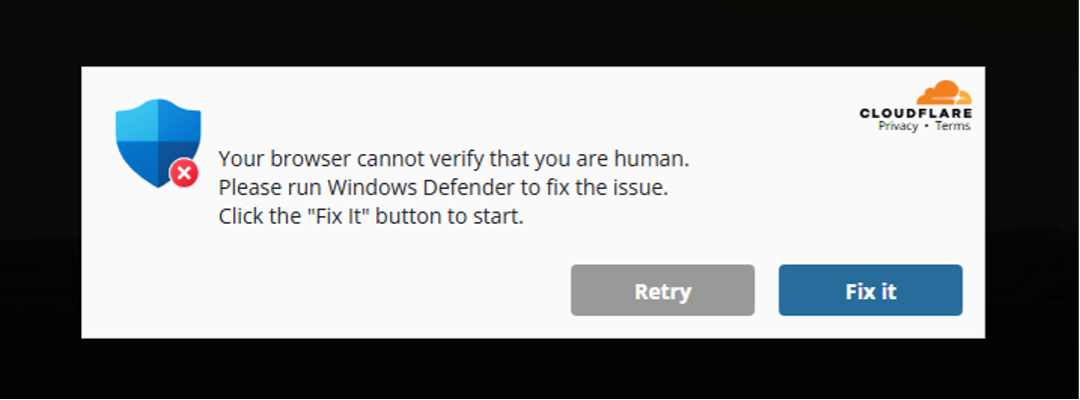
This article describes an ongoing malware campaign utilizing malicious WordPress plugins to spread the LummaStealer trojan. The malware trick users into running harmful PowerShell commands, thus collecting sensitive data from infected PCs. The campaign exploits fake human verification prompts primarily targeting Windows users. Affected: WordPress websites, Windows operating system users
Keypoints :
- LummaStealer is an infostealer malware designed to collect sensitive data.
- Malicious WordPress plugins are used to trick users into running harmful commands.
- Fake human verification prompts are primarily targeting Windows OS users.
- Attackers utilize URL shortening services for obfuscation of malicious links.
- The malware operates covertly to avoid detection and maximize data theft.
- Malicious users can access sensitive login information and personal data once the malware is installed.
- Website owners are advised to maintain security practices to prevent infections.
MITRE Techniques :
- TA0007 – Execution: The users are tricked into running malicious PowerShell commands.
- TA0011 – Command-Line Interface: The malware uses command prompt to execute hidden operations.
- TA0030 – Data Exfiltration: The stolen data is collected and sent to the attacker’s server.
- TA0009 – Credential Access: The Trojan captures sensitive information including login credentials.
- TA0020 – Resource Development: The attackers create malicious plugins to serve as backdoors.
Indicator of Compromise :
- [Domain] short[.]gy
- [Domain] warther[.]info
- [Domain] bestieslos[.]com
- [File Path] ./wp-content/plugins/SwiftPress/SwiftPress.php
- [File Path] ./wp-content/plugins/nwPostSaver/nwPostSaver.php
Full Story: https://blog.sucuri.net/2025/03/fake-cloudflare-verification-results-in-lummastealer-trojan-infections.html