Summary: This article discusses the ongoing growth of a highly advanced server-side malware campaign known as Ebury, which has expanded to include credit card and cryptocurrency theft.
Threat Actor: Ebury | Ebury
Victim: Linux servers | Linux servers
Key Point :
- Ten years after the initial publication of the Operation Windigo white paper, Ebury, a Linux malware campaign, continues to expand and evolve.
- The arrest and conviction of one of the Ebury perpetrators did not stop the botnet from growing.
- Ebury is an OpenSSH backdoor and credential stealer that has been updated multiple times over the years.
- Honeypots are being used to track new samples and network indicators related to Ebury.
ESET Research
One of the most advanced server-side malware campaigns is still growing, with hundreds of thousands of compromised servers, and it has diversified to include credit card and cryptocurrency theft
14 May 2024
•
,
3 min. read

Ten years ago we raised awareness of Ebury by publishing a white paper we called Operation Windigo, which documented a campaign that leveraged Linux malware for financial gain. Today we publish a follow-up paper on how Ebury has evolved, and the new malware families its operators use to monetize their botnet of Linux servers.
The arrest and conviction of one of the Ebury perpetrators following the Operation Windigo paper did not stop the botnet from expanding. Ebury, the OpenSSH backdoor and credential stealer, was still being updated, as we reported in 2014 and 2017.
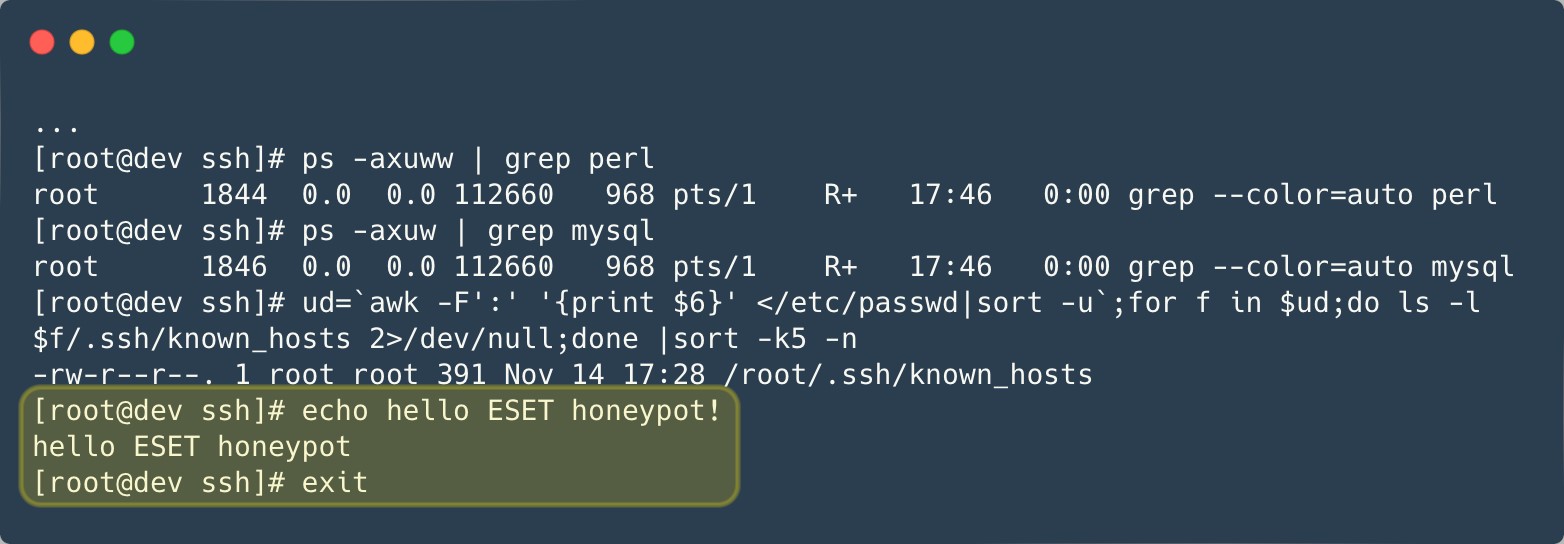
We maintain honeypots to track new samples and network indicators. However, it has become more and more difficult to run such honeypots as Ebury evolved. For instance, one of our honeypots did not react exactly as expected when Ebury was installed. After spending hours trying to debug what was going on, Ebury operators finally abandoned the server and sent a message to show that they knew about our attempts at tricking them, as shown in Figure 1.
In 2021, the Dutch National High Tech Crime Unit (NHTCU) reached out to ESET after they had found Ebury on the server of a victim of cryptocurrency theft. Working together, we gained great visibility into the recent activities of the group and the malware it uses.
Ebury, Ebury everywhere
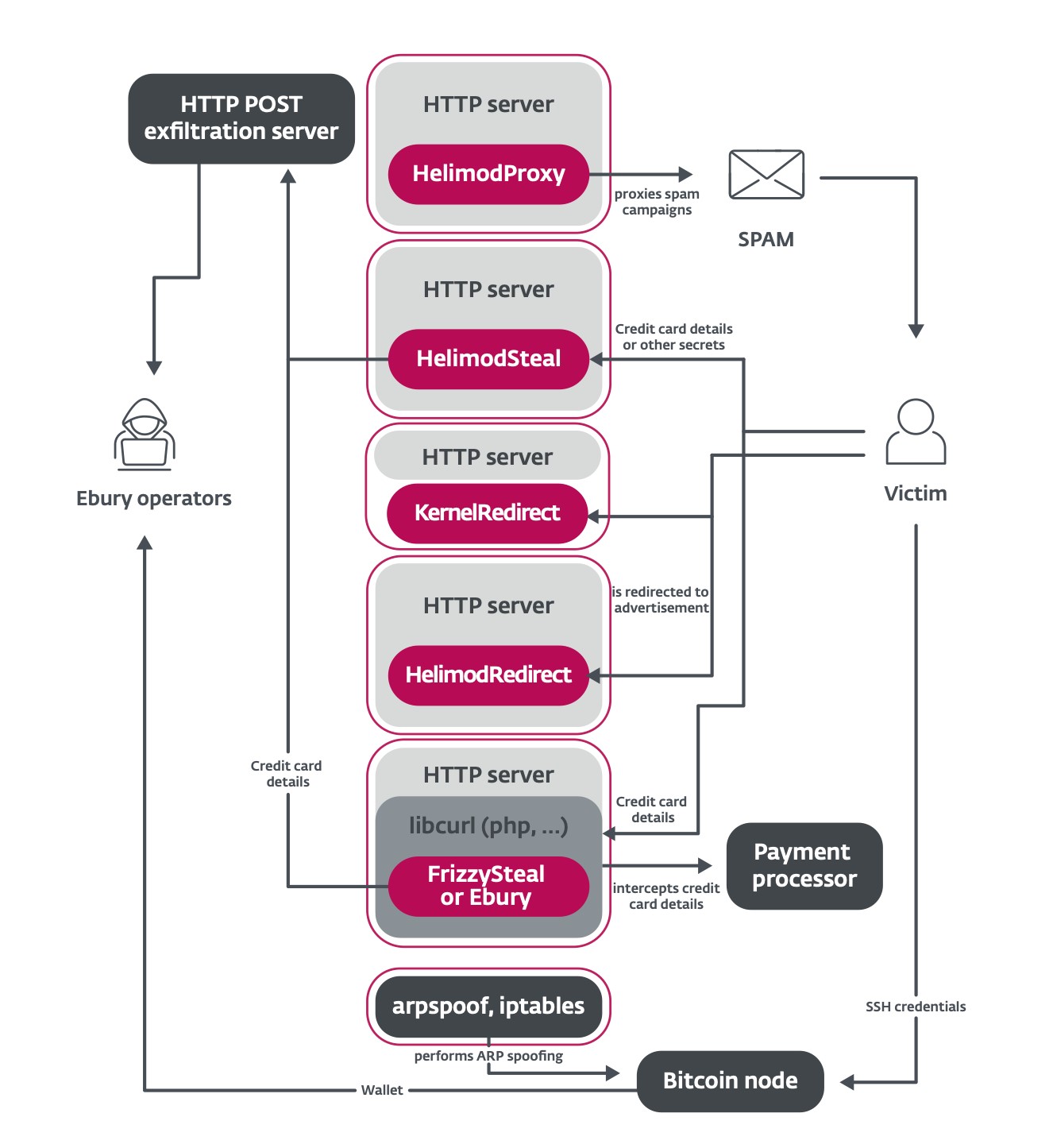
This paper reveals new methods used to propagate Ebury to new servers. Figure 2 summarizes the methods we could document.
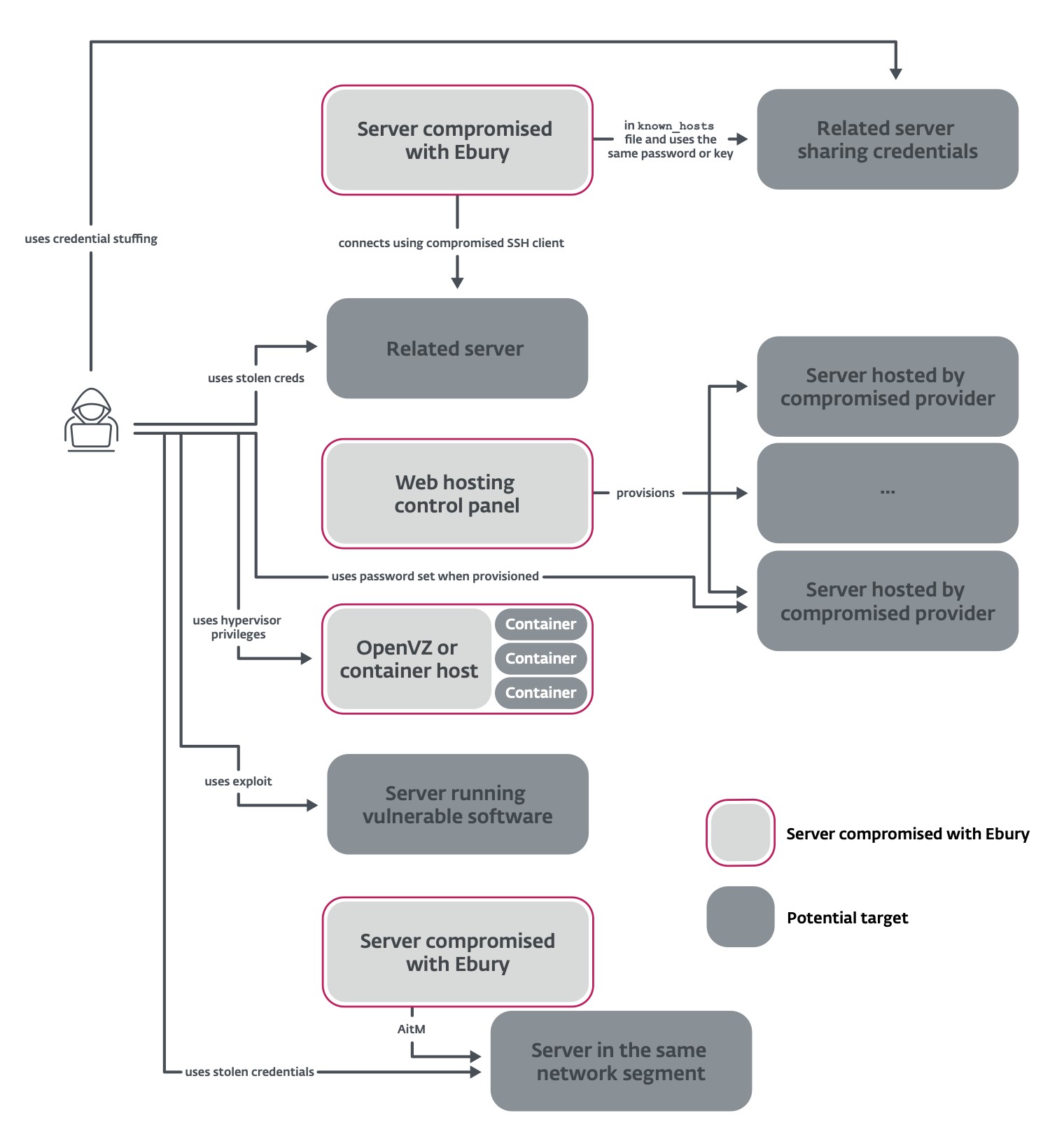
Among the victims are many hosting providers. The gang leverages its access to the hosting provider’s infrastructure to install Ebury on all the servers that are being rented by that provider. As an experiment, we rented a virtual server from one of the compromised hosting providers: Ebury was installed on our server within seven days.
