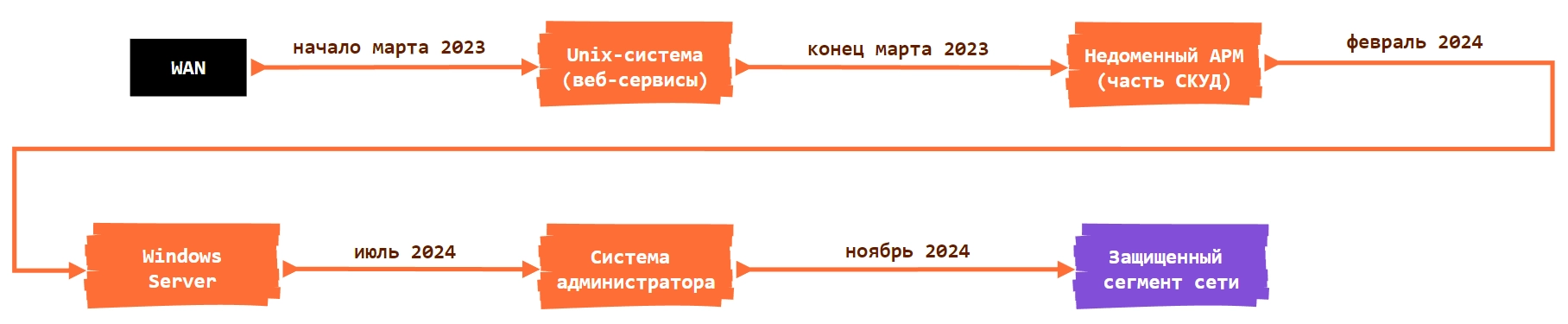
In November 2024, Solar 4RAYS reported on a malicious campaign targeting Russian IT organizations providing services for the public sector. The group, dubbed Erudite Mogwai by Solar 4RAYS and Space Pirates by Positive Technologies, is utilizing a modified version of the public proxy tool Stowaway. This custom tool, used alongside other malware like ShadowPad Light, demonstrated enhancements and adaptions for unauthorized access against sensitive networks. The report outlines attacks, techniques, and IOCs linked to this APT group. Affected: Russian IT sector, government institutions
Keypoints :
- Solar 4RAYS discovered a custom version of the Stowaway proxy tool used in attacks against Russian IT organizations.
- The group responsible for the attacks is referred to as Erudite Mogwai and has been active since at least 2017.
- Erudite Mogwai employs various tools, including Stowaway and ShadowPad Light, to target public sector organizations.
- The group has evolved its techniques over time, incorporating methodologies and using lightweight versions of existing tools.
- The latest version of Stowaway utilizes LZ4 for data compression and XXTEA for encryption, along with support for QUIC protocol.
MITRE Techniques :
- T1071.001 – Application Layer Protocol: Stowaway acts as a proxy tool for command and control traffic.
- T1071.003 – Application Layer Protocol: Support for QUIC protocol indicated advanced evasion techniques.
- T1005 – Data from Local System: Usage of tools for data exfiltration illustrates techniques for gathering sensitive information from compromised systems.
Indicator of Compromise :
- [File MD5] 8d2315cfe0d678f9318d15a848d8ab33
- [File MD5] d423dc26492d3212def0db188bdfb76d
- [File MD5] 1d9b8f08fb046ab644861f5f172582ee
- [File MD5] b9c4ef019202d96e18672fad1c6508dd
- [Domain] wiod[.]mynetav[.]net
Full Story: https://rt-solar.ru/solar-4rays/blog/5261/