Short Summary:
The Trend Micro Threat Hunting Team has identified EDRSilencer, a red team tool that can disrupt endpoint detection and response (EDR) solutions by blocking their communication with management consoles. This tool is being repurposed by threat actors to evade detection, complicating malware identification and removal. EDRSilencer dynamically identifies running EDR processes and creates filters to block their outbound communications, enhancing the stealth of malicious activities.
Key Points:
- EDRSilencer is a red team tool discovered by Trend Micro’s Threat Hunting Team.
- It interferes with EDR solutions using the Windows Filtering Platform (WFP).
- The tool blocks telemetry and alerts from EDR products, complicating malware detection.
- EDRSilencer can dynamically identify and block multiple EDR processes.
- Threat actors are leveraging EDRSilencer to enhance their attack strategies.
- Trend Micro products already detect EDRSilencer as malware.
- Recommendations include implementing multi-layered security controls and continuous monitoring.
MITRE ATT&CK TTPs – created by AI
- Process Discovery – T1057
- Identifying running processes associated with EDR products.
- Command and Scripting Interpreter – T1059
- Executing commands to block EDR processes.
- Create or Modify System Process – T1543.00
- Modifying system processes to evade detection.
- Impair Defenses: Disable or Modify Tools – T1562.001
- Disabling EDR tools to prevent detection.
- Network Traffic Filtering – T1569.002
- Blocking outbound communications from EDR processes.
- Network Denial of Service – T1498
- Disrupting EDR communications to hinder detection.
- Endpoint Denial of Service – T1499
- Rendering EDR tools ineffective by blocking their communications.
Trend Micro’s Threat Hunting Team discovered EDRSilencer, a red team tool that threat actors are attempting to abuse for its ability to block EDR traffic and conceal malicious activity.
Summary
- The Trend Micro Threat Hunting Team recently discovered EDRSilencer, a red team tool originally designed to interfere with endpoint detection and response solutions via the Windows Filtering Platform.
- However, our internal telemetry showed threat actors attempting to integrate EDRSilencer in their attacks, repurposing it as a means of evading detection.
- EDRSilencer disrupts the transmission of telemetry or alerts to EDR management consoles, which complicates the identification and removal of malware.
- The tool dynamically identifies any running EDR processes and creates WFP filters to block their outbound communication.
- During testing, it was also found to block communication for processes not included in its hardcoded list, further demonstrating its effectiveness.
Red team tools, which identify and address weaknesses in an organization’s security infrastructure, are crucial to the improvement of its overall security posture. However, threat actors are continuously finding ways to repurpose these tools for malicious purposes. Recently, the Trend Micro Threat Hunting Team discovered EDRSilencer, a red team tool that is able to interfere with endpoint detection and response (EDR) solutions by leveraging the Windows Filtering Platform (WFP). According to the author of this tool, it was inspired by the closed-source tool FireBlock by MdSec NightHawk.
EDRs are security tools that monitor endpoints like computers for signs of malicious activity. EDRSilencer is designed to block network communication for processes associated with various EDR products. This interference can prevent EDR solutions from sending telemetry or alerts to their management consoles, making it significantly harder to identify and remove malware. It is effective in blocking network communication for processes associated with various EDR products (Table 1).
The WFP is a powerful framework built into Windows for creating network filtering and security applications. It provides APIs for developers to define custom rules to monitor, block, or modify network traffic based on various criteria, such as IP addresses, ports, protocols, and applications. WFP is used in firewalls, antivirus software, and other security solutions to protect systems and networks.
However, this tool demonstrates a technique that can be used by adversaries to evade detection: By blocking EDR traffic, malware could potentially remain hidden on a system, making it harder to identify and remove. Understanding how this code works is crucial for defenders to develop effective countermeasures.