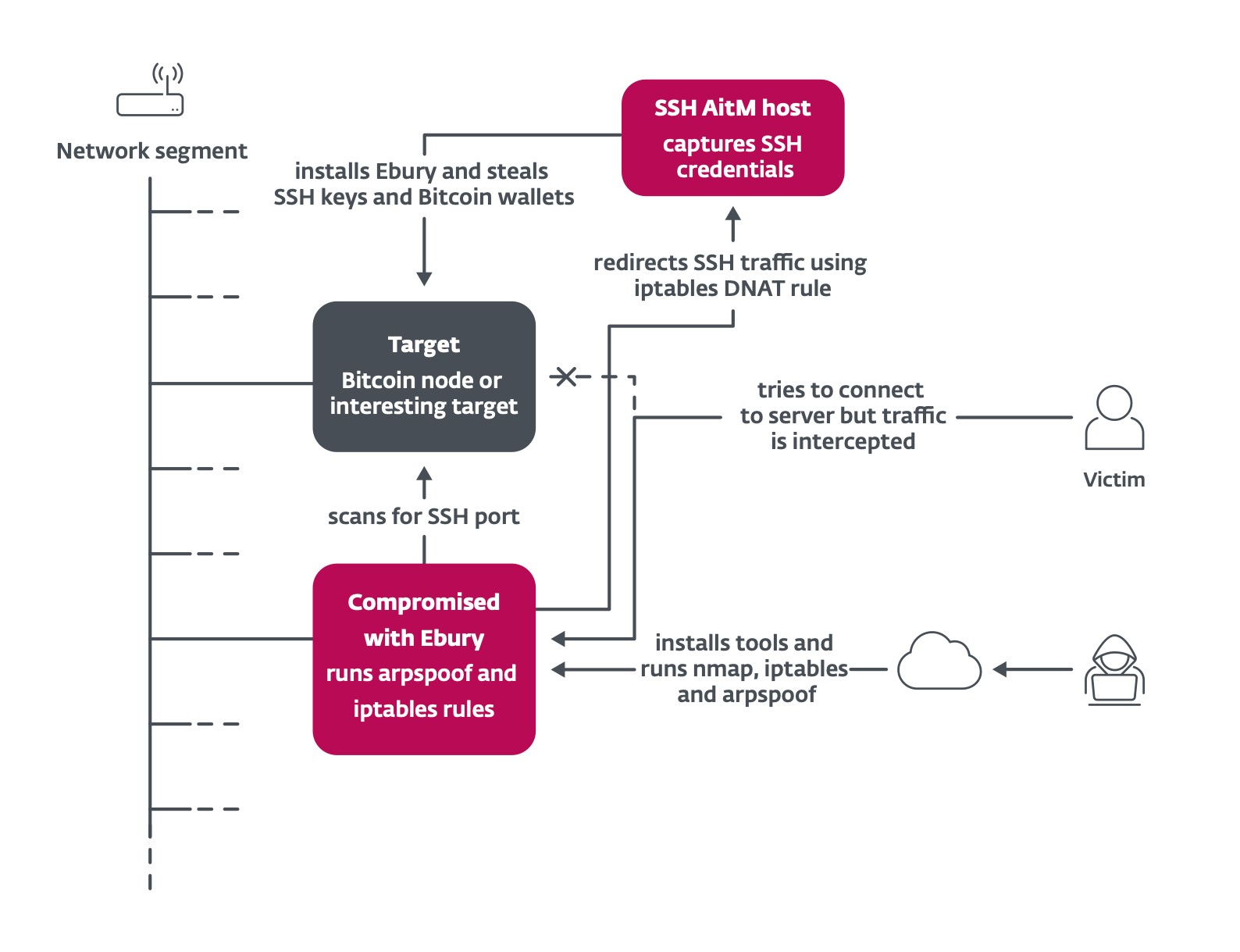
Another interesting method is the use of adversary in the middle to intercept SSH traffic of interesting targets inside data centers and redirect it to a server used to capture credentials, as summarized in Figure 3. Ebury operators leverage existing Ebury-compromised servers in the same network segment as their target to perform ARP spoofing. According to internet telemetry, more than 200 servers were targeted in 2023. Among the targets are Bitcoin and Ethereum nodes. Ebury automatically steals cryptocurrency wallets hosted on the targeted server once the victim types the password to log into it.