| EDR Product | Process |
| Carbon Black Cloud | RepMgr.exe, RepUtils.exe, RepUx.exe, RepWAV.exe, RepWSC.exe |
| Carbon Black EDR | cb.exe |
| Cisco Secure Endpoint (Formerly Cisco AMP) | sfc.exe |
| Cybereason | AmSvc.exe, CrAmTray.exe, CrsSvc.exe, ExecutionPreventionSvc.exe, CybereasonAV.exe |
| Cylance | CylanceSvc.exe |
| Elastic EDR | winlogbeat.exe, elastic-agent.exe, elastic-endpoint.exe, filebeat.exe |
| ESET Inspect | EIConnector.exe, ekrn.exe |
| FortiEDR | fortiedr.exe |
| Harfanglab EDR | hurukai.exe |
| Microsoft Defender for Endpoint and Microsoft Defender Antivirus | MsMpEng.exe, MsSense.exe, SenseIR.exe, SenseNdr.exe, SenseCncProxy.exe, SenseSampleUploader.exe |
| Palo Alto Networks Traps/Cortex XDR | Traps.exe, cyserver.exe, CyveraService.exe, CyvrFsFlt.exe |
| Qualys EDR | QualysAgent.exe |
| SentinelOne | SentinelAgent.exe, SentinelAgentWorker.exe, SentinelServiceHost.exe, SentinelStaticEngine.exe, LogProcessorService.exe, SentinelStaticEngineScanner.exe, SentinelHelperService.exe, SentinelBrowserNativeHost.exe |
| Tanium | TaniumClient.exe, TaniumCX.exe, TaniumDetectEngine.exe |
| Trellix EDR | xagt.exe |
| TrendMicro Apex One | CETASvc.exe, WSCommunicator.exe, EndpointBasecamp.exe, TmListen.exe, Ntrtscan.exe, TmWSCSvc.exe, PccNTMon.exe, TMBMSRV.exe, CNTAoSMgr.exe, TmCCSF.exe |
The code leverages WFP by dynamically identifying running EDR processes and creating WFP filters (Figure 1) to block their outbound network communications on both the internet protocols IPv4 and IPv6, effectively preventing EDRs from sending telemetry or alerts to their management consoles (Figure 2).
To verify whether the EDR was effectively blocked by EDRSilencer, we utilized EDRNoiseMaker, a tool available on GitHub that is designed to identify potential silencers of an EDR or a process of the user’s choosing (Figure 4). It tries to detect the silenced processes by examining a list of executables that have been silenced using WFP, which corresponds directly to the functionality of EDRSilencer.
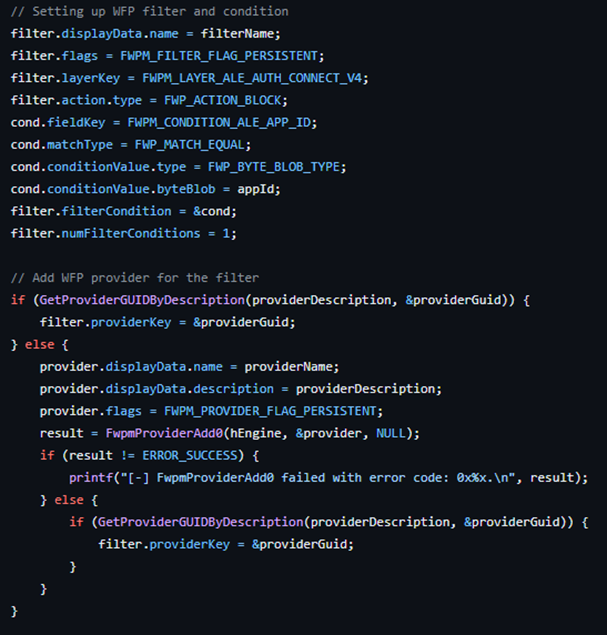
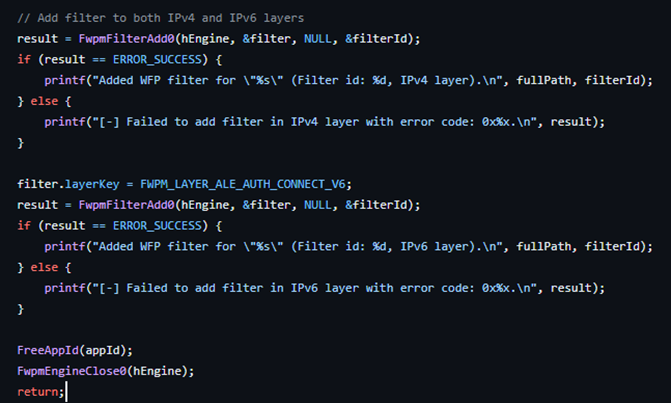
The WFP filters are marked as persistent, ensuring that they remain active even after the code has finished executing or the system is rebooted.