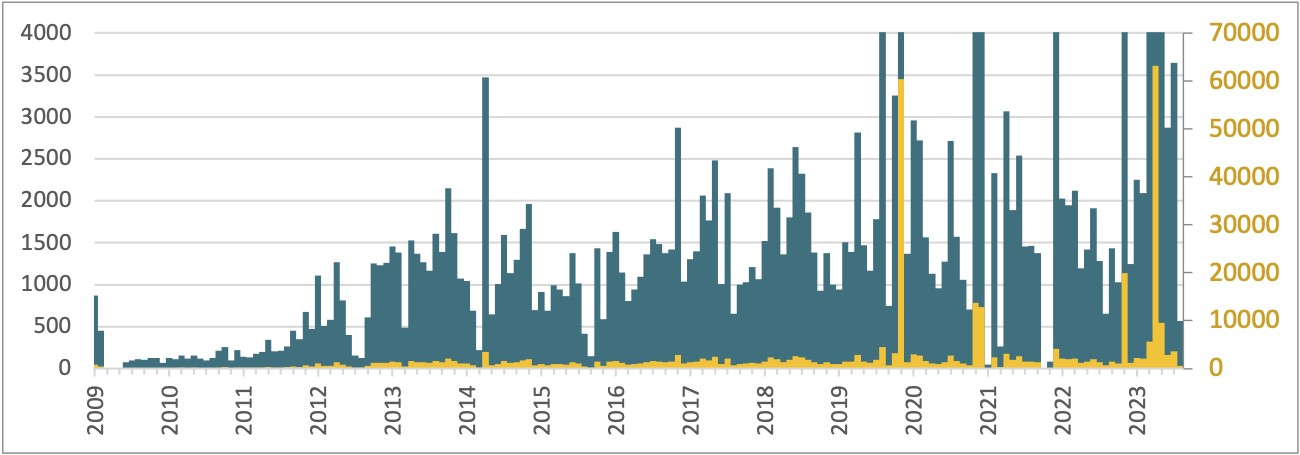
So how effective are all these methods? Combined, about 400,000 servers have been compromised by Ebury since 2009, and more than 100,000 were still compromised as of late 2023. The perpetrators keep track of the systems they compromised, and we used that data to draw a timeline of the number of new servers added to the botnet each month (Figure 4). It is shown using two scales, to demonstrate some of the major incidents where Ebury was deployed on tens of thousands of servers at once.
Monetization
This new paper uncovers new malware families used to leverage the Ebury botnet (Figure 5). In addition to spam and web traffic redirection that are still perpetrated by the gang, HTTP POST requests made to, and from, the servers are leveraged to steal financial details from transactional websites.