The tool provides a command-line interface with the following options:
- blockedr – Automatically block traffic from all detected EDR processes
- block <path> – Block traffic from a specific process specified by its full path
- unblockall – Remove all WFP filters created by the tool
- unblock <filter id> – Remove a specific WFP filter using its ID
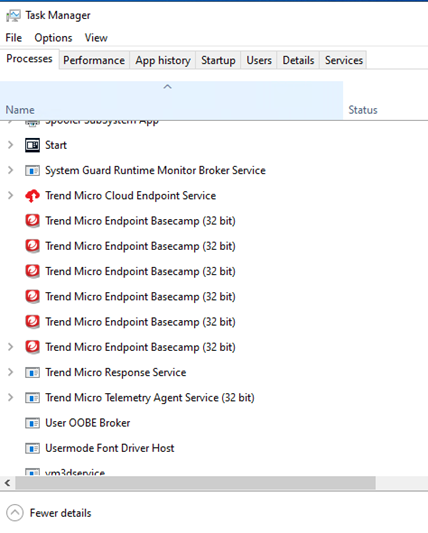
During our investigation, we tested the tool with our Vision One Endpoint Agent. On the first attempt using the tool with the blockedr argument, the endpoint agent was still able to send outbound traffic, as some executable files reporting to Vision One are not included in the hardcoded list.
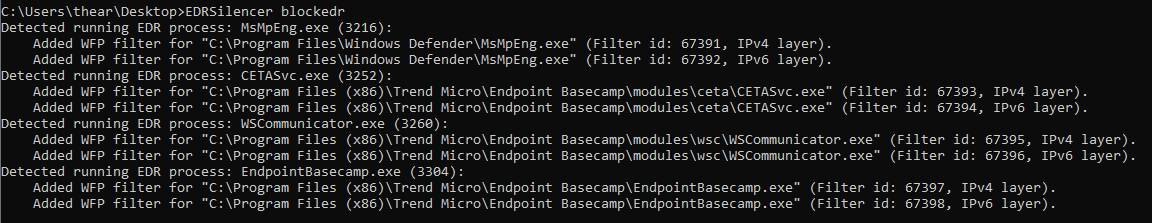
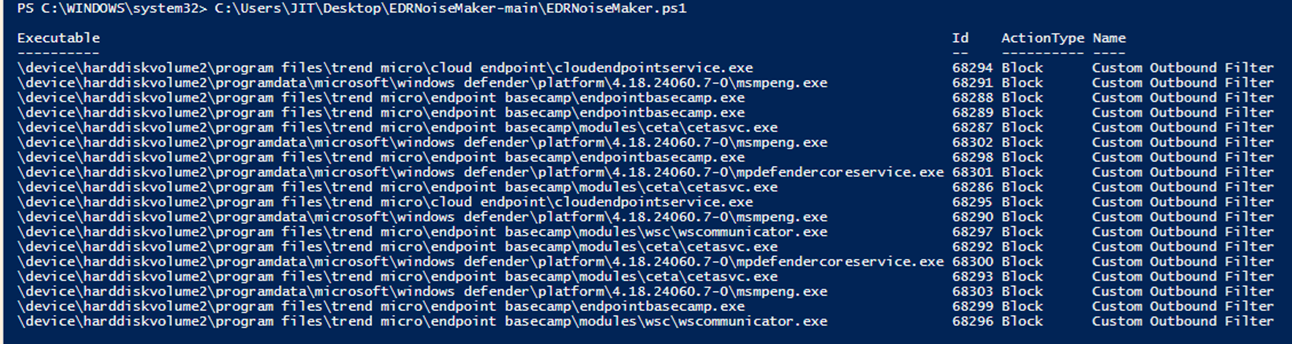
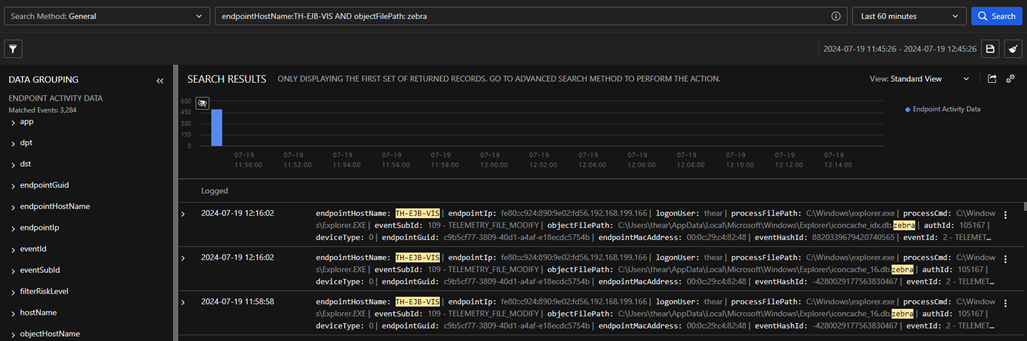
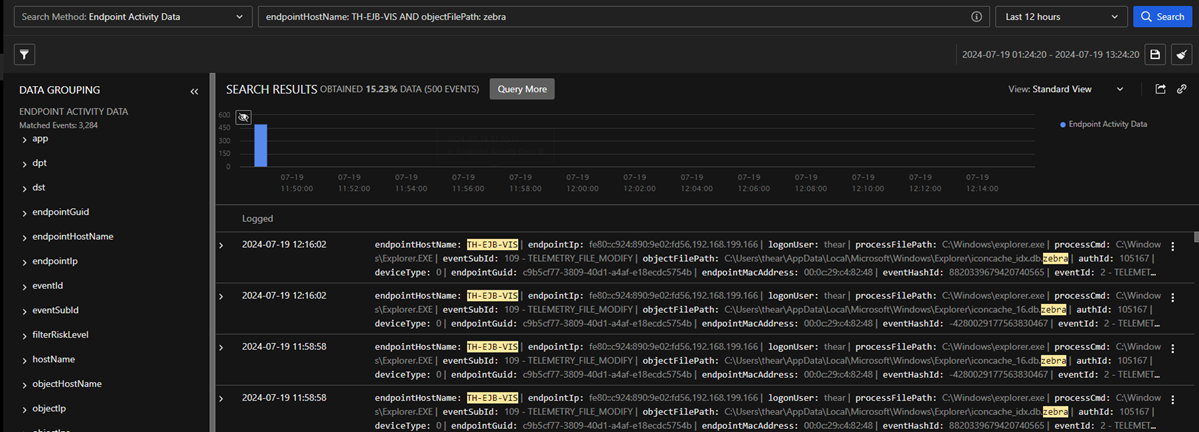
On the second attempt, we first checked for running Trend Micro products, saw two processes running that were not included in the hardcoded list (Figure 6) and copied their respective full file paths. We then used both blockedr and block <path> arguments to apply the filters (Figure 7). When we executed a ransomware binary, no logs were reflected on the portal; the device appeared disconnected or inactive, which indicates that the tool was effective (Figure 9). By utilizing the same command line for blockedr as shown in Figure 5, along with the block <path> command illustrated in Figure 8, EDRSilencer successfully blocked the logs from the endpoint.


Attack Chain
As shown in Figure 10, EDRSilencer is executed as follows:
Process Discovery
The attack chain begins with the process discovery phase, where EDRSilencer scans the system to compile a list of running processes associated with common EDR products.
Execution
In the execution phase, the attacker runs EDRSilencer using the blockedr argument to block traffic from all detected EDR processes. Alternatively, the attacker can use the block <path> argument to block traffic from a specific process by providing its full path.
Privilege Escalation
Moving to privilege escalation, EDRSilencer configures WFP filters to block outbound network communications for both IPv4 and IPv6 protocols. These filters are marked as persistent, ensuring they remain effective even after the system reboots. The tool dynamically identifies running EDR processes and applies WFP filters to block their communications.
Impact
Finally, EDR tools are rendered ineffective as they are unable to send telemetry, alerts, or other data to their management consoles. During testing, it was observed that some EDR processes were still able to communicate because they were not included in the hardcoded list. After identifying and blocking additional processes not included in the hardcoded list, the EDR tools failed to send logs, confirming the tool’s effectiveness. This allows malware or other malicious activities to remain undetected, increasing the potential for successful attacks without detection or intervention.