Hiding deeper
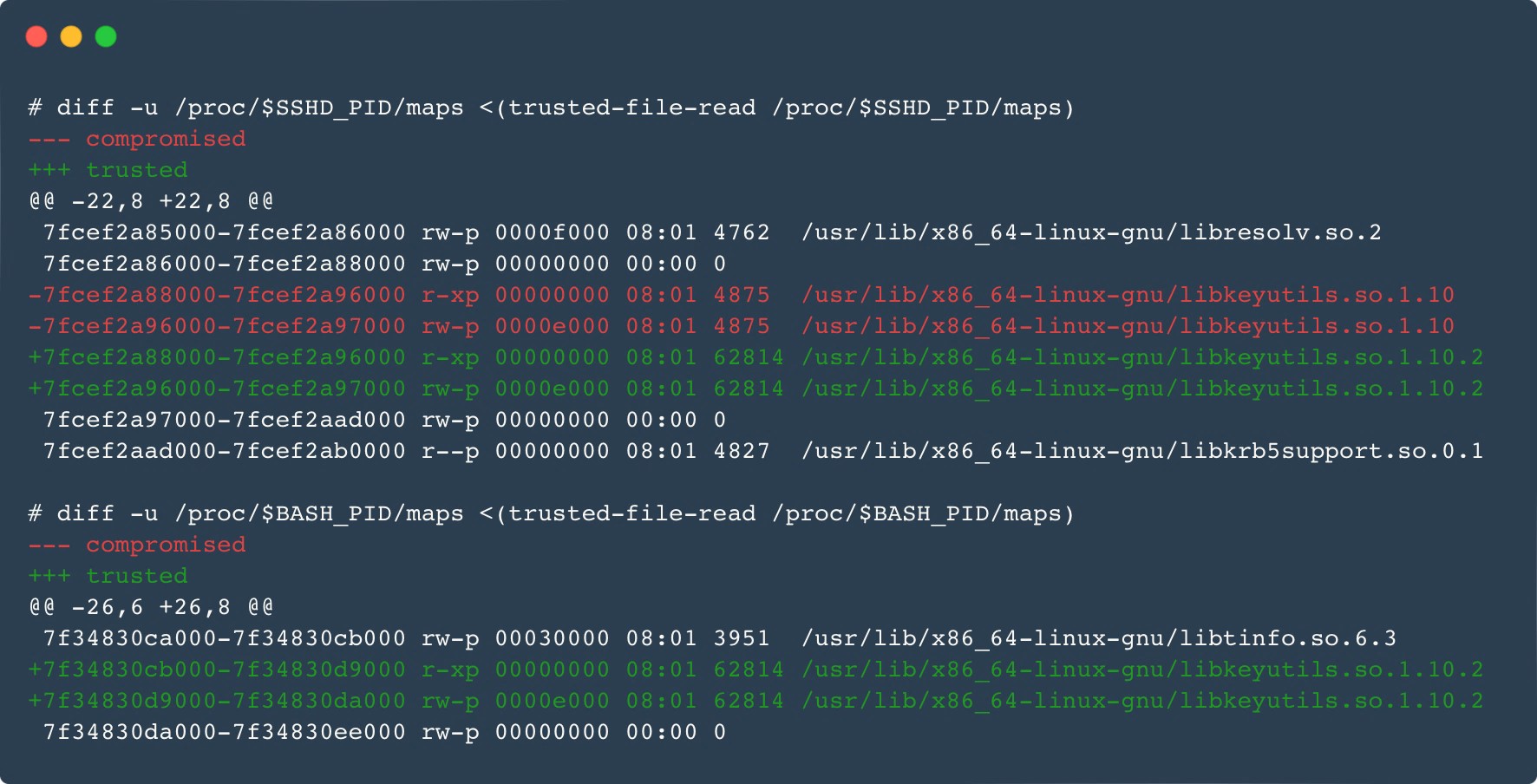
The Ebury malware family itself has also been updated. The new major version update, 1.8, was first seen in late 2023. Among the updates are new obfuscation techniques, a new domain generation algorithm (DGA), and improvements in the userland rootkit used by Ebury to hide itself from system administrators. When active, the process, the file, the socket, and even the mapped memory (Figure 6) are hidden.
Want to know more? Am I compromised?
The new paper, Ebury is alive but unseen: 400k Linux servers compromised for cryptocurrency theft and financial gain, goes into more details about each of Ebury’s aspects, including many technical specifics.
Indicators of compromise are also available in ESET’s malware-ioc GitHub repository, and a detection script is in the malware-research repository.
For any inquiries about our research published on WeLiveSecurity, please contact us at threatintel@eset.comESET Research offers private APT intelligence reports and data feeds. For any inquiries about this service, visit the ESET Threat Intelligence page.
“An interesting youtube video that may be related to the article above”