Conclusion
In our ongoing efforts to monitor and mitigate emerging threats, we have observed based on our internal telemetry that certain threat actors are attempting to leverage EDRSilencer as part of their attack strategies. This highlights the ongoing trend of threat actors seeking more effective tools for their attacks, especially those designed to disable antivirus and EDR solutions.
The emergence of EDRSilencer as a means of evading endpoint detection and response systems marks a significant shift in the tactics employed by threat actors. By disabling critical security communications, it enhances the stealth of malicious activities, increasing the potential for successful ransomware attacks and operational disruptions. This is indicative of an evolving threat landscape that necessitates a proactive and adaptive security posture, combining multi-layered defenses and continuous monitoring to mitigate risks. Organizations must remain vigilant, employing advanced detection mechanisms and threat hunting strategies to counteract these sophisticated tools and protect their digital assets. As threat actors continue to innovate, Trend Micro persists in its commitment to enhancing security measures and sharing insights to safeguard against future attacks.
Security recommendations
Trend Micro products already detect this tool as malware. As an additional layer of protection, Behavior Monitoring (AEGIS) also flags this malware’s behavior and prevents its execution for Trend Micro products that have this advanced detection feature enabled.
We have also developed a suite of proactive detection strategies and solutions that security practitioners can apply to identify and neutralize this threat before it can be fully deployed and exploited by threat actors:
- Implementing multi-layered security controls
- Network segmentation – Isolate critical systems and sensitive data to limit lateral movement
- Defense-in-depth – Use multiple layers of security controls (including firewalls, intrusion detection systems, antivirus, and EDR) to create redundancy.
- Enhancing endpoint security
- Behavioral analysis – Deploy security solutions that use behavioral analysis and anomaly detection to identify unusual activities that might bypass traditional EDR
- Application whitelisting – Only allow approved applications to run, reducing the risk of malicious software execution.
- Conducting continuous monitoring and threat hunting
- Threat hunting – Proactively search for indicators of compromise (IoCs) and advanced persistent threats (APTs) within your network.
- Implementing strong access controls
- Principle of least privilege – Ensure users and applications have the minimum level of access necessary to perform their functions.
Trend Micro Vision One Threat Intelligence
To stay ahead of evolving threats, Trend Micro customers can access a range of Intelligence Reports and Threat Insights within Trend Micro Vision One. Threat Insights helps customers stay ahead of cyber threats before they happen and be better prepared for emerging threats. It offers comprehensive information on threat actors, their malicious activities, and the techniques they use. By leveraging this intelligence, customers can take proactive steps to protect their environments, mitigate risks, and respond effectively to threats.
Trend Micro Vision One Intelligence Reports App [IOC Sweeping]
EDRSilencer Compromising Endpoint Security Monitoring
Trend Micro Vision One Threat Insights App
Emerging Threats: EDRSilencer Compromising Endpoint Security Monitoring
Hunting Queries
Trend Micro Vision One Search App
Trend Micro Vision Once Customers can use the Search App to match or hunt the malicious indicators mentioned in this blog post with data in their environment.
Detecting potential incidents involving EDRSilencer
malName:*Win64.EDRSilencer* AND eventName:MALWARE_DETECTION
More hunting queries are available for Vision One customers with Threat Insights Entitlement enabled.
MITRE ATT&CK Tactics and Techniques
| Tactic | Technique | MITRE ID |
| Discovery | Process Discovery | T1057 |
| Execution | Command and Scripting Interpreter | T1059 |
| Privilege Escalation | Create or Modify System Process | T1543.00 |
| Defense Evasion | Impair Defenses: Disable or Modify Tools | T1562.001 |
| Network Traffic Filtering | T1569.002 | |
| Impact | Network Denial of Service | T1498 |
| Endpoint Denial of Service | T1499 |
Indicators of Compromise (IOCs)
| SHA256 | Detection |
| 721af117726af1385c08cc6f49a801f3cf3f057d9fd26fcec2749455567888e7 | HackTool.Win64.EDRSilencer.REDT |
Source: Original Post